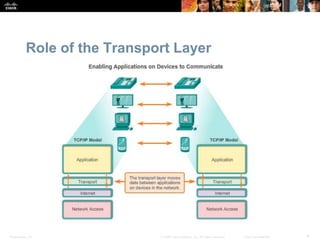
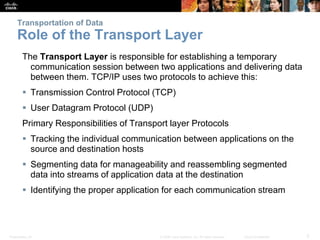
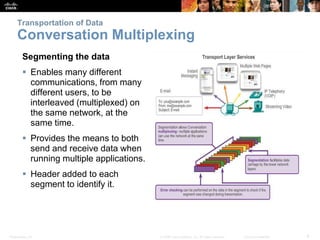
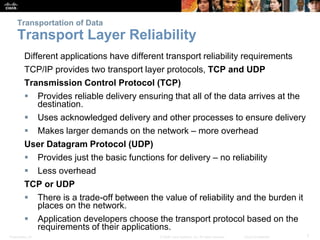
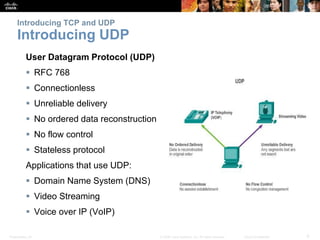
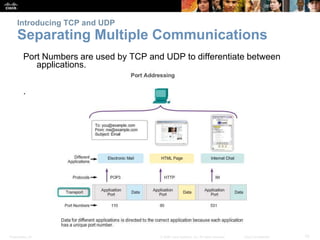
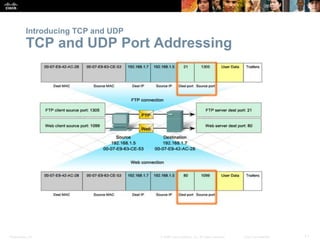
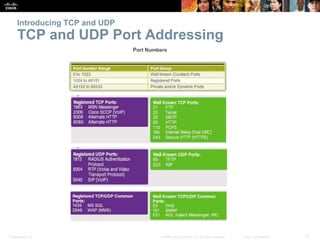
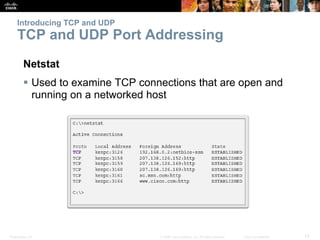
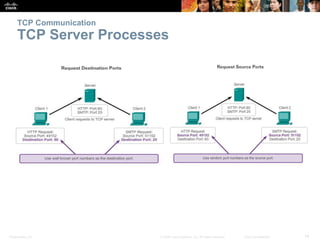
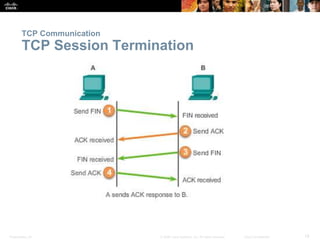
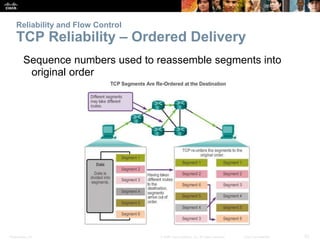
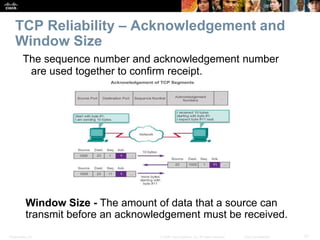
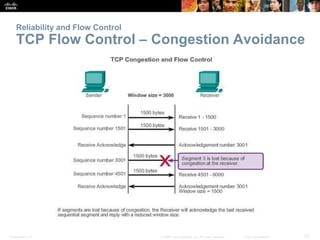
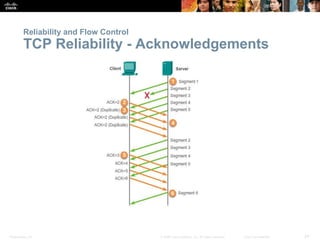
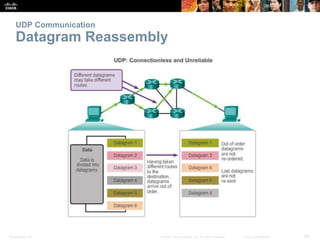
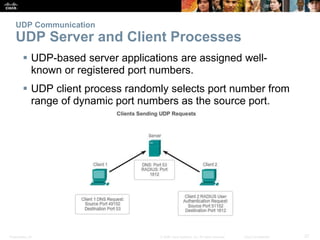
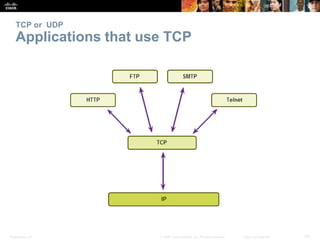
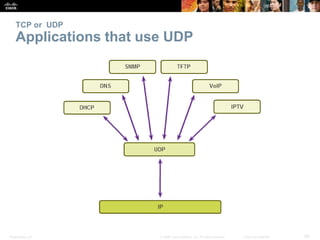
This document summarizes the transport layer and its key protocols TCP and UDP. It describes the transport layer's role in establishing communication sessions and delivering data between applications. TCP provides reliable, ordered delivery using acknowledgments, while UDP is unreliable but lower overhead. The document explains how ports distinguish communications and lists applications commonly using each protocol.