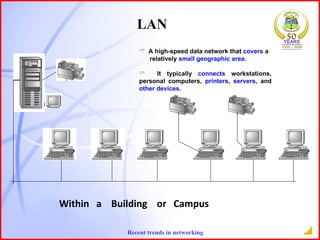
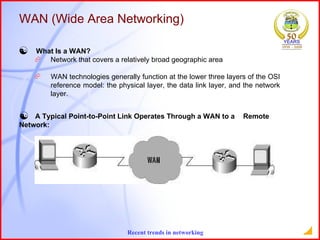
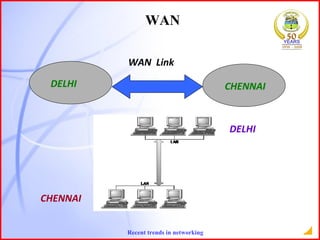
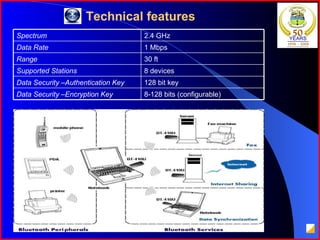
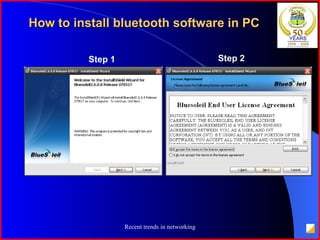
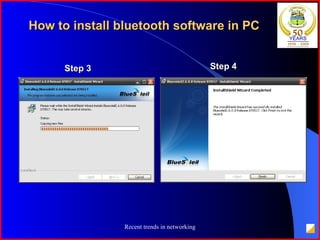
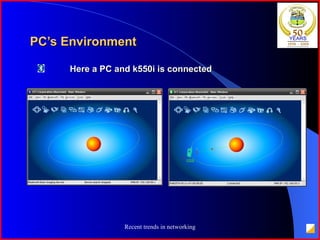
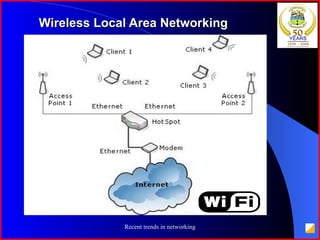
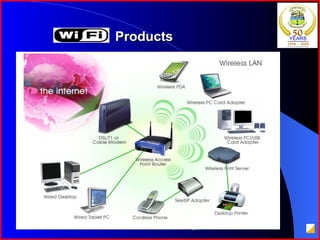
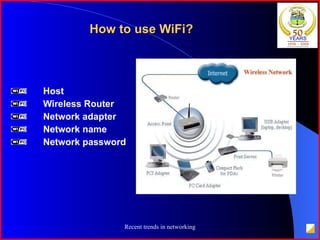
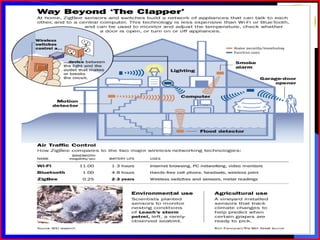
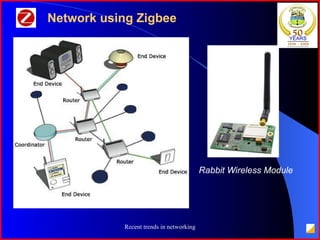
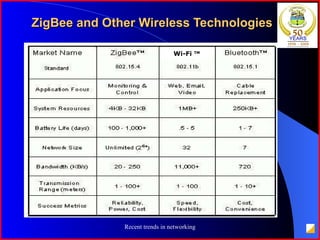
The document provides an overview of recent trends in networking, including Local Area Networks (LAN), Wide Area Networks (WAN), Bluetooth, Wi-Fi, Zigbee, and concludes with a thank you and bibliography. It discusses LAN as a high-speed network within a building or campus, and WAN as a network covering a broader geographic area. It also provides technical details and comparisons of Bluetooth, Wi-Fi, and Zigbee wireless technologies.