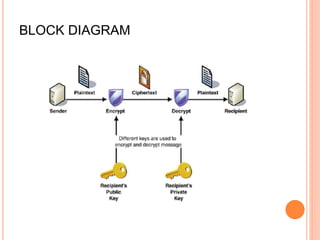
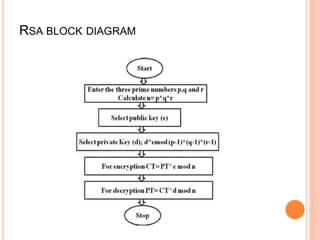
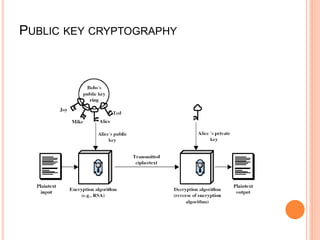
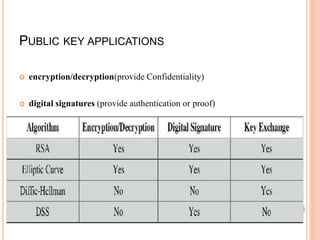
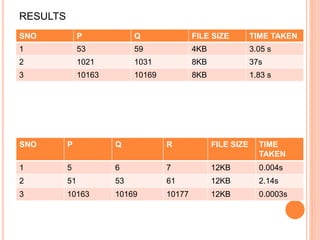
The document discusses using the RSA algorithm to provide data security in cloud computing. It begins with an objective to ensure security and optimize encryption/decryption time using RSA. It then provides background on cloud computing and the need for security. It describes the RSA algorithm, including key generation, encryption, and decryption. It also discusses a proposed method to improve data security and decrease execution time by increasing key length.