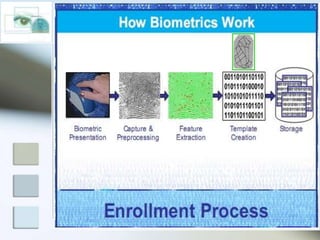
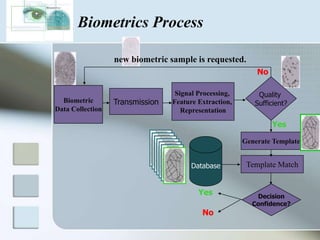
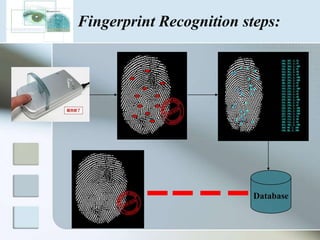
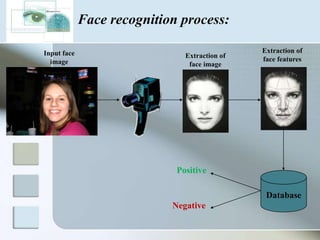
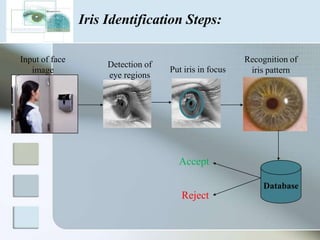
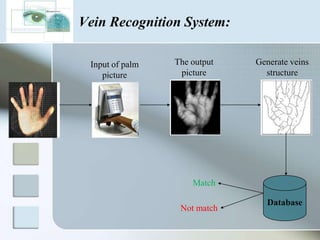
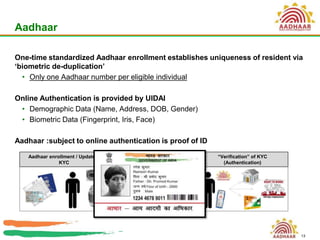
The document discusses biometrics as a method of authentication, highlighting three main types: knowledge-based, possession-based, and inherent characteristics. It details various biometric identifiers, such as fingerprints and facial recognition, elaborates on the Aadhaar system for identity verification in India, and outlines the advantages and disadvantages of biometrics. The conclusion states that while not yet perfect, biometrics are evolving and becoming more secure and convenient.