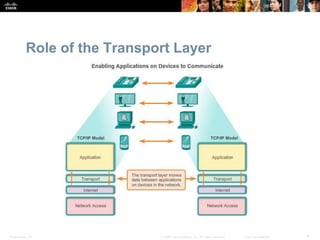
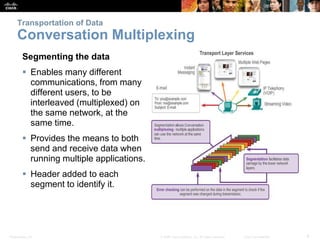
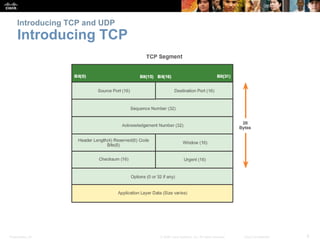
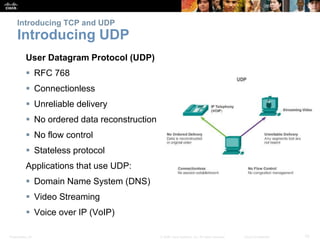
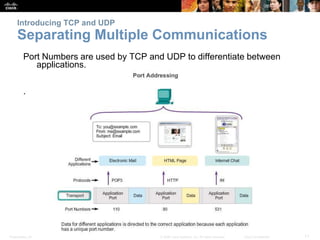
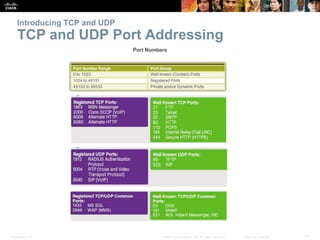
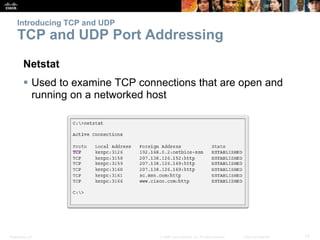
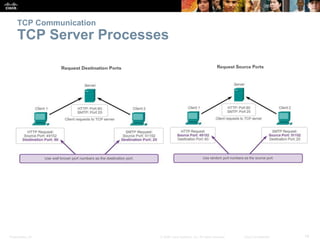
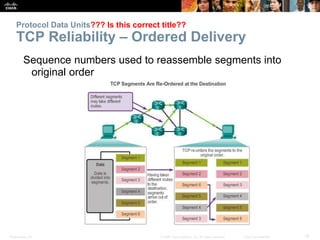
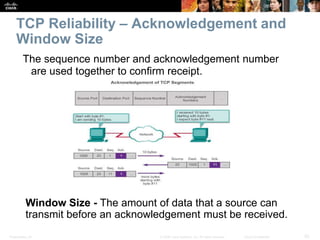
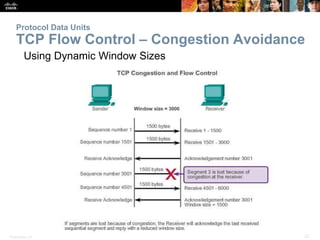
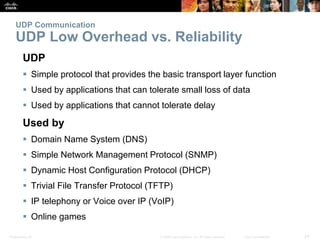
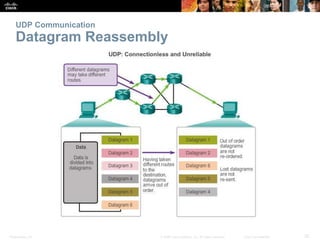
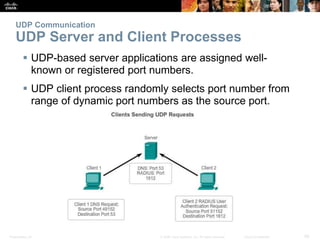
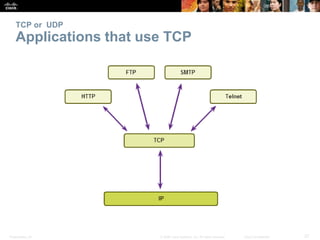
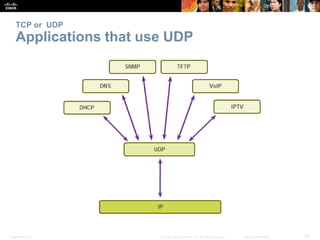
This document summarizes the transport layer and the key protocols TCP and UDP. It explains that the transport layer establishes communication sessions between applications, segments data for transmission, and ensures proper delivery. TCP provides reliable, ordered delivery using acknowledgements, while UDP is simpler but unreliable. Popular applications of each are discussed, showing how TCP and UDP address different network requirements.