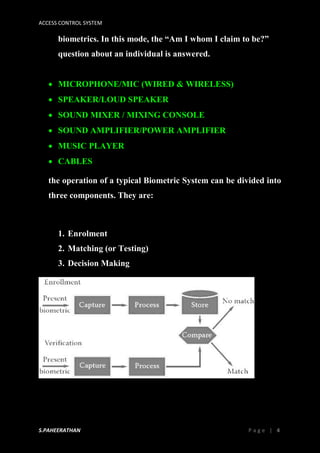
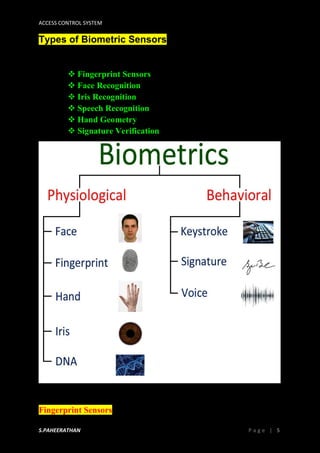
Access control systems aim to control physical and logical access to locations and systems. They authenticate users through identification methods like passwords, biometrics, security tokens and more. Biometric authentication is especially important as biometric traits like fingerprints, iris scans, and facial recognition cannot be stolen or forgotten like passwords. Access control helps minimize security risks from unauthorized access to physical locations and computer systems, networks, files and data.