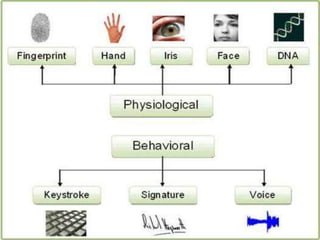
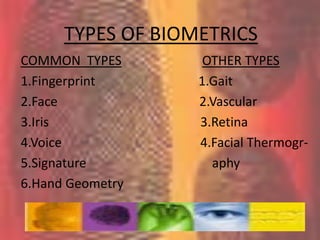
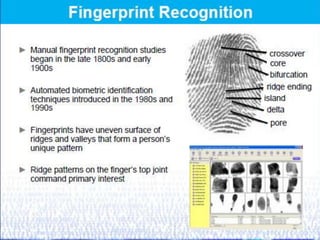
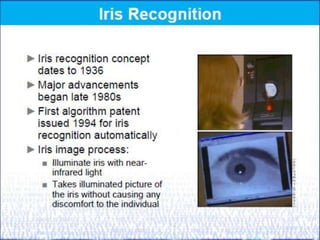
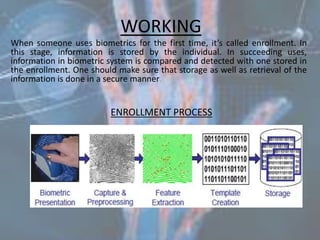
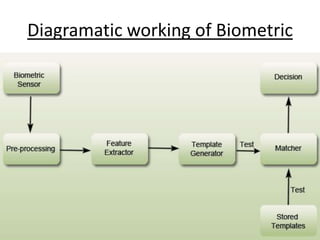
Biometrics, defined as life measurement, utilizes unique physiological and behavioral characteristics for individual identification, primarily for security purposes. Key types include fingerprint, facial recognition, iris recognition, voice, and signature, which are processed through an enrollment phase where data is securely stored and later compared for verification. The future of biometrics promises advancements in security technology, with applications in law enforcement and e-commerce to enhance safety and reduce fraud.