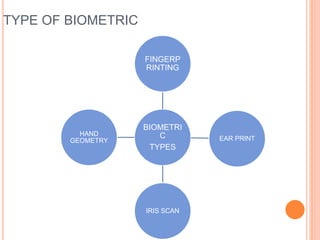
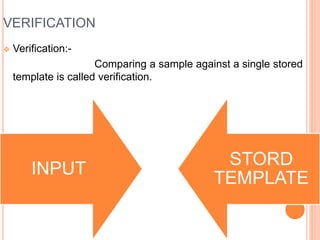
This document discusses biometrics and how biometric systems work. It defines biometrics as using physiological or behavioral characteristics to identify individuals uniquely. Common biometric types include fingerprints, iris scans, hand geometry, and facial recognition. Biometric systems work by enrollment, where a biometric sample is captured and stored as a template, and authentication, where a new sample is compared to stored templates. The document also covers biometric standards, advantages like increased security over passwords, disadvantages like privacy concerns, and applications for access control and verification.