This document provides an overview of various application layer protocols including HTTP, HTTPS, SMTP, POP3, FTP, SFTP, SCP, Telnet, and SSH. It describes each protocol, including what they are used for and how they differ. Some key points:
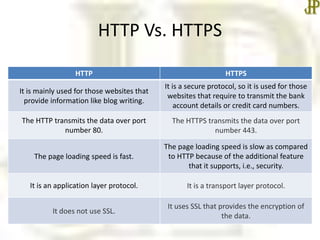
- HTTP and HTTPS are used to access data on the world wide web, with HTTPS providing encryption for secure transactions.
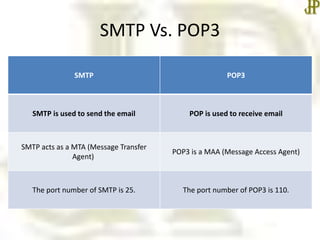
- SMTP and POP3 are used for email, with SMTP sending messages between servers and POP3 allowing users to receive messages from their inbox.
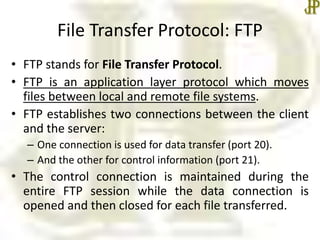
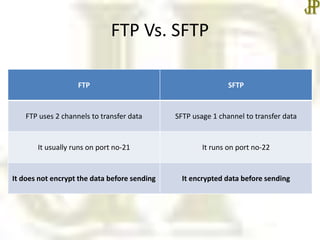
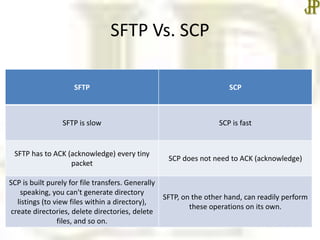
- FTP and SFTP are used for file transfer, with SFTP encrypting data for security unlike regular FTP. SCP also provides secure file transfer.
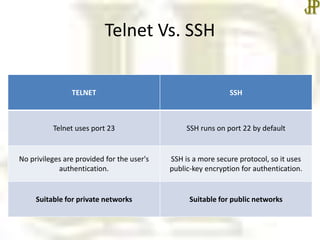
- Tel