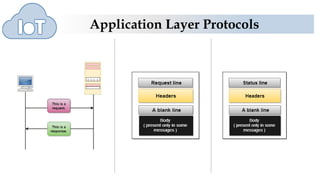
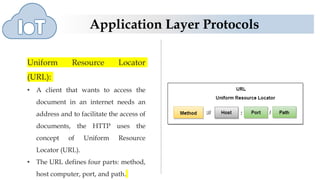
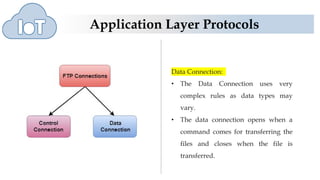
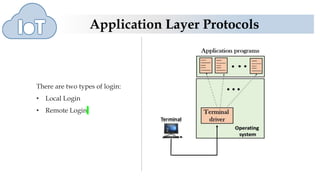
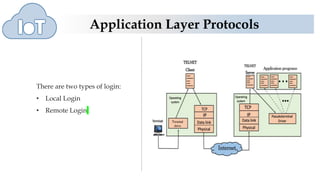
The document discusses several application layer protocols used in TCP/IP including HTTP, HTTPS, FTP, and Telnet. HTTP is used to access resources on the world wide web over port 80 and is stateless. HTTPS is a secure version of HTTP that encrypts communications over port 443. FTP is used to transfer files between hosts but sends data and passwords in clear text. Telnet allows users to access programs on remote computers.