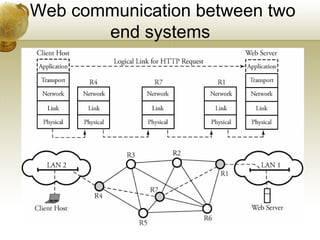
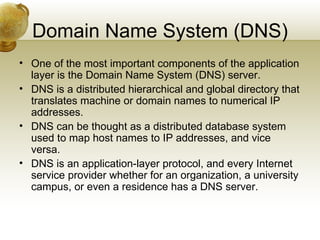
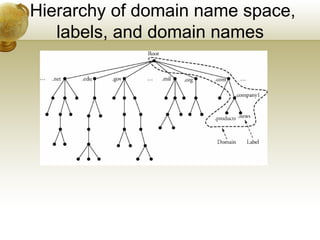
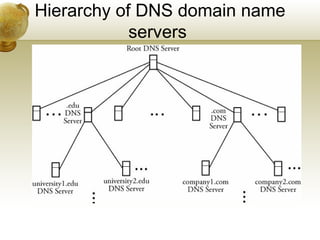
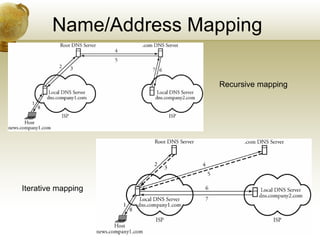
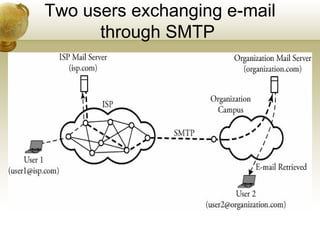
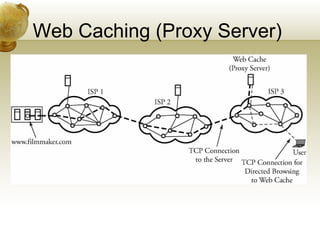
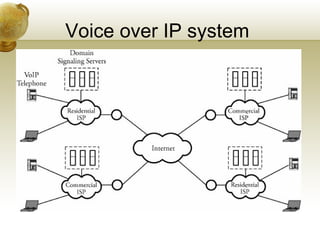
The document summarizes several key application layer protocols in computer networks. It discusses the Domain Name System (DNS) which maps domain names to IP addresses. It also describes remote login protocols like Telnet and SSH, electronic mail protocols like SMTP, file transfer protocols like FTP and SCP, and the Hypertext Transfer Protocol (HTTP) which underlies the World Wide Web. It provides an overview of Voice over IP (VoIP) technology and signaling protocols used for call setup and management in IP telephony systems.