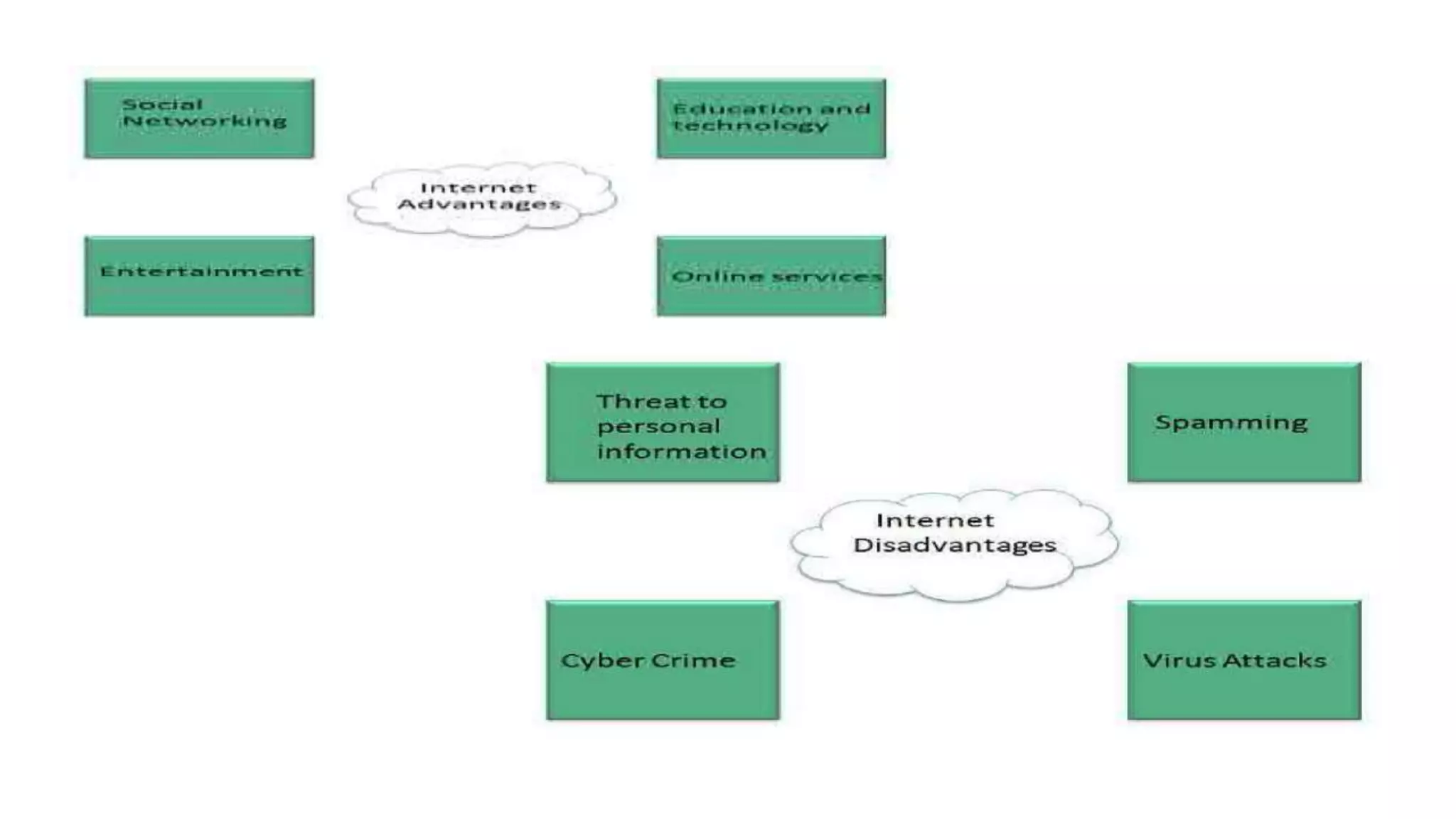
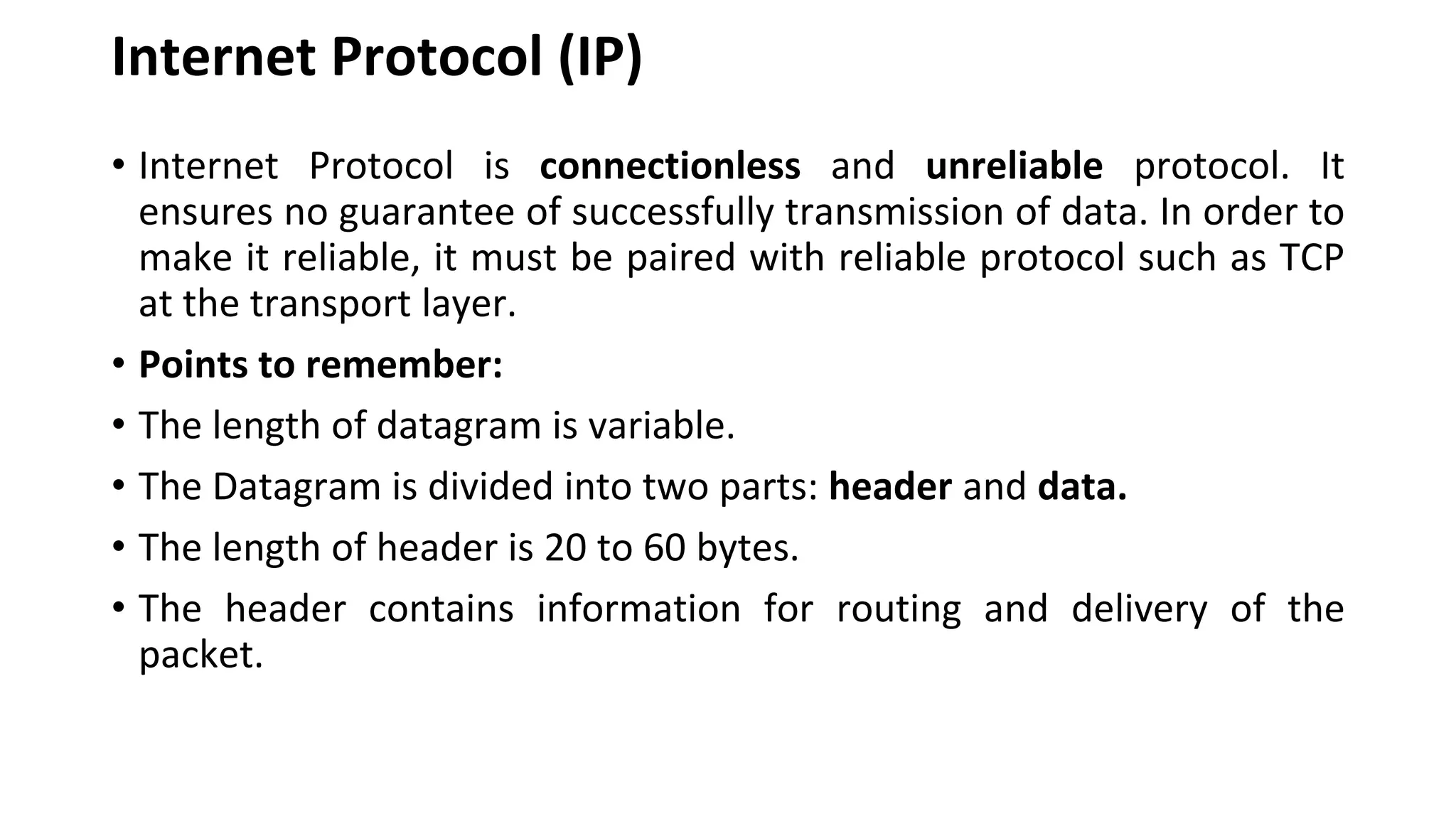
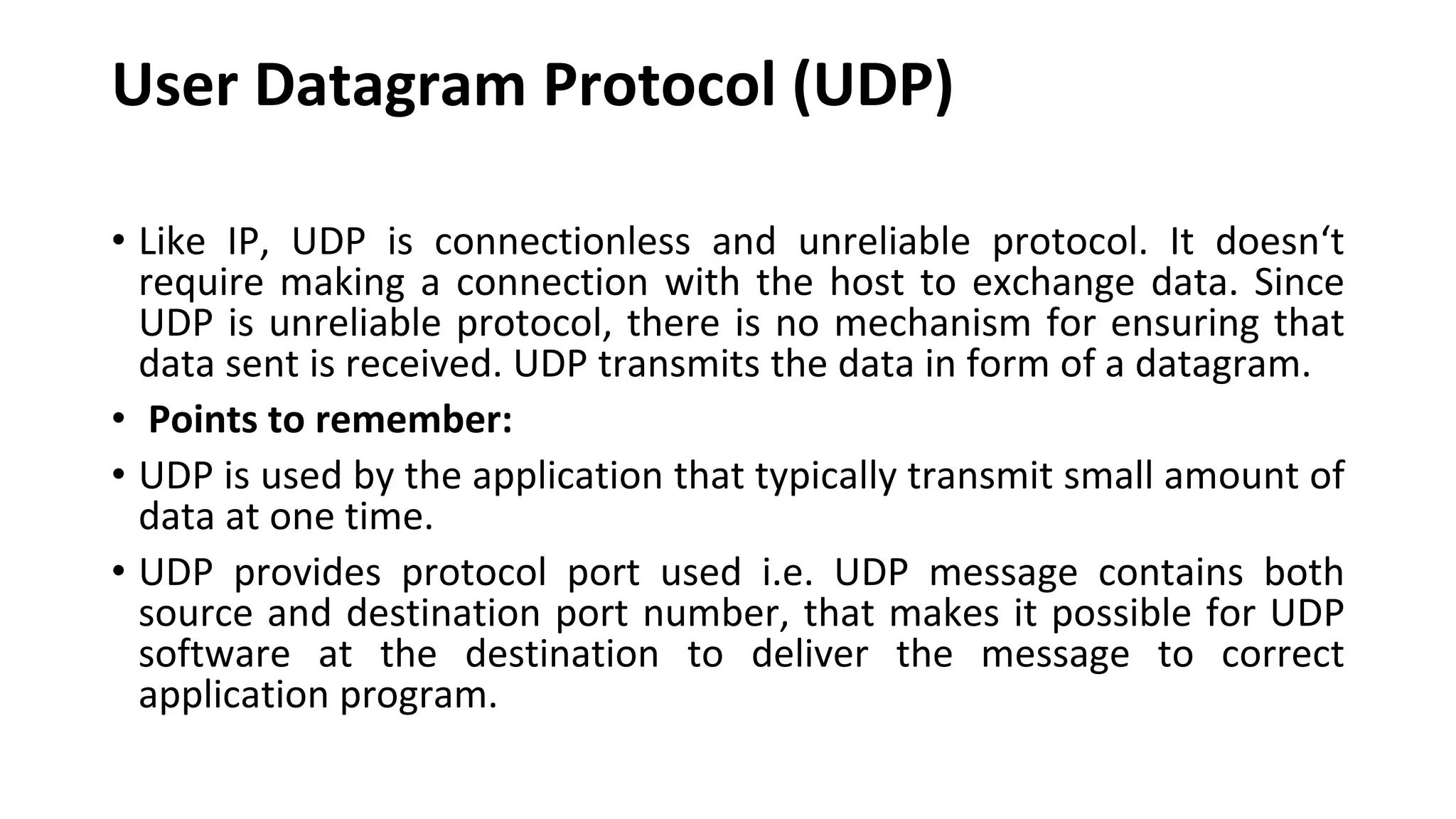
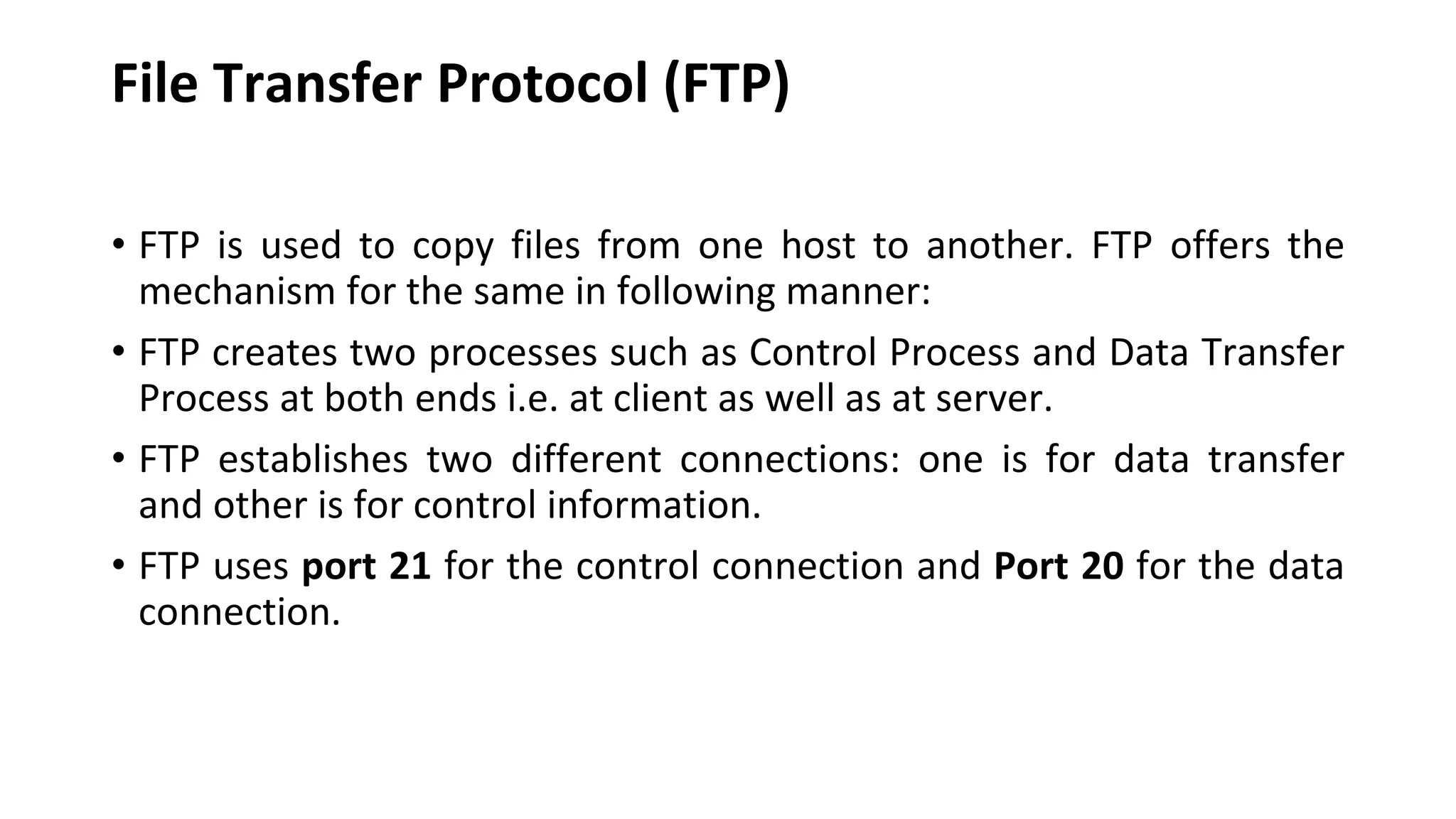
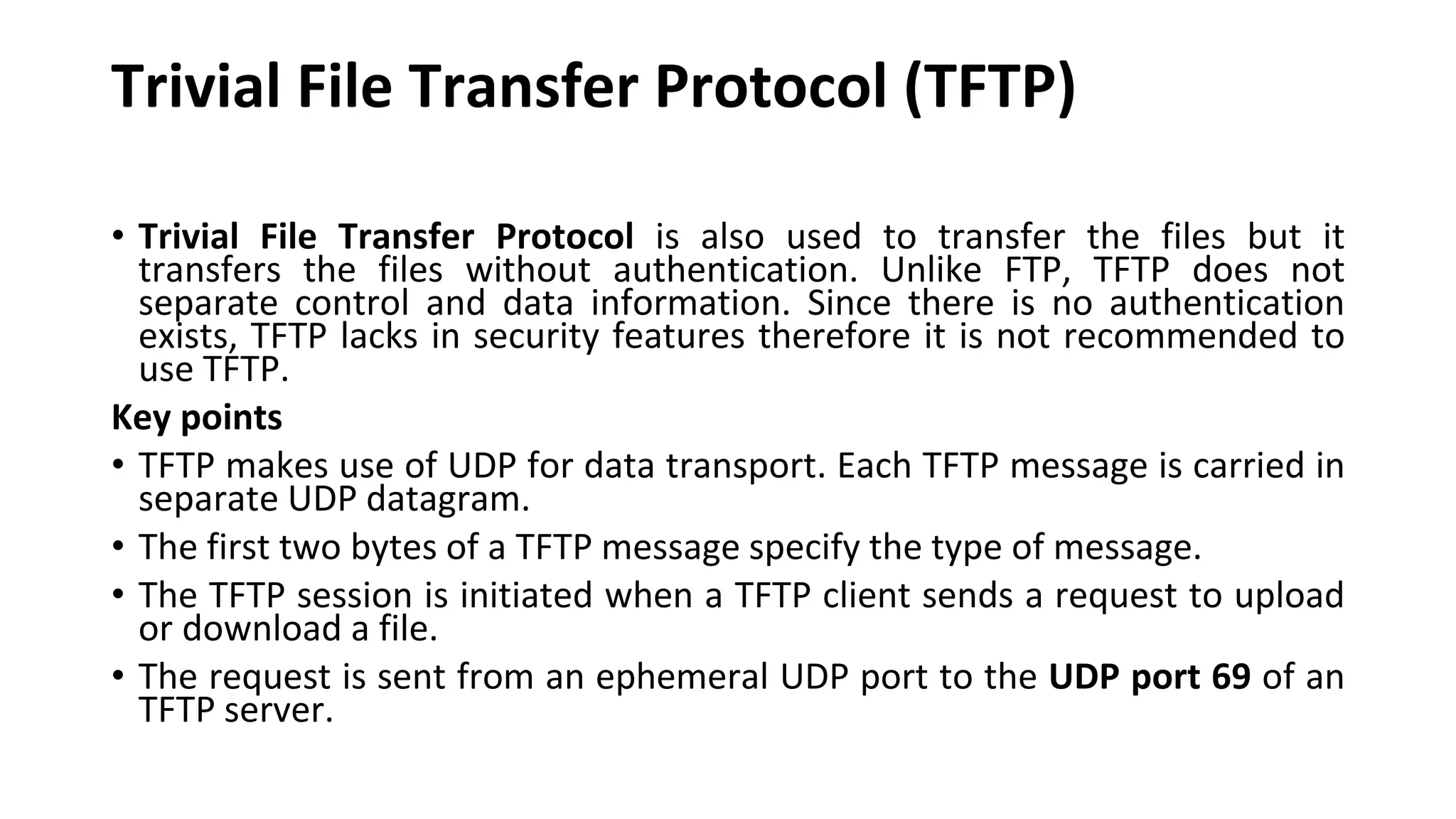
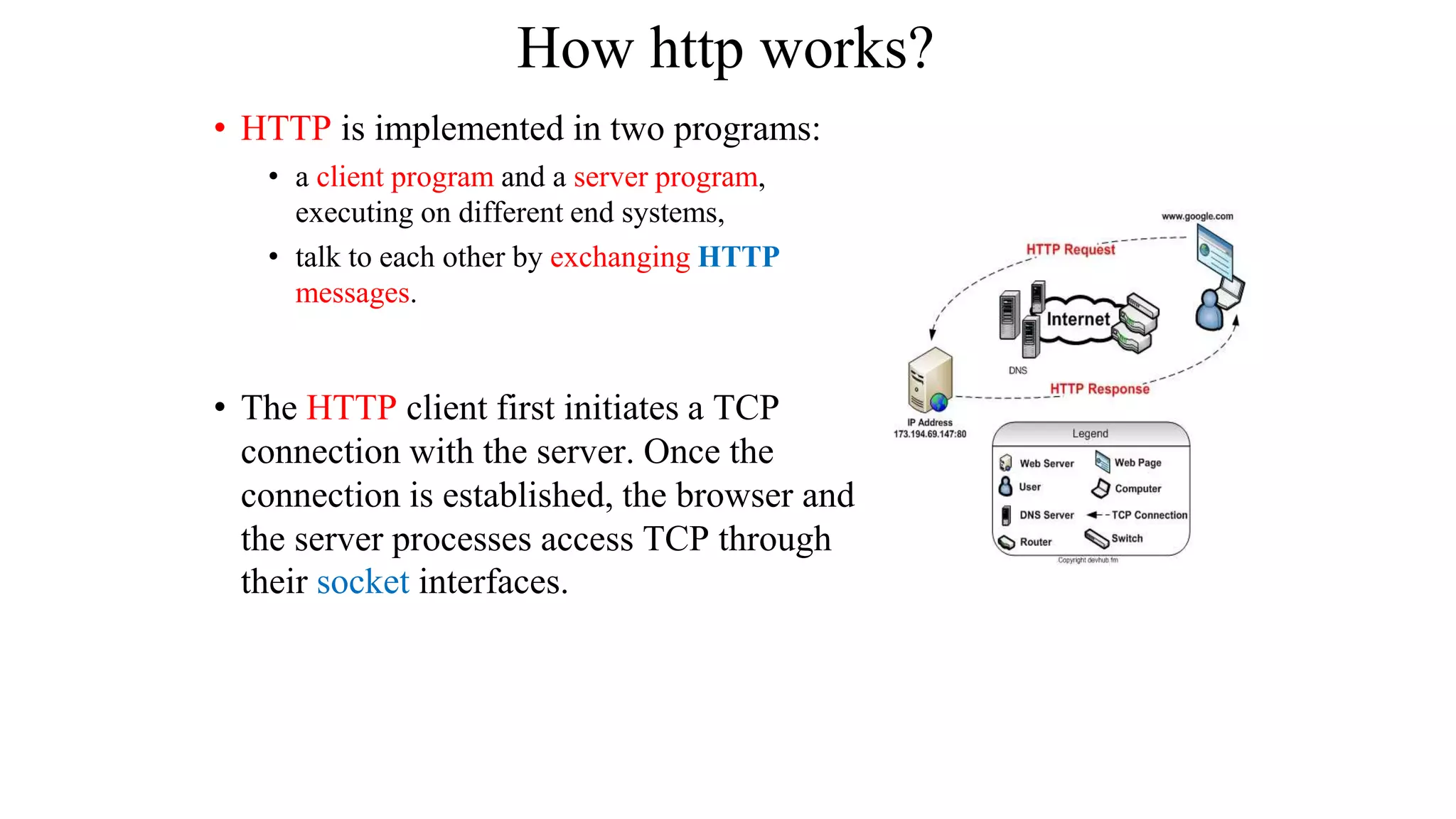
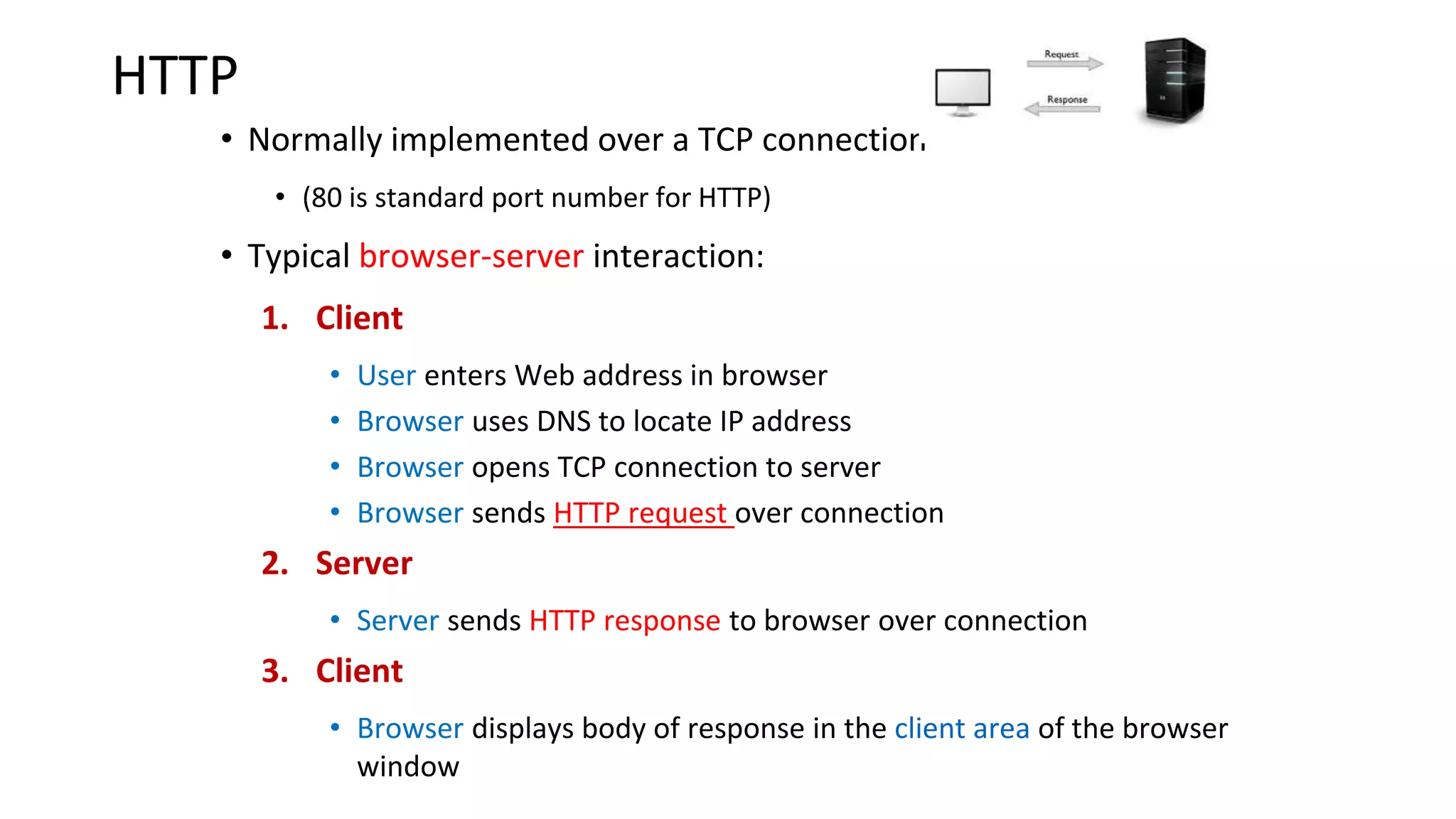
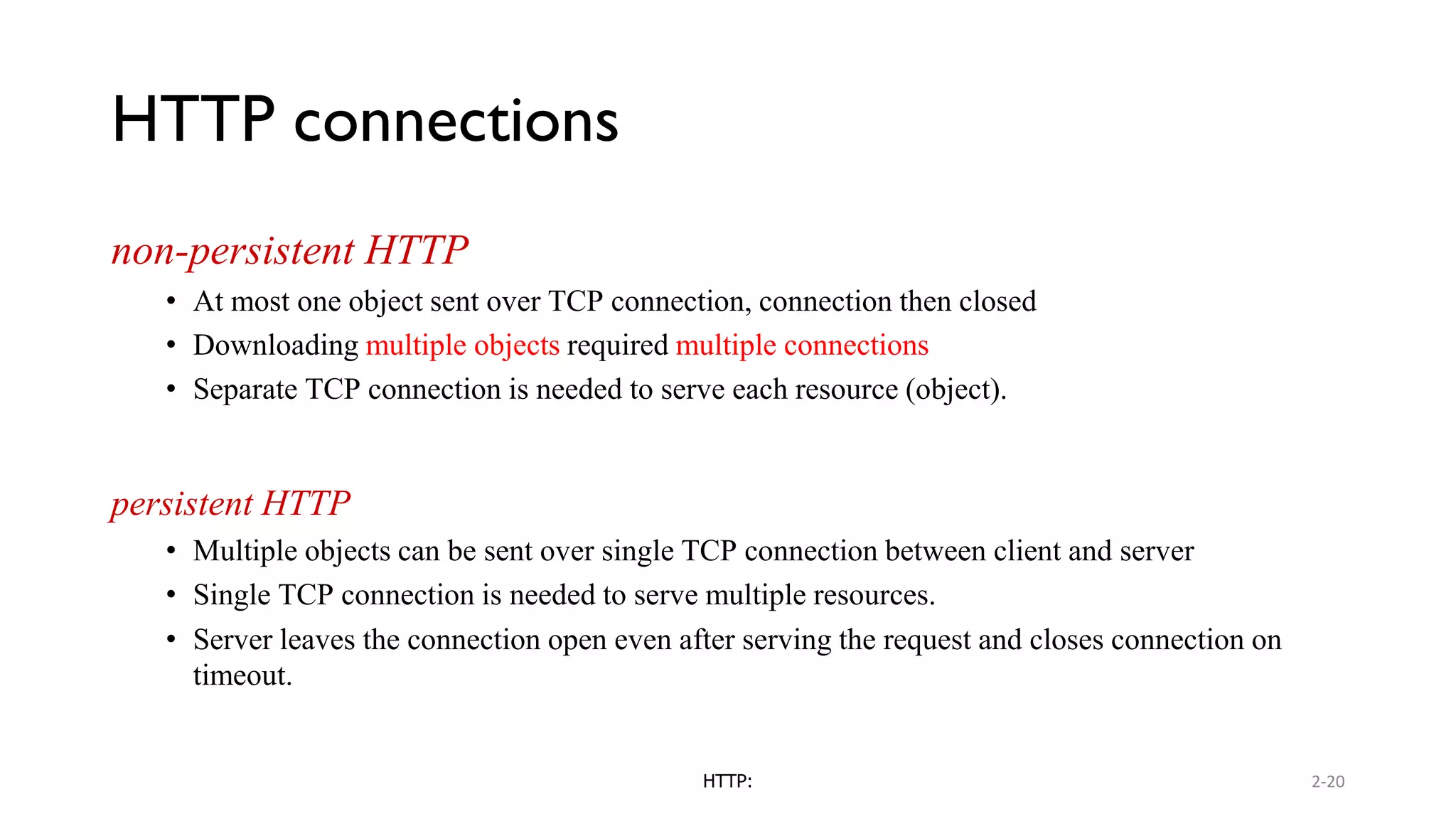
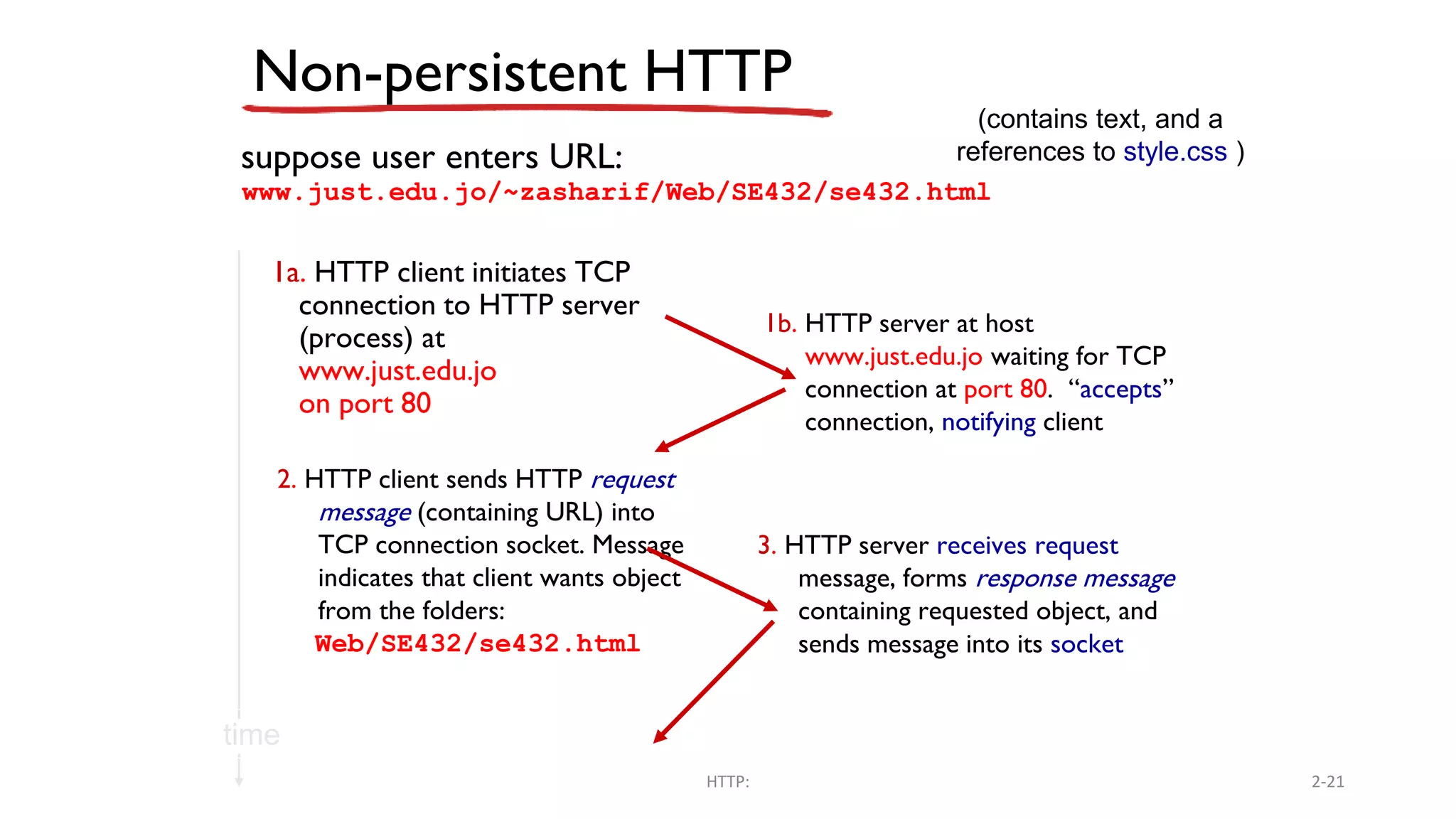
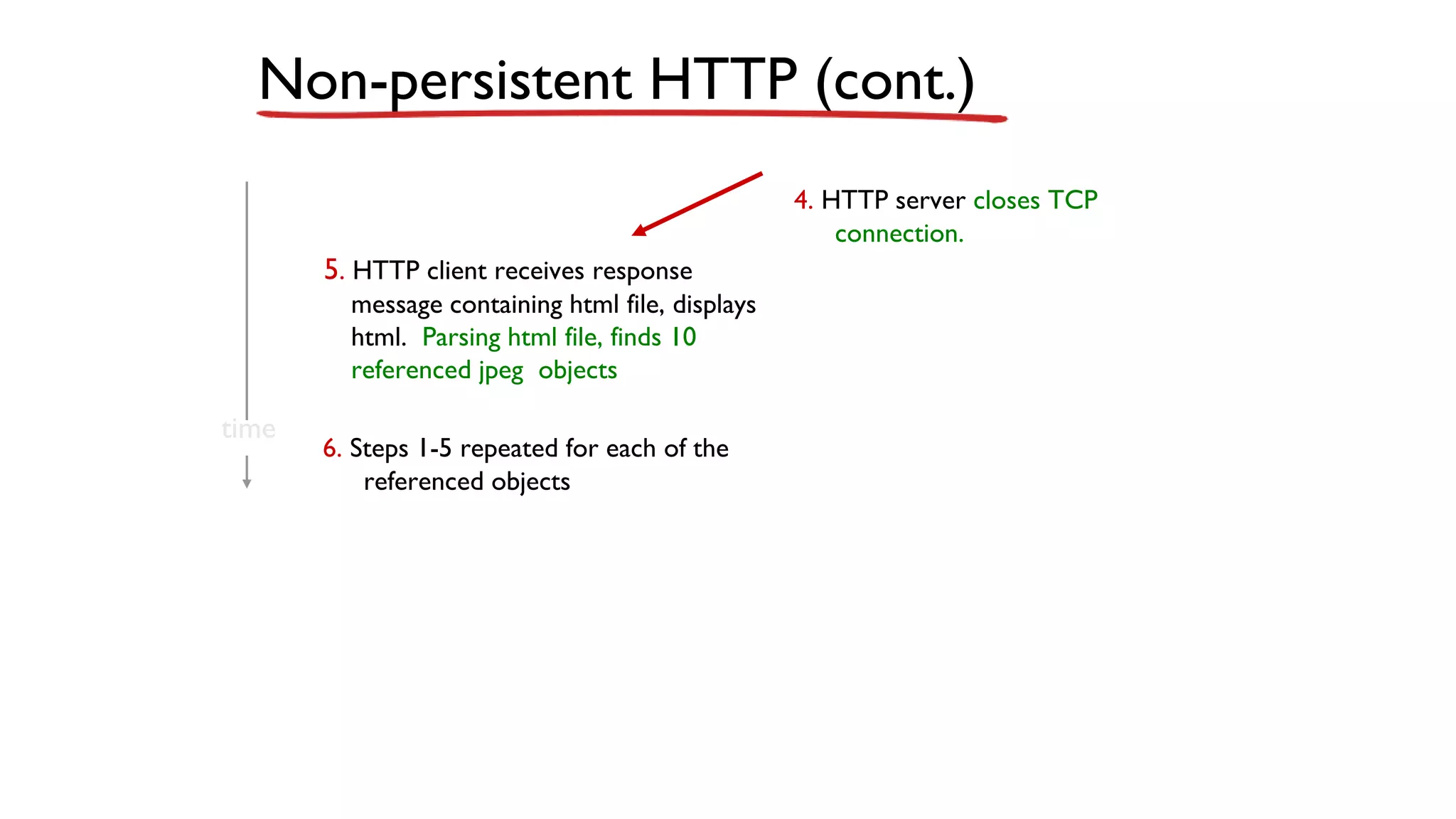
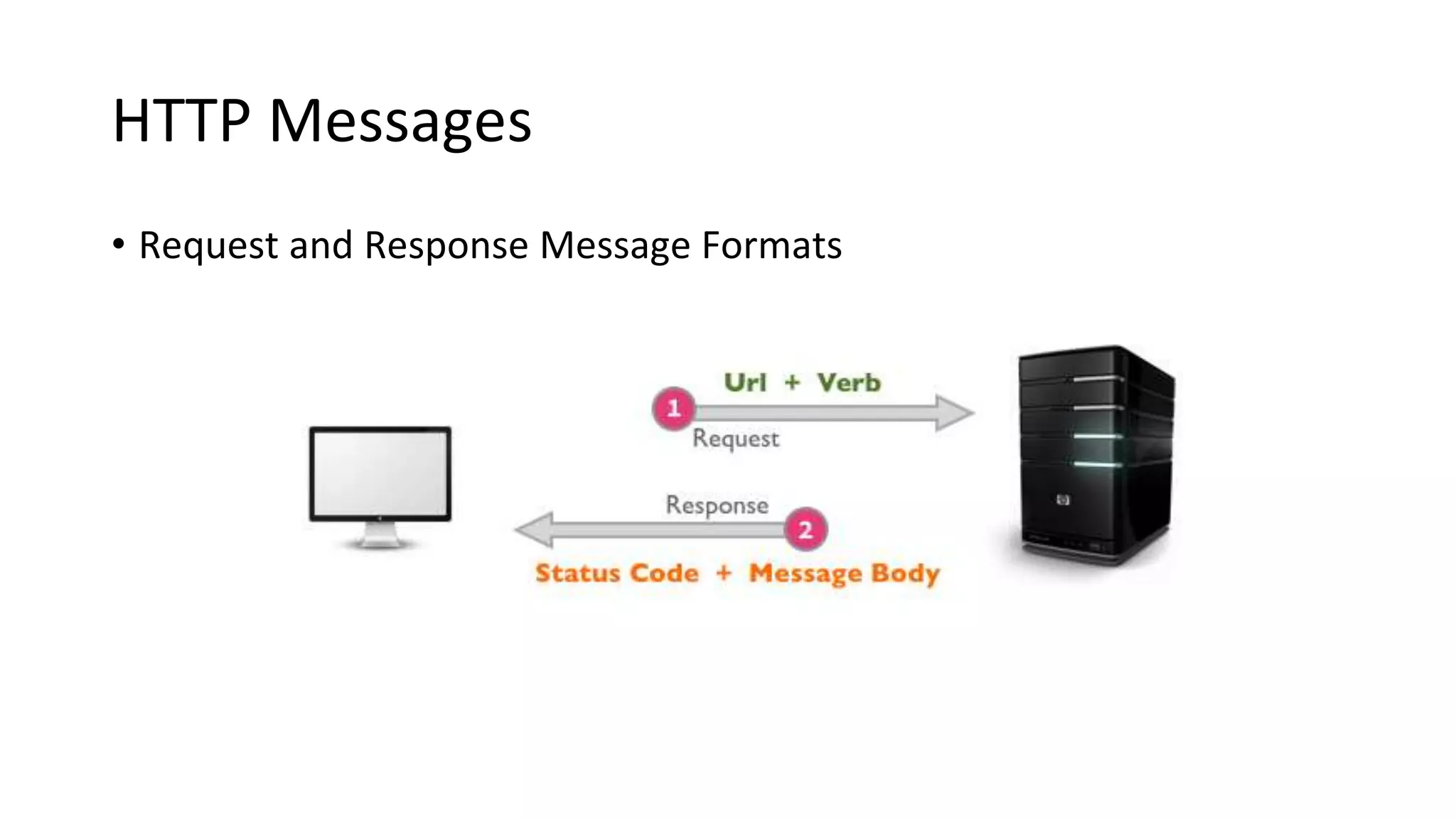
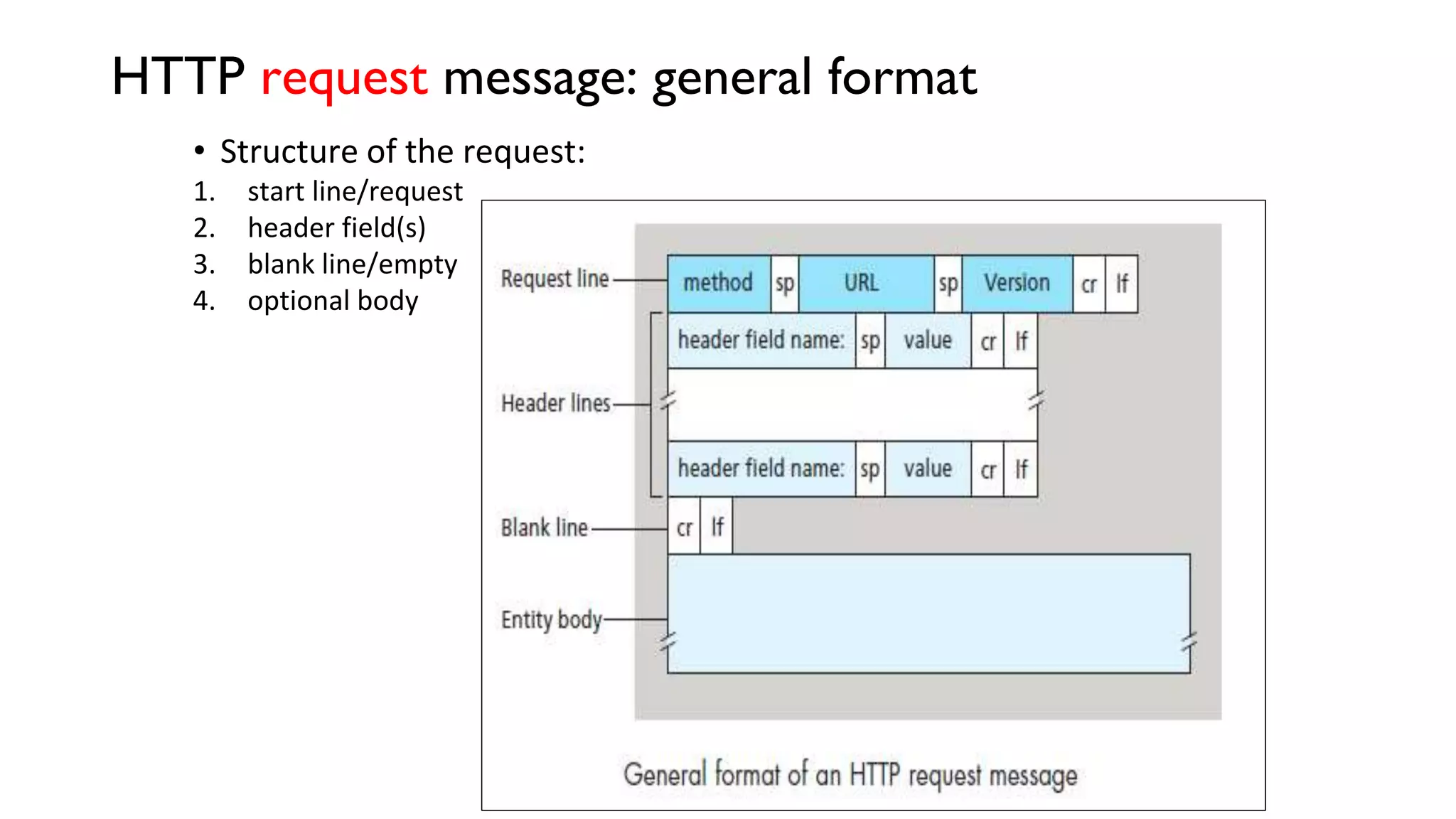
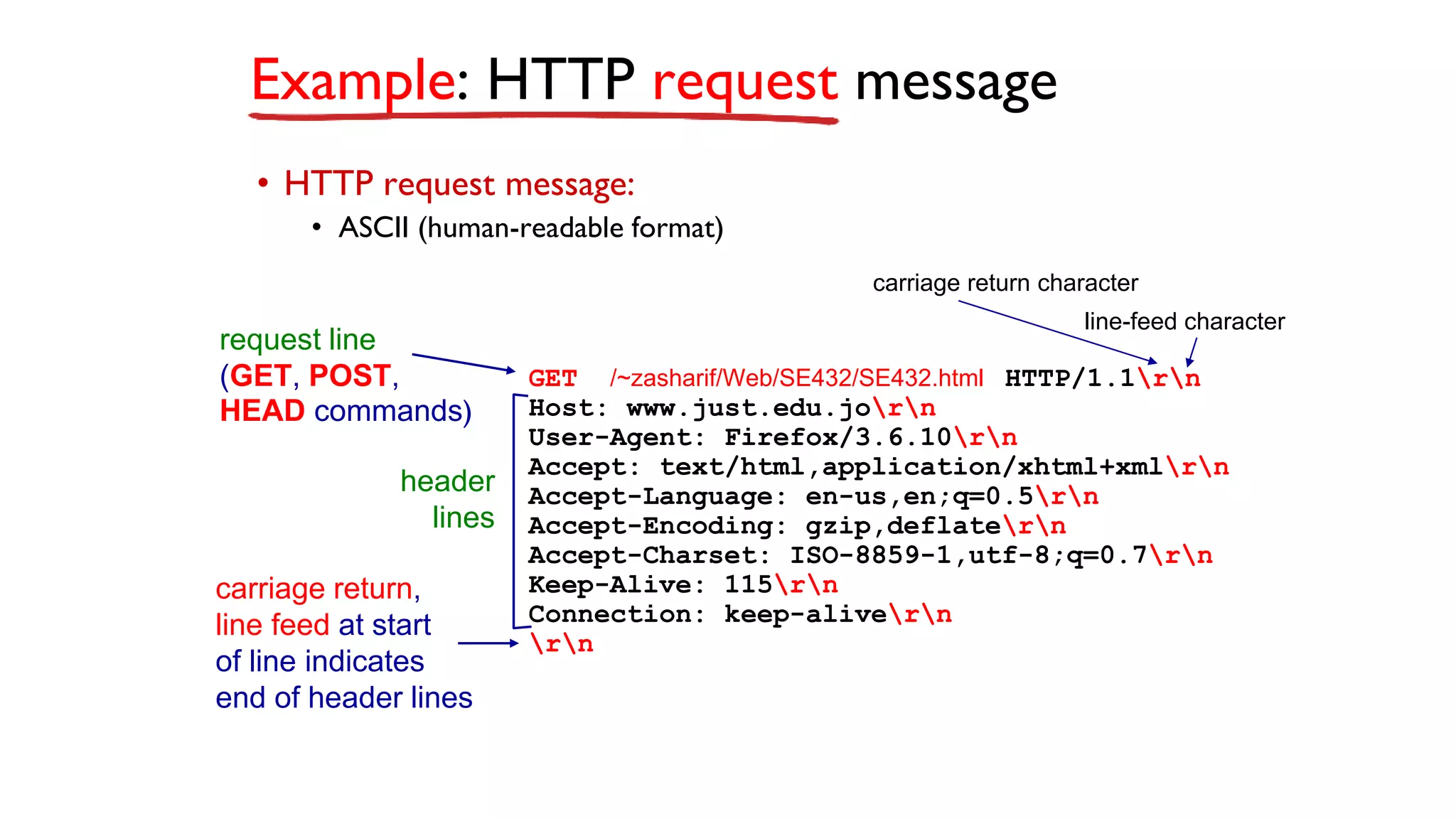
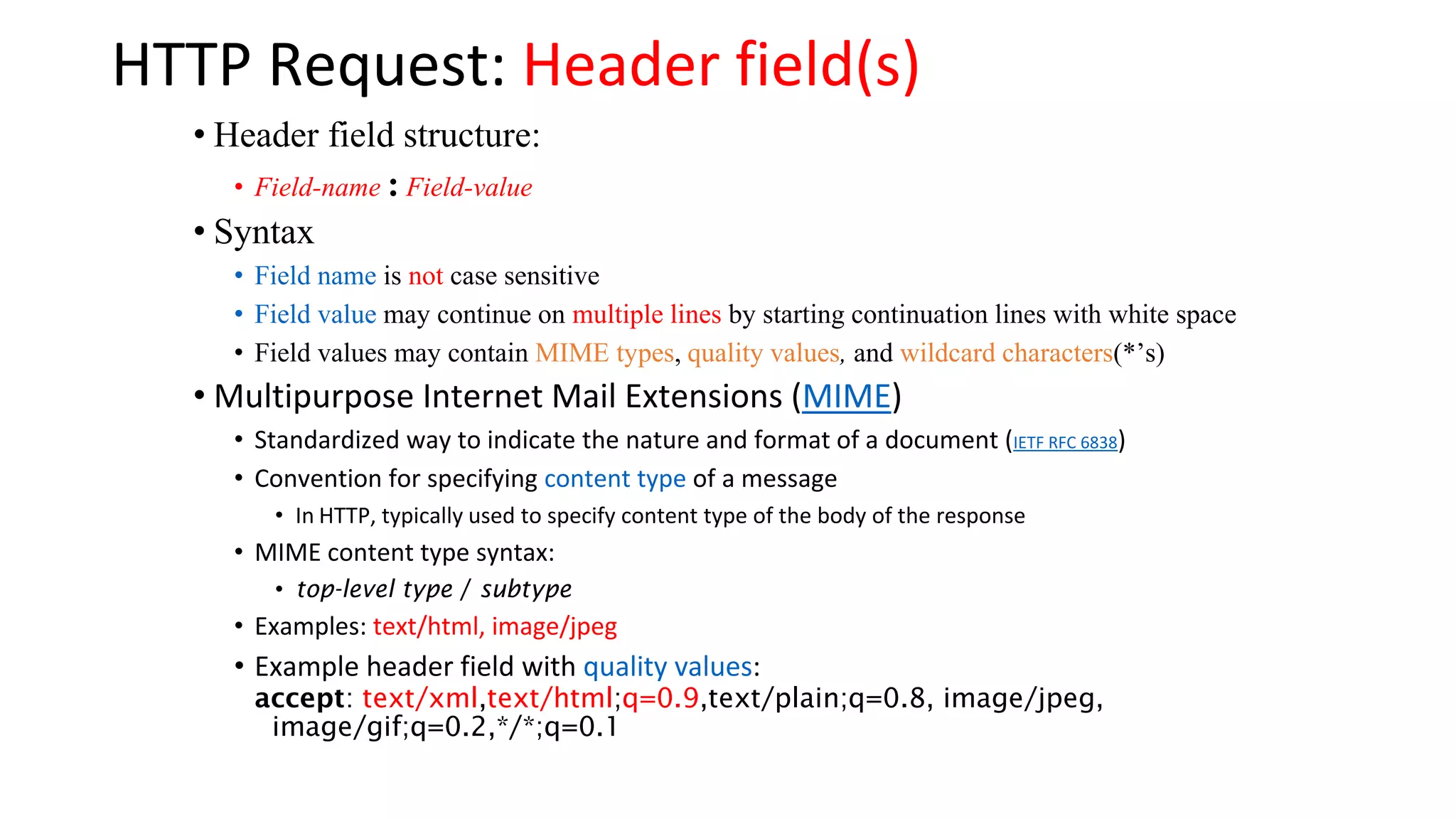
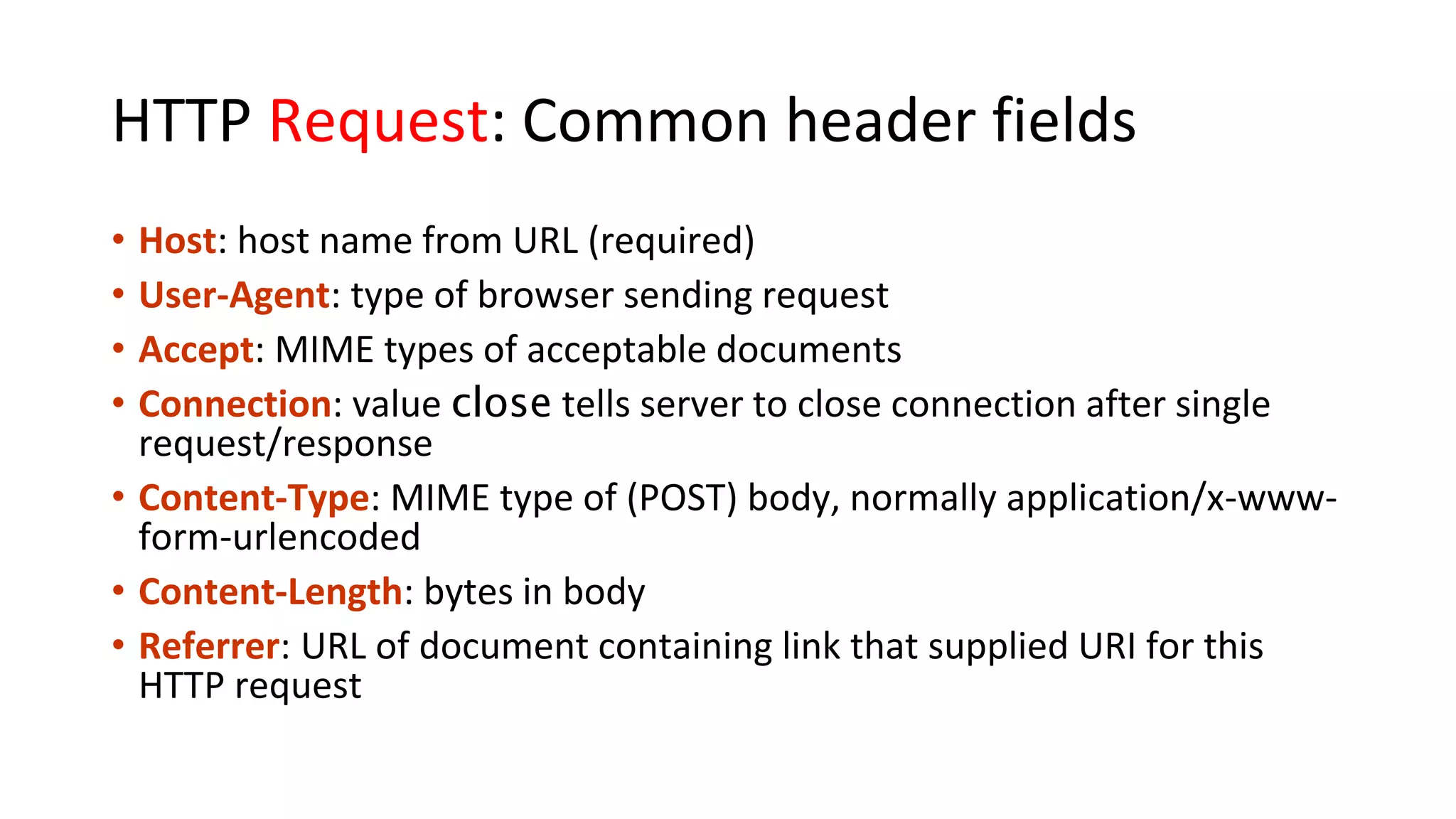
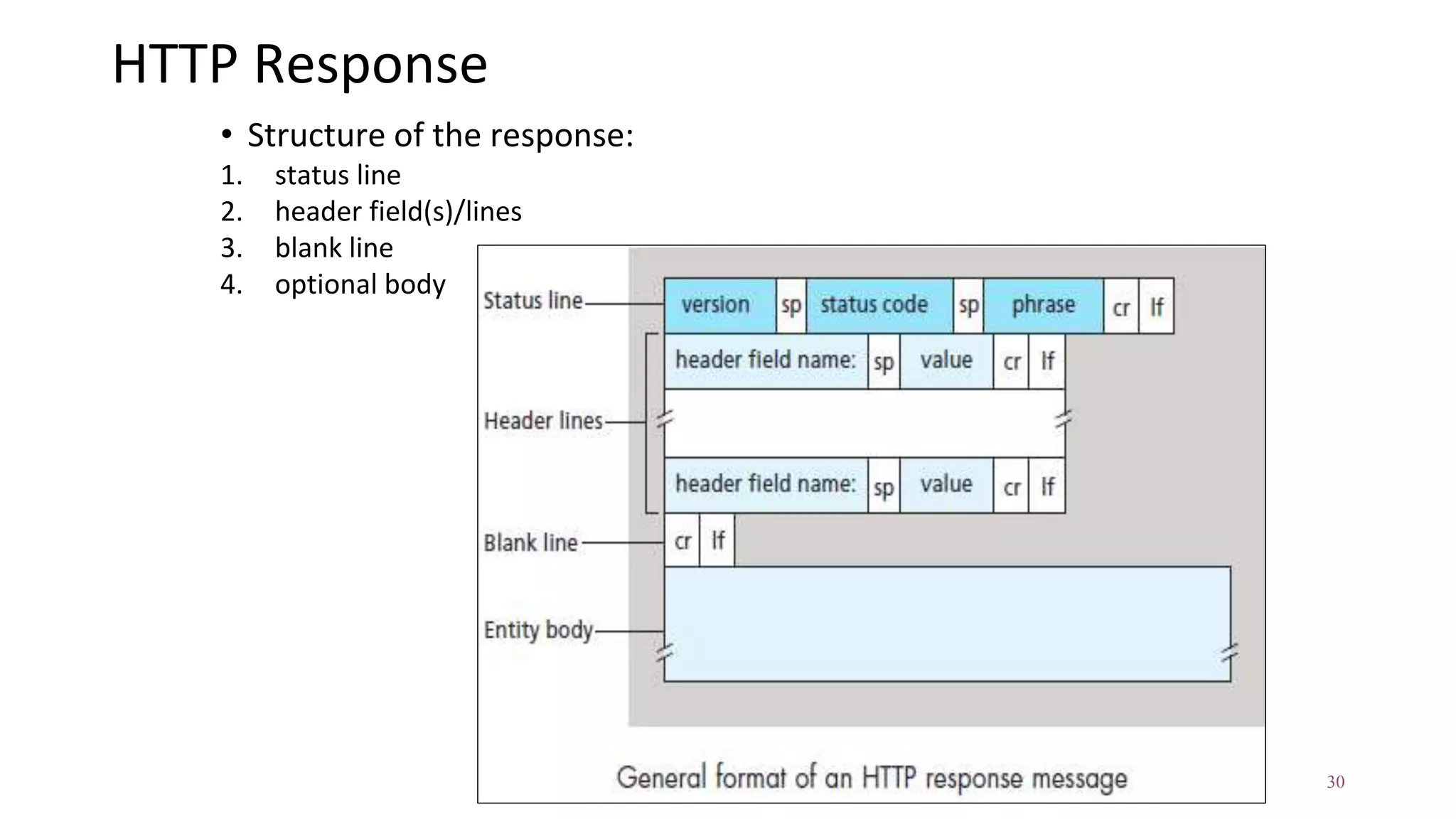
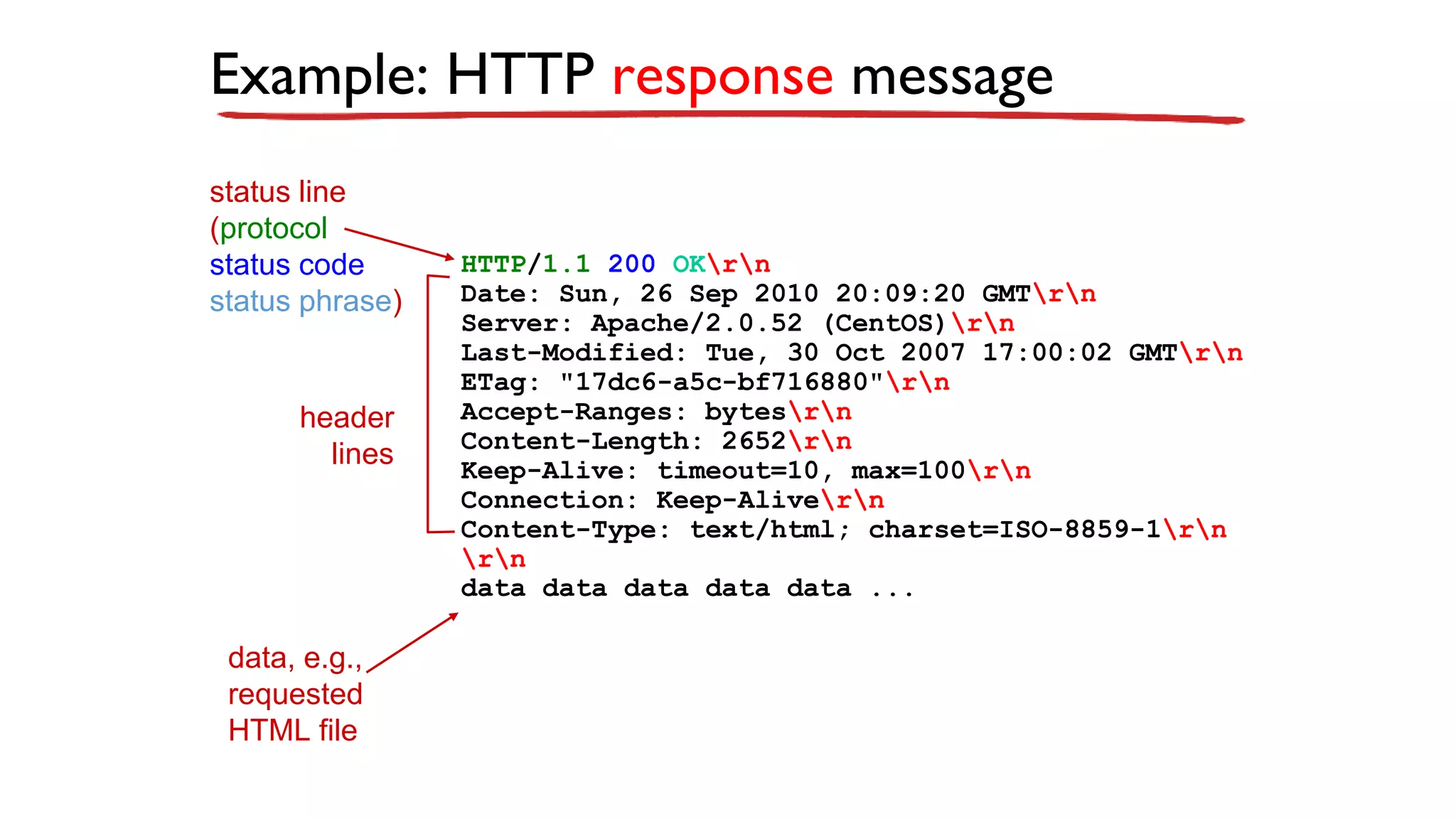
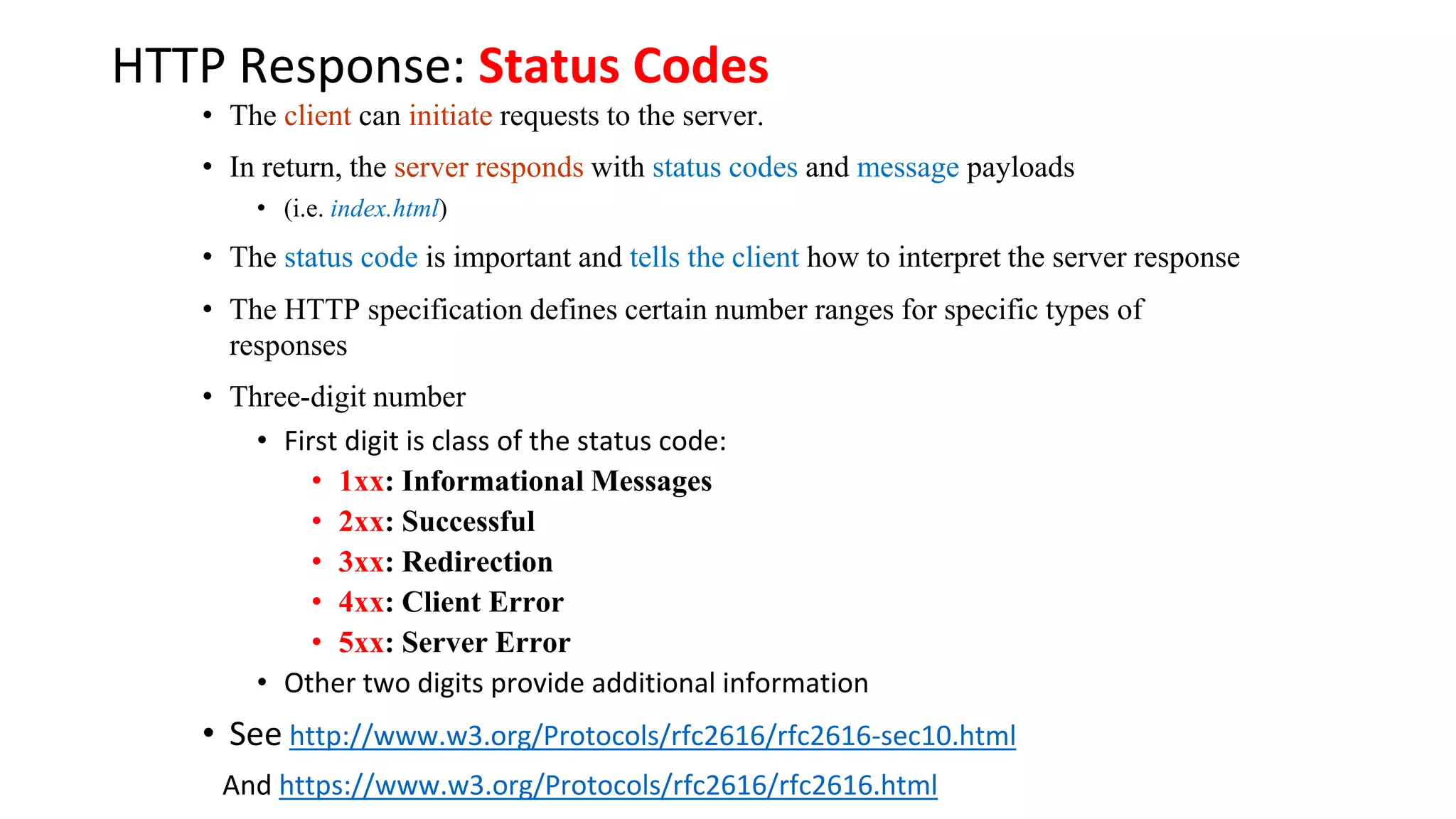
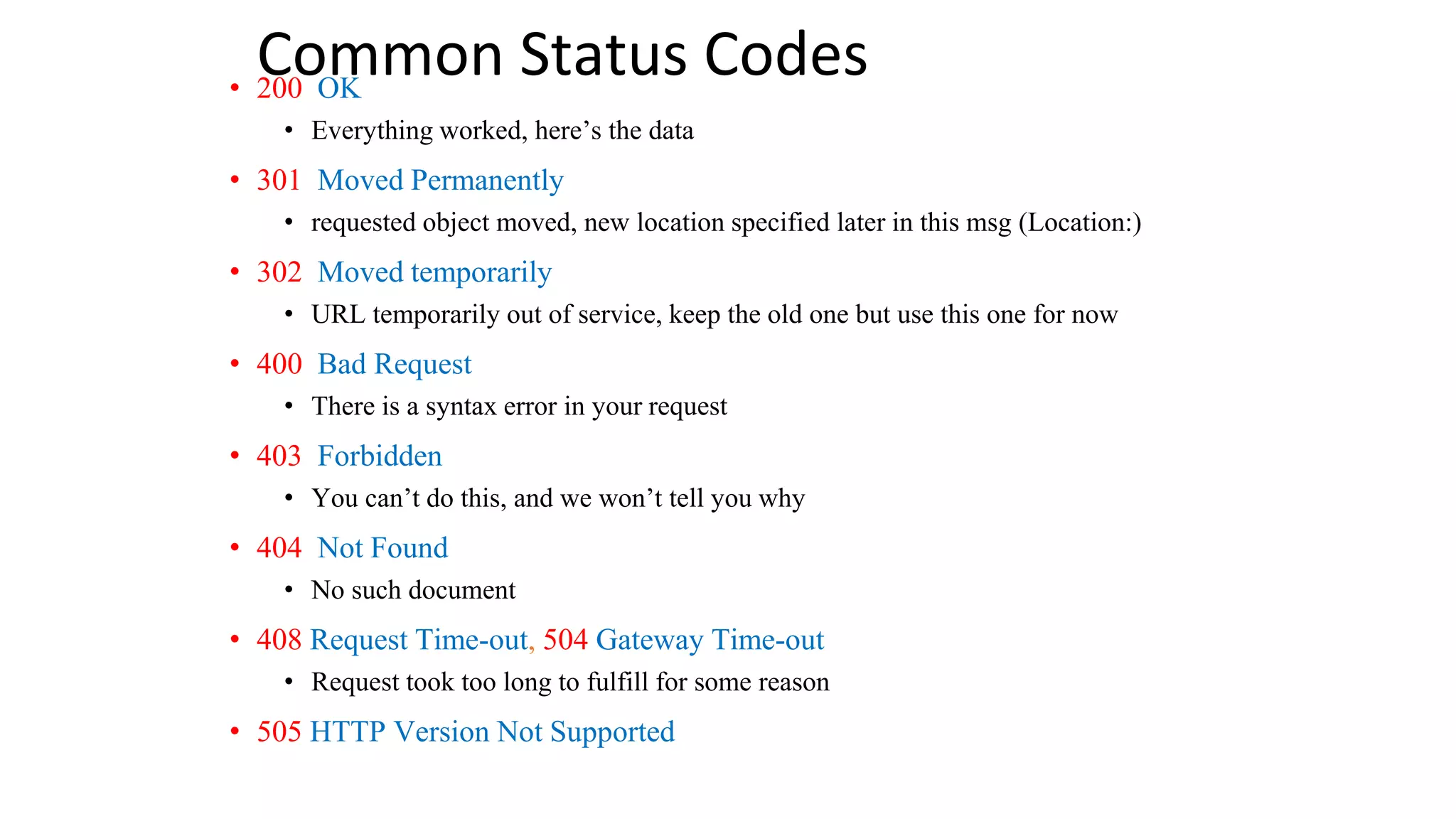
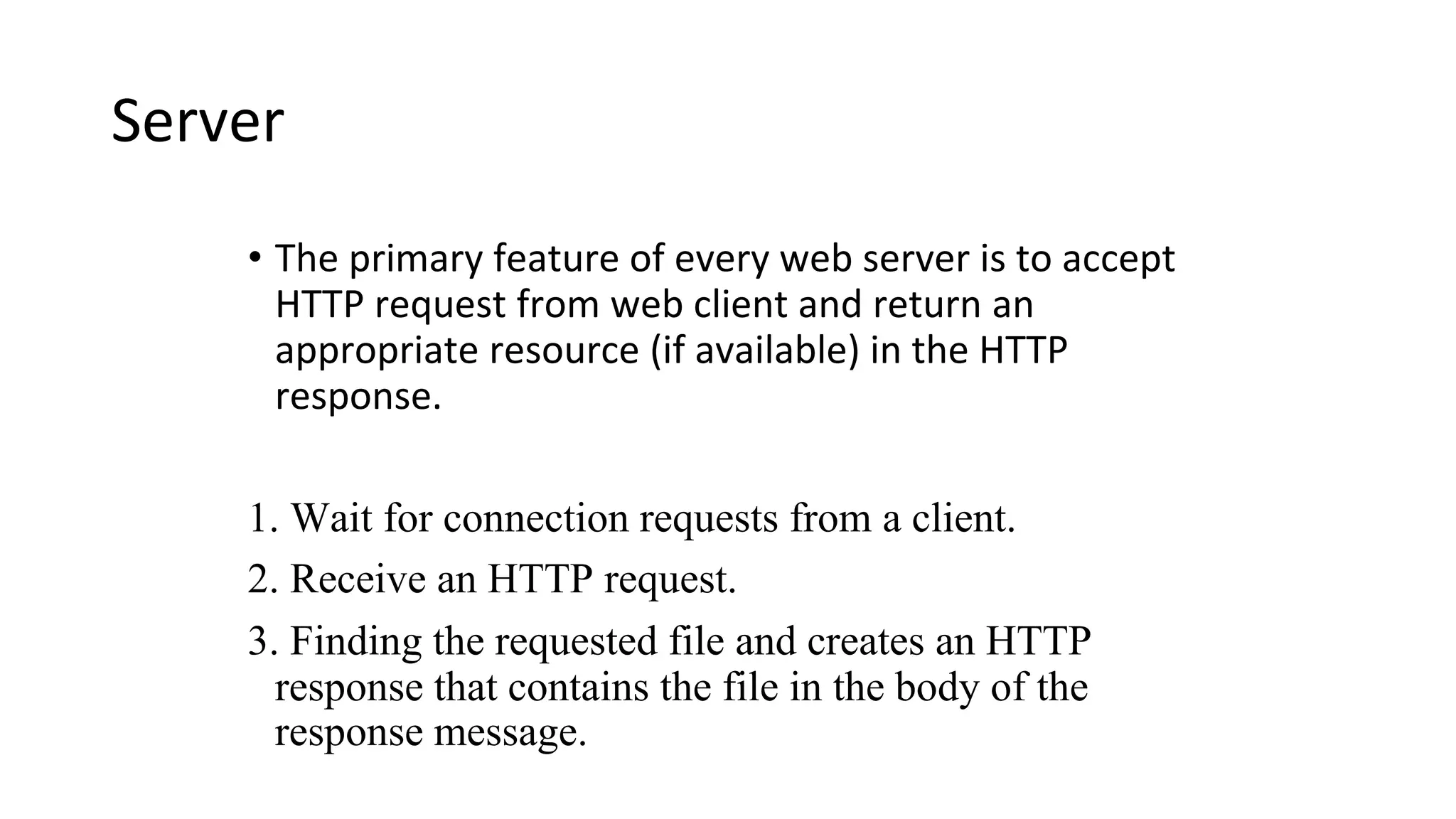
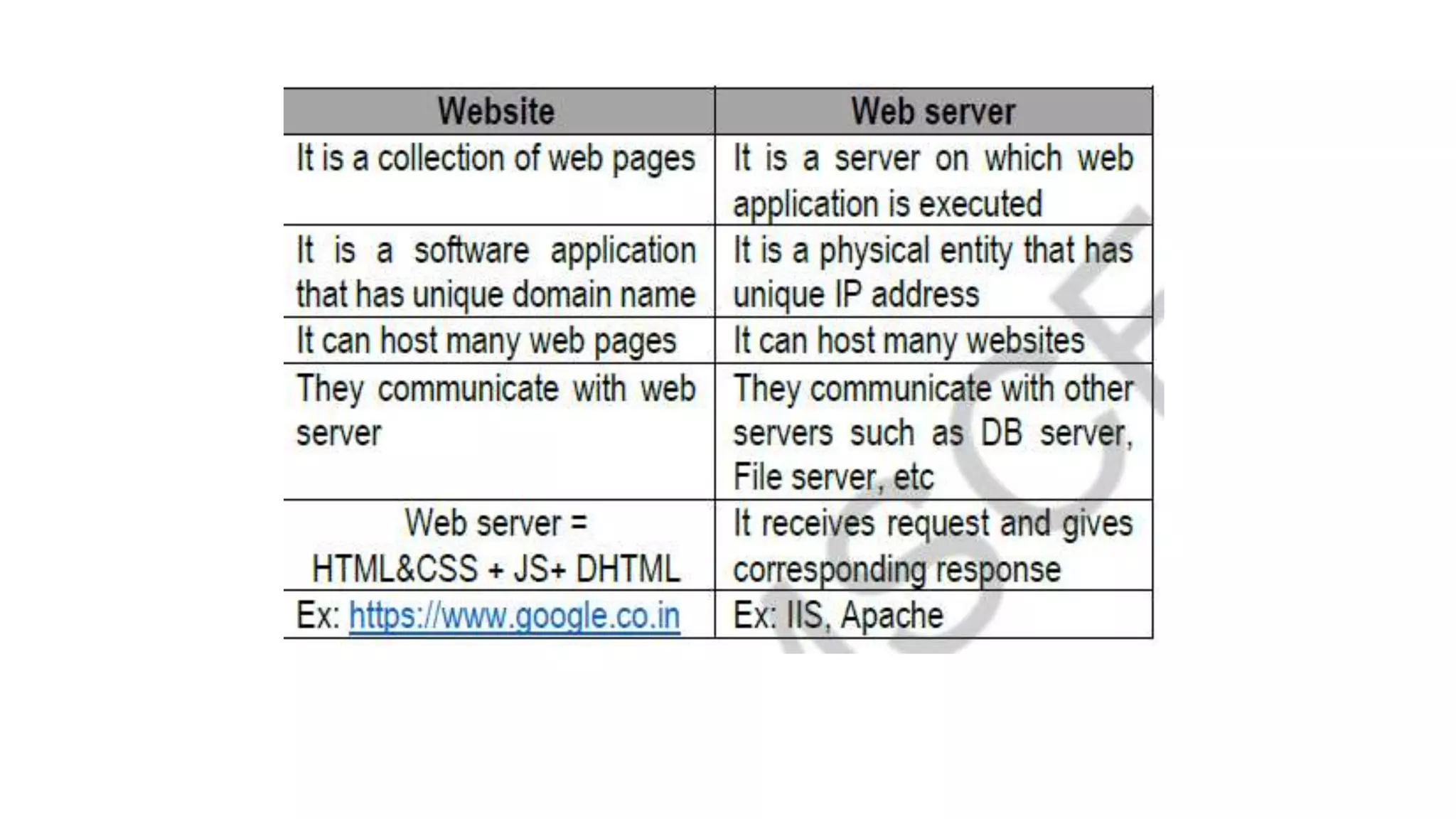
A website is a collection of web pages that can be accessed over the internet. It is hosted on a web server and viewed using web clients like browsers. Websites can be developed using languages like HTML, JavaScript, and PHP. The internet connects computers globally using TCP/IP and allows users to access websites by domain names that resolve to IP addresses. HTTP is the main protocol used to access websites. It establishes connections between clients and servers to request and transfer web pages and other content.