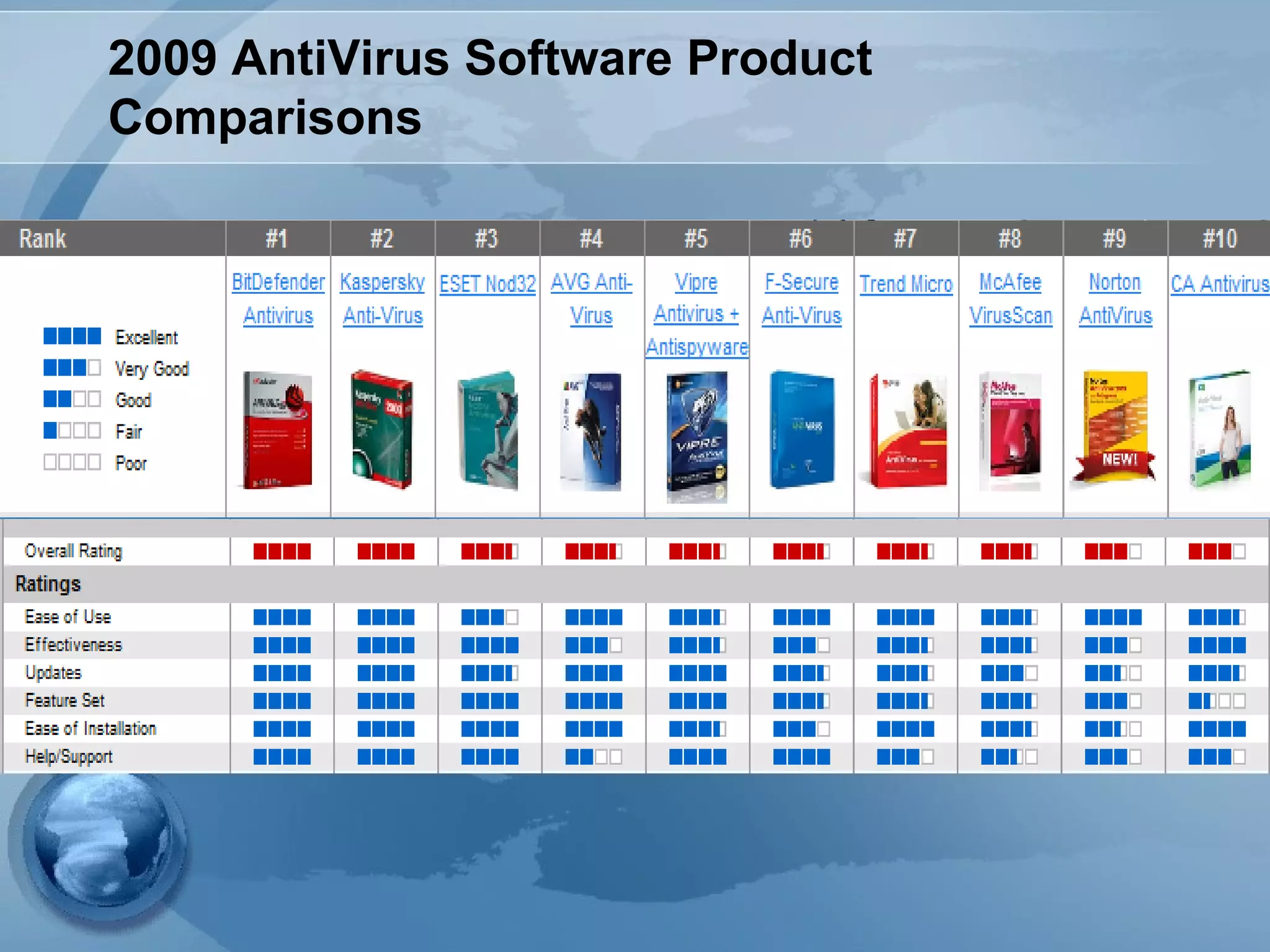
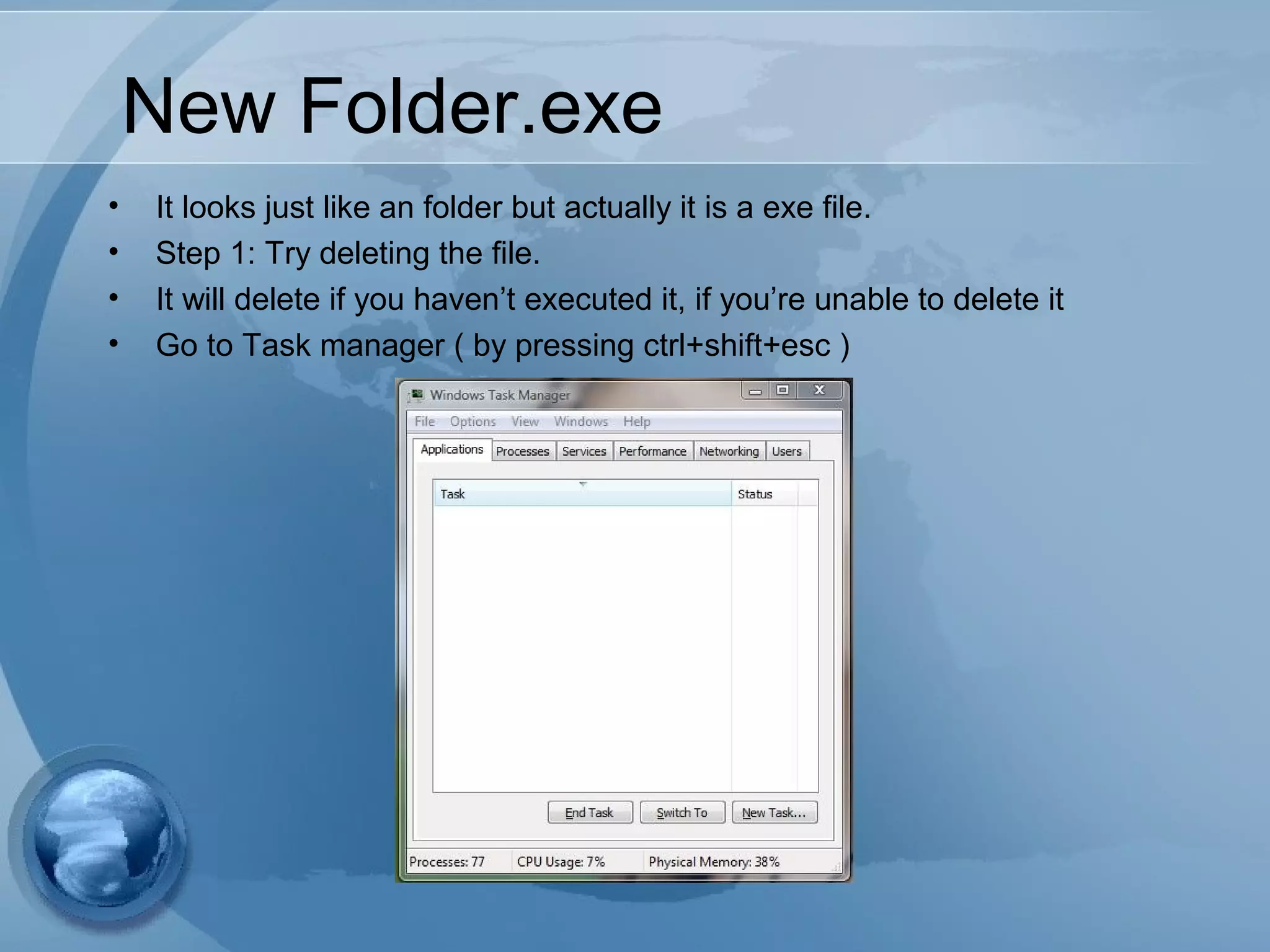
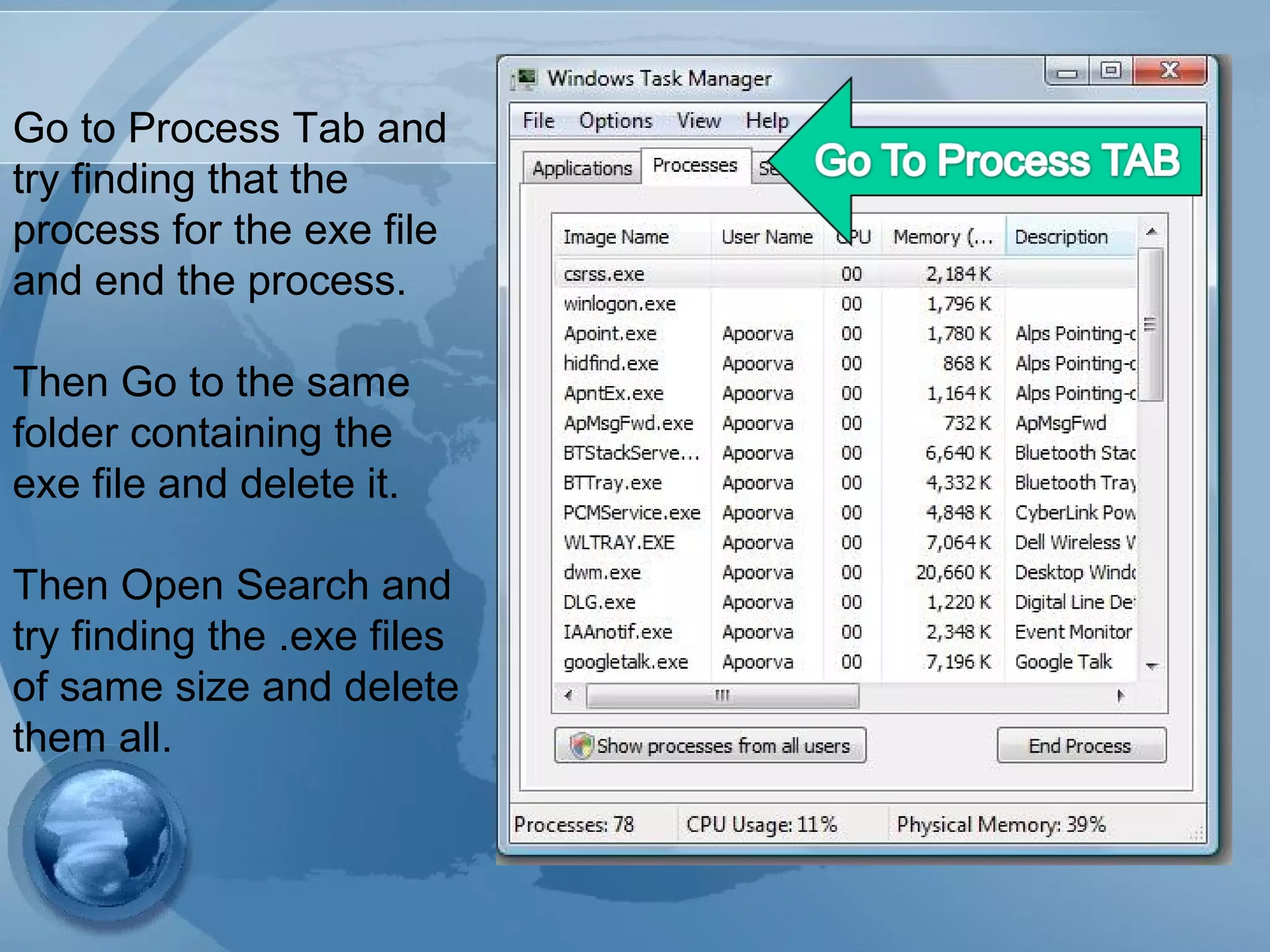
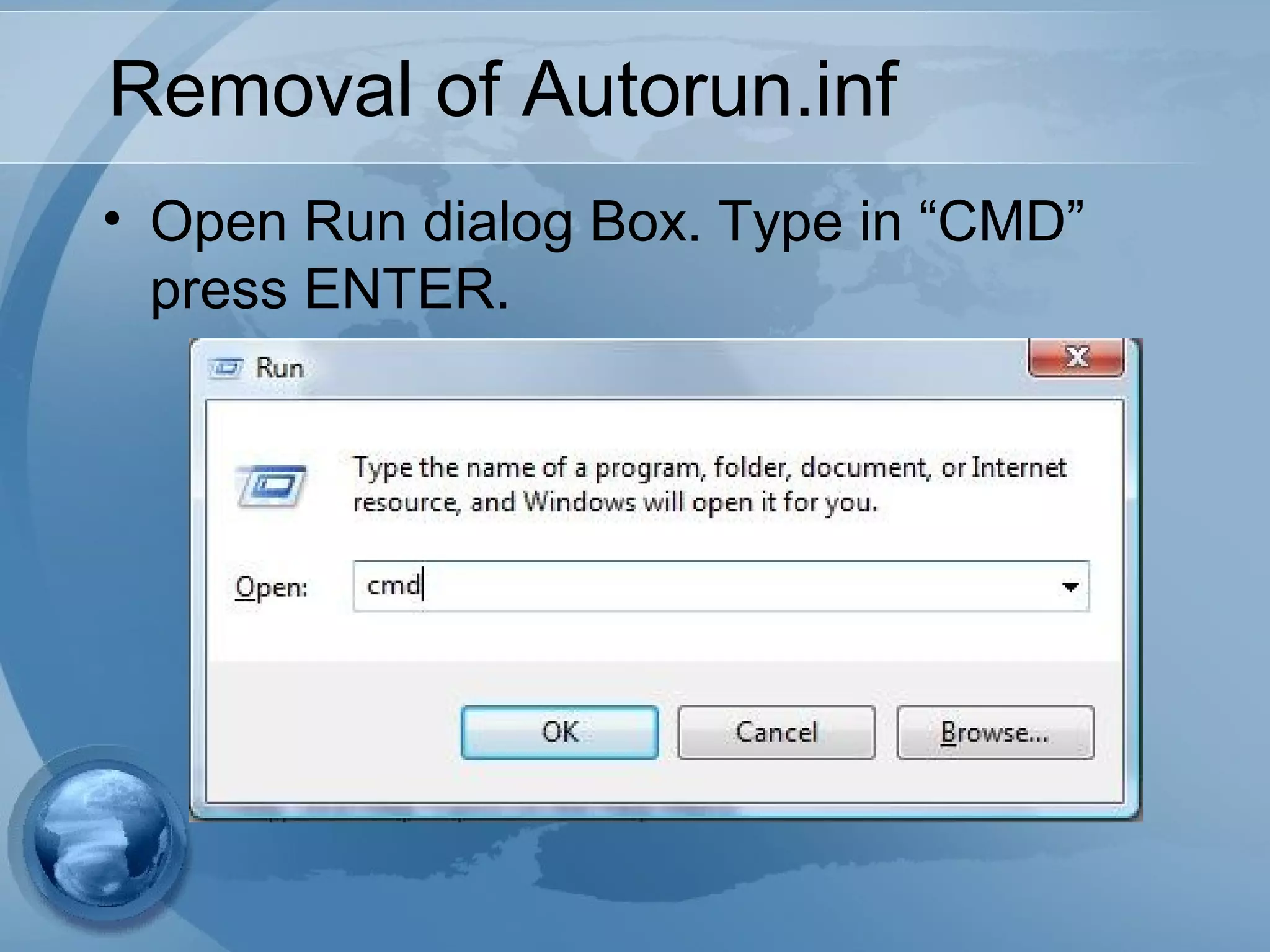
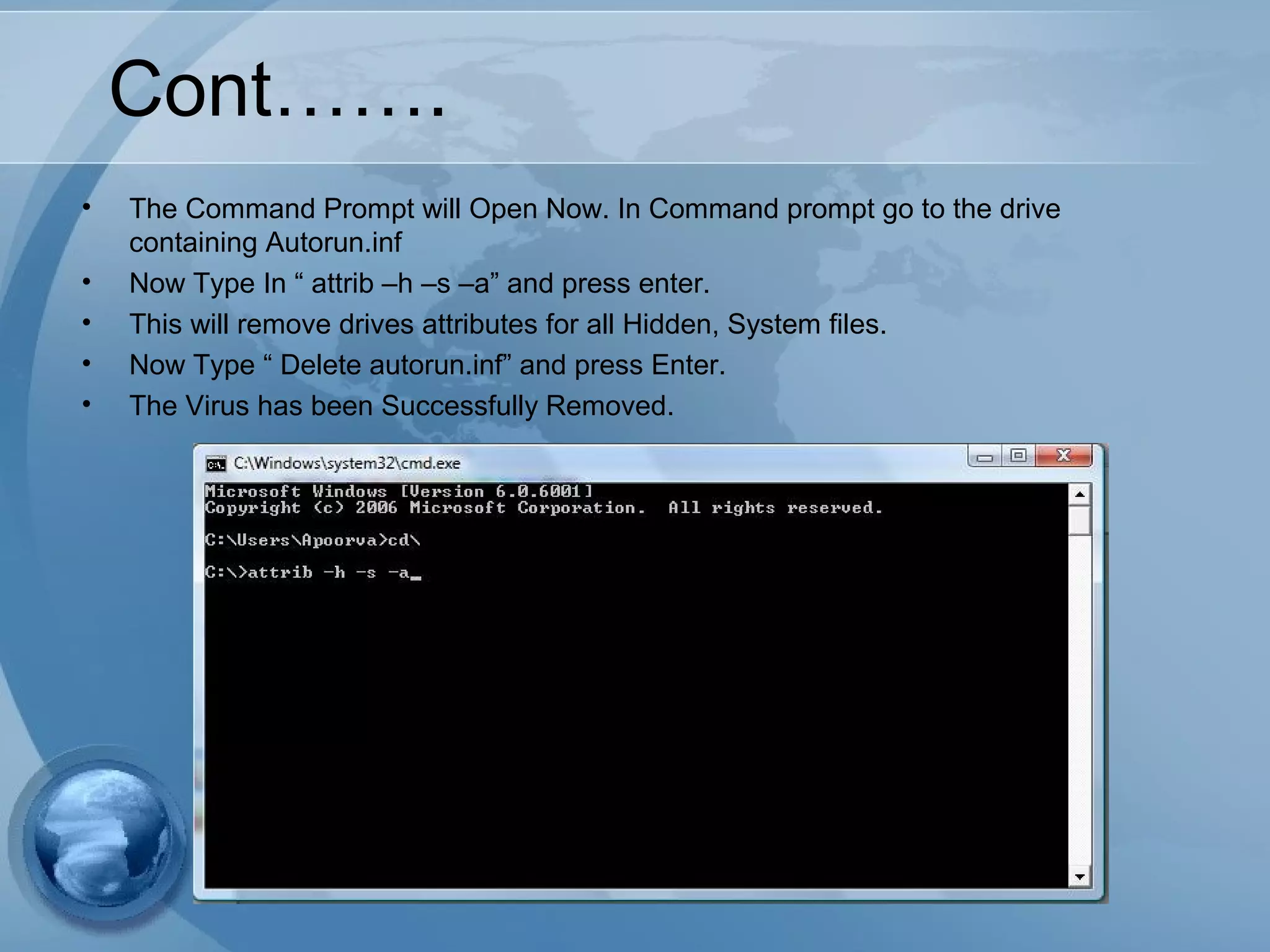
The document discusses computer viruses, including their history, how they spread, symptoms, and prevention methods. It notes that viruses are created by individuals to copy themselves and infect other computers. Today, 87% spread through the internet within hours or days. Symptoms include computers not booting, slowing down, or crashing. The best prevention methods involve using updated antivirus software, being cautious of unexpected files/attachments, and educating others to limit spread.