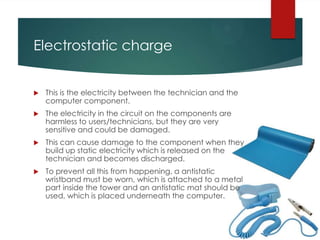
The document outlines potential problems during hardware installation, emphasizing the need for technician training and awareness of risks. It discusses issues such as electrostatic charge, component damage, and data loss, providing preventive measures like using antistatic wristbands and proper handling techniques. Additionally, it highlights the importance of backing up data to avoid corruption and loss, which can have severe consequences for organizations.