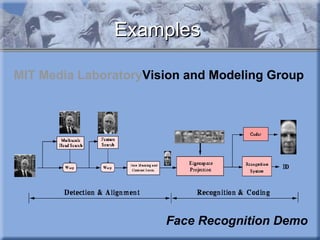
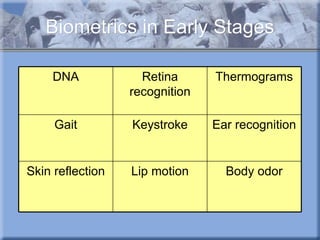
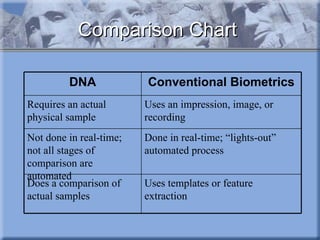
The document discusses various types of biometric technologies, including physiological and behavioral biometrics. It provides examples of common biometrics like fingerprint recognition and face recognition. It then describes several emerging or less common biometric technologies in more detail, such as DNA recognition, retina recognition, thermograms, gait analysis, keystroke recognition, ear recognition, skin reflection analysis, and lip motion analysis. The document also briefly discusses future challenges and possibilities for using biometrics.