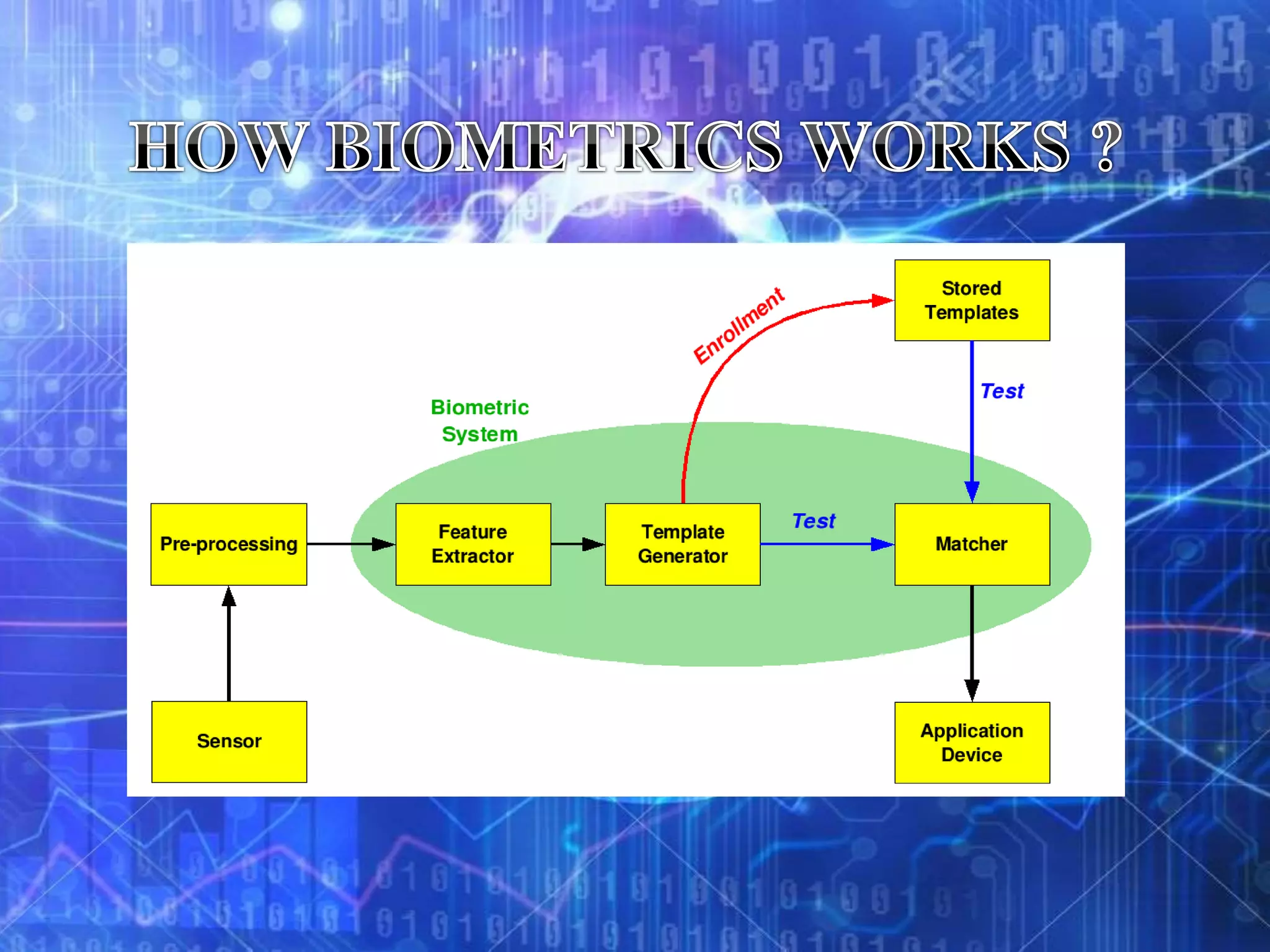
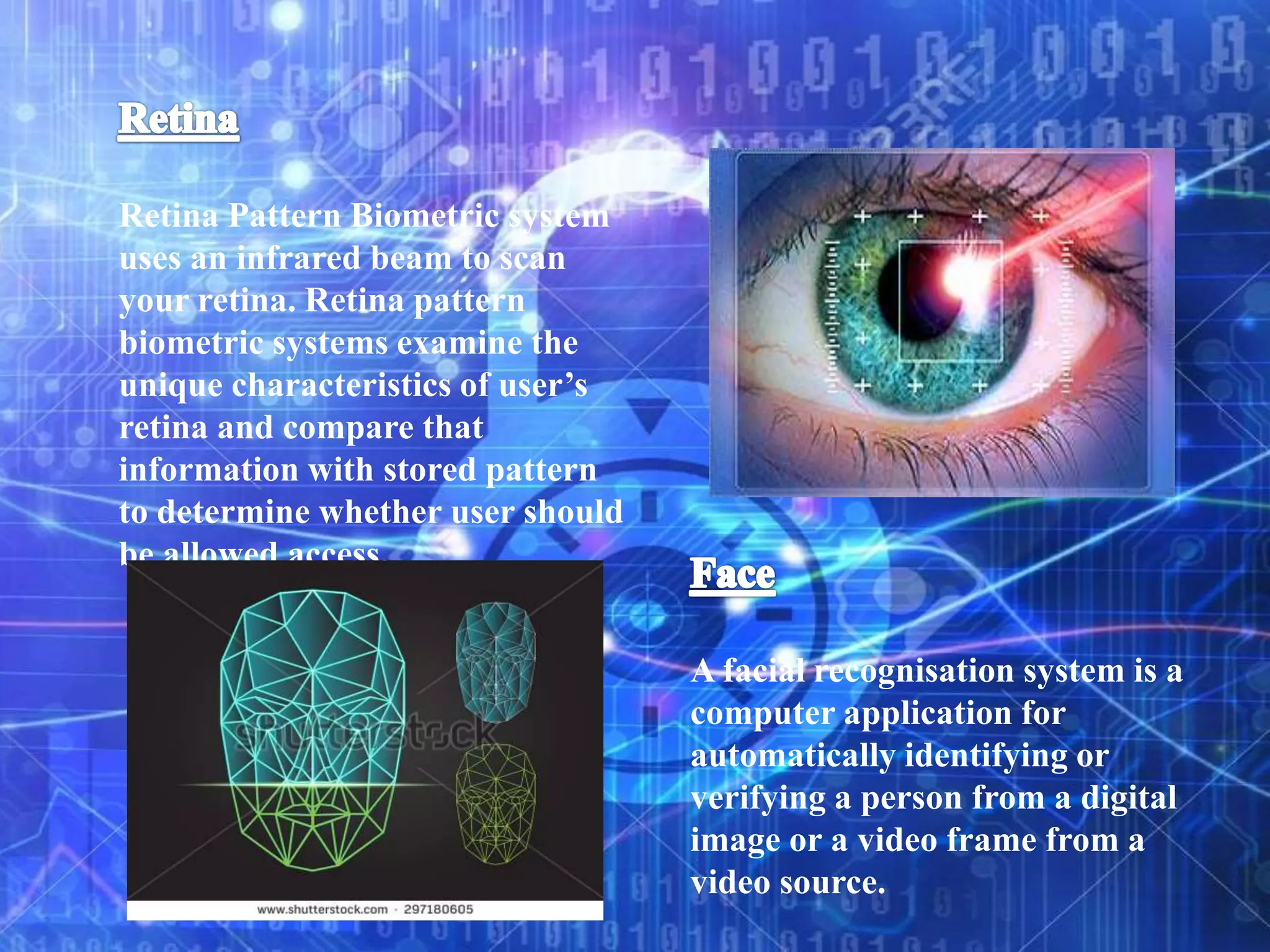
Biometrics refers to authentication techniques that rely on measurable physiological and individual characteristics to automatically verify identity. There are two main types of biometrics: physiological, which relate to the body shape like fingerprints, retina, and face; and behavioral, which relate to behaviors like voice, handwriting, and typing patterns. Biometric systems use verification to compare a sample to a single stored template or identification to search a sample against a database of templates to resolve a person's identity. While biometrics can provide strong authentication for applications like secure banking, border control, and access control, they are not perfect and have limitations like cost, accuracy, and privacy concerns.