This document discusses network security and provides information on several related topics in 3 paragraphs or less:
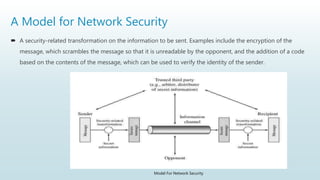
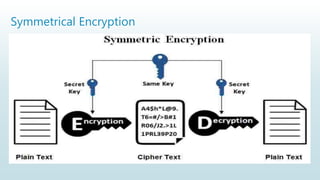
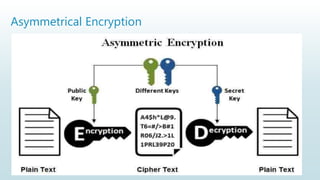
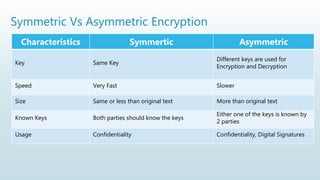
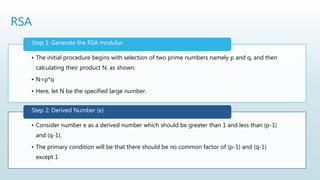
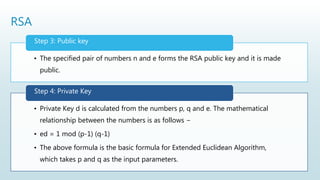
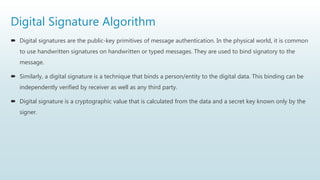
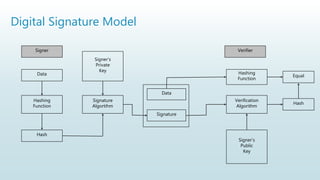
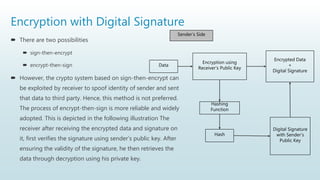
It begins with an overview of a general model for network security that involves designing secure algorithms, generating and distributing secret information, and specifying communication protocols. It then explains the principles of symmetric and asymmetric cryptography, noting examples like AES and RSA. The document concludes with a brief discussion of digital signatures and their importance in message authentication and ensuring data integrity.























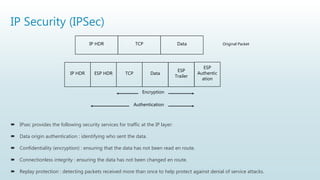
![IP Security (IPSec)
Applications of IPSec
As we all know to help in the security of a network the Internet community has done lot of work and developed
application-specific security mechanisms in numerous application areas, including electronic mail (Privacy Enhanced
Mail, Pretty Good Privacy [PGP]), network management (Simple Network Management Protocol Version
3[SNMPv3]), Web access (Secure HTTP, Secure Sockets Layer [SSL]), and others.
Benefits of IPSec
When IPSec is implemented in a firewall or router, it provides strong security whose application is to all traffic
crossing this perimeter. Traffic within a company or workgroup does not incur the overhead of securityrelated
processing.
IPSec is below the transport layer (TCP, UDP), and is thus transparent to applications. There is no need to change
software on a user or server system when IPSec is implemented in the firewall or router.
Even if IPSec is implemented in end systems, upper layer software, including applications is not affected. IPSec can
be transparent to end users.](https://image.slidesharecdn.com/unit7-211026172902/85/Unit-7-Network-Security-34-320.jpg)