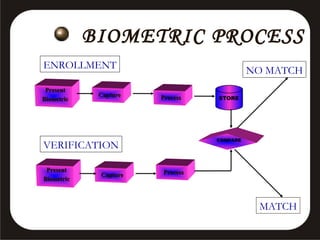
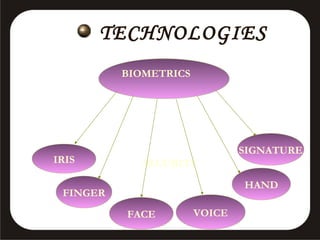
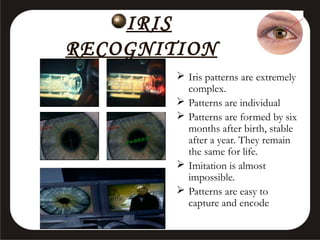
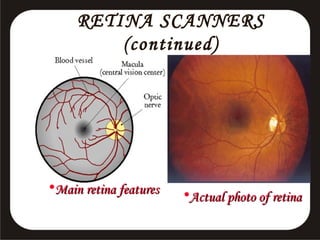
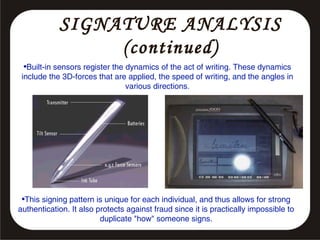
This document discusses various biometric security systems used for identification and verification. It describes physiological biometrics like fingerprint, iris, retina, and facial recognition that analyze unique physical characteristics. It also covers behavioral biometrics like signature, voice recognition, and hand geometry that analyze unique behavioral characteristics. For each biometric method, it explains how the technology works, its accuracy, advantages and limitations. It emphasizes that multimodal biometric systems integrating multiple technologies provide more secure authentication.