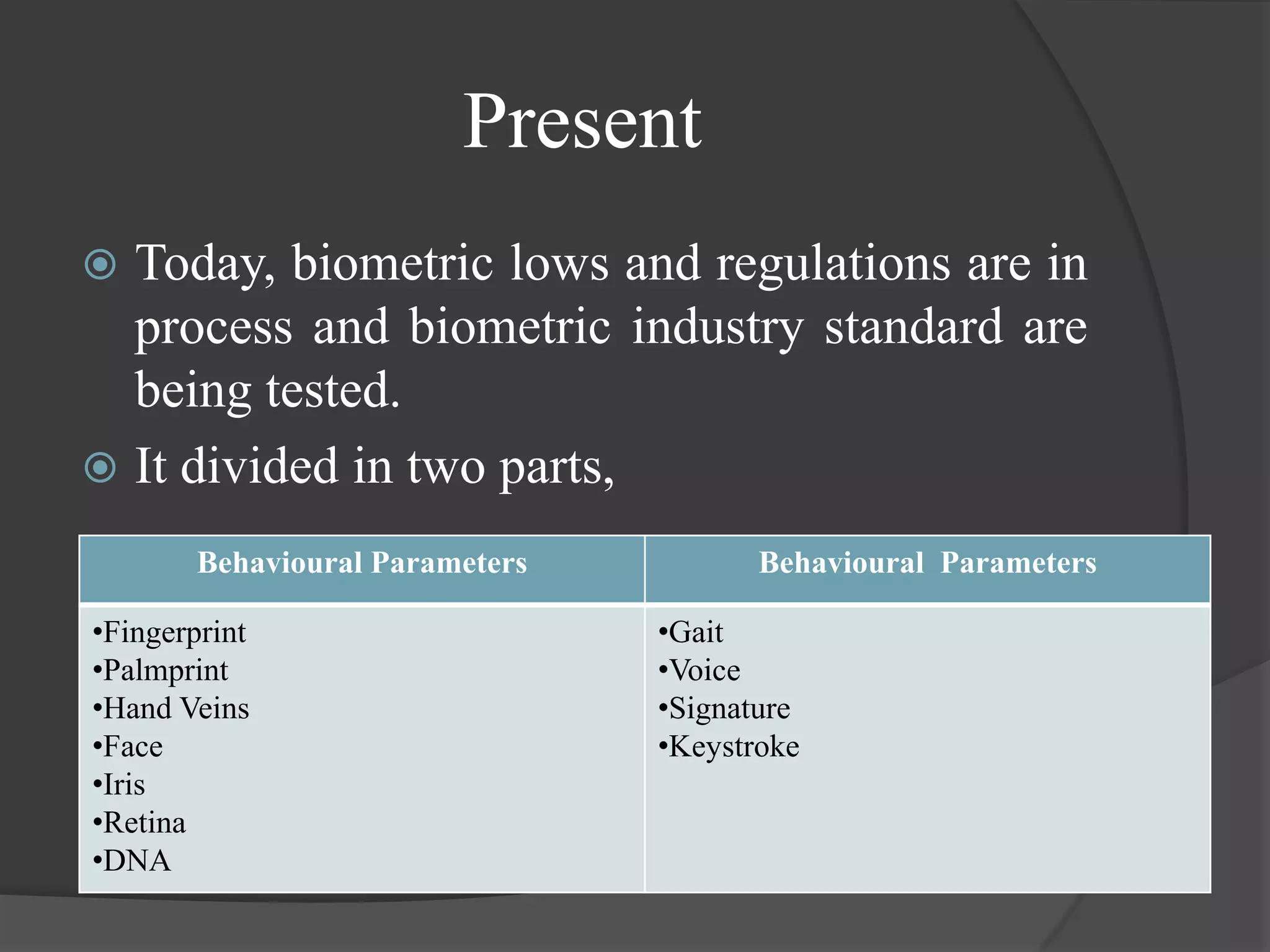
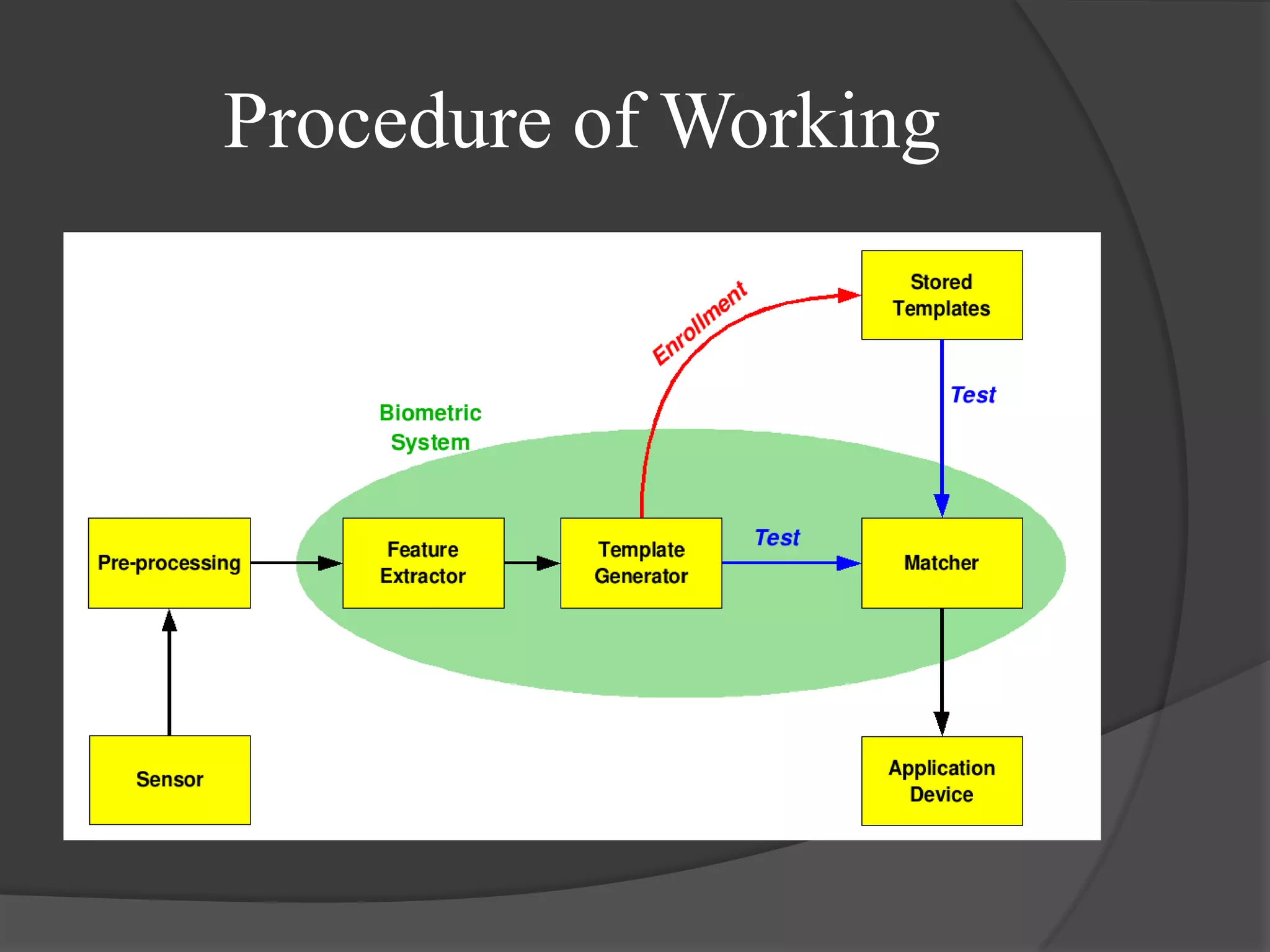
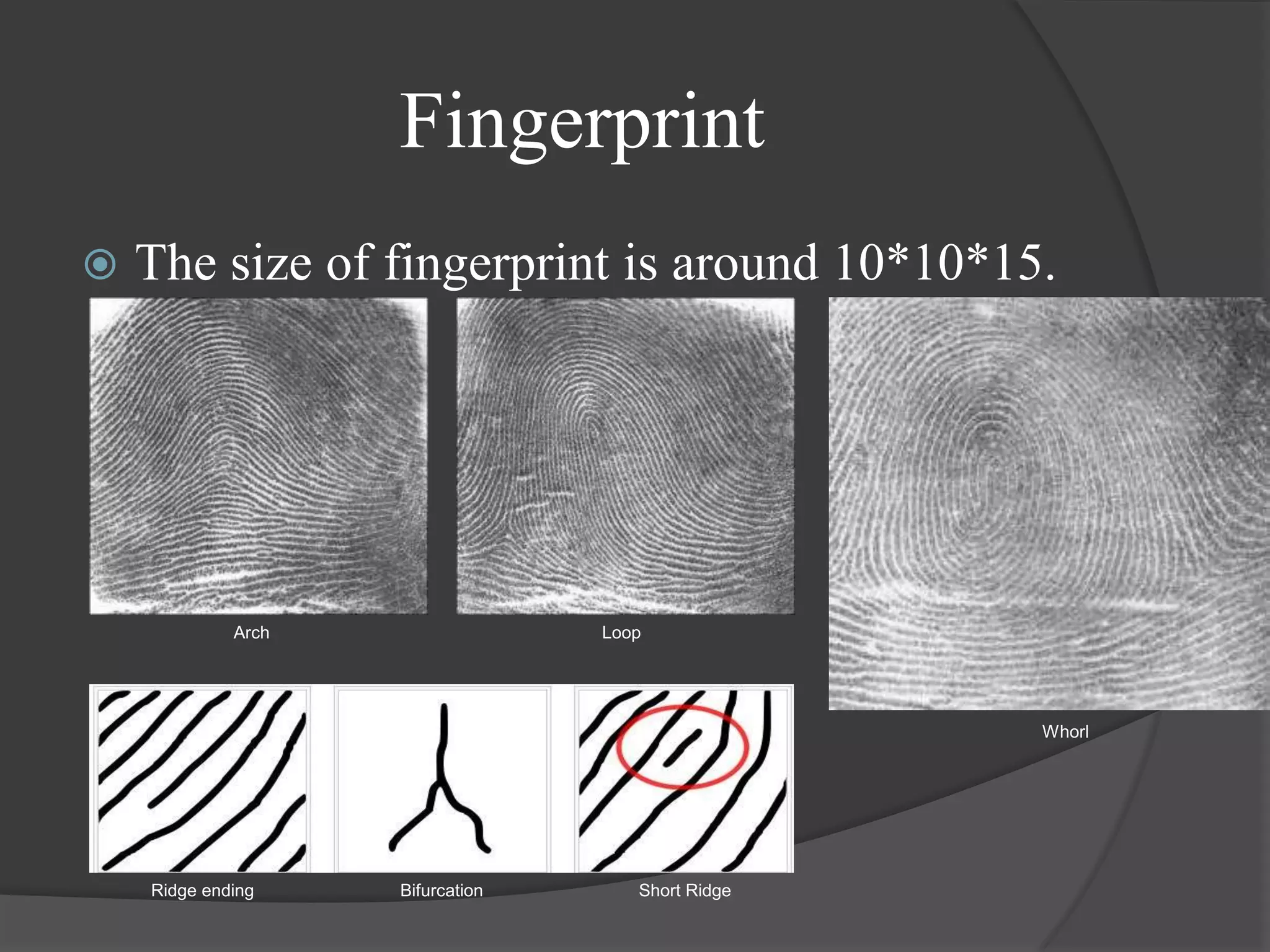
The document discusses the technology of the future. It covers several topics related to biometrics including a brief history, current applications, and the future potential of various biometric technologies such as fingerprints, iris recognition, and voice recognition. The document also discusses how biometric systems work and compares the features and accuracy of different biometric parameters.












![References
[1] Smart Cart Alliance Identity Council (2007): Identity and Smart Card Technology and Application
Glossary, http://www.smartcardalliances.org
[2] Langenburg, Glenn (January 24, 2005). "Are one's fingerprints similar to those of his or her parents in any discernable way?".
Scientific American. Retrieved 28 August 2010.
[3] Thornton, John (May 9, 2000). "Latent Fingerprints, Setting Standards In The Comparison and Identification". 84th Annual
Training Conference of the California State Division of IAI. Retrieved 30 August 2010.
[4] Wikipedia Image
http://en.wikipedia.org/wiki/File:Biometric_system_diagram.png
[5] Sanjay R. Ganorkar, Ashok A. Ghatol, “Iris Recognition: An Emerging Biometrics Technology”, In Proc. of The sixth WSEAS
International Conference on Single Processing, Robotics and Automation, Greece, Feb. 2007, pp. 91 – 96
[6] J. L. Wayman, A. K. Jain, D. Maltoni, and D. Maio, Eds, “Biometrics Systems: Technology, Design and Performance
Evolution”, New York: Spinger Verlag, 2005
[7] M. A. Dabbah, W. L. Woo, and S. S. Dlay, “Secure Authentication for Face Recognition”, In Proc. of IEEE Symposium on
computational Intelligence in Image and Signal Processing, April 2007, USA, pp. 121 – 126
[8] A. Kumar, D. C. Wong, H. C. Shen and A. K. Jain , “Personal Verification using Palmprinnt and Hand Geometry Biometrics”, In
Proc. of fourth International Conference on Audio and Video based Biometric Person Authentication, Guildford, U.K.
January 2003, pp 668-678
[9] S. Furui, “Recent Advances in Speaker Recognition”, In Proc. of first International Conference on Audio and video based
Biometric person Authentication, UK, March 1997, pp 859 – 872
[10] A.K. Jain, A. Ross, and S. Prabhakar, “An Introduction to Biometrics Recognition,” IEEE Trans. Circuit Syst. Video
Technology, Special Issue Image and Video based Biometrics, Volume 14, Issue 1st January 2004, pp. 4 – 20](https://image.slidesharecdn.com/biometricsppt-120827114744-phpapp01/75/Slide-show-on-Biometrics-19-2048.jpg)
