This document provides an overview of biometric authentication techniques. It discusses what biometric authentication is, the different types of biometric techniques including fingerprint, face, iris, hand geometry, and voice recognition. It covers how biometric systems work, performance metrics, applications, limitations, and concludes that biometric authentication provides strong security for applications like e-commerce and e-government by utilizing unique physical and behavioral human traits.




![Biometric Technique
Classification
[3]](https://image.slidesharecdn.com/astudyonbiometricauthenticationtechniques-131105123214-phpapp01/85/A-study-on-biometric-authentication-techniques-9-320.jpg)
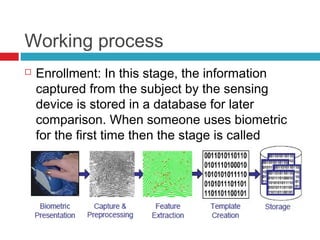
![Working of biometric system
Steps:
Capturing
Pre-processing
Feature extraction
Template matching
Matcher/Comparison
Application Device
[3]](https://image.slidesharecdn.com/astudyonbiometricauthenticationtechniques-131105123214-phpapp01/85/A-study-on-biometric-authentication-techniques-11-320.jpg)

![Different biometric technique
Fingerprint technology:
It is the oldest and most widely used method.
It needs a fingerprint reader.
Registered points are located and compared.
Optical sensors are used for scanning purpose.
It can be used for many applications like pc
login security, voting system,
attendance system etc.
[12]](https://image.slidesharecdn.com/astudyonbiometricauthenticationtechniques-131105123214-phpapp01/85/A-study-on-biometric-authentication-techniques-15-320.jpg)

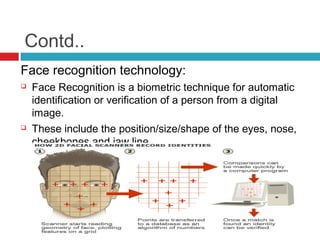

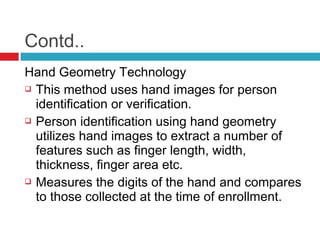
![Contd..
Places hand on the system, which takes the
three dimensional image of the hand.
[6]](https://image.slidesharecdn.com/astudyonbiometricauthenticationtechniques-131105123214-phpapp01/85/A-study-on-biometric-authentication-techniques-20-320.jpg)


![Comparison Between Different
Technique
[3]](https://image.slidesharecdn.com/astudyonbiometricauthenticationtechniques-131105123214-phpapp01/85/A-study-on-biometric-authentication-techniques-23-320.jpg)
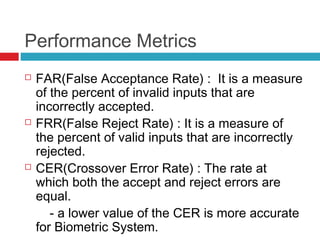
![Performance Metrics Curve
[4]](https://image.slidesharecdn.com/astudyonbiometricauthenticationtechniques-131105123214-phpapp01/85/A-study-on-biometric-authentication-techniques-25-320.jpg)