Internet protocols and smart devices for better living.pptx
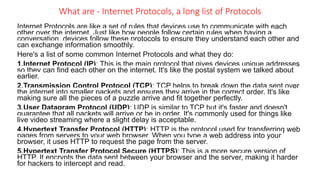
- 1. What are - Internet Protocols, a long list of Protocols Internet Protocols are like a set of rules that devices use to communicate with each other over the internet. Just like how people follow certain rules when having a conversation, devices follow these protocols to ensure they understand each other and can exchange information smoothly. Here's a list of some common Internet Protocols and what they do: 1.Internet Protocol (IP): This is the main protocol that gives devices unique addresses so they can find each other on the internet. It's like the postal system we talked about earlier. 2.Transmission Control Protocol (TCP): TCP helps to break down the data sent over the internet into smaller packets and ensures they arrive in the correct order. It's like making sure all the pieces of a puzzle arrive and fit together perfectly. 3.User Datagram Protocol (UDP): UDP is similar to TCP but it's faster and doesn't guarantee that all packets will arrive or be in order. It's commonly used for things like live video streaming where a slight delay is acceptable. 4.Hypertext Transfer Protocol (HTTP): HTTP is the protocol used for transferring web pages from servers to your web browser. When you type a web address into your browser, it uses HTTP to request the page from the server. 5.Hypertext Transfer Protocol Secure (HTTPS): This is a more secure version of HTTP. It encrypts the data sent between your browser and the server, making it harder for hackers to intercept and read.
- 2. Internet Protocols, a long list of Protocols 6. File Transfer Protocol (FTP): FTP is used for transferring files between computers on a network. It's commonly used by web developers to upload files to a website's server. 7. Simple Mail Transfer Protocol (SMTP): SMTP is used for sending email messages between servers. When you hit "send" on an email, your email client uses SMTP to send the message to the recipient's email server. 8. Post Office Protocol (POP): POP is used by email clients to retrieve messages from an email server. It allows you to download your emails onto your device so you can read them offline. 9. Internet Message Access Protocol (IMAP): Similar to POP, IMAP is used by email clients to access messages on an email server. However, unlike POP, it allows you to keep your messages stored on the server so you can access them from multiple devices. These are just a few examples of the many Internet Protocols that make the internet work! Each one plays a specific role in ensuring that data is transmitted efficiently and securely across the vast network of the internet.
- 3. What are - Internet Protocols, a long list of Protocols 10.Domain Name System (DNS): DNS translates human-readable domain names (like google.com) into IP addresses that computers can understand. It's like a phonebook for the internet, helping your browser find the correct web server when you enter a website address. 11.Dynamic Host Configuration Protocol (DHCP): DHCP automatically assigns IP addresses to devices on a network when they connect. It's like a host at a party handing out name tags to guests as they arrive, ensuring everyone gets a unique identifier without conflicts. 12.Internet Control Message Protocol (ICMP): ICMP is used for diagnostics and error reporting in network communication. It helps devices communicate status and troubleshoot issues, like when a server is unreachable. 13.Border Gateway Protocol (BGP): BGP is used by internet routers to exchange routing information and make decisions on how to forward data between autonomous systems (like internet service providers). It's like a network of road signs directing traffic on the internet's highways. 14.Simple Network Management Protocol (SNMP): SNMP allows network administrators to monitor and manage network devices remotely. It provides a standardized way to collect information about devices and detect and resolve issues. 15.Internet Protocol Security (IPsec): IPsec provides security features for IP packets, such as encryption and authentication, to protect data as it travels over the internet. It's like putting your data in a secure envelope with a lock and key before sending it out.
- 4. What are - Internet Protocols, a long list of Protocols 16. File Transfer Protocol Secure (FTPS): FTPS is a secure version of FTP that adds encryption to protect file transfers from eavesdropping and unauthorized access. 17. Secure Shell (SSH): SSH provides secure remote access to computers and servers over an unsecured network. It encrypts the communication between the client and server, preventing eavesdropping and tampering. 18. Simple Object Access Protocol (SOAP): SOAP is a protocol for exchanging structured information in web services. It defines how messages are formatted and transmitted between applications over the internet. 19. WebSocket: WebSocket is a communication protocol that provides full- duplex communication channels over a single TCP connection. It's commonly used for real-time web applications, like chat and gaming, where low latency and high throughput are crucial. These protocols, among many others, work together to make the internet a functional and reliable global network, enabling communication, data exchange, and collaboration on an unprecedented scale.
- 5. Further into some additional Internet Protocols:, a long list of Protocols 20.Simple Network Time Protocol (SNTP): SNTP is used to synchronize the clocks of devices on a network to a coordinated universal time reference. It ensures that all devices have accurate timestamps for events, which is crucial for tasks like logging and coordination across distributed systems. 21.Trivial File Transfer Protocol (TFTP): TFTP is a simplified version of FTP used primarily for transferring files between devices in a local network. It's lightweight and doesn't require user authentication, making it suitable for tasks like updating firmware on network devices. 22.Voice over Internet Protocol (VoIP): VoIP enables voice communication over the internet by converting analog voice signals into digital data packets. Services like Skype and Zoom use VoIP to facilitate voice and video calls, offering cost-effective and flexible communication options. 23. Session Initiation Protocol (SIP): SIP is a signaling protocol used for initiating, maintaining, and terminating multimedia sessions, including voice and video calls over IP networks. It's widely used in VoIP systems and other real-time communication applications.
- 6. Internet Protocols, contd… 20.Real-time Transport Protocol (RTP): RTP is used in conjunction with SIP for delivering audio and video streams over IP networks. It provides mechanisms for packetization, timestamping, and delivery monitoring, ensuring smooth and synchronized media playback. 21.Internet Group Management Protocol (IGMP): IGMP is used by multicast routers to manage membership in multicast groups on a network. It enables hosts to join and leave multicast groups dynamically, facilitating efficient distribution of multimedia content to multiple recipients. 22.Simple Mail Transfer Protocol Secure (SMTPS): SMTPS is a secure version of SMTP that adds encryption to protect email communication between clients and servers. It uses SSL or TLS to encrypt the data transmitted over the network, safeguarding sensitive information from interception. 23.Network Time Protocol (NTP): NTP is an updated and more robust version of SNTP, used for synchronizing the clocks of devices on a network. It employs more sophisticated algorithms and mechanisms for clock adjustment, offering higher accuracy and reliability.
- 7. What are - Internet Protocols, a long list of Protocols 24. Internet Control Protocol (ICP): ICP is a caching protocol used in web proxy servers to improve performance by storing and serving frequently accessed web content locally. It reduces latency and bandwidth usage by retrieving content from the cache instead of fetching it from the origin server every time. 25. Border Gateway Protocol 4 (BGP-4): BGP-4 is an enhanced version of BGP used in large-scale networks, such as the internet backbone. It includes features for route aggregation, policy-based routing, and traffic engineering, enabling efficient and flexible management of network traffic flows. These protocols, with their specific functions and capabilities, form the foundation of the modern internet, enabling a wide range of applications and services that we rely on every day.
- 8. What are - Internet Protocols, a long list of Protocols Use practical examples and analogies to make the concepts of internet protocols more relatable: 1.HTTP/HTTPS: Explain HTTP as requesting a webpage (like asking for a book from a library) and HTTPS as requesting a webpage securely (like sending a letter in a locked envelope). 2.TCP/IP: Compare TCP to ensuring a package is delivered correctly by confirming receipt and checking for errors (like getting a delivery confirmation when ordering online), and IP to addressing the package to the right location (like putting the correct address on an envelope). 3.DNS: Describe DNS as a phonebook for the internet that translates website names to IP addresses (like looking up a contact in your phone to call them). 4.SMTP: Illustrate SMTP as sending emails (like sending a letter through the mail) and servers acting as post offices to route the emails to their destinations. 5.FTP: Explain FTP as transferring files (like sending a file through a courier service) and ensuring the file reaches its destination intact. 6.UDP: Compare UDP to sending a postcard (fast but less reliable than a sealed letter) and being suitable for tasks like video streaming or online gaming. 7.POP3/IMAP: Describe POP3 as picking up mail from a post office (downloading emails to your device) and IMAP as accessing your mailbox remotely (checking emails online). 8.SSH: Explain SSH as a secure tunnel to access a computer remotely (like having a secret passage into a castle) and ensuring only authorized users can enter. 9.SSL/TLS: Compare SSL/TLS to speaking in a secret code (encryption) to protect conversations between your browser and websites (like having a private conversation in a crowded room).
- 9. What are - Internet Protocols, a long list of Protocols 1.SNMP: Describe SNMP as monitoring and managing devices on a network (like checking if a printer needs ink or if a server is overheating) using a dashboard-like interface. 2.DHCP: Explain DHCP as automatically assigning IP addresses to devices on a network (like getting assigned seats at a dinner party) without manual configuration. Using these everyday analogies can make the concepts of internet protocols more relatable and easier to understand for students with limited computer backgrounds.
- 10. some additional day-to-day examples to explain internet protocols: Some additional day-to-day examples to explain internet protocols: 1.HTTP/HTTPS: HTTP is like requesting a specific item from a menu at a restaurant, while HTTPS is like ordering the same item but making sure it's prepared securely and delivered to your table without anyone tampering with it. 2.TCP/IP: TCP is like ensuring that a package you ordered online is tracked every step of the way until it safely reaches your doorstep, while IP is like the postal address on the package that directs it to your home. 3.DNS: DNS is like using a GPS to find the exact location of a restaurant based on its name, helping you navigate to the right place without getting lost. 4.SMTP: SMTP is like sending a message to a friend through a messaging app, where the app's servers ensure that your message is delivered to your friend's app securely. 5.FTP: FTP is like transferring photos from your phone to your computer using a USB cable, ensuring that all photos are copied correctly without any missing or corrupted files.
- 11. What are - Internet Protocols, a long list of Protocols 6. UDP: UDP is like streaming music on your phone, where small interruptions in the internet connection may cause a brief pause in playback but generally doesn't affect your overall listening experience. 7 POP3/IMAP: POP3 is like checking your physical mailbox and taking all the letters home, while IMAP is like accessing your mailbox at the post office from anywhere using your phone or computer. 8. SSH: SSH is like securely logging into your bank account using a password and an additional authentication method, ensuring that only you can access your account information. 9. SSL/TLS: SSL/TLS is like having a private conversation with someone in a crowded room by speaking in a language only the two of you understand, keeping your conversation confidential. 10. SNMP: SNMP is like using a smart home app to monitor the temperature in your house while you're away, allowing you to adjust the thermostat remotely if it gets too hot or too cold. 11. DHCP: DHCP is like attending a conference where organizers assign seats to attendees based on availability, ensuring that everyone has a place to sit without having to choose seats themselves. These examples should further enhance understanding by relating internet protocols to
- 13. What are - Internet Protocols, a long list of Protocols
- 14. What are - Internet Protocols, a long list of Protocols
- 15. What are - Internet Protocols, a long list of Protocols