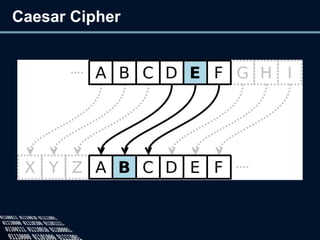
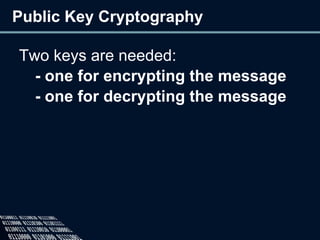
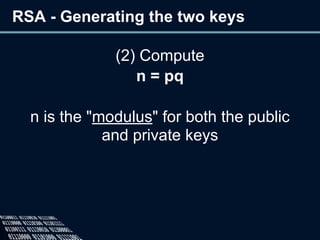
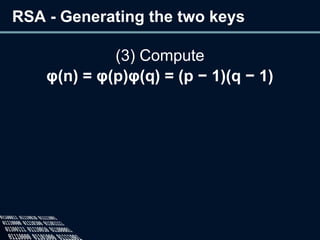
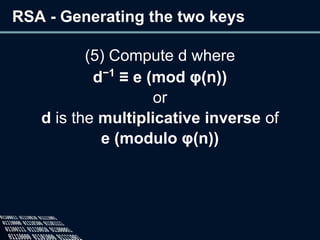
The document provides an overview of cryptography, defining it as the practice of secure communication and outlining its two main branches: private key and public key cryptography. It explains private key cryptography with examples like the Caesar cipher and techniques for cracking it, while also detailing public key cryptography, particularly RSA, including its key generation process. The document emphasizes the importance of mathematics in cryptographic techniques and the need for key secrecy.