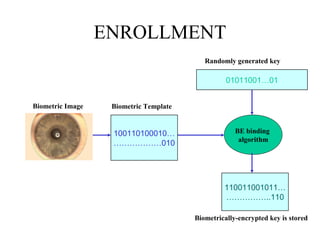
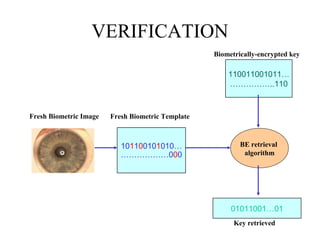
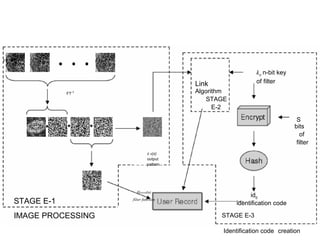
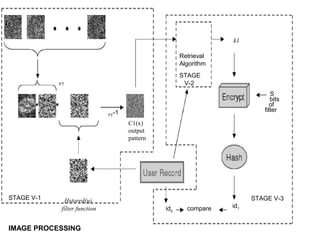
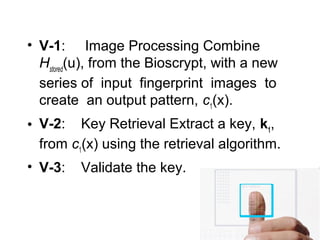
Biometric encryption is a technique that securely binds a cryptographic key to a biometric template. During enrollment, a random key is linked to a user's biometric template using a binding algorithm. During verification, applying the same biometric will regenerate the key through a retrieval algorithm. This allows authentication while preventing storage of the actual biometric data. Biometric encryption offers advantages like improved security, ability to revoke compromised keys, and privacy by not retaining biometric images.