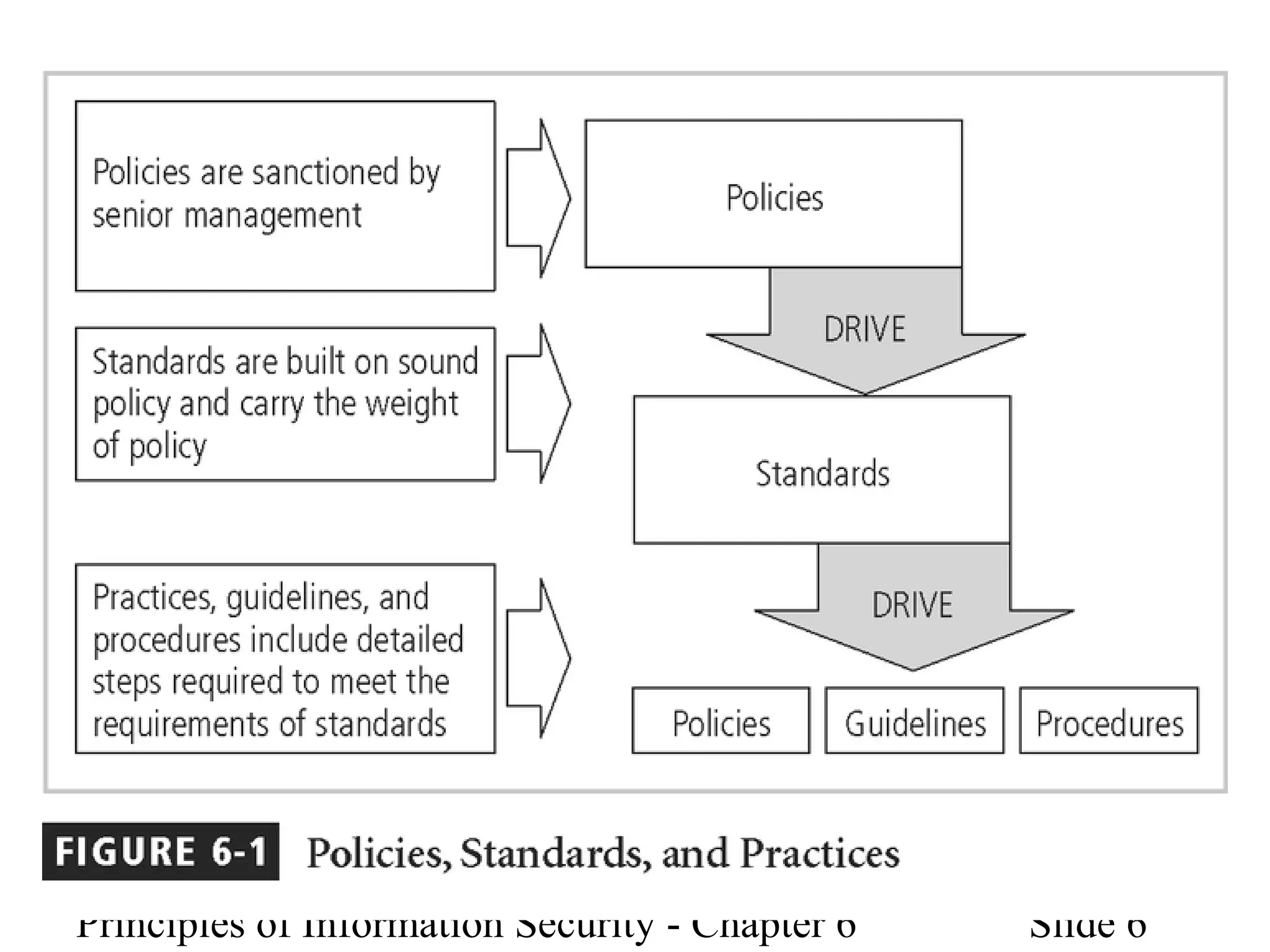
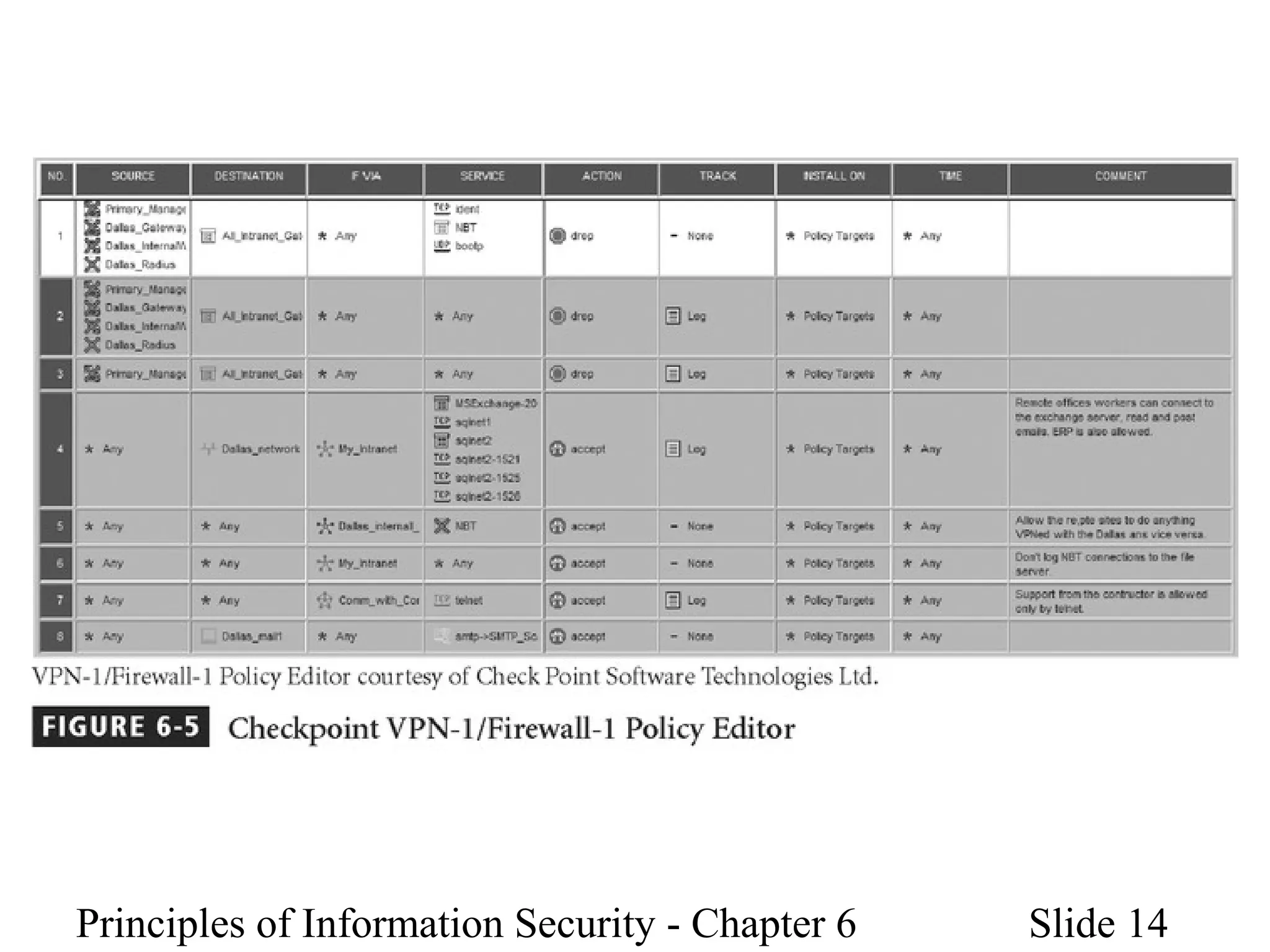
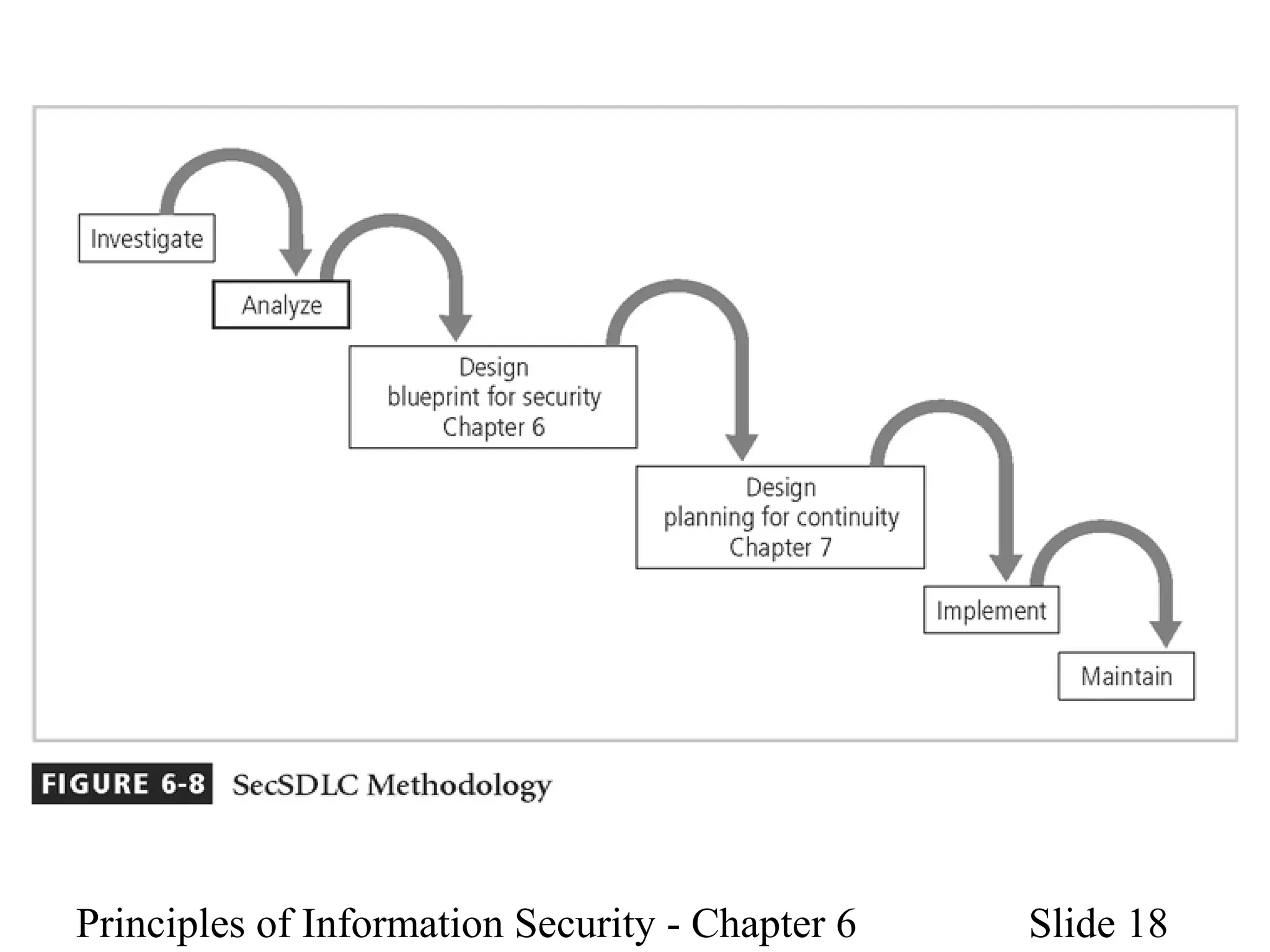
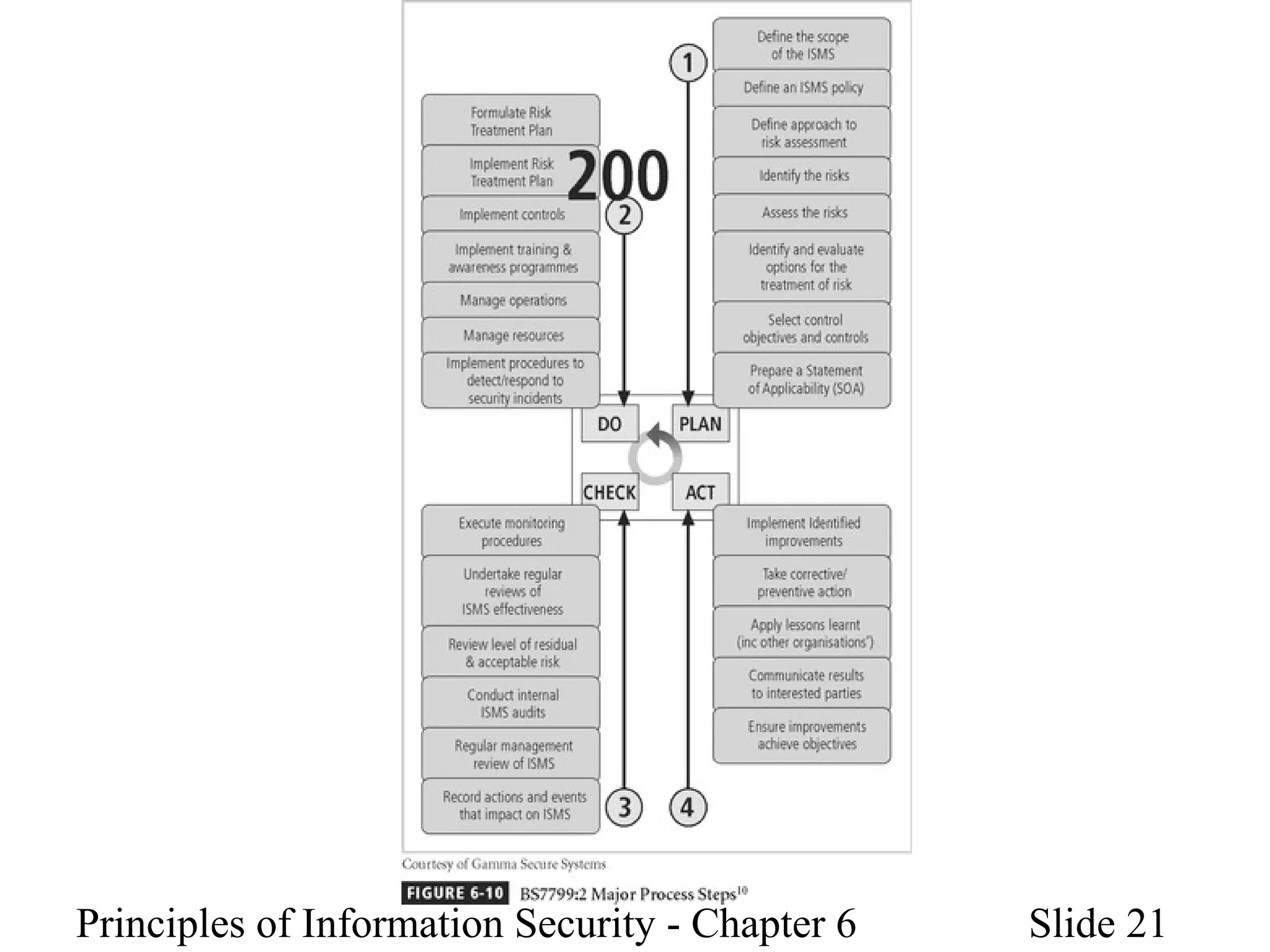
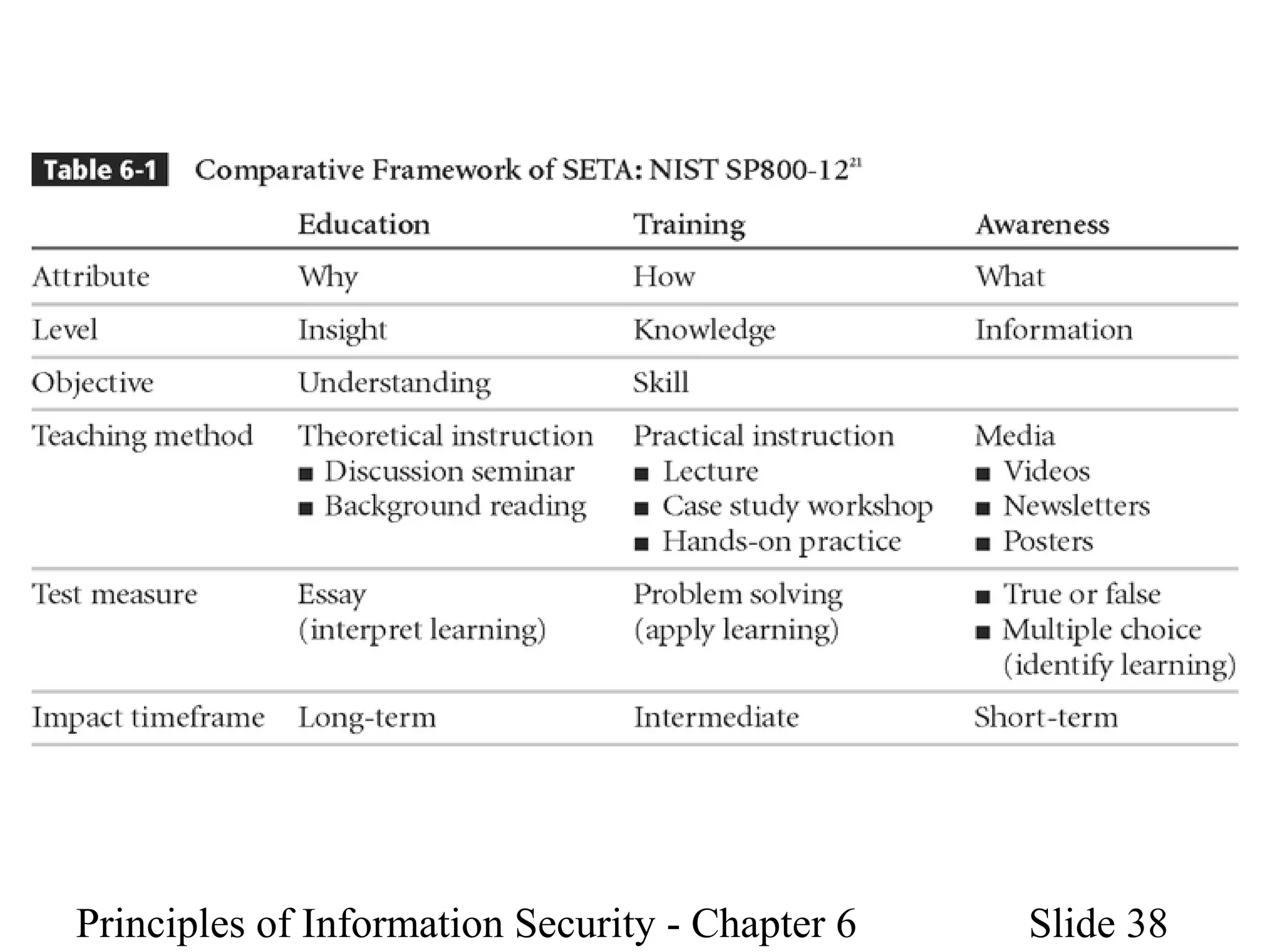
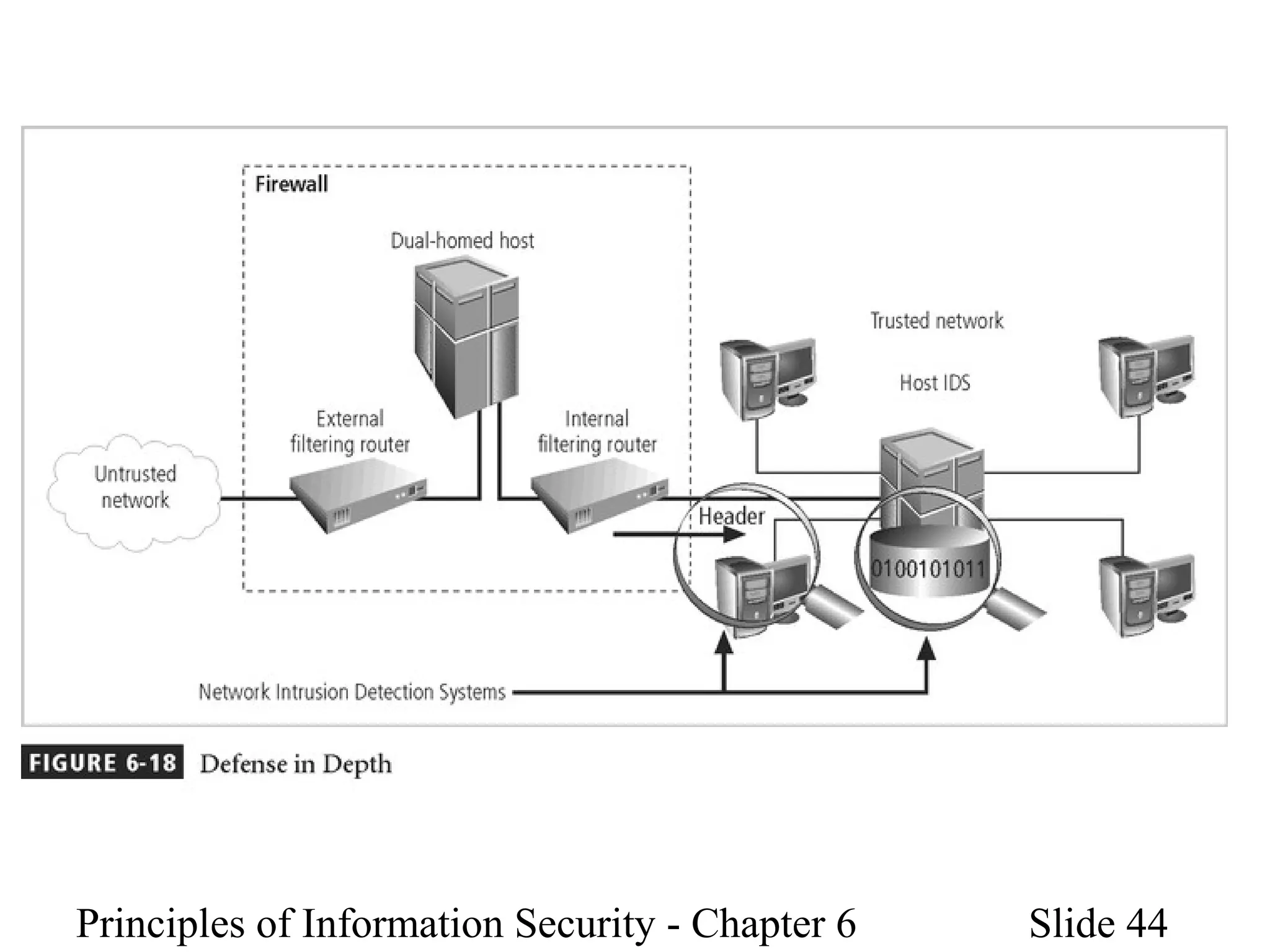
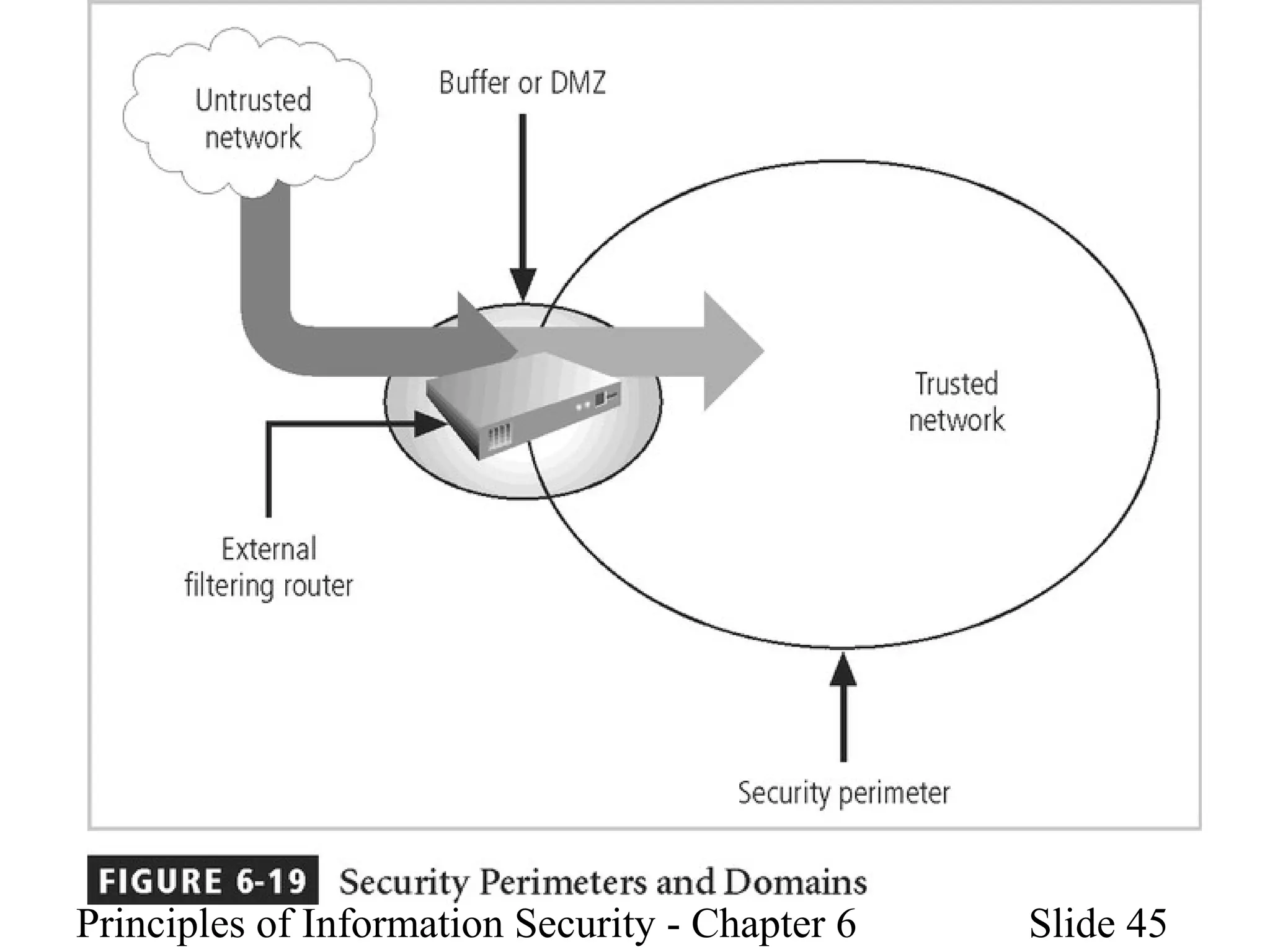
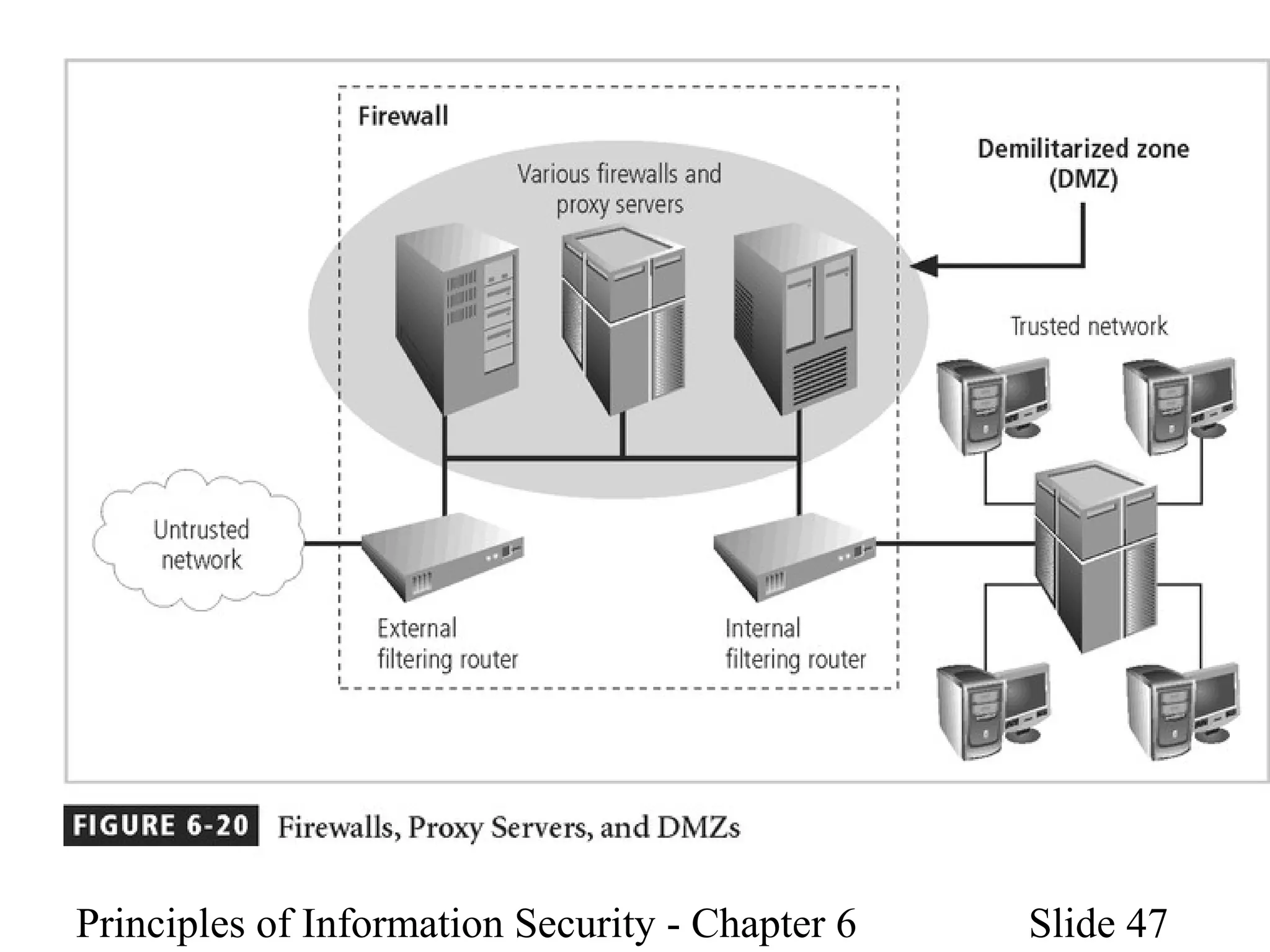
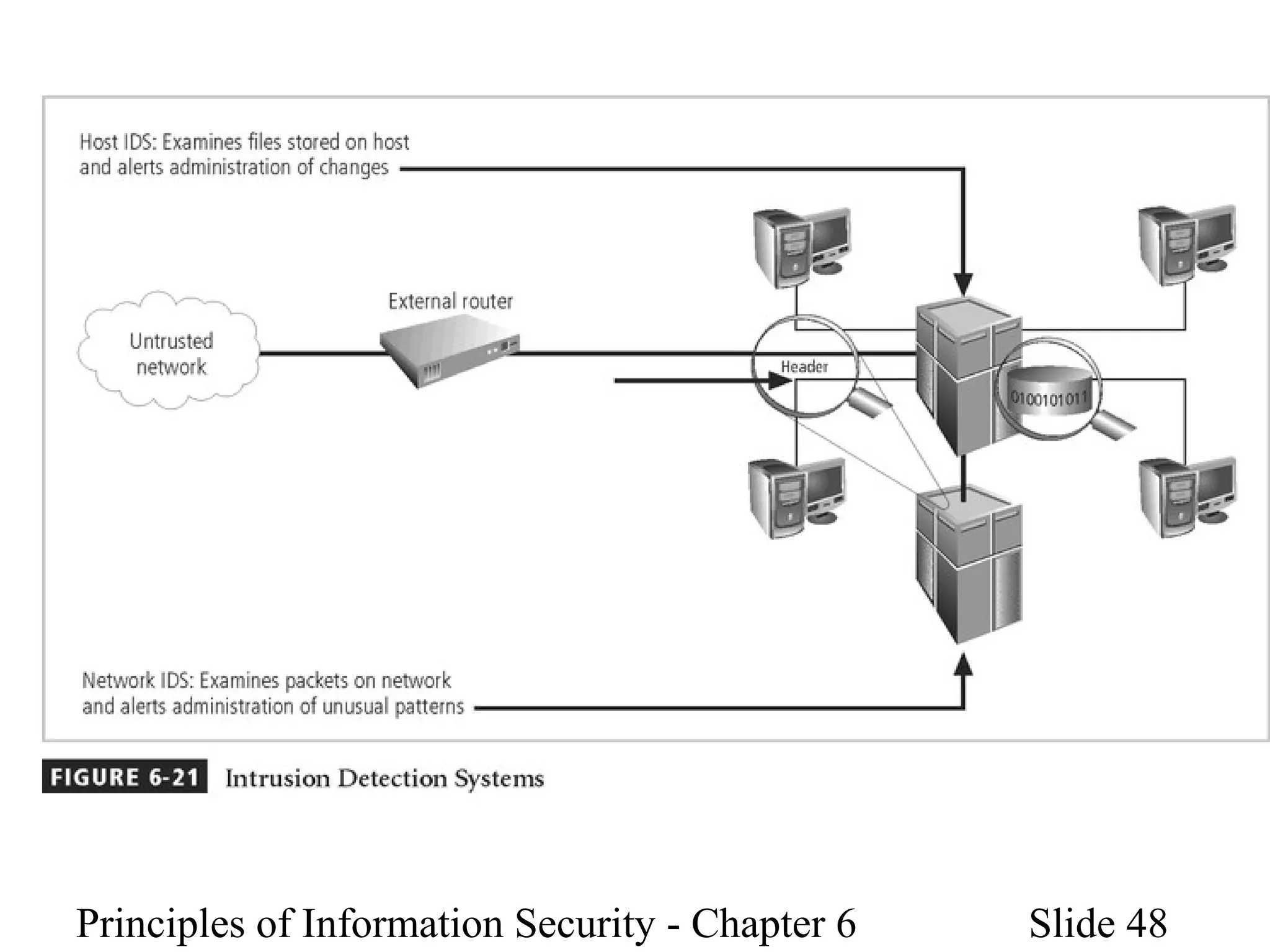
This document discusses information security policies, standards, and practices. It explains the different types of security policies an organization may have, including general security policies, issue-specific policies, and system-specific policies. It emphasizes the importance of management support for security policies and outlines the key components of an information security blueprint, including management controls, operational controls, and technical controls. The document also discusses the importance of security education, training, and awareness programs to ensure all employees understand and comply with security policies and procedures.