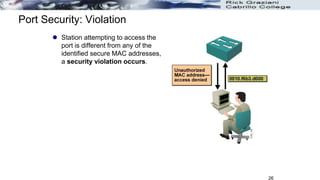
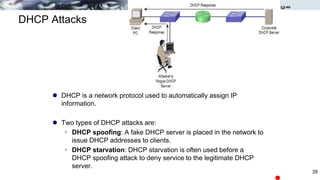
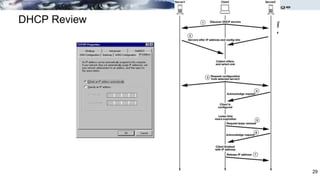
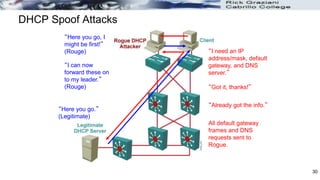
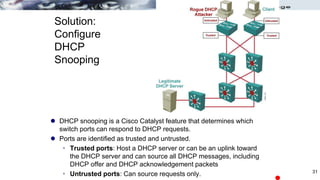
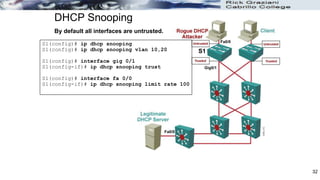
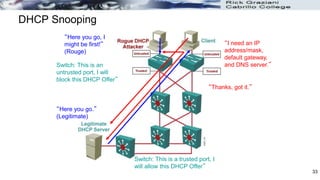
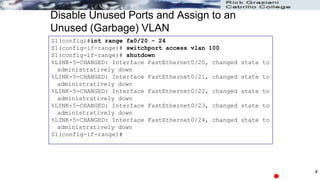
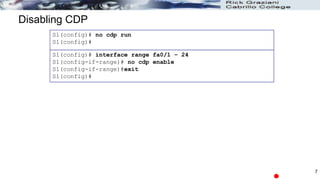
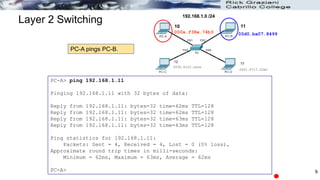
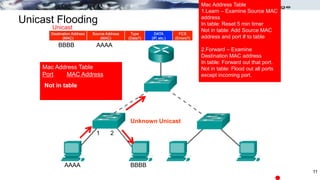
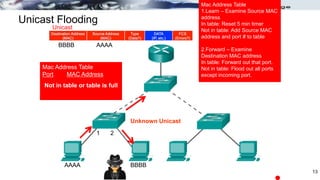
The document discusses security concerns and mitigation strategies for switches in local area networks (LANs). It describes various attacks that switches are vulnerable to, such as password attacks, denial-of-service attacks, CDP attacks, and MAC address flooding. It recommends disabling unused ports, disabling the Cisco Discovery Protocol when not in use, configuring port security, and configuring DHCP snooping to help mitigate these attacks. The document then provides configuration examples for disabling unused ports, the Cisco Discovery Protocol, and configuring port security on interfaces.





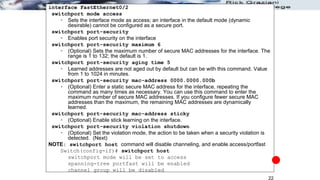
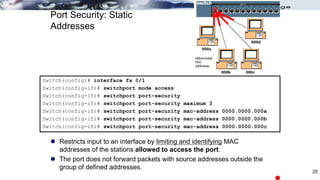
![Configuring Port Security
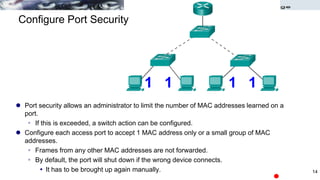
Use the switchport port-security interface command to
enable port security on a port.
It is used to:
Set a maximum number of MAC addresses.
Define violation actions.
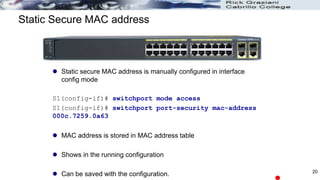
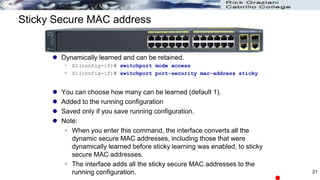
MAC address(es) can be learned dynamically, entered manually,
or learned and retained dynamically.
Set the aging time for dynamic and static secure address entries.
To verify port security status: show port-security
switchport port-security [max value] [violation {protect |
restrict | shutdown}] [mac-address mac-address [sticky]]
[aging time value]
Switch(config-if)#
15](https://image.slidesharecdn.com/securityconcernsinlans-230913062403-d1e0fb75/85/Security-Concerns-in-LANs-pptx-14-320.jpg)