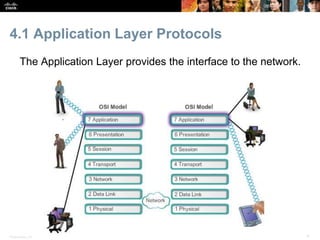
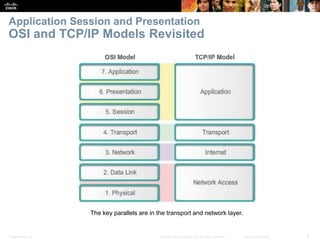
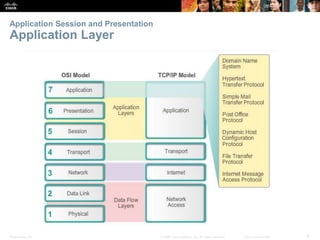
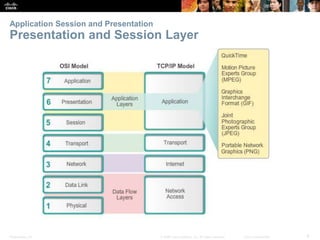
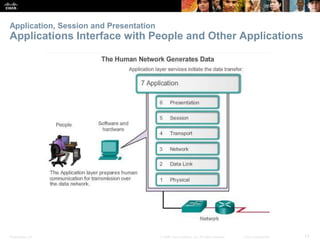
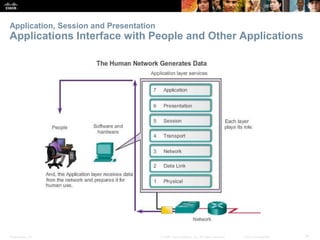
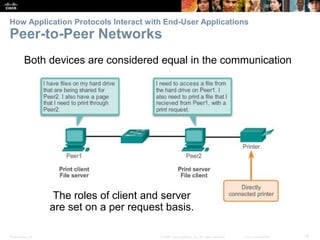
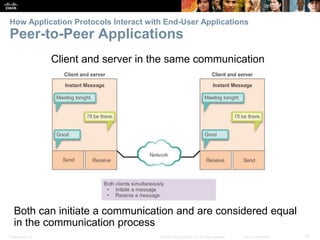
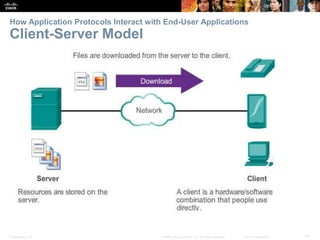
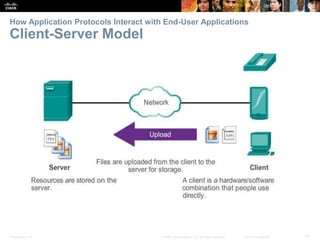
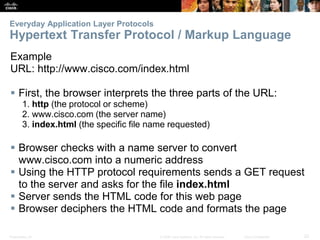
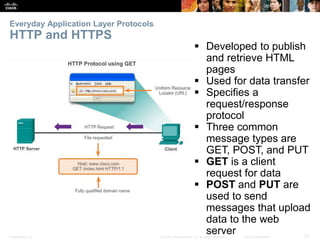
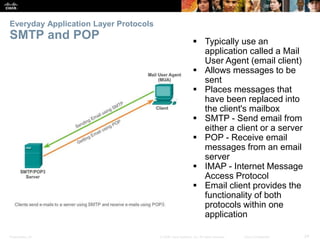
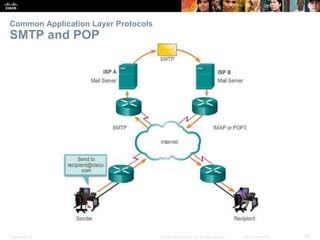
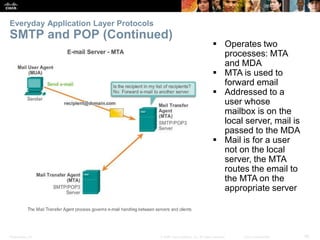
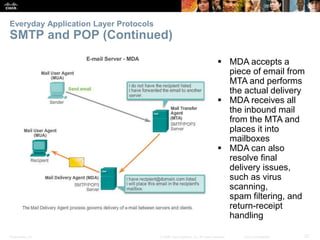
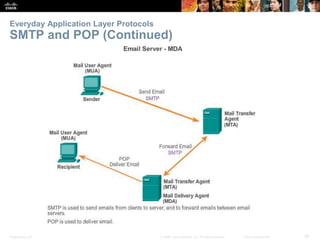
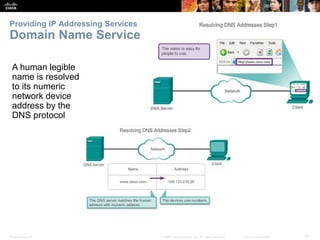
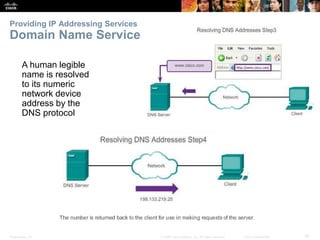
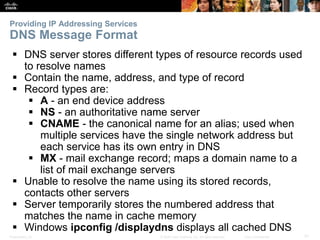
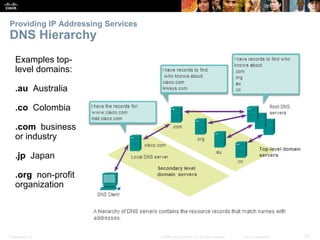
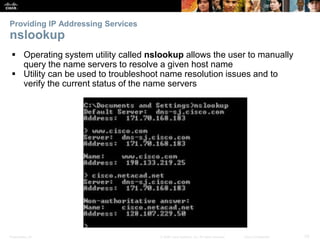
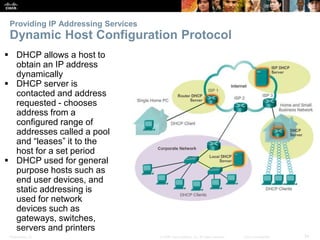
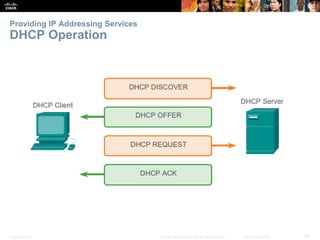
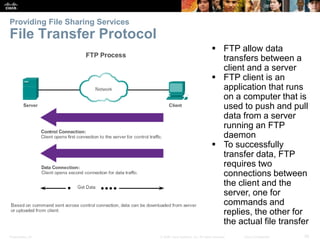
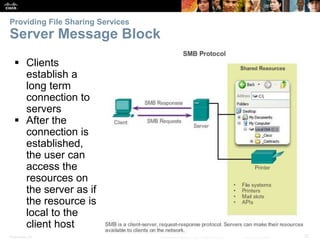
The document discusses the application layer of the OSI model. It describes how application layer protocols like HTTP, SMTP, and FTP allow end-user applications to access network services and interact with other applications. It also covers protocols that provide IP addressing services, such as DNS for translating names to addresses and DHCP for dynamically assigning IP addresses. The document provides examples of common application layer protocols and how they facilitate file transfers, email, and web browsing. It concludes with a high-level summary of the key roles of the application layer.