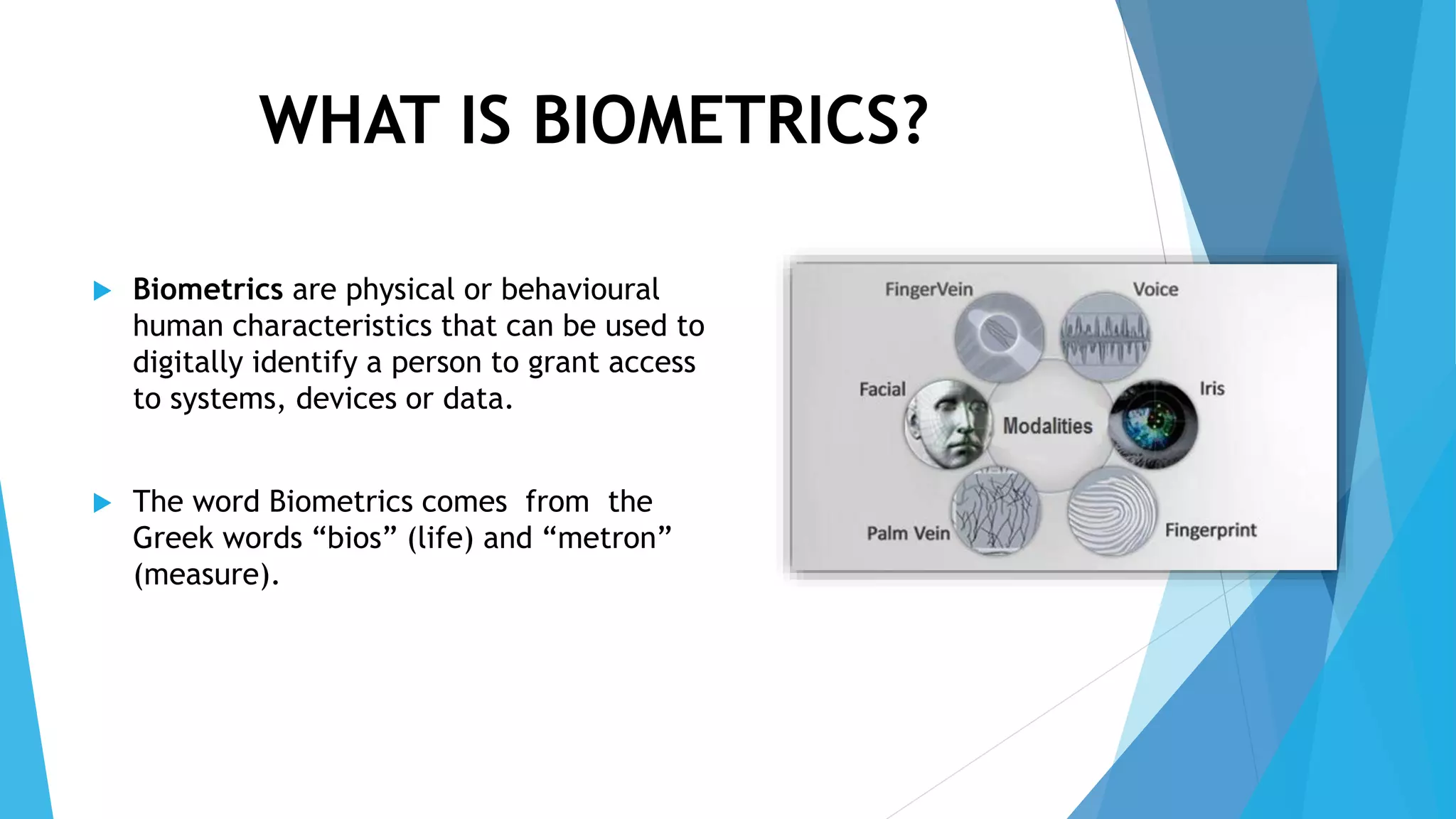
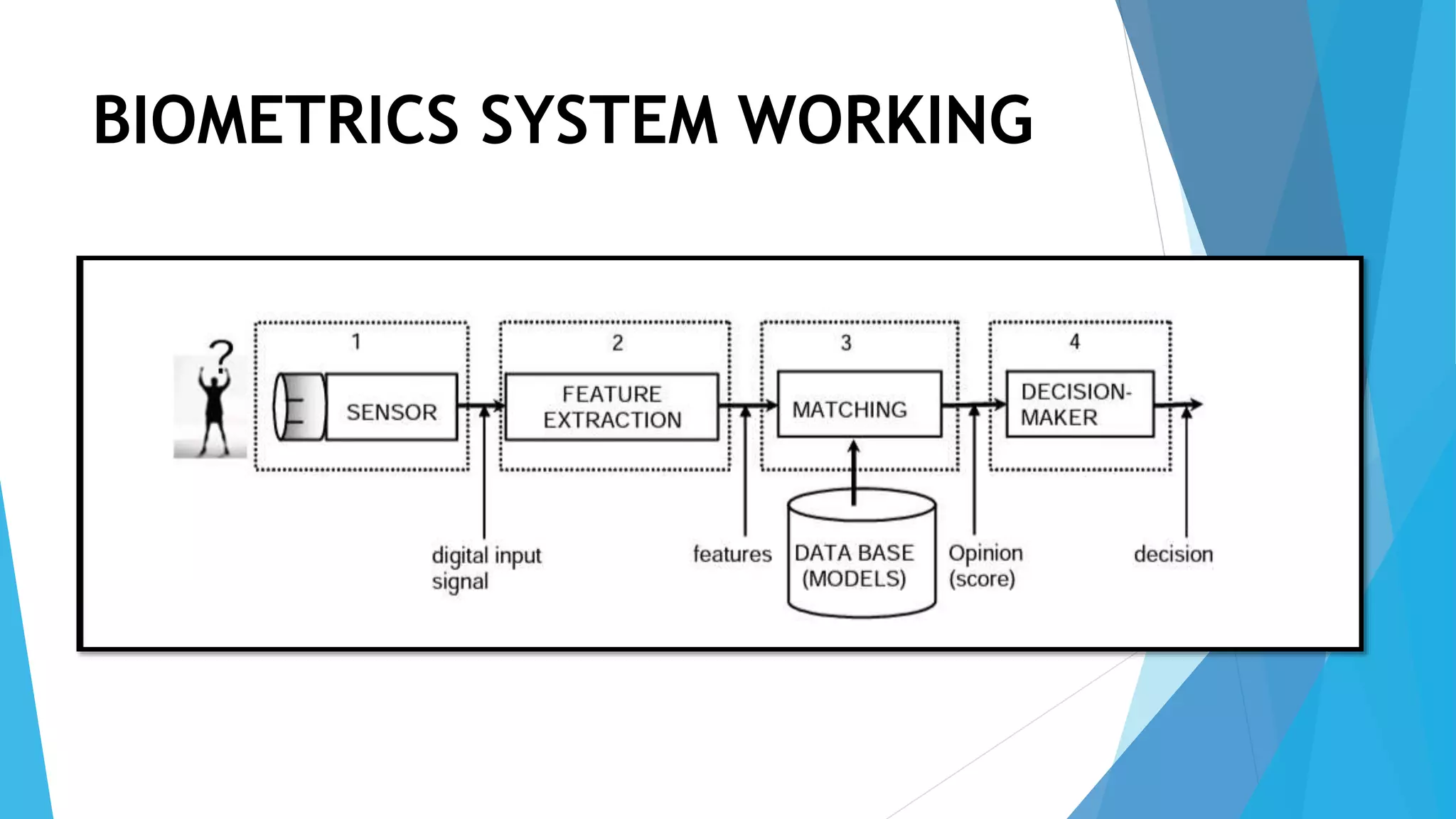
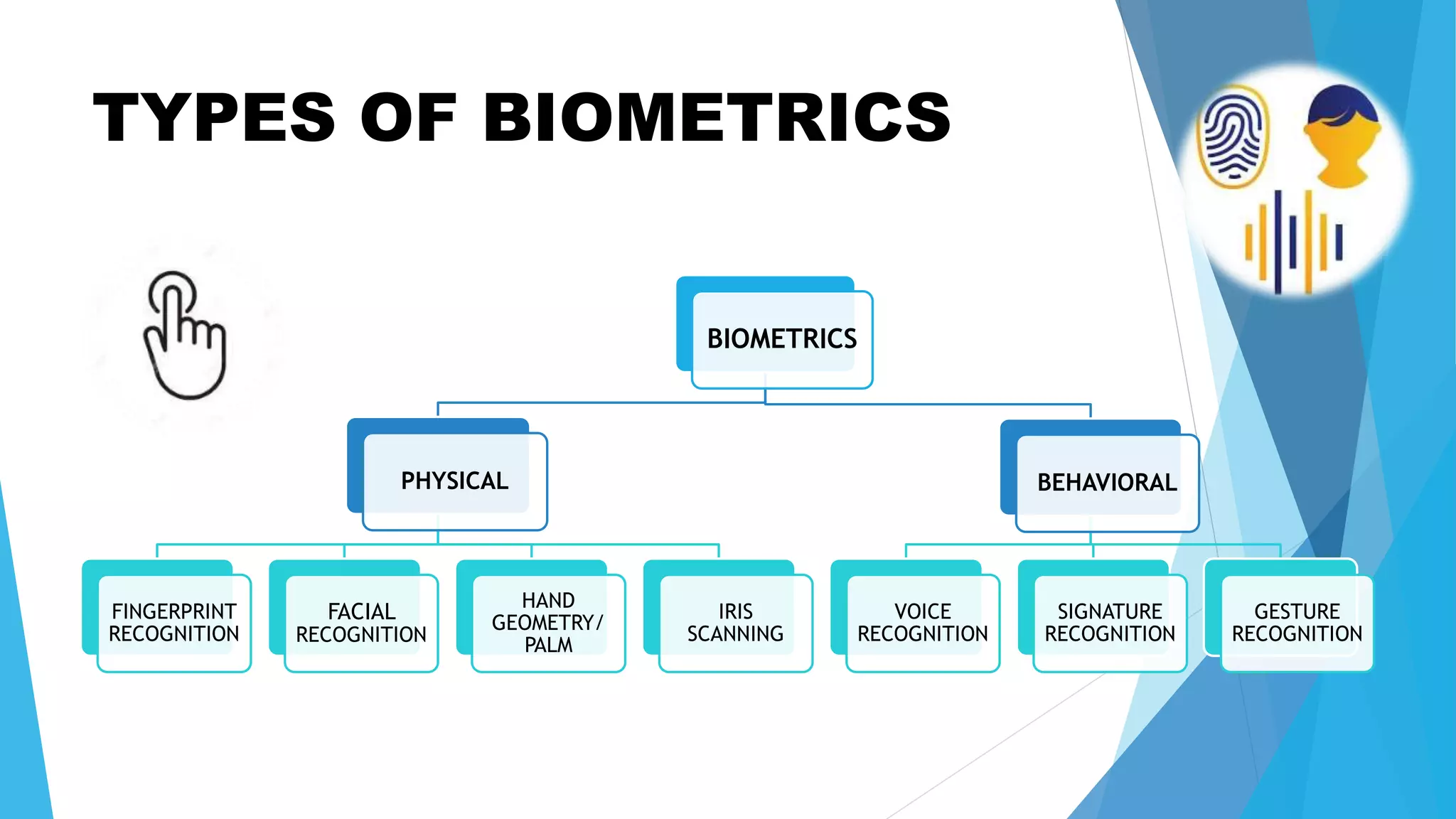
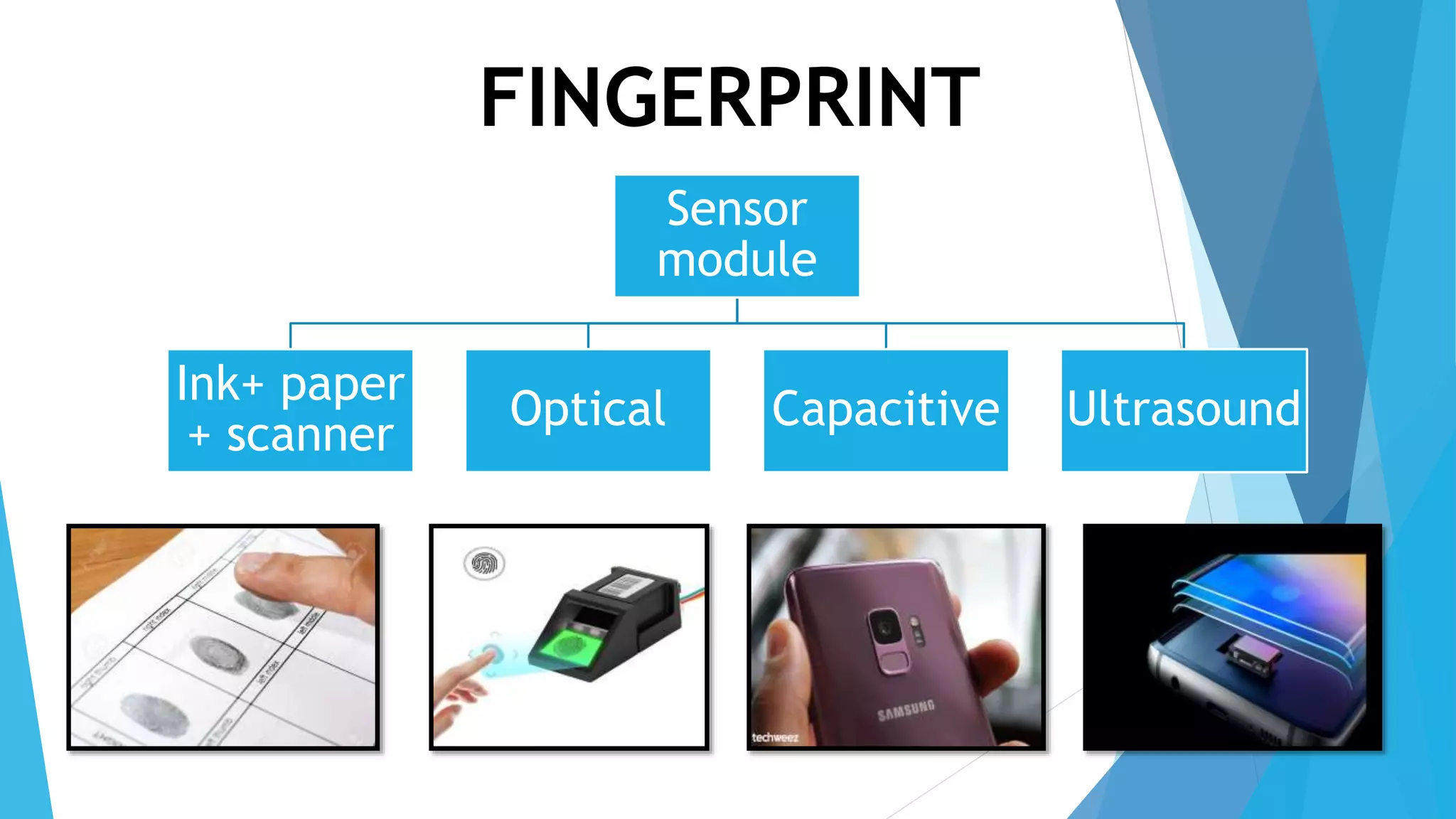
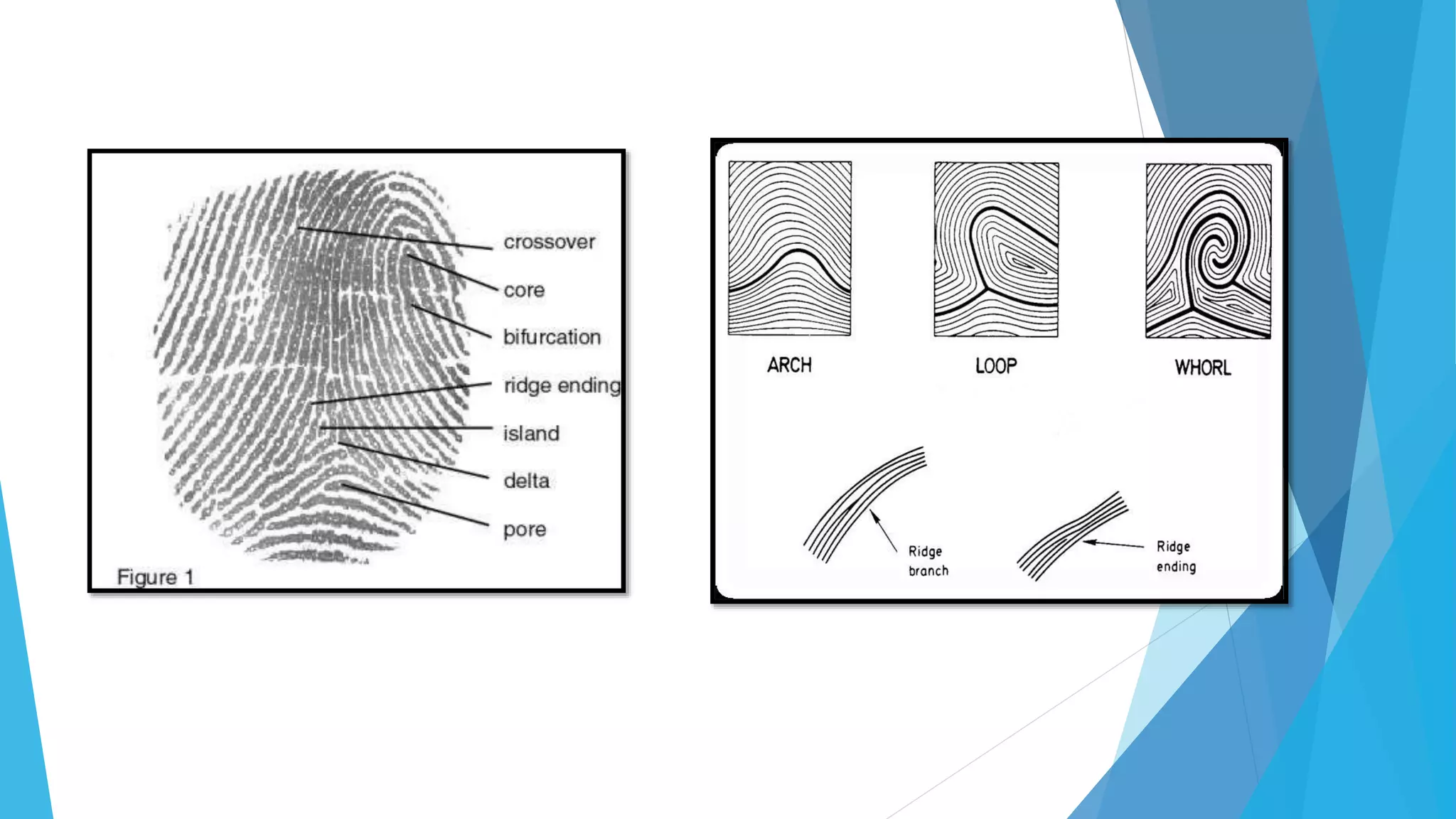
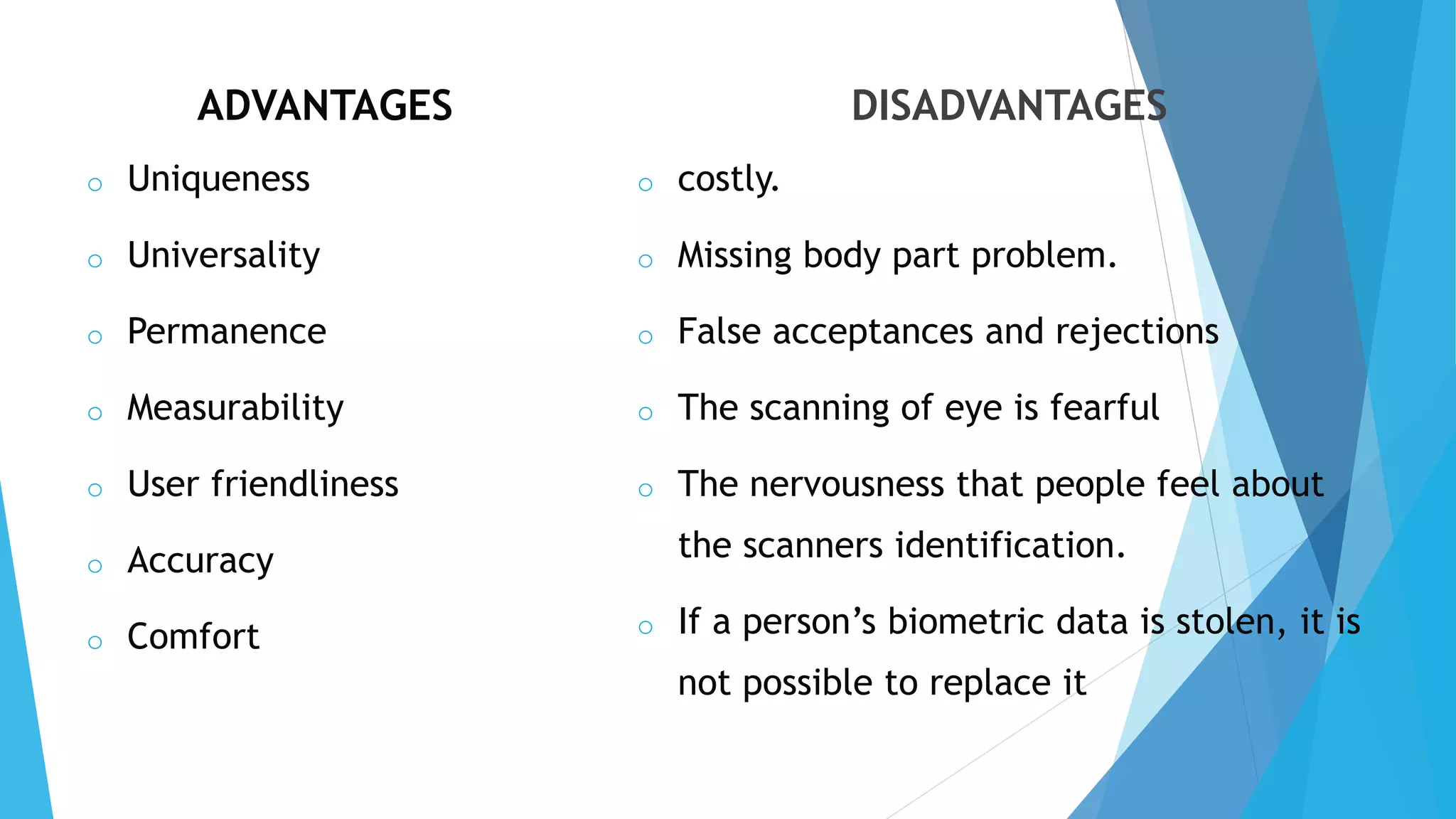
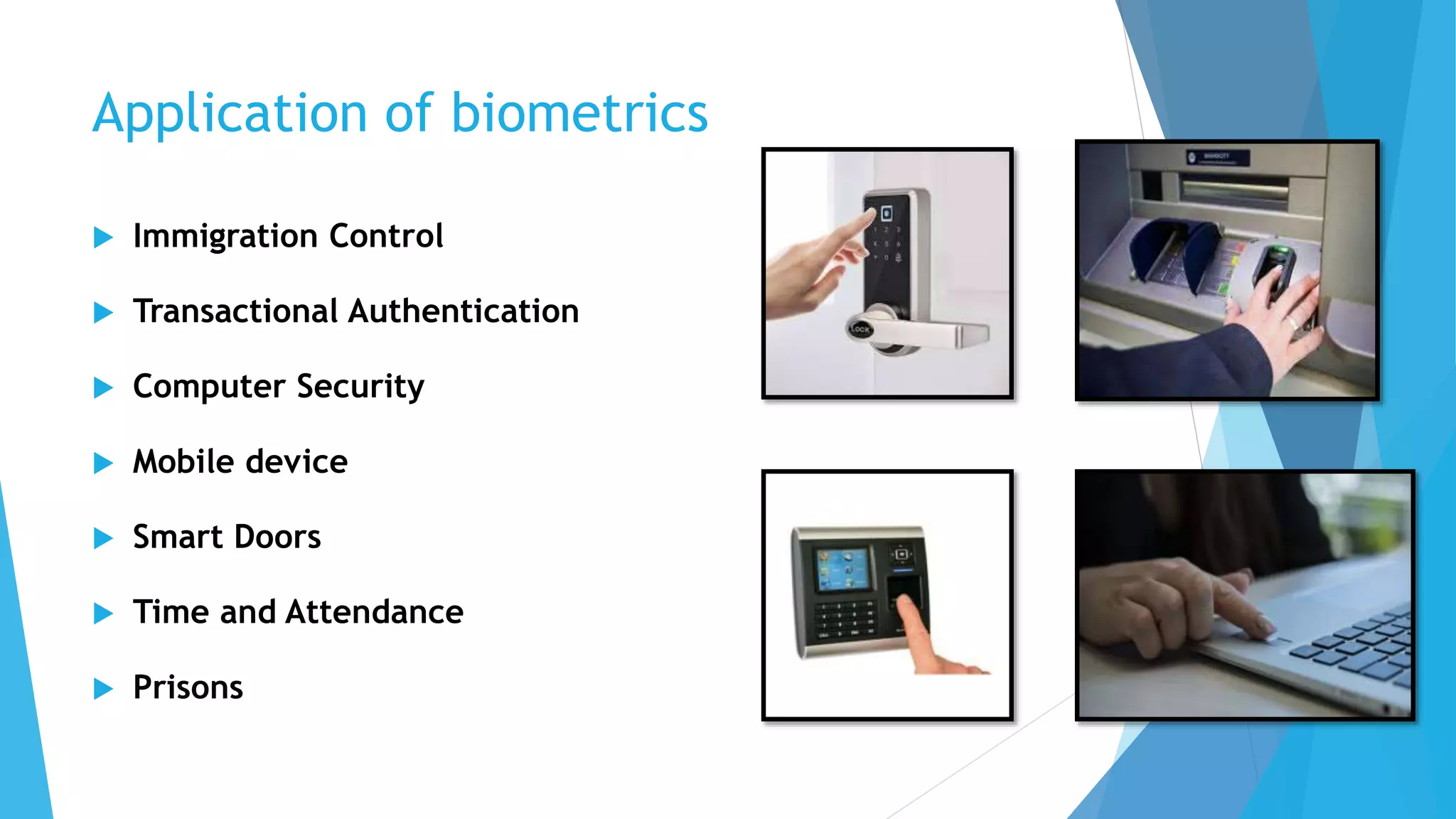
Ketan Bhagawat Sawakare will be giving a seminar presentation on biometrics technology. The presentation will include an introduction to biometrics, a history of biometrics, different types of biometrics such as fingerprint recognition and facial recognition, how biometrics systems work, advantages and disadvantages of biometrics, and applications and future scope of biometrics technology. The presentation will conclude with references used in preparing the seminar.