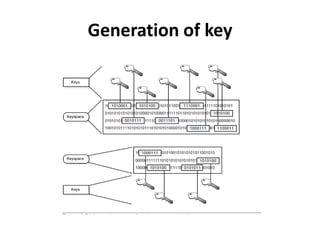
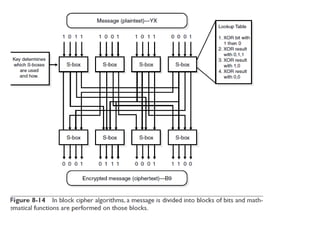
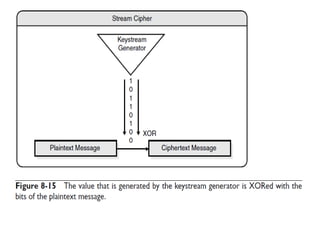
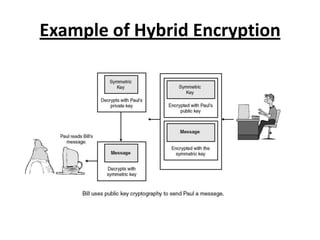
This document provides an overview of cryptography. It begins by defining cryptography as the science of encrypting and decrypting written communications. It then discusses the history of cryptography dating back to ancient Egypt and the Spartans. The document outlines some common cryptosystem services like confidentiality, integrity, and authentication. It also discusses key concepts like keyspace, symmetric and asymmetric encryption algorithms like AES and RSA, and hybrid encryption approaches. The presentation concludes by thanking the audience and offering to answer any questions.