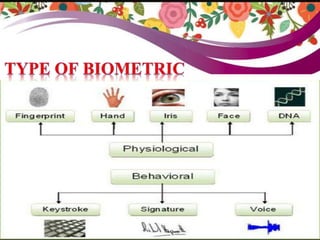
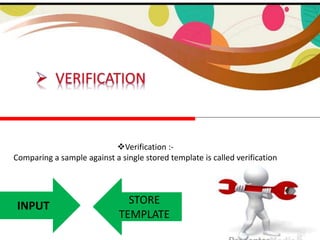
This document discusses biometrics, which uses physiological or behavioral characteristics to identify individuals. It outlines the history of biometrics dating back to fingerprint use in China in the 14th century. Various biometric techniques are described like fingerprints, facial recognition, iris scans, and hand geometry. Biometrics works by recording and comparing these characteristics using biometric devices and databases. Applications of biometrics include access control systems, e-commerce, banking, and crime investigation. While biometrics provides security, issues around privacy, identity risks, and technology limitations require consideration.