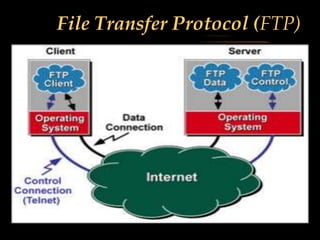
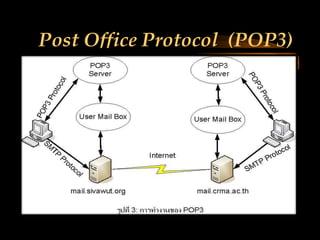
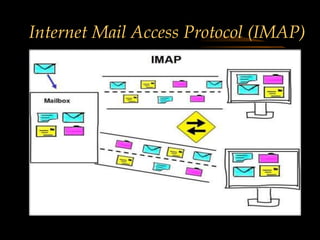
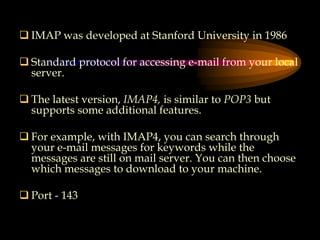
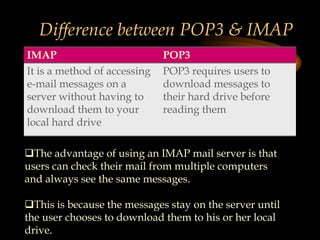
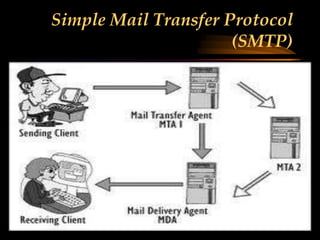
The document discusses several internet protocols including IP, HTTP, HTTPS, FTP, POP3, IMAP, SMTP, and MIME. IP defines how data is sent between computers on the internet using packets. HTTP and HTTPS govern how data is exchanged over the world wide web, with HTTPS providing encryption. FTP, POP3, IMAP, and SMTP define standards for file transfer and email transmission, storage, and access between servers and clients. MIME extended email to allow transmission of non-text files.