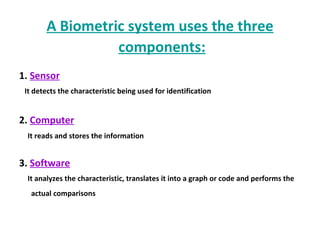
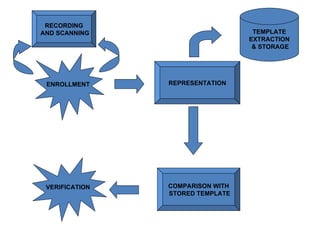
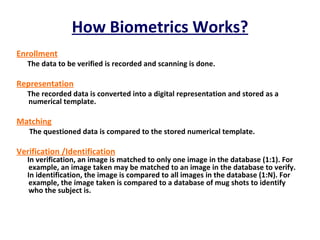
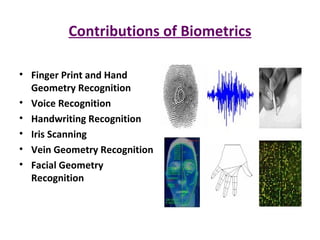
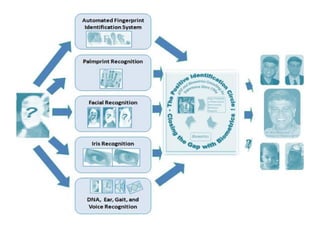
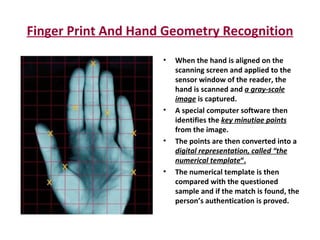
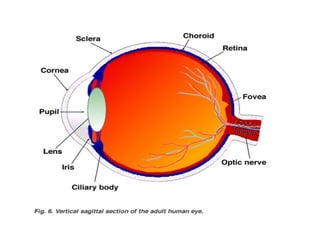
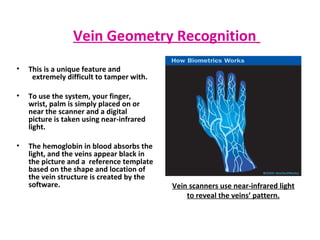
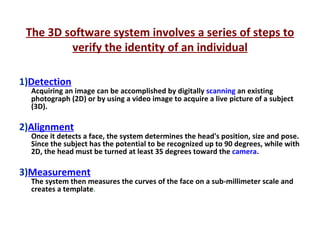
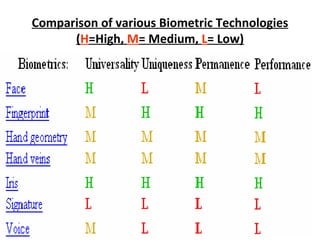
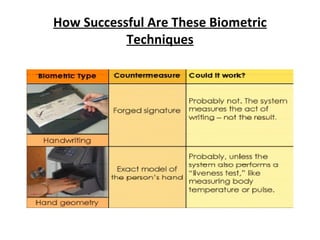
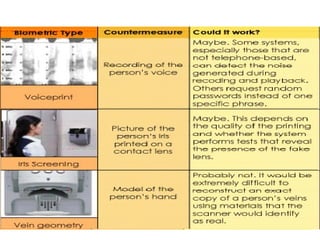
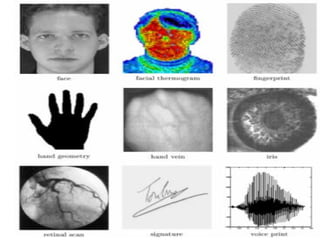
The document discusses biometrics, a technology for identifying individuals based on unique physical or behavioral traits, addressing its working mechanism, benefits, and various applications across fields such as security. It provides a comparative analysis of different biometric techniques like fingerprint recognition, iris scanning, and facial recognition, highlighting their success rates and future prospects. The document emphasizes the reliability and security advantages of biometrics over traditional authentication methods but also notes some challenges and limitations in certain recognition systems.