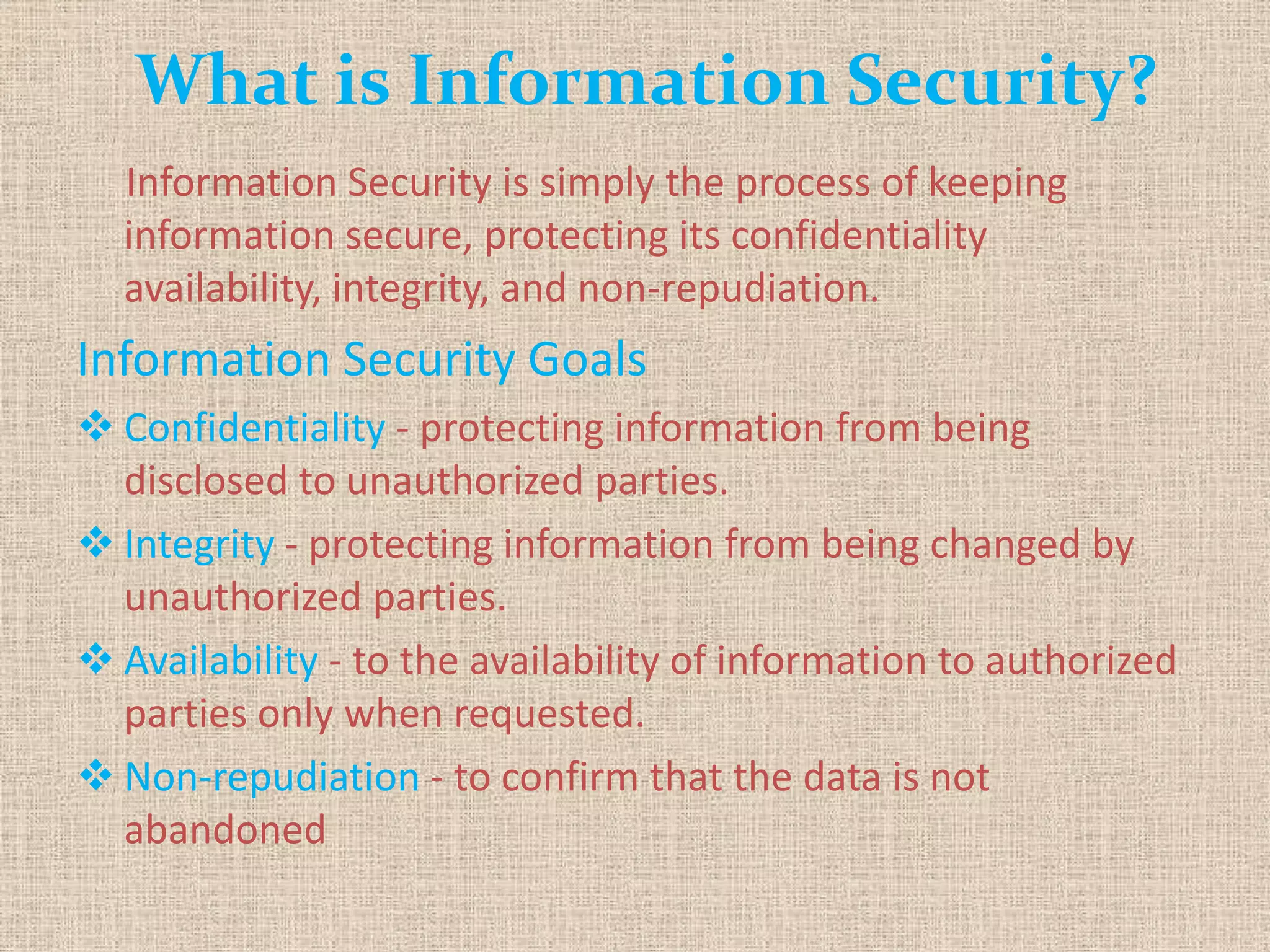
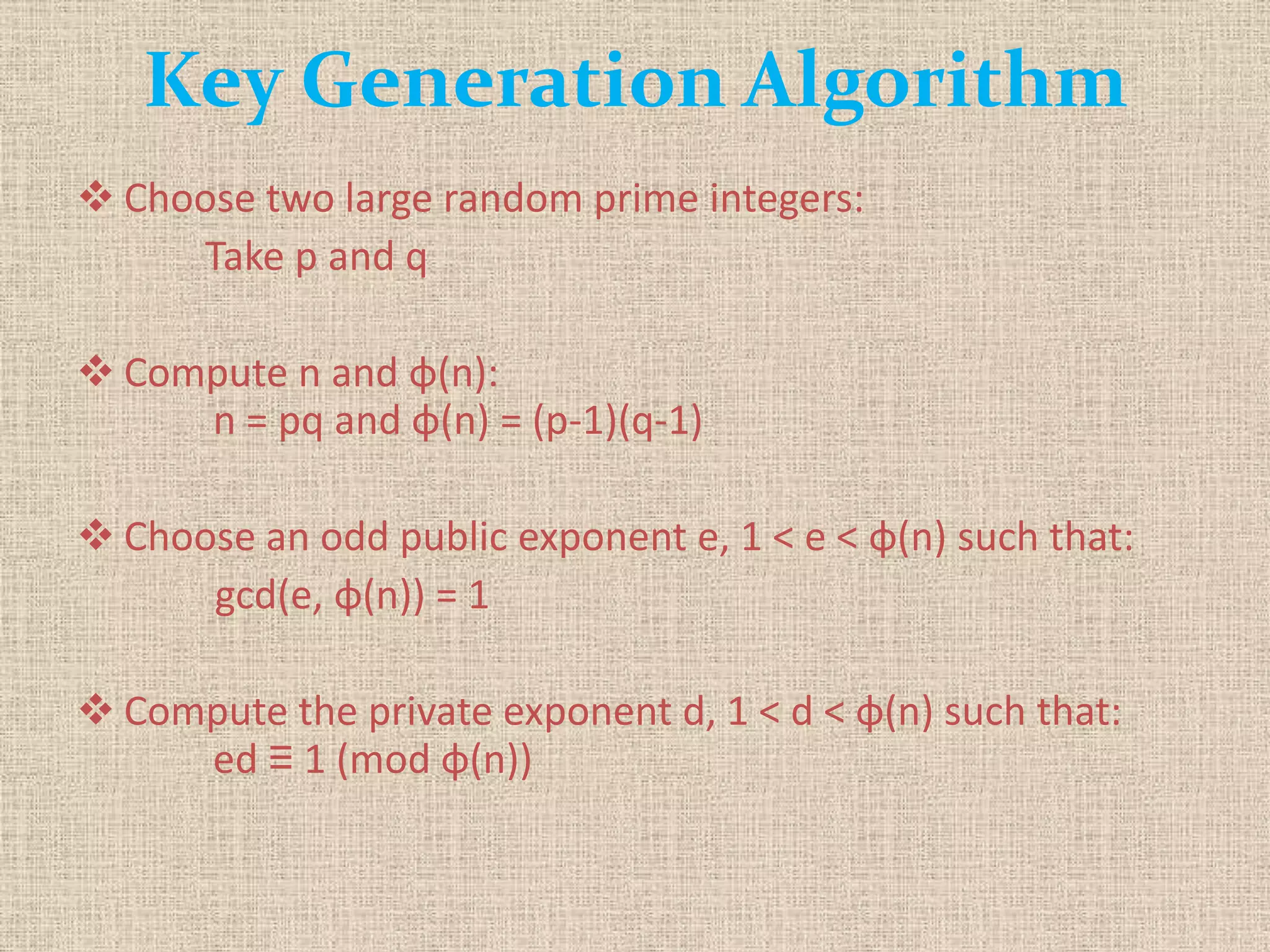
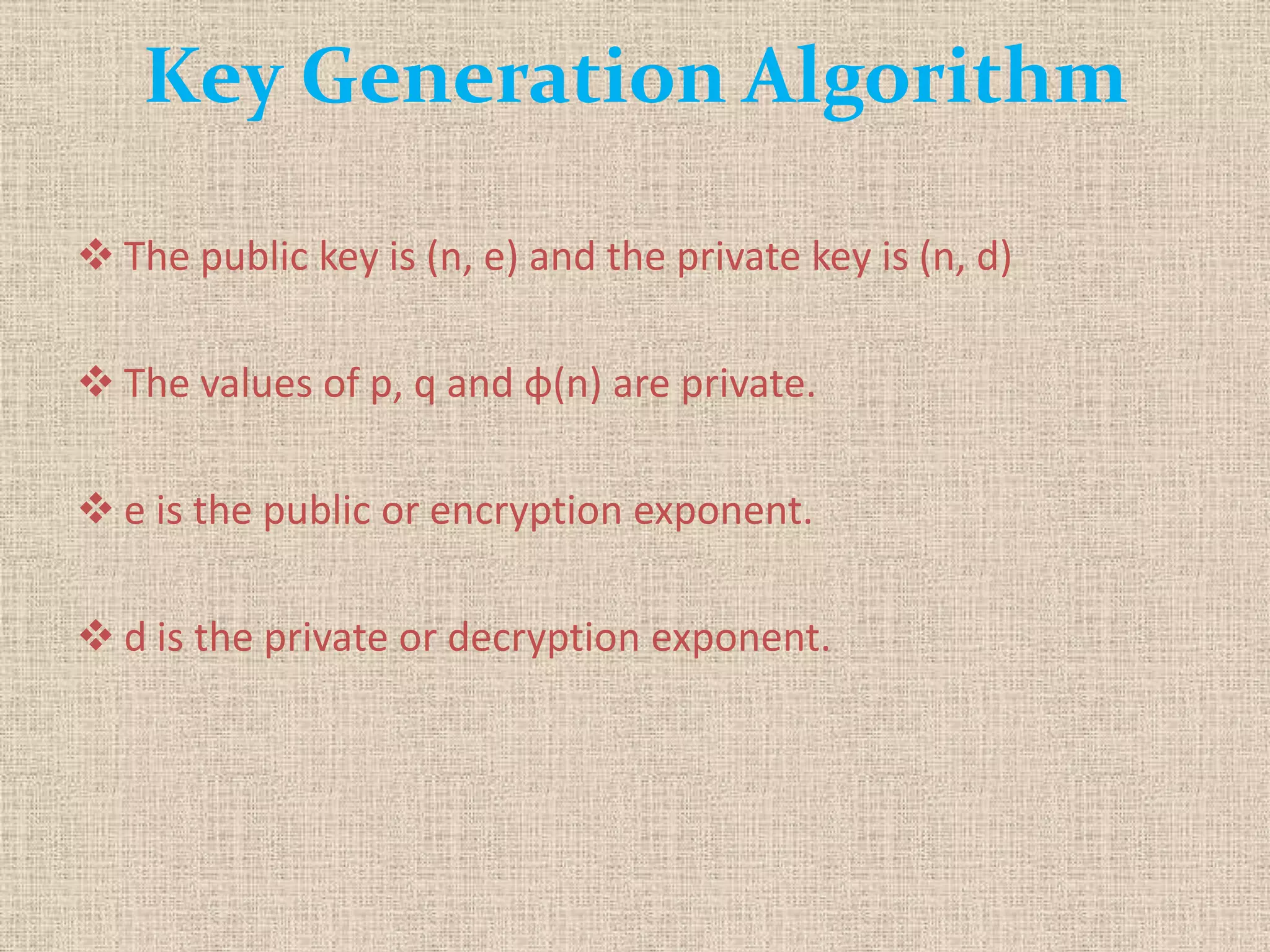
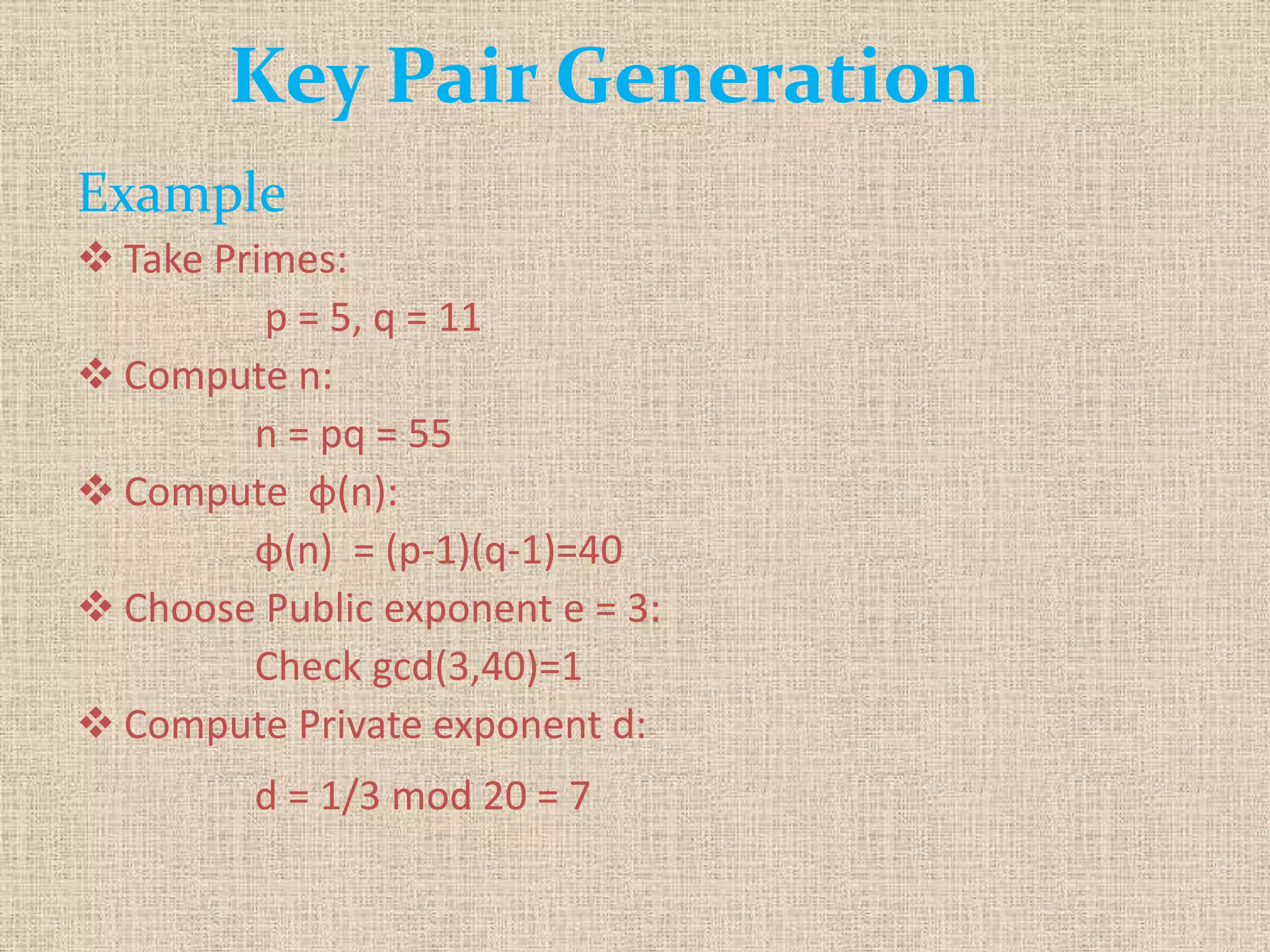
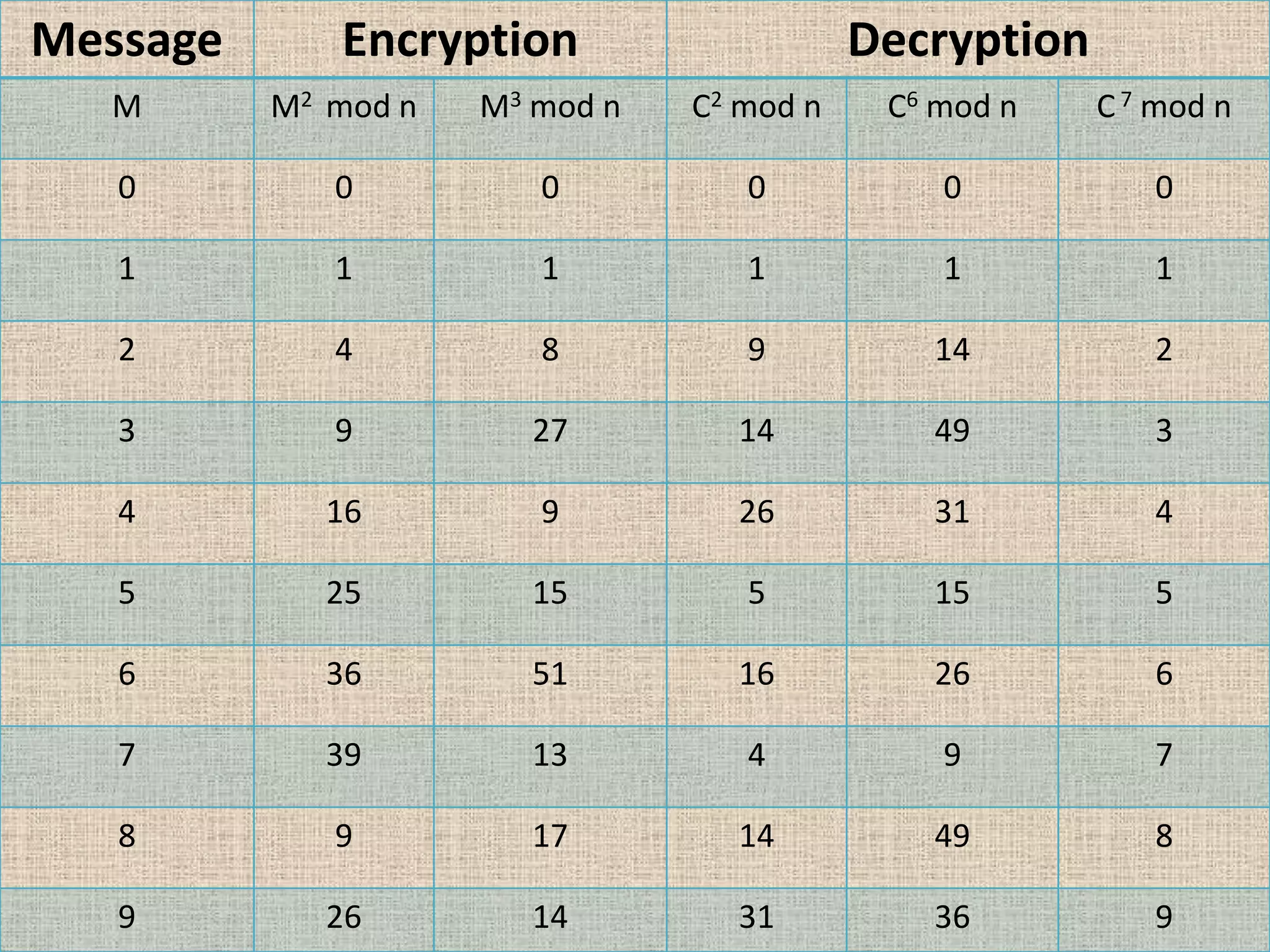
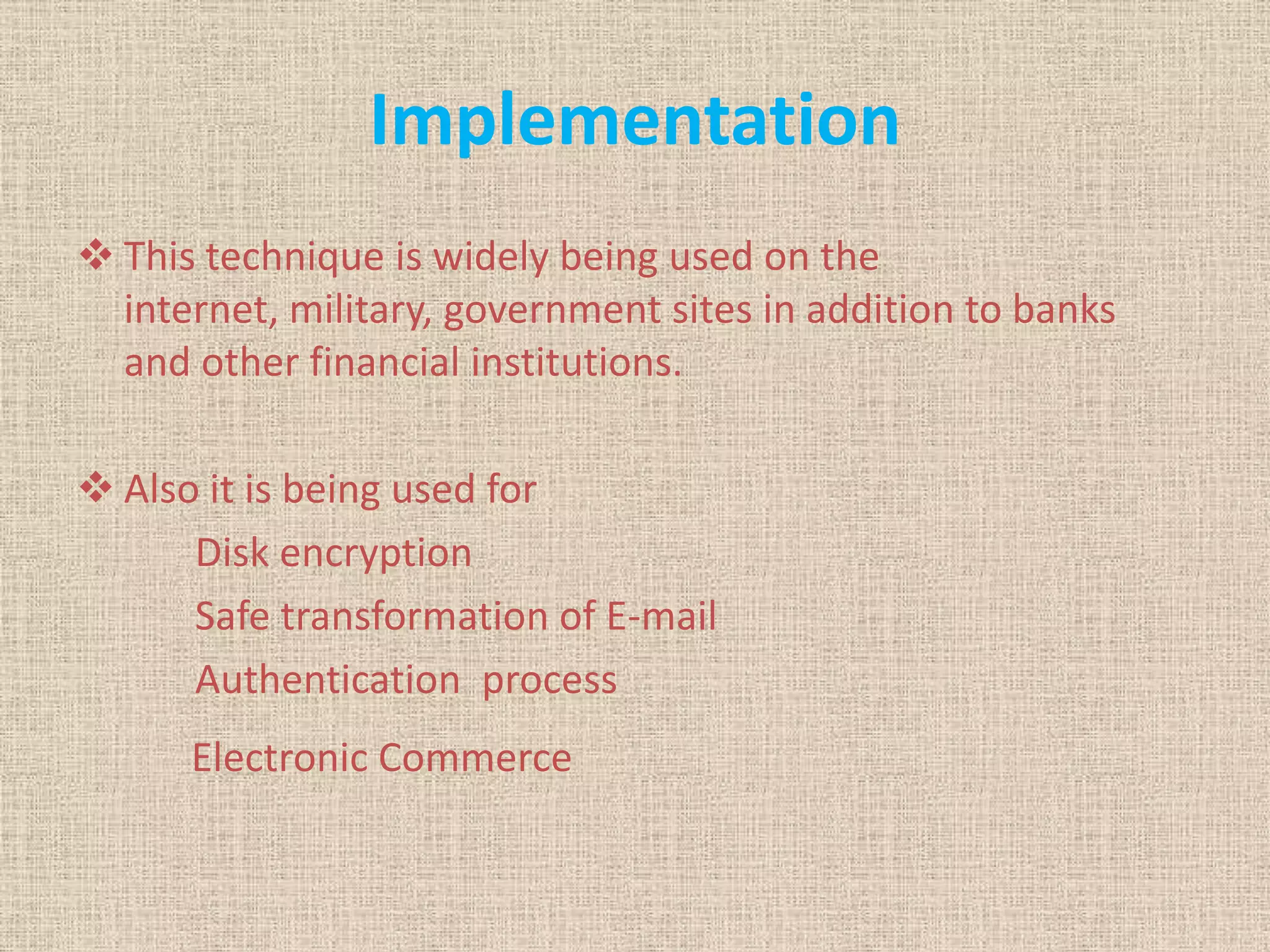
The document provides a comprehensive overview of data, information security, and cryptography, focusing particularly on the RSA cryptosystem. It explains key concepts such as data representation, the role of information security in maintaining confidentiality, integrity, and availability, as well as the mechanics of RSA encryption and decryption using key pairs. The conclusion emphasizes the widespread use and resilience of RSA in cryptographic applications.