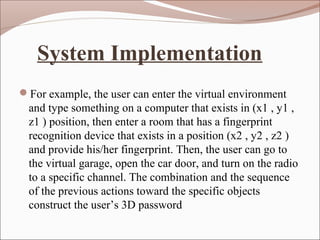
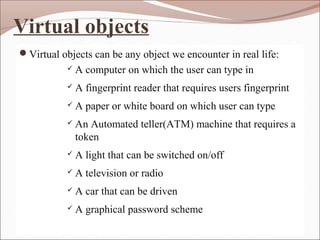
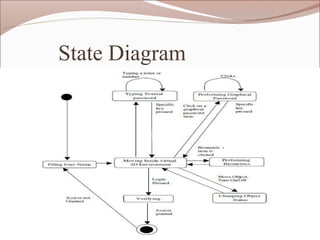
The document proposes a 3D password authentication system that combines recognition, recall, tokens, and biometrics by having users navigate a virtual 3D environment and interact with virtual objects in a specific sequence. This addresses weaknesses in traditional text passwords that are vulnerable to dictionary attacks. The 3D password would be more secure and customizable than existing authentication methods.