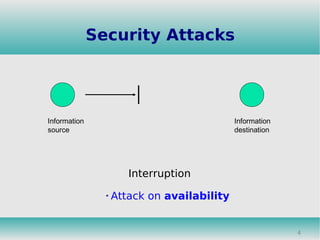
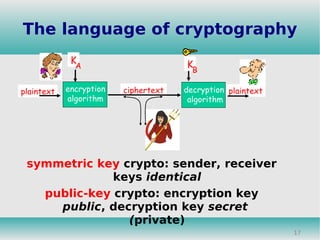
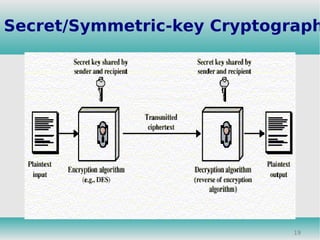
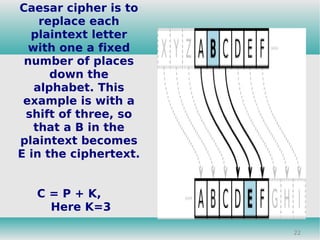
This document discusses cryptography and its role in information security. It describes different types of security attacks like interception, modification, and fabrication. It also summarizes common security services like confidentiality, authentication, integrity, and different encryption techniques like symmetric key cryptography, public key cryptography, Caesar cipher and RSA algorithm. The document concludes with explanations of firewalls and their technical working as a security measure to monitor and control access between networks.