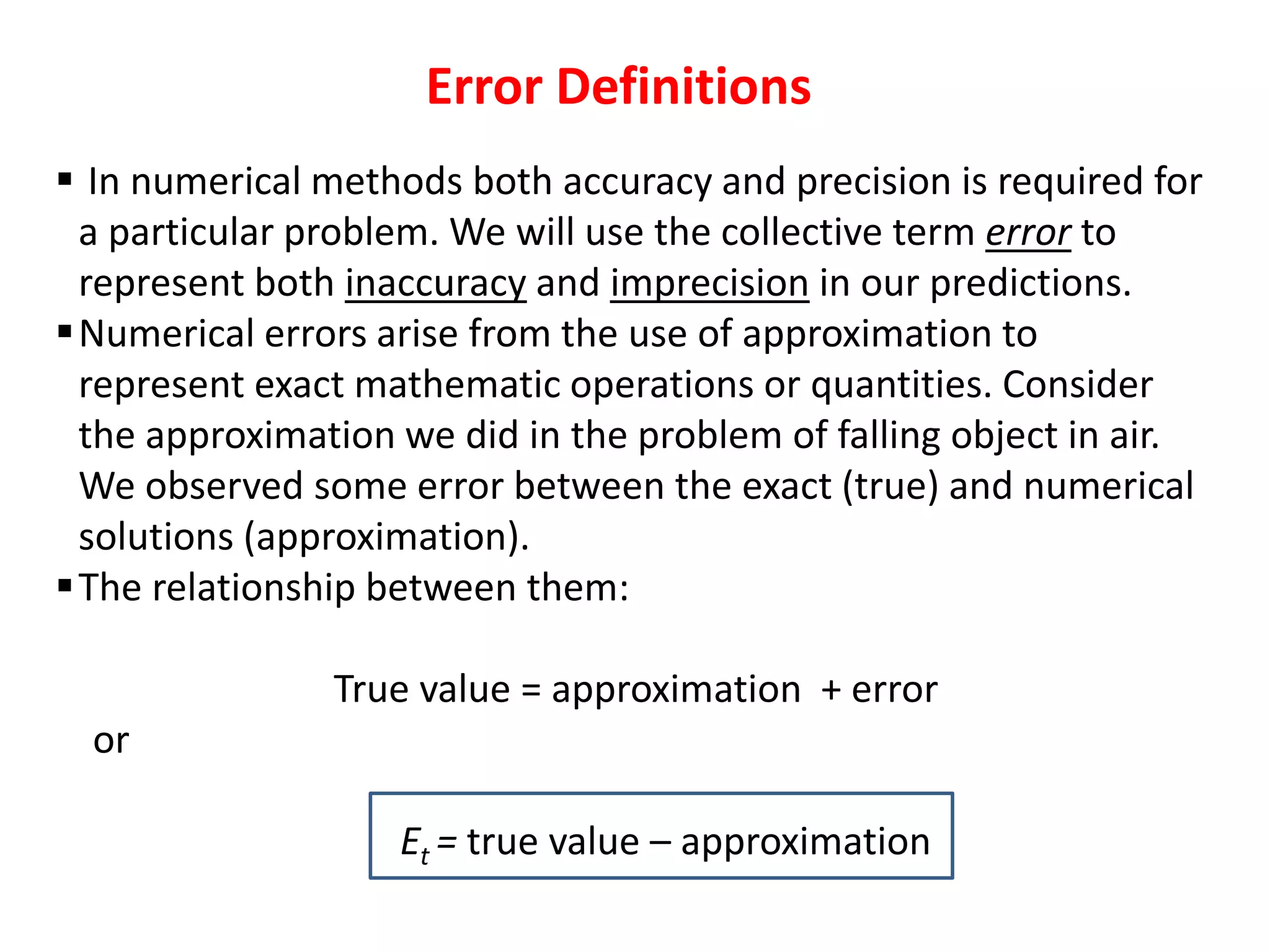
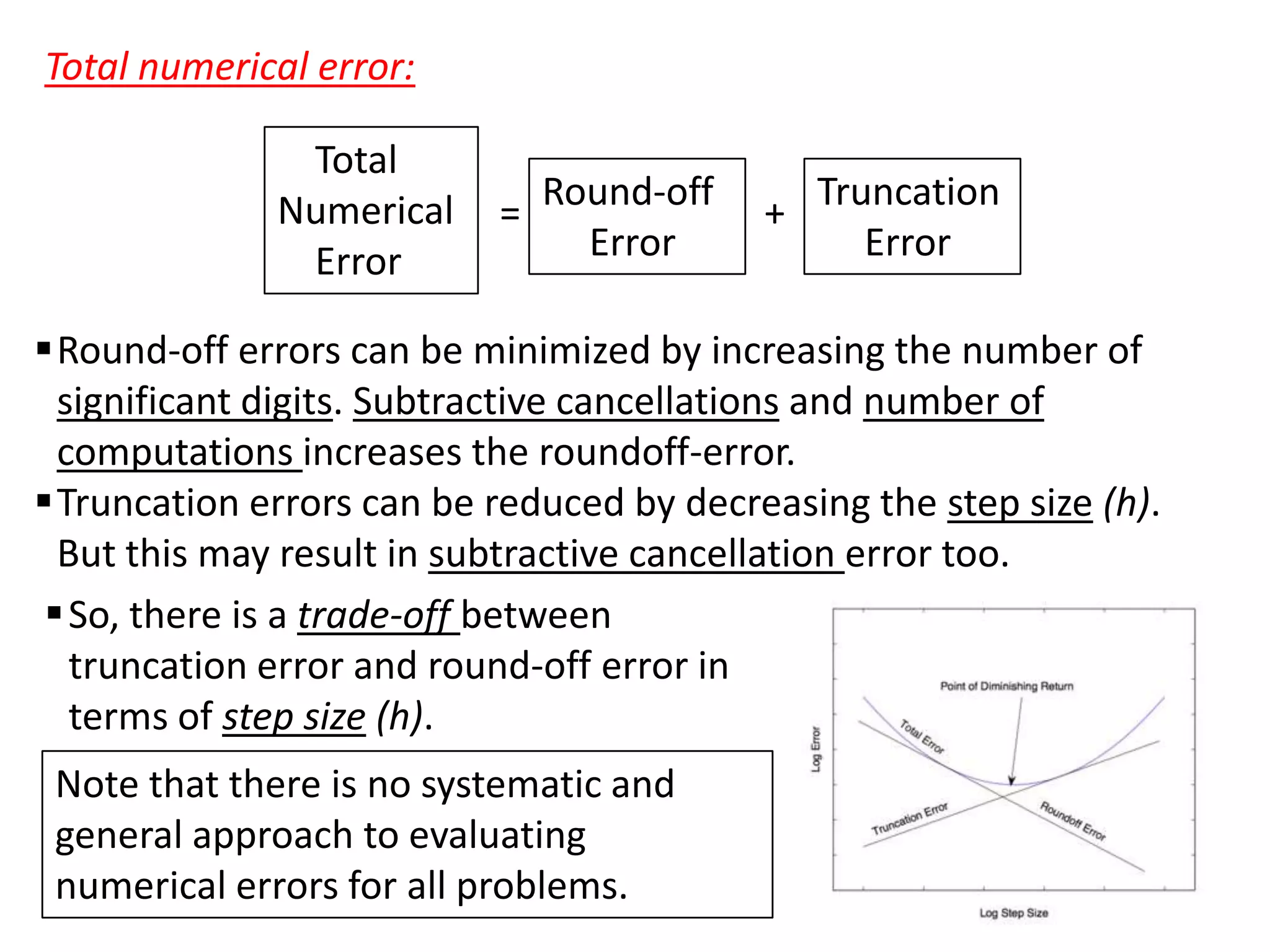
This chapter discusses various types of errors that can occur in numerical analysis calculations, including:
- Round-off errors due to limitations in significant figures and binary representation in computers
- Truncation errors from using approximations instead of exact mathematical representations
- Error propagation when combining results with arithmetic operations
It also covers topics like accuracy vs precision, definitions of relative and absolute errors, floating point representation standards, and techniques to estimate errors like Taylor series expansions and machine epsilon values. The goal is to understand the sources and magnitudes of different errors to improve the reliability of numerical analysis methods.