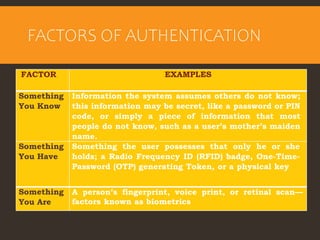
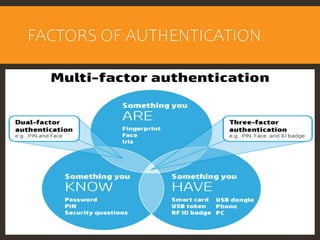
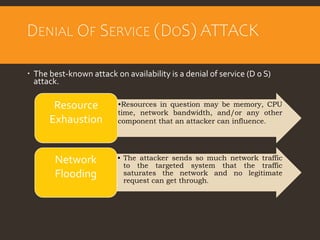
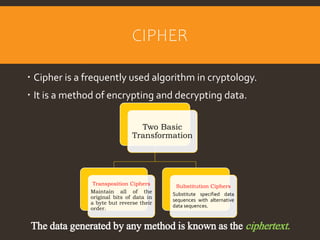
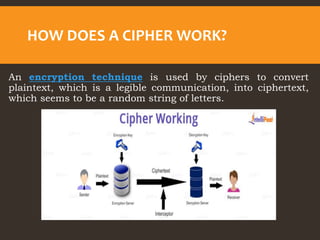
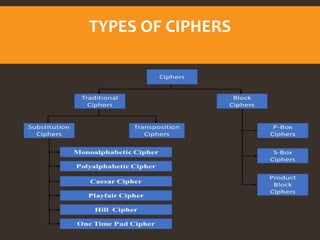
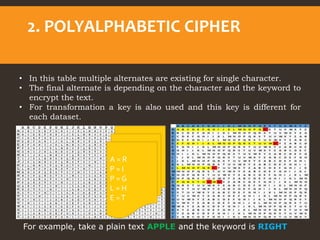
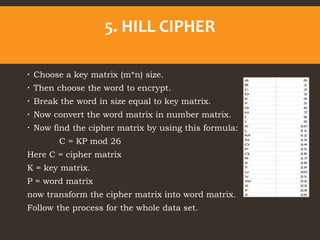
This document provides an overview of cyber security fundamentals and concepts including information assurance, authentication, authorization, non-repudiation, confidentiality, integrity, and availability. It defines these terms and describes how they relate to maintaining the security properties of systems. The document also discusses specific authentication methods like factors of authentication. It explains concepts like authorization, encryption techniques including symmetric and asymmetric cryptography, and the goals of confidentiality, integrity and availability.