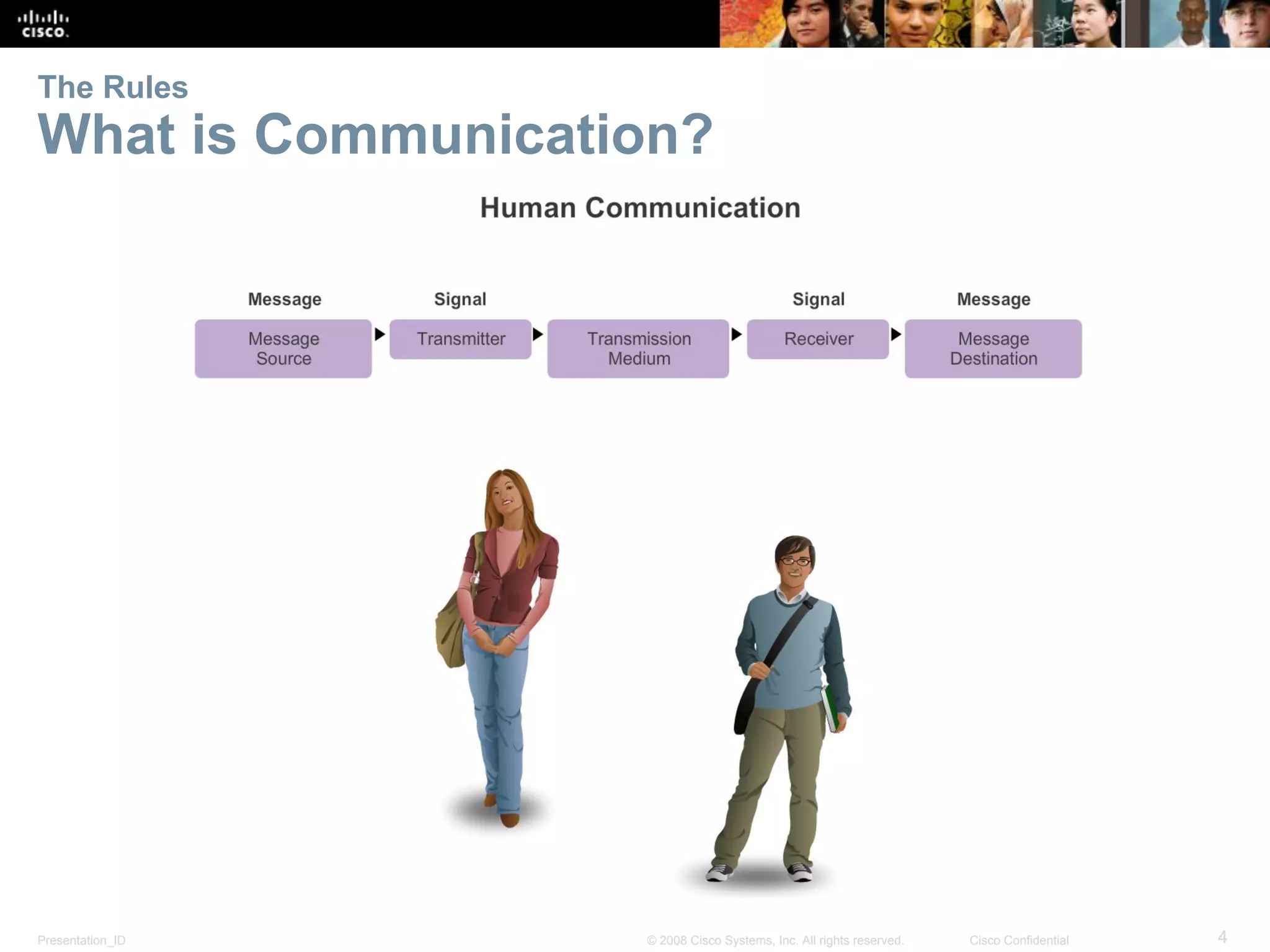
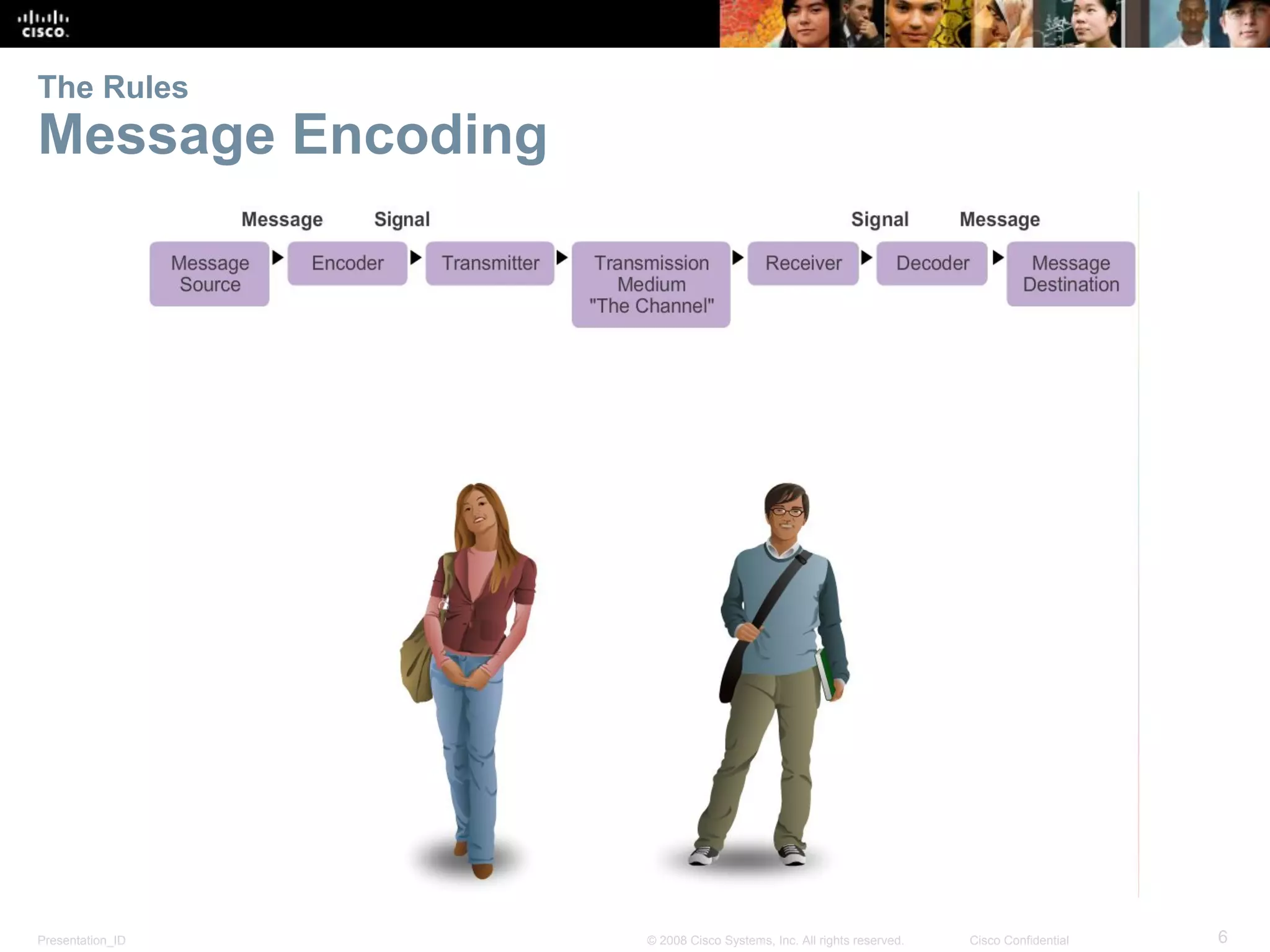
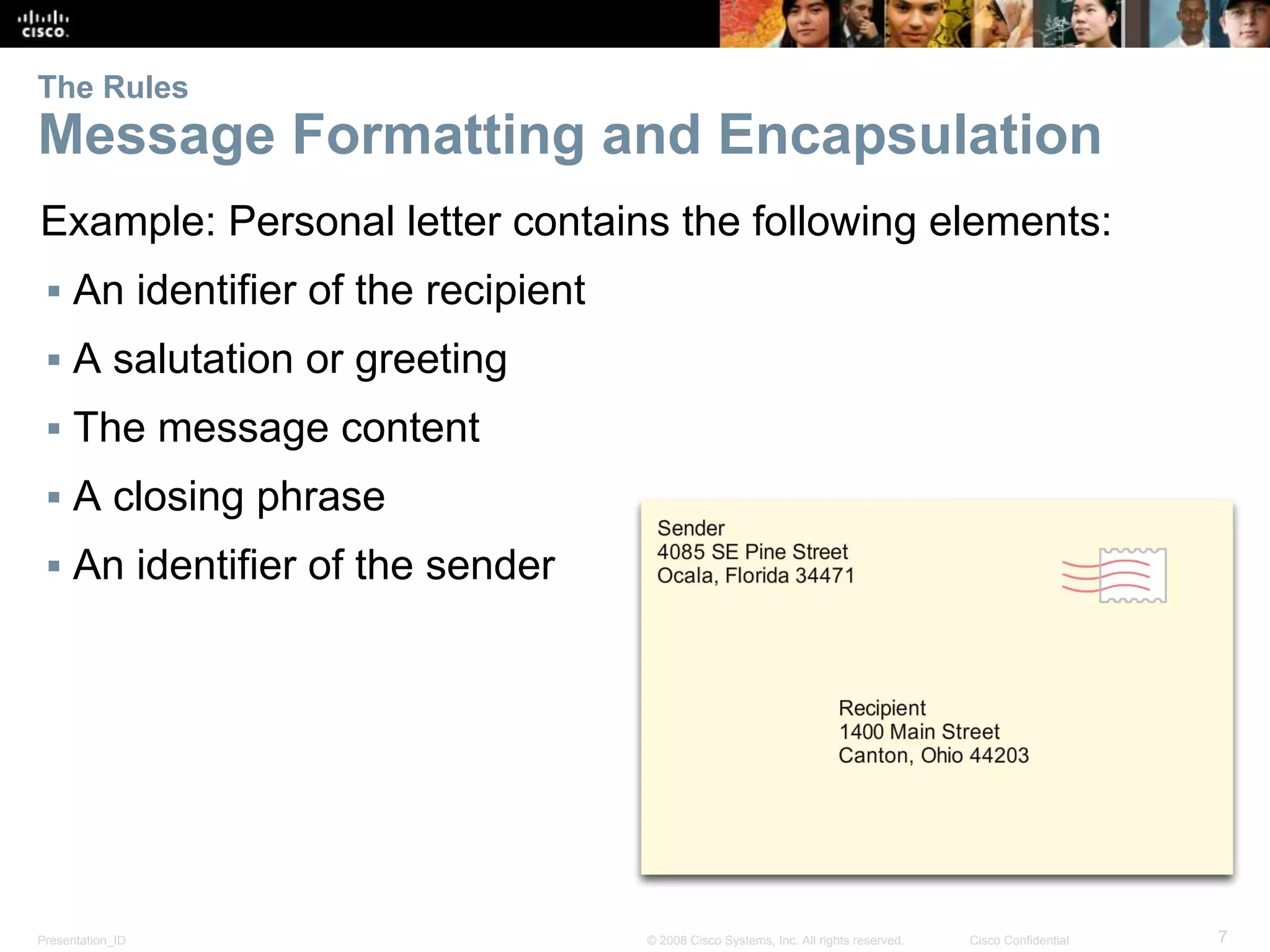
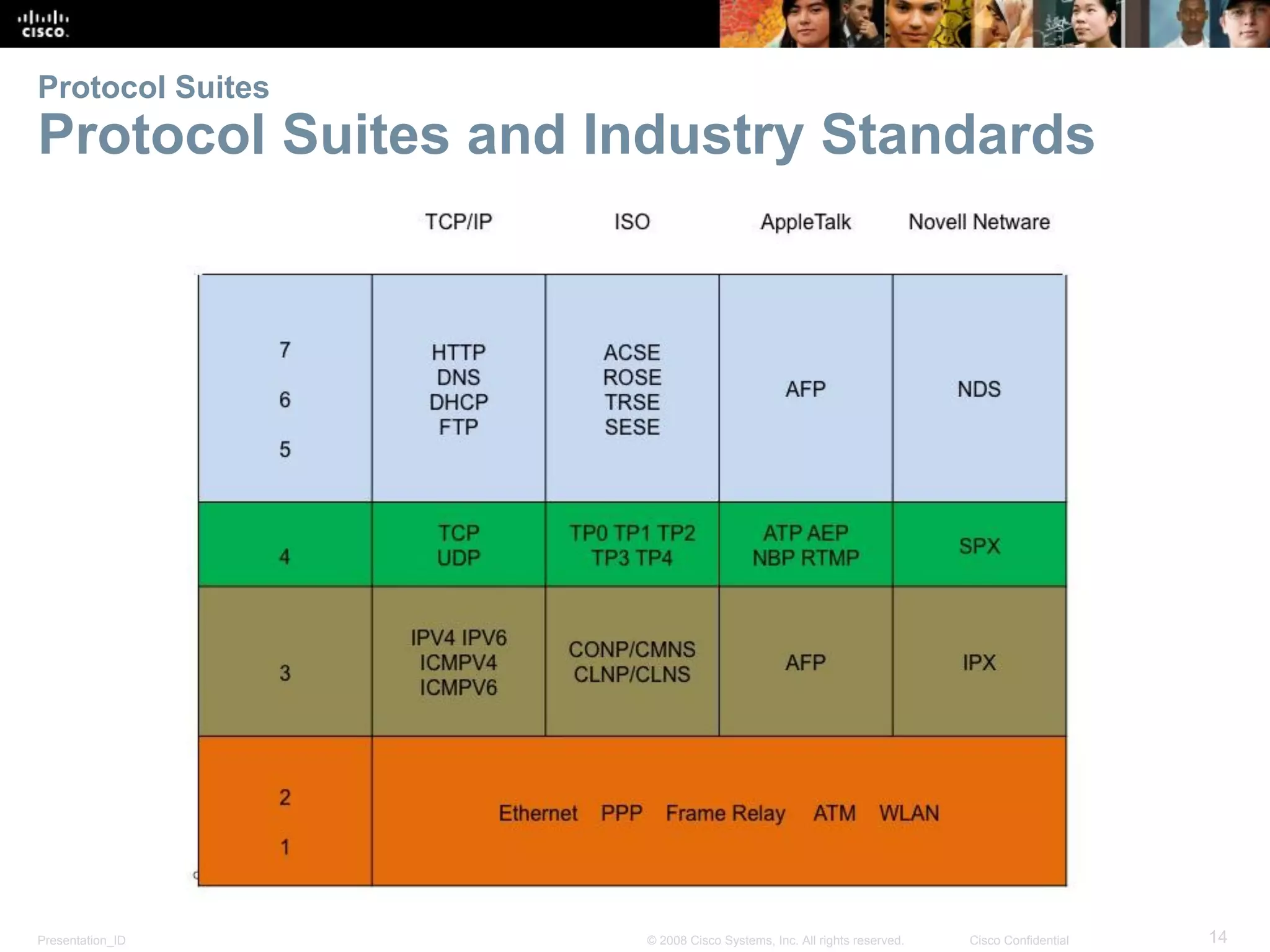
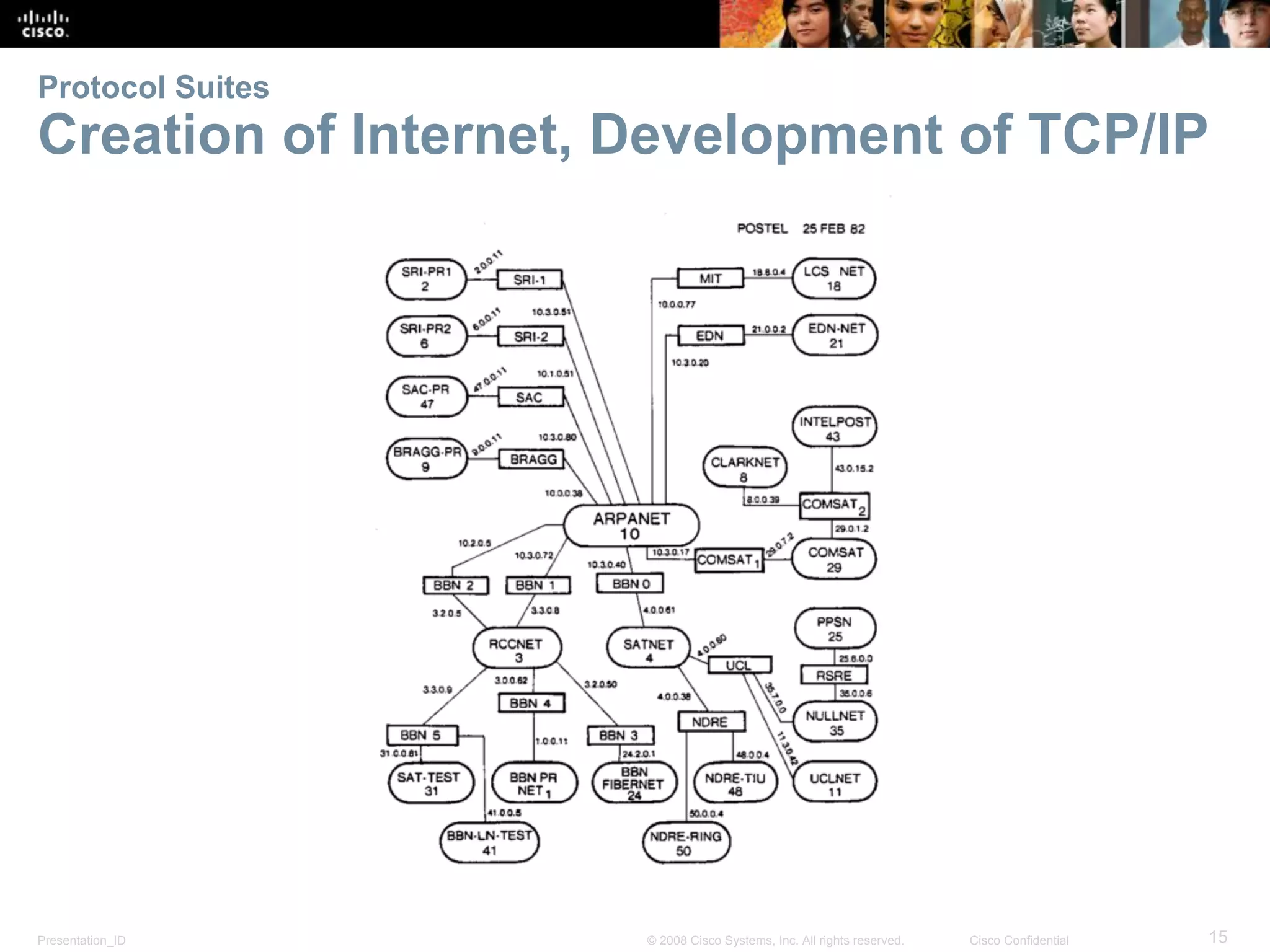
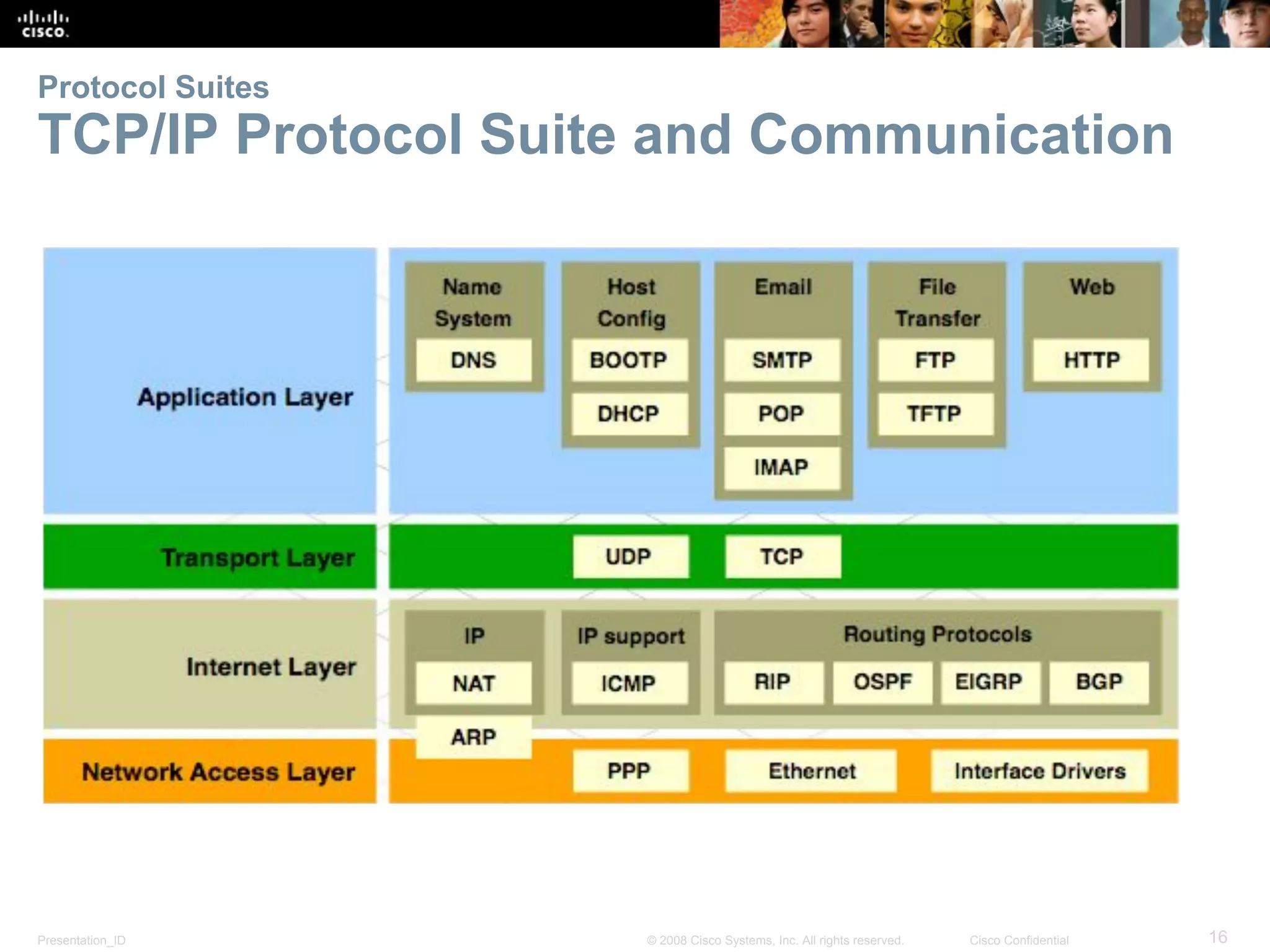
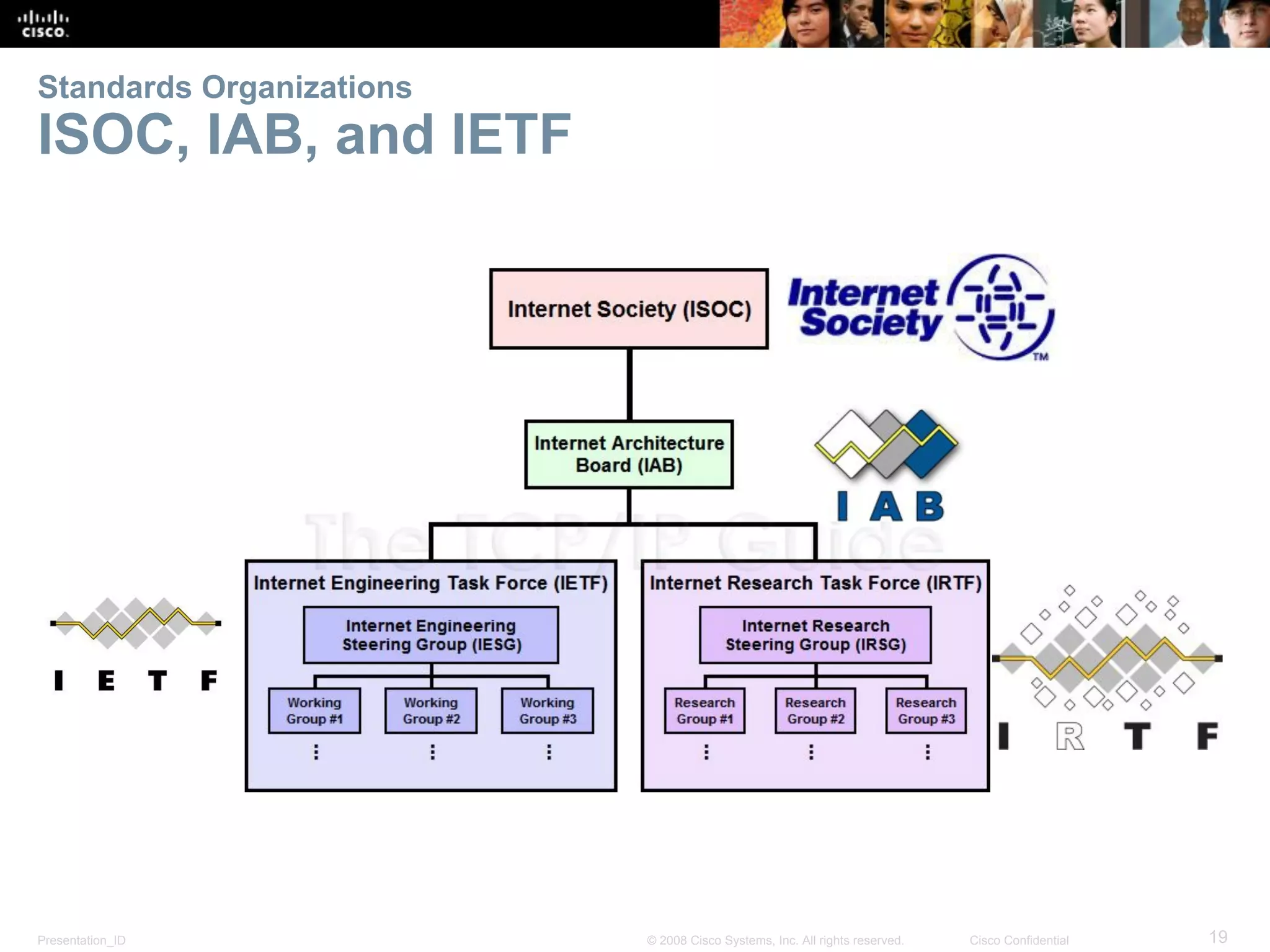
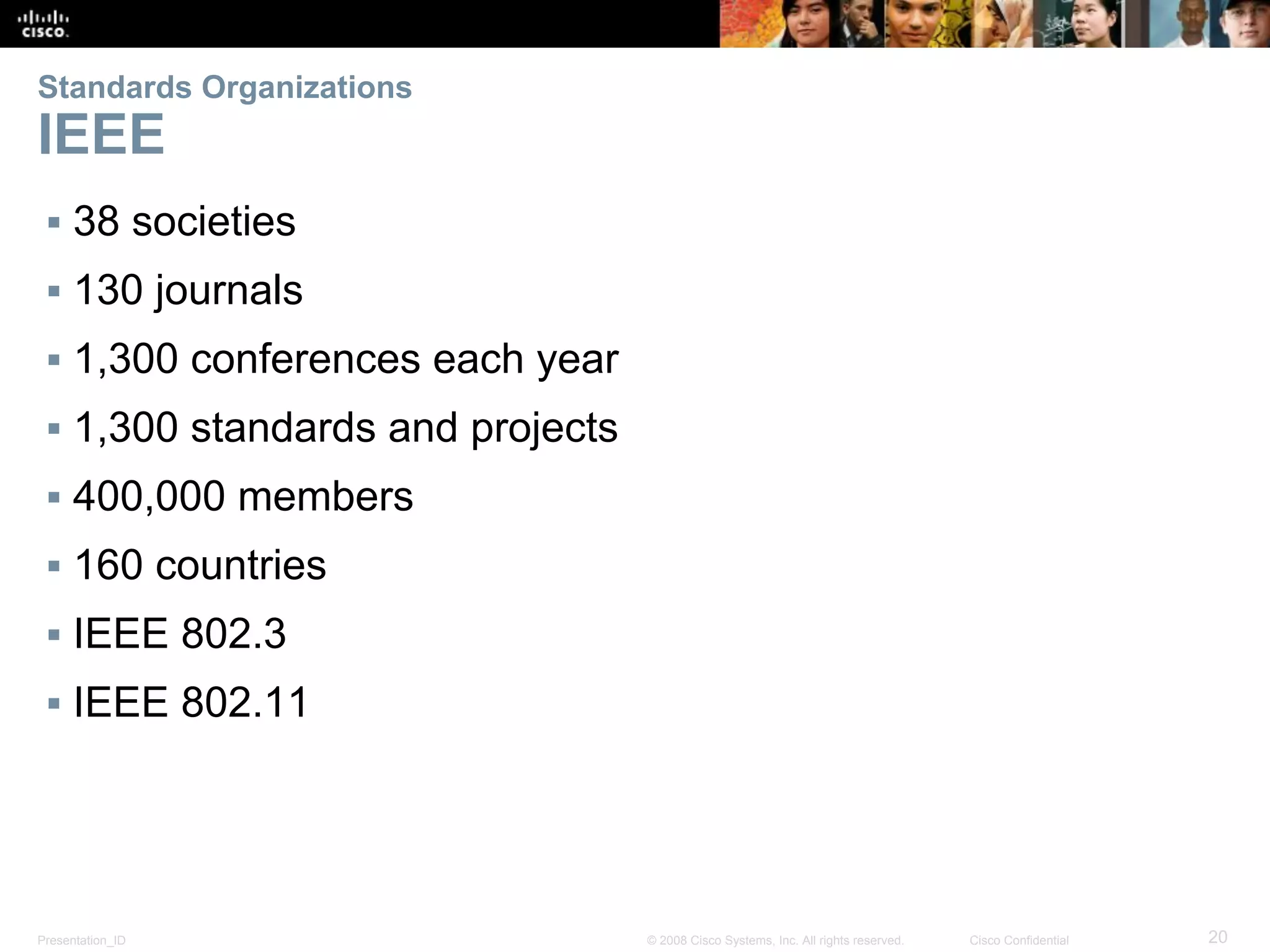
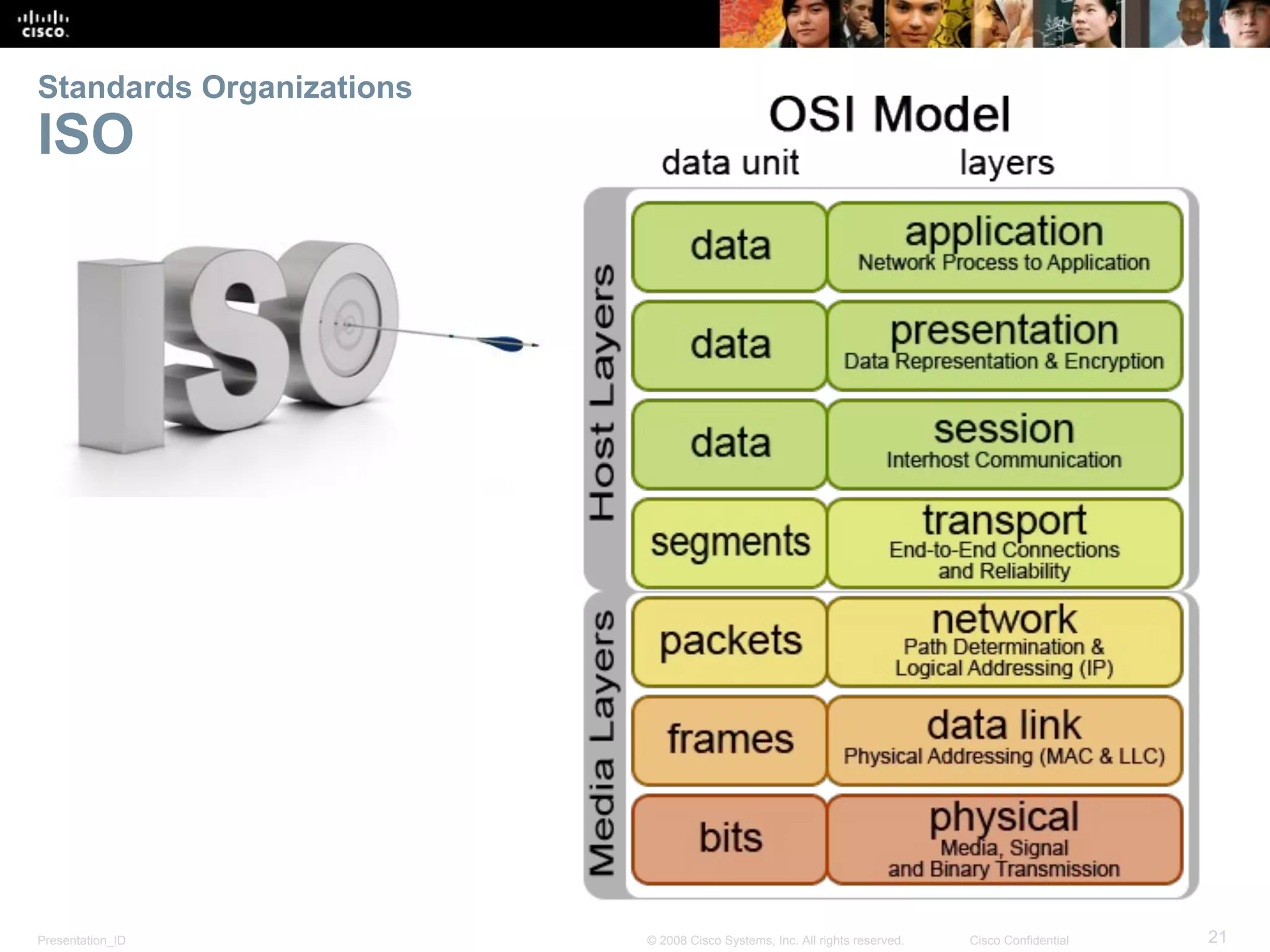
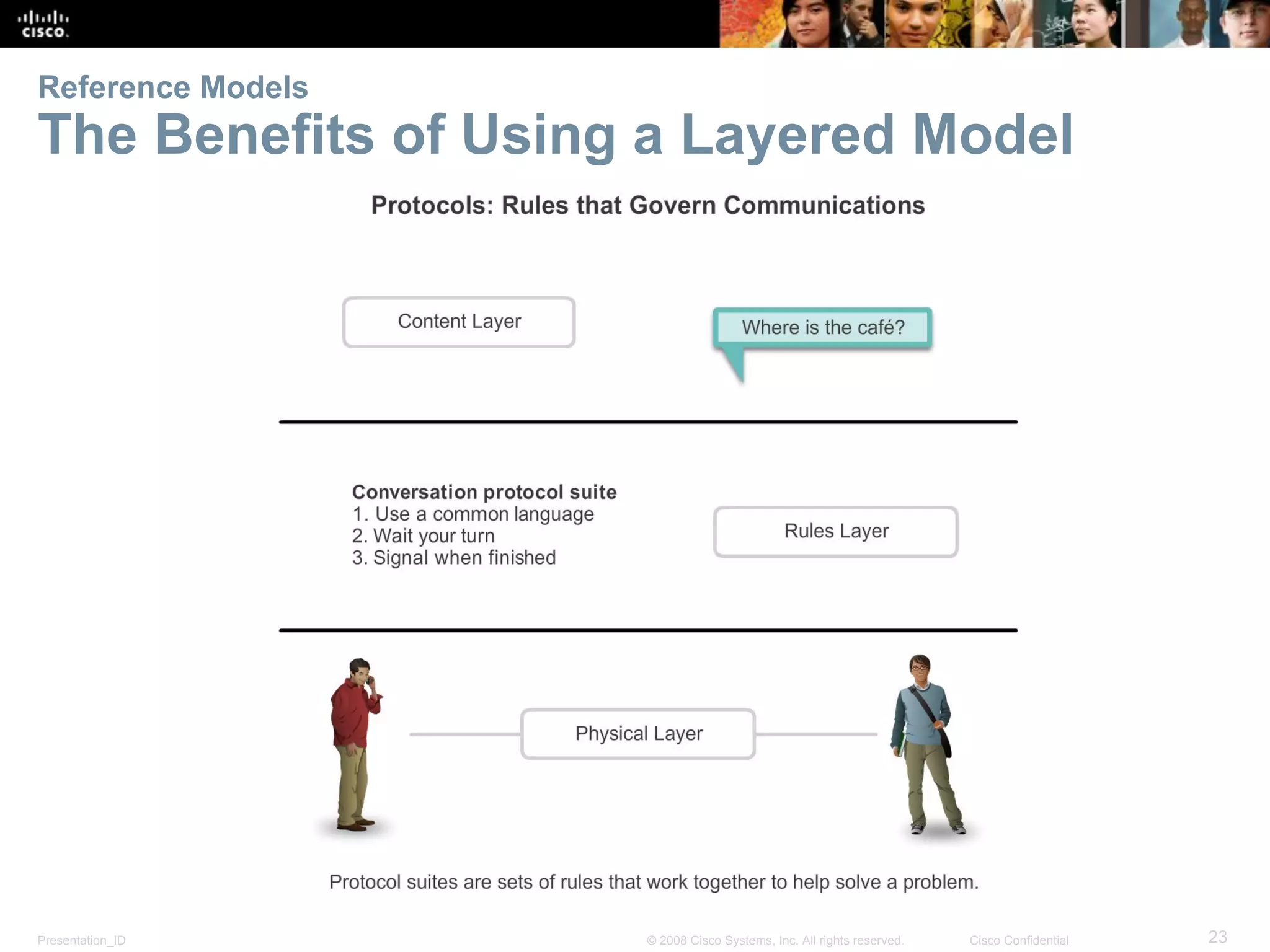
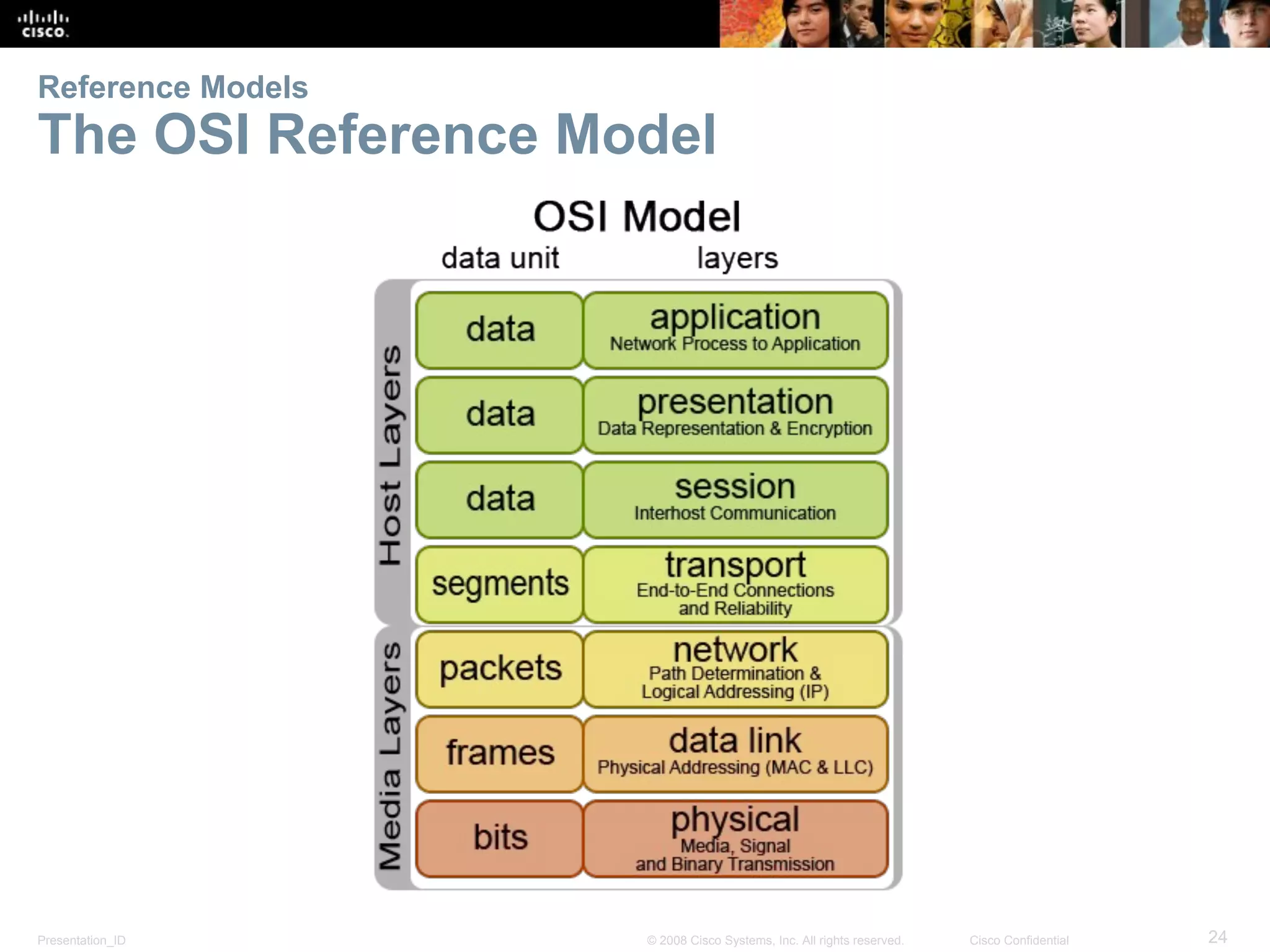
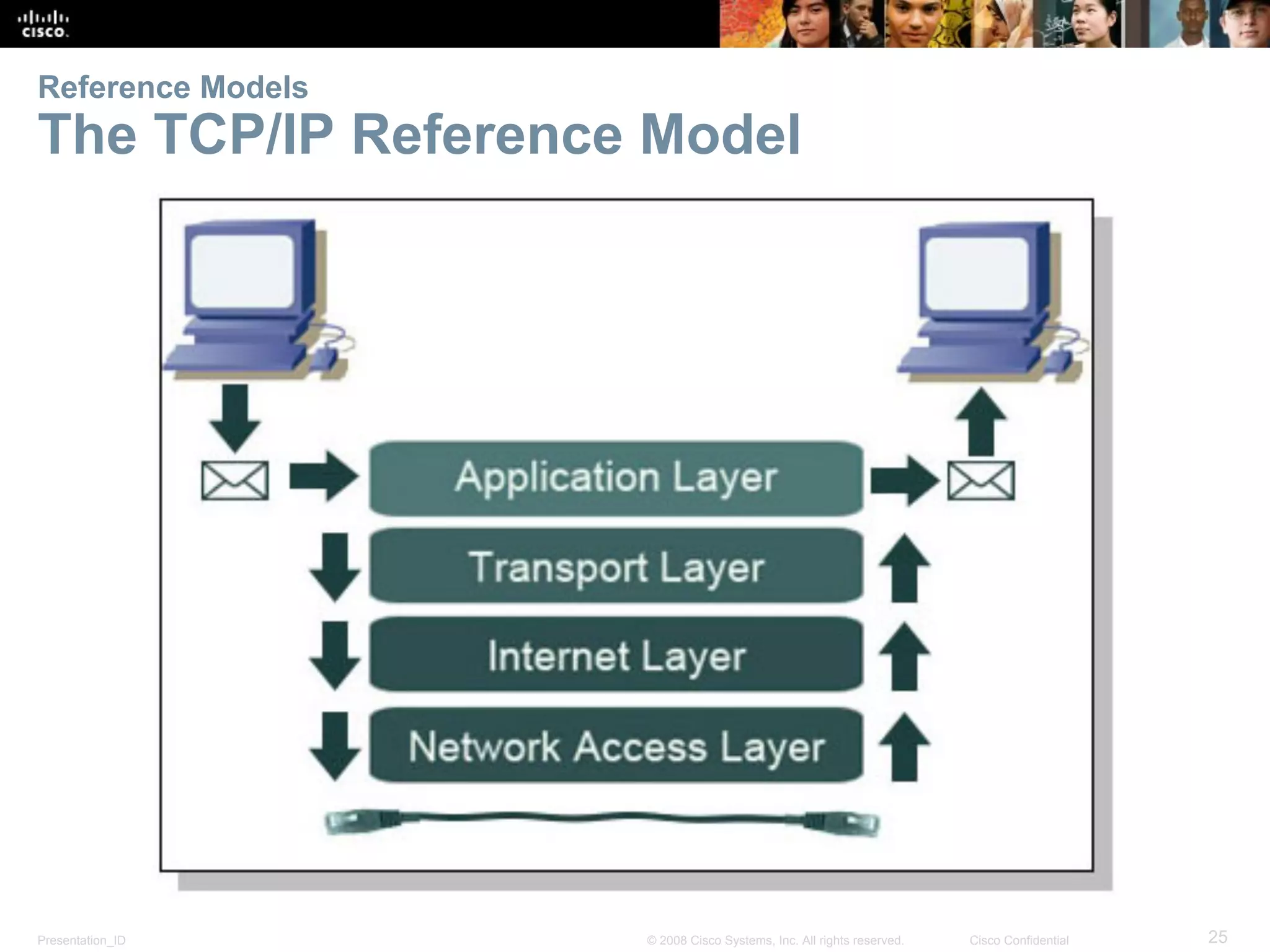
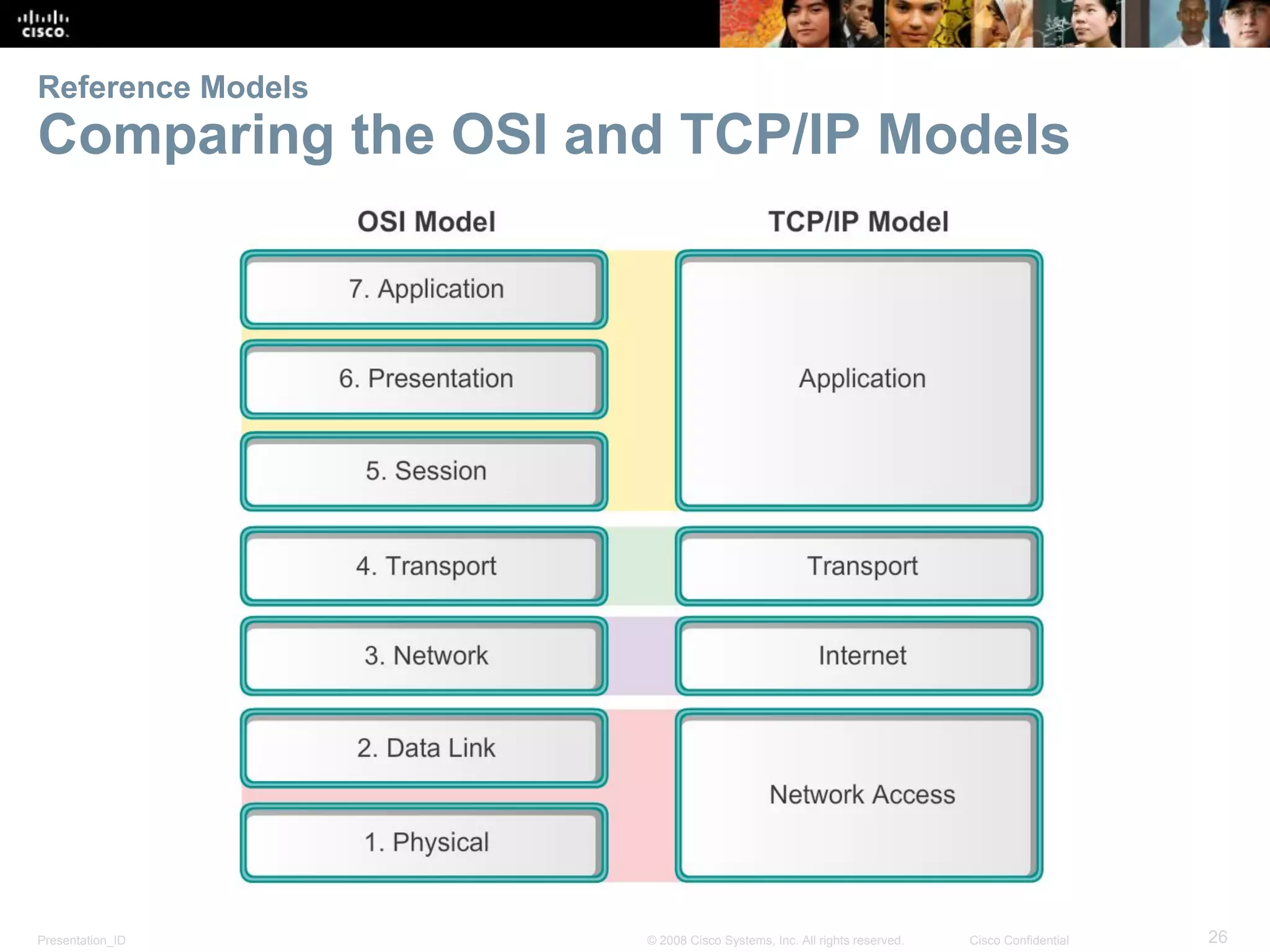
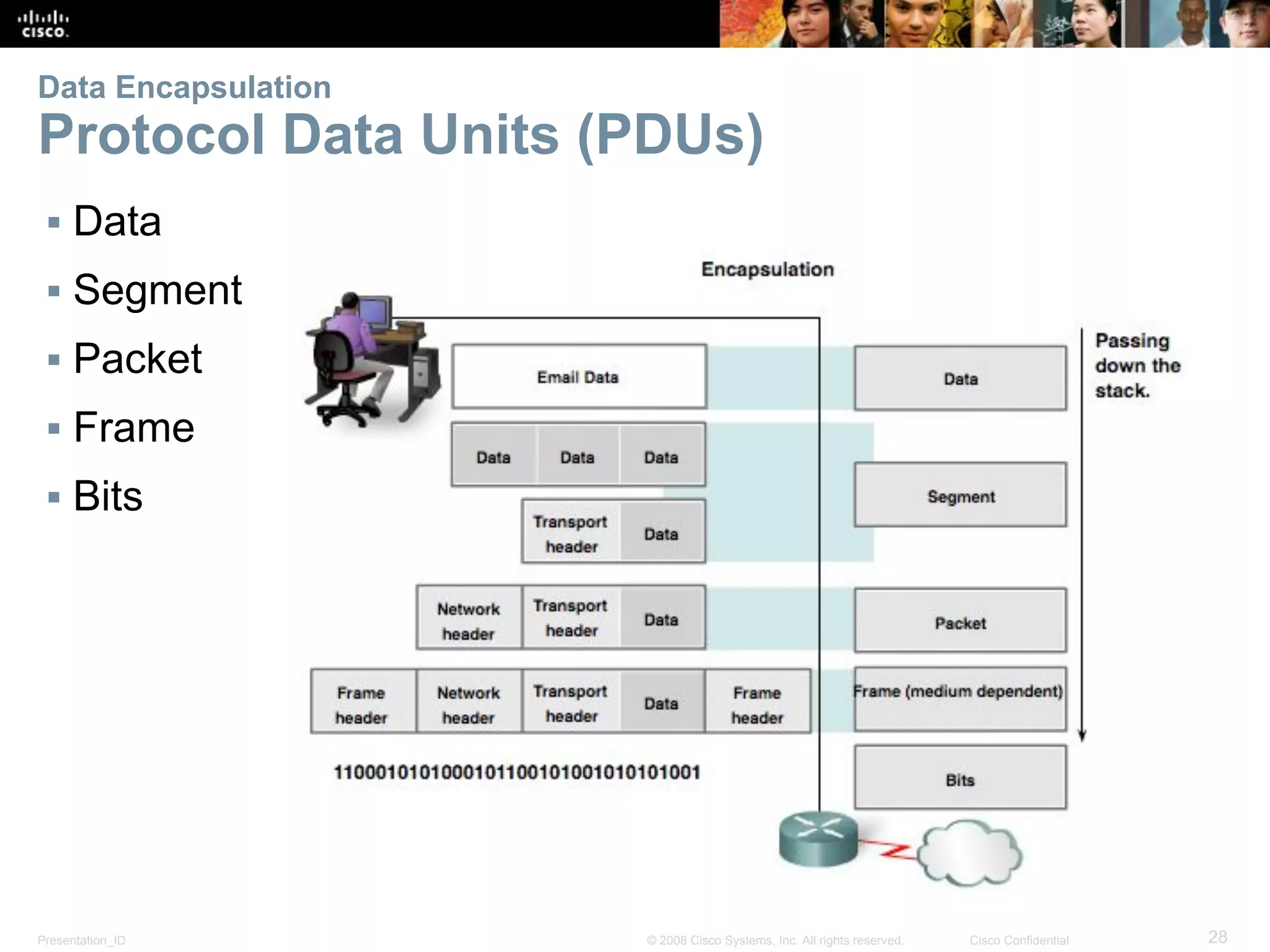
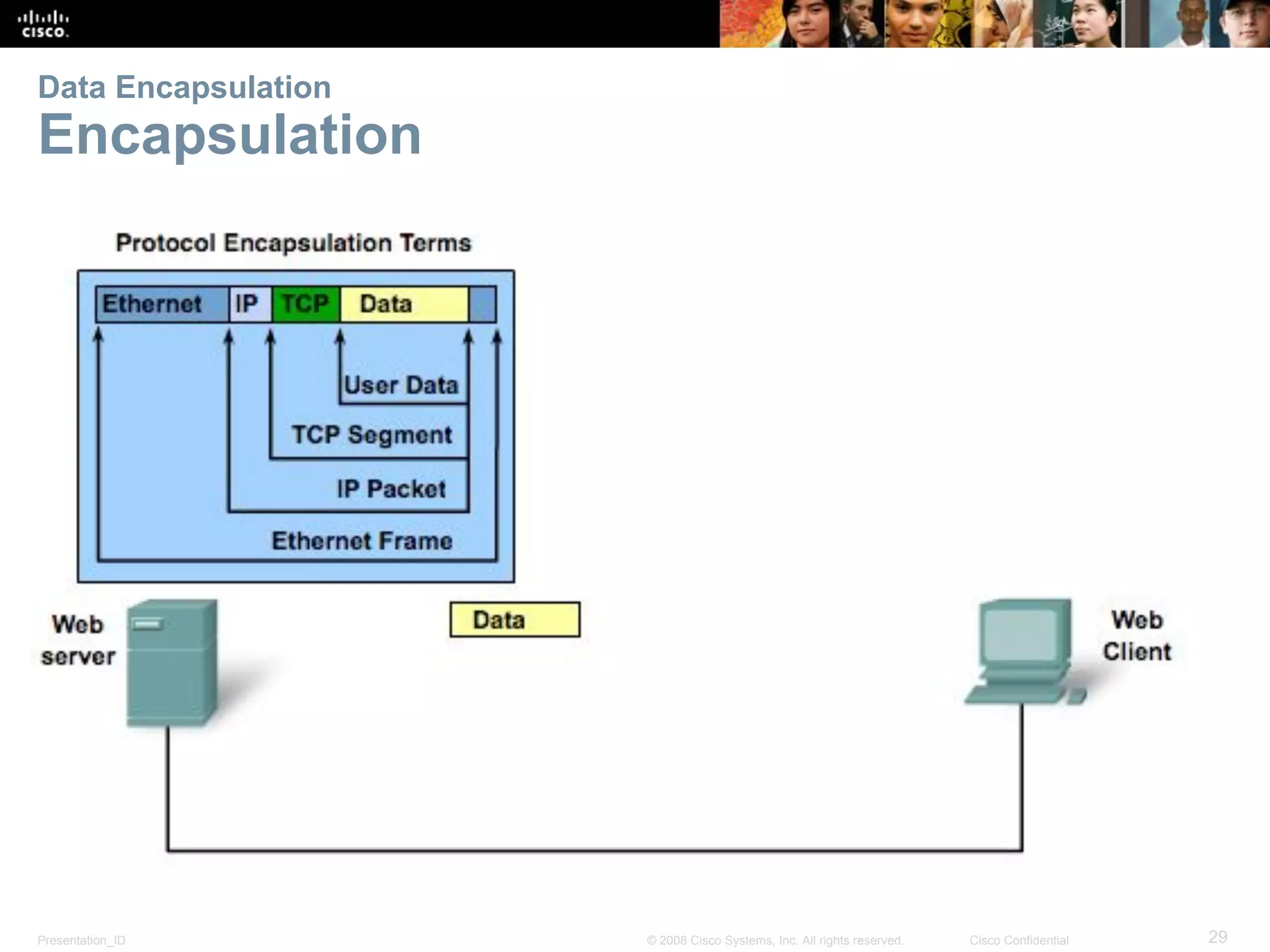
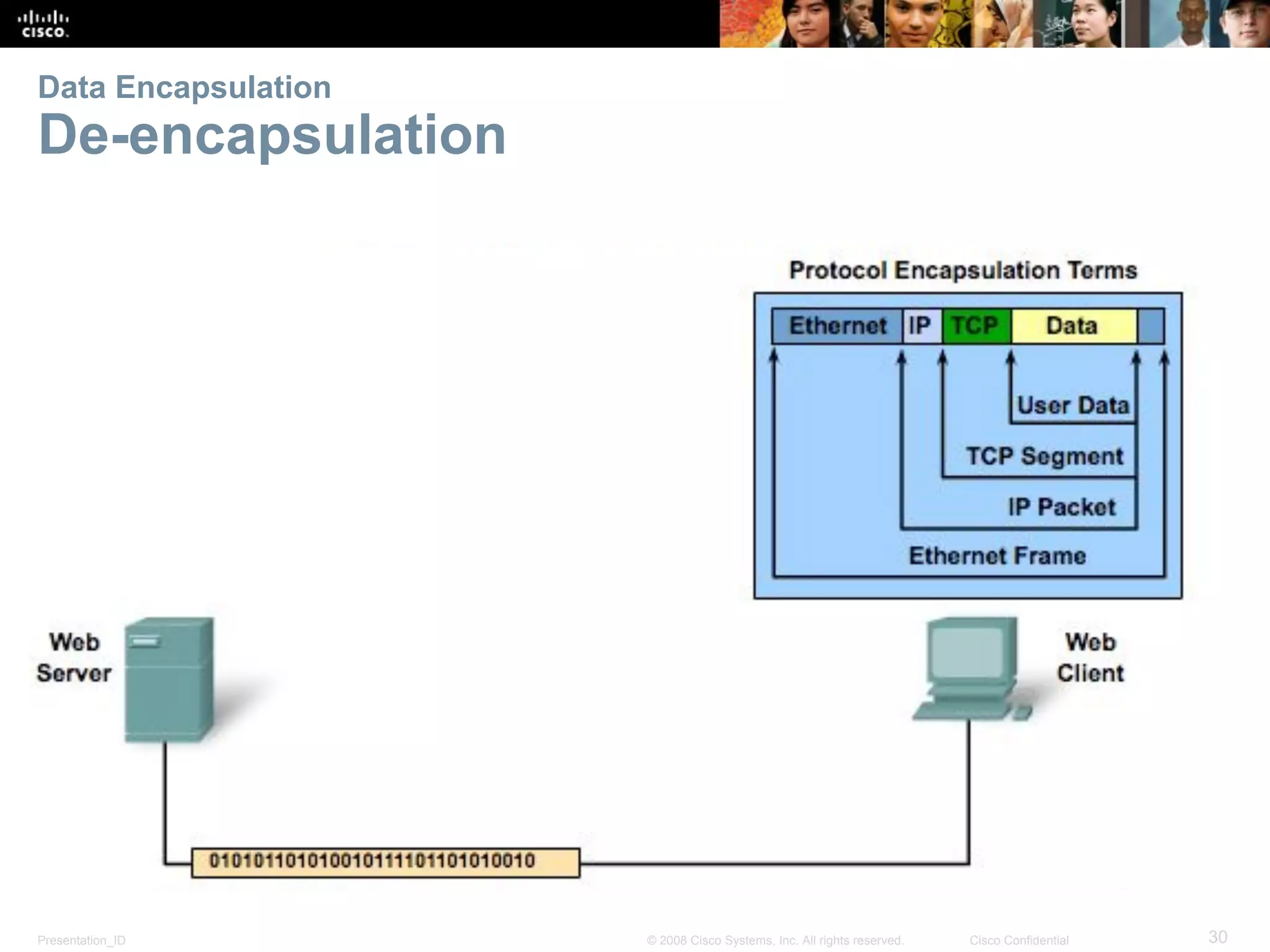
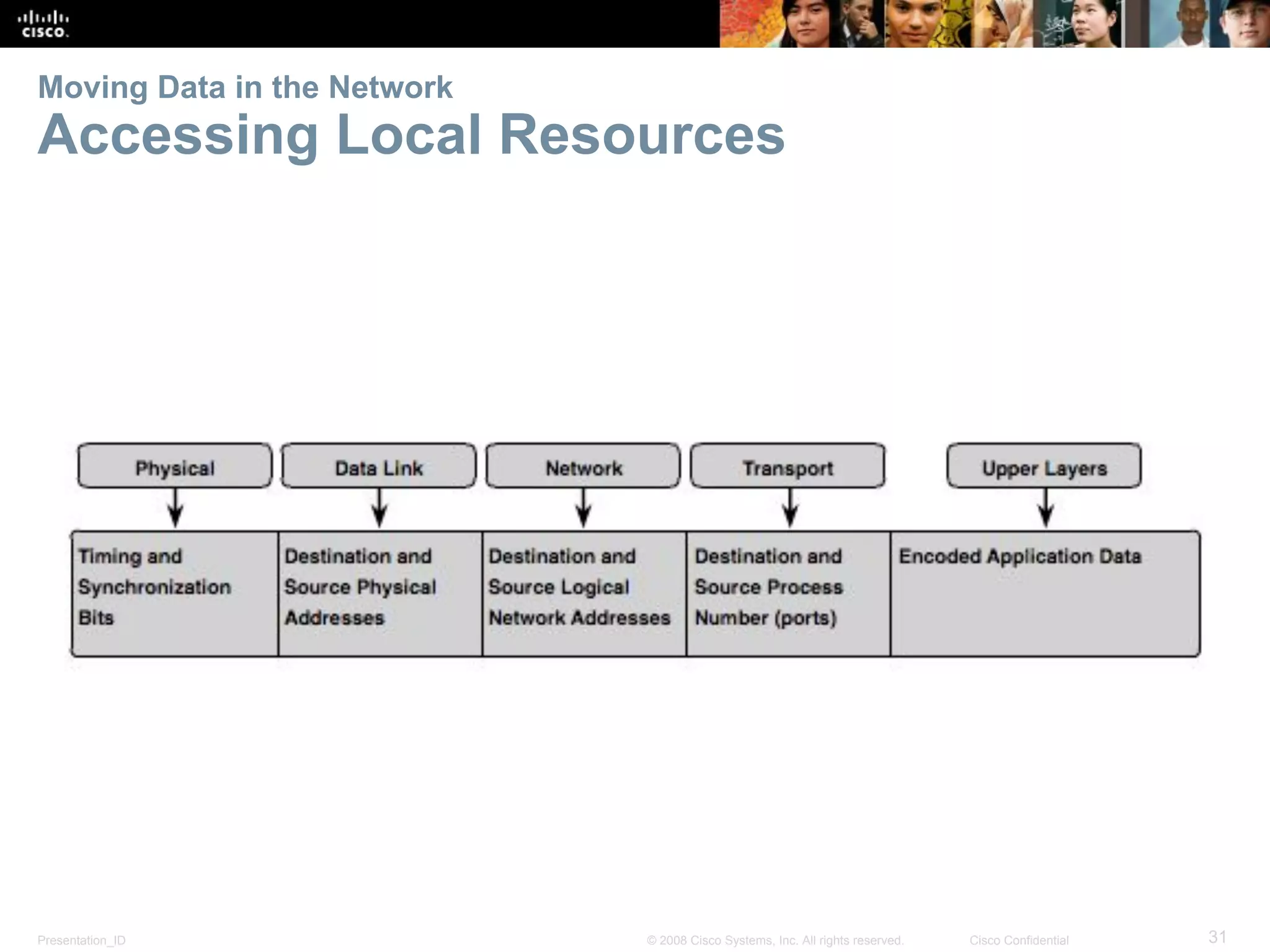
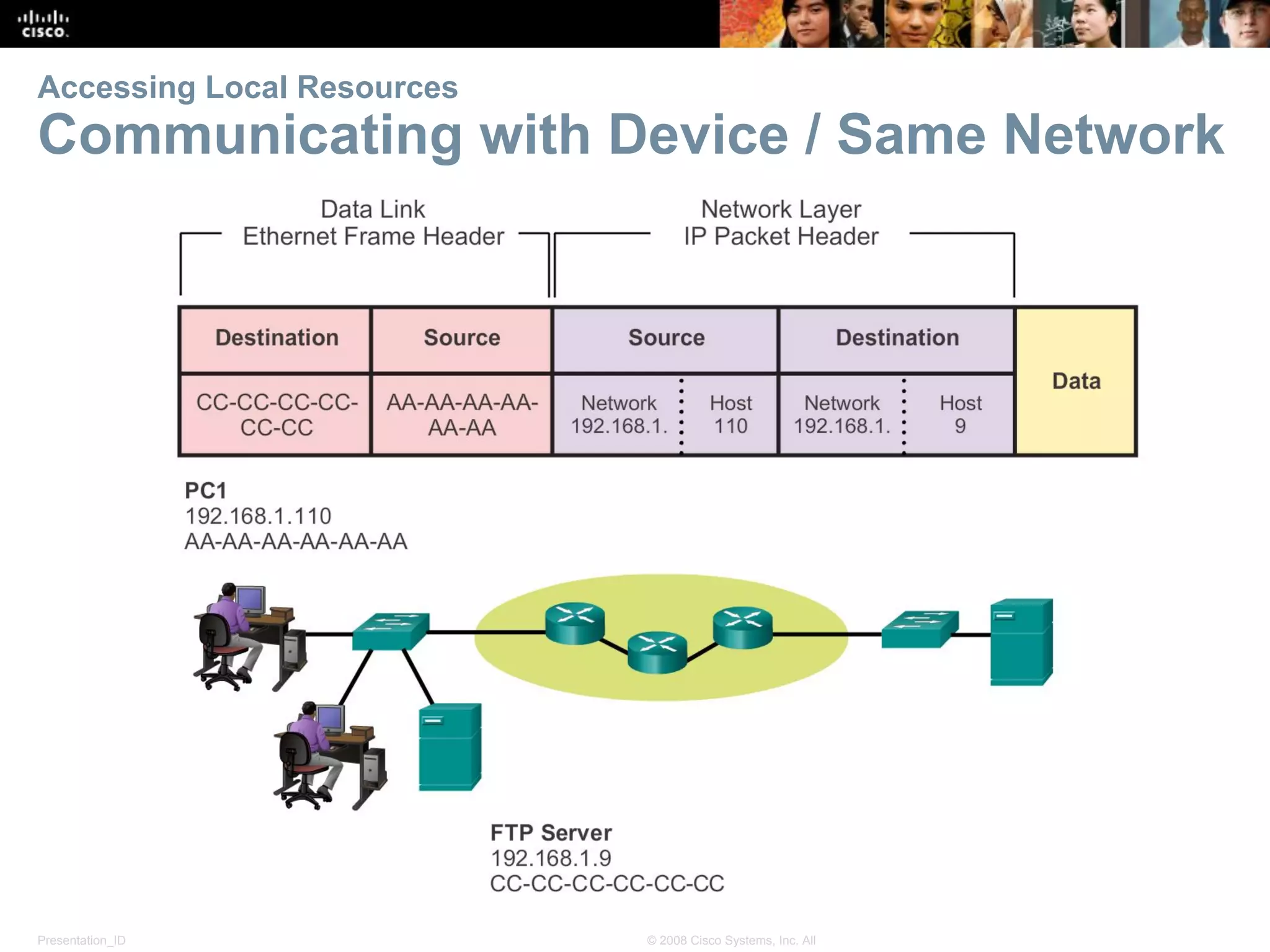
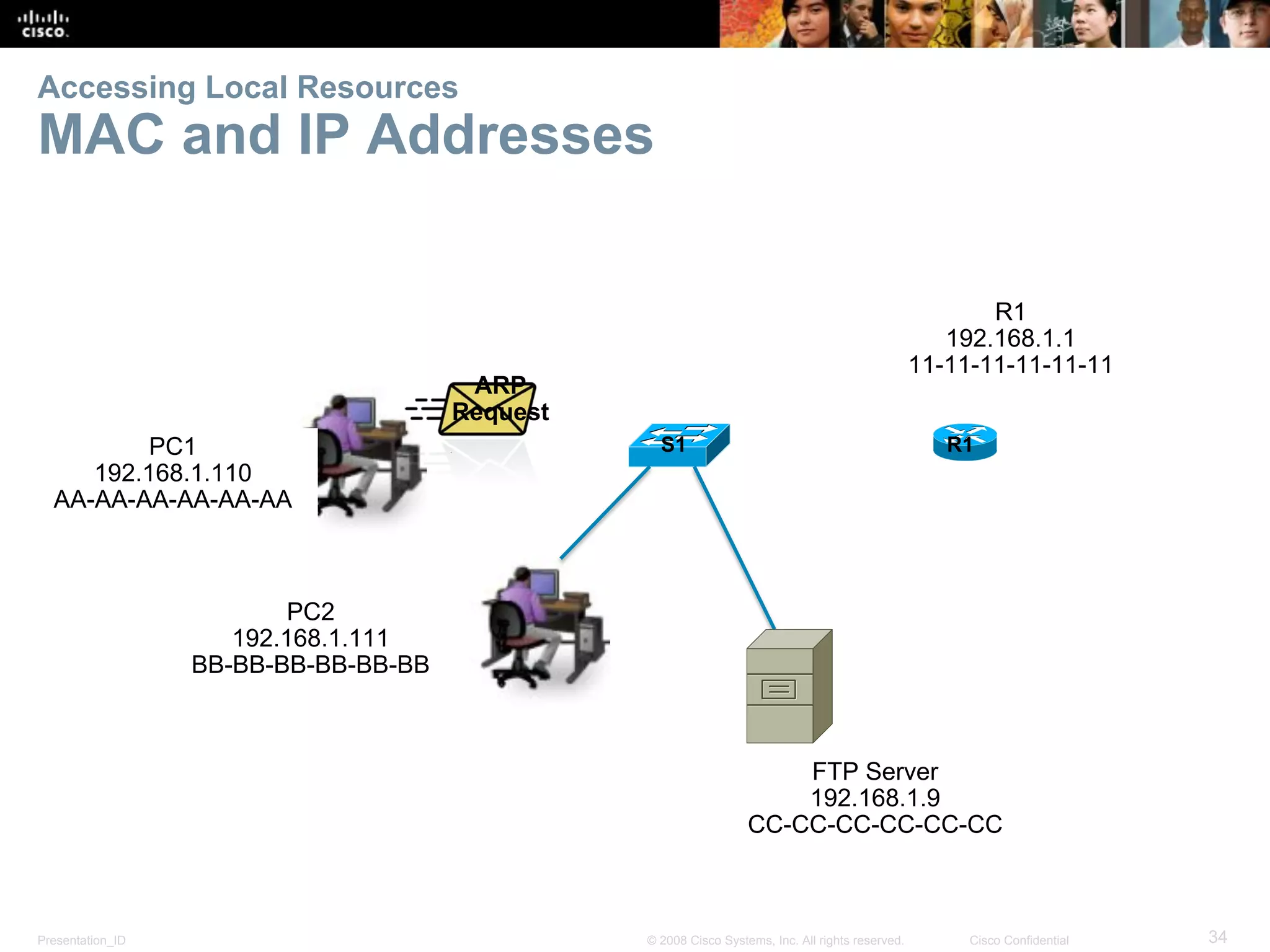
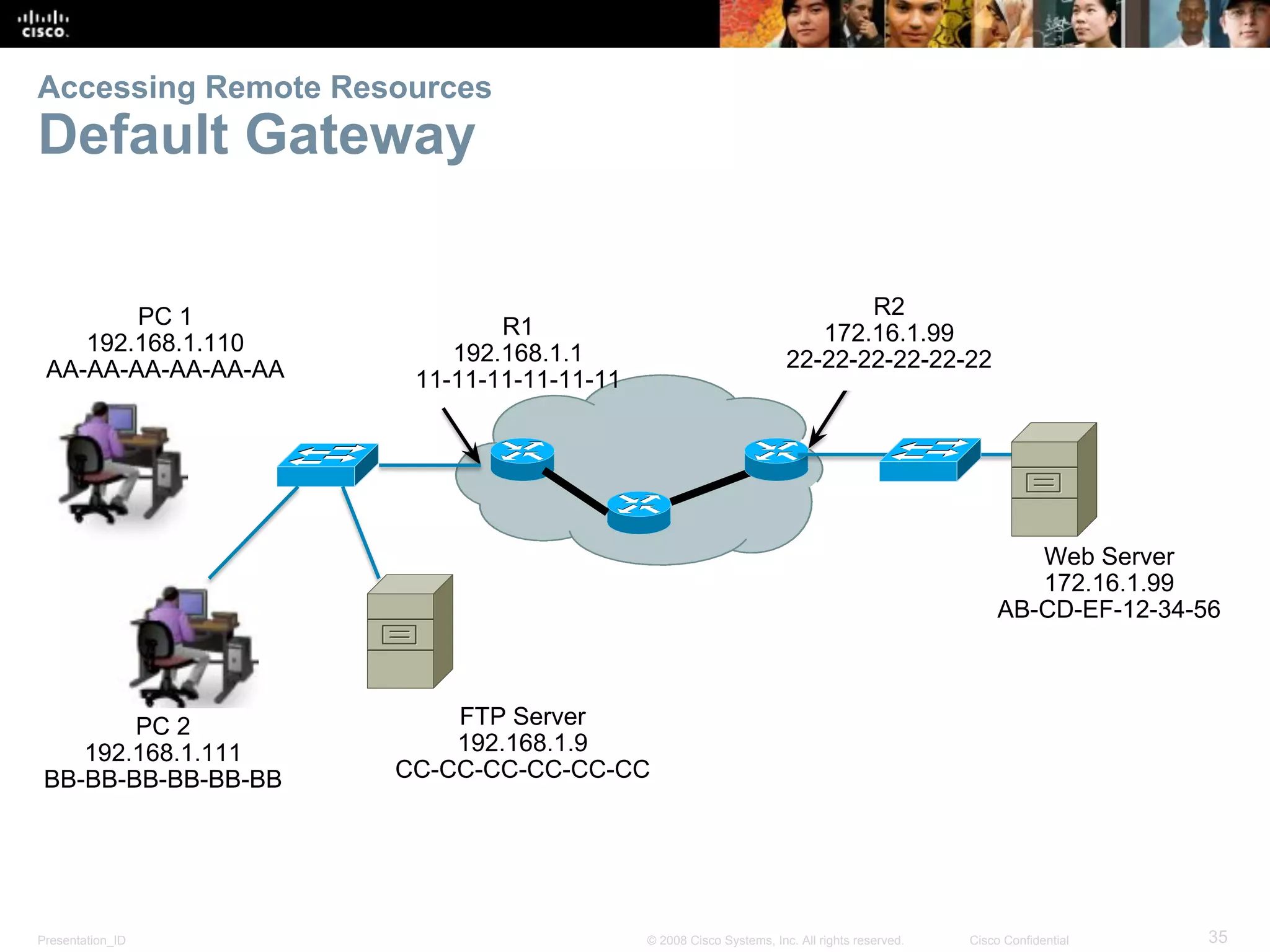
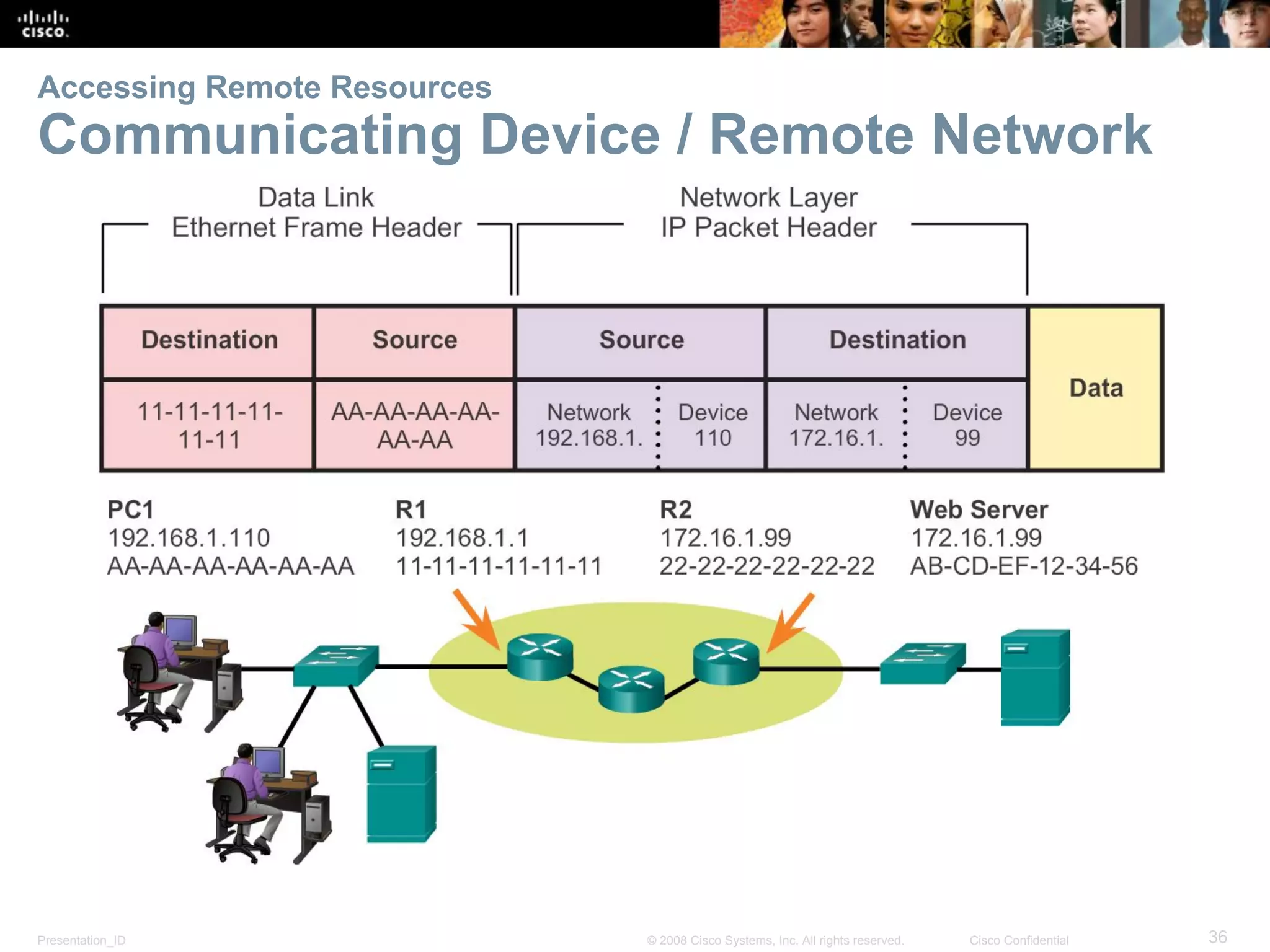
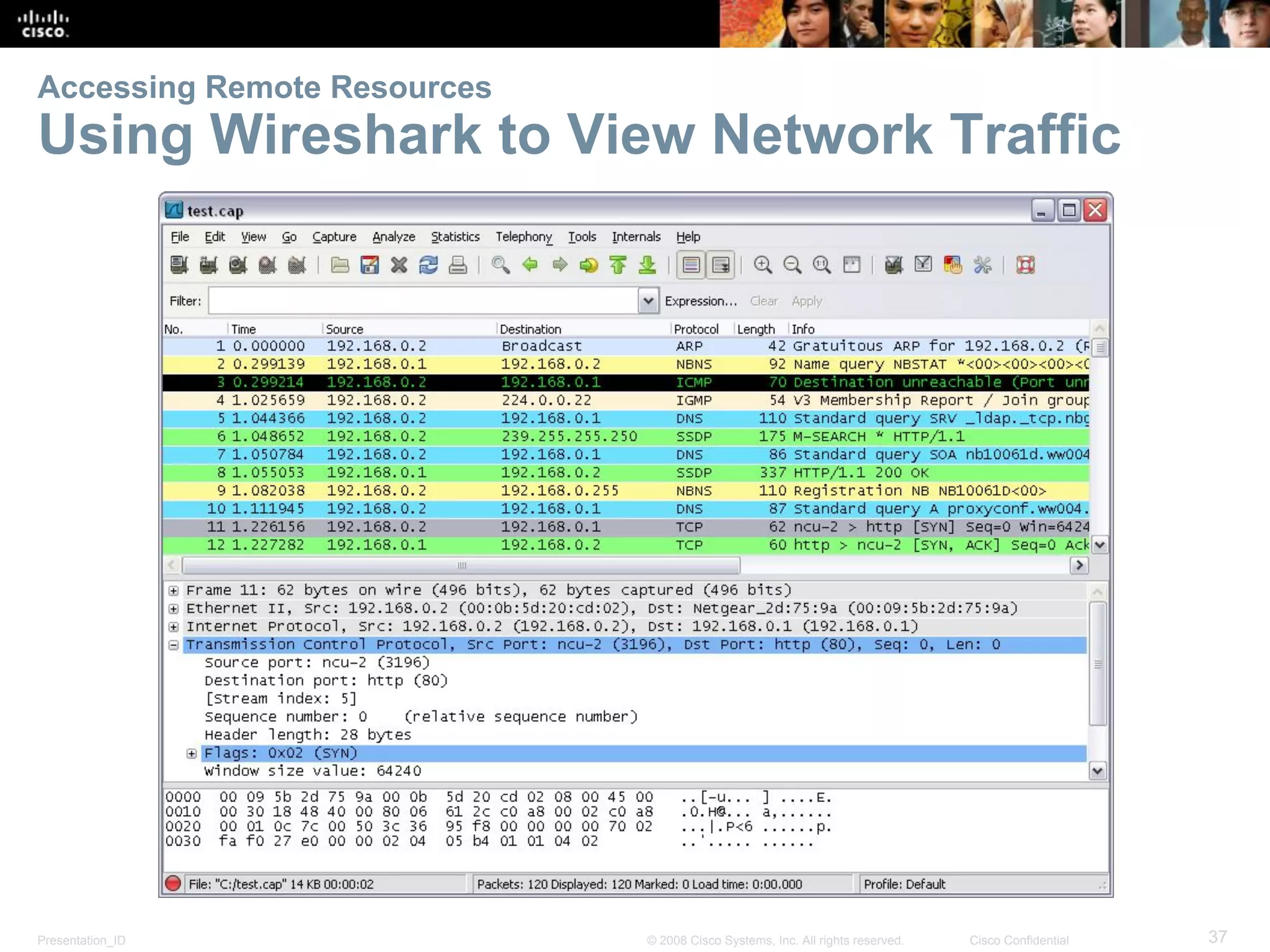
This document discusses network protocols and communications. It explains that protocols establish rules for communication between devices. Standards organizations create common protocols to ensure interoperability. The OSI and TCP/IP models describe how data is encapsulated when moving through a network in layers. Devices locate resources on both local networks using addresses, and on remote networks by going through a default gateway.