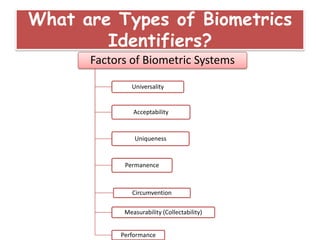
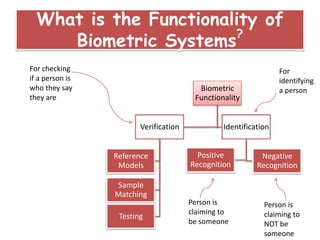
Biometrics refers to the identification of individuals based on unique physical or behavioral traits, making it a more reliable method than traditional password-based authentication. The document discusses various types of biometric identifiers, their functionality, and the criteria for selecting biometric systems, emphasizing the benefits of secure and accurate identity verification. Despite challenges in widespread adoption, the document asserts that the use of biometrics is expanding in corporate and business settings.