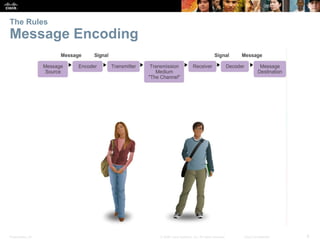
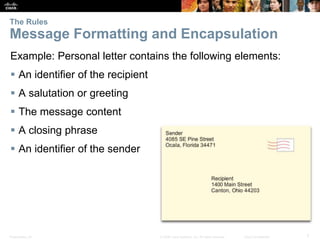
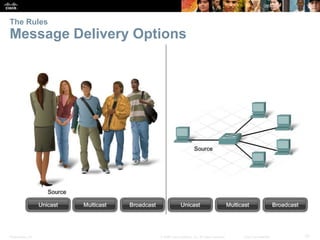
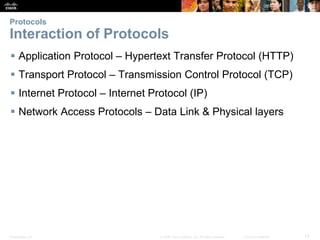
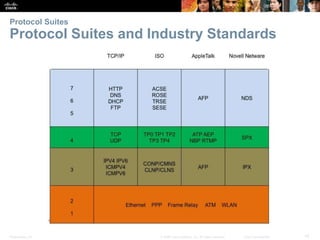
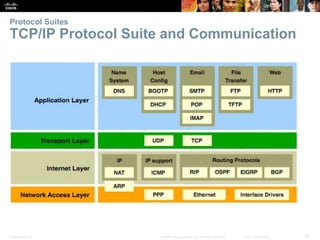
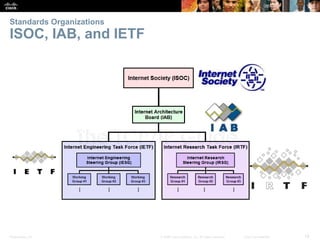
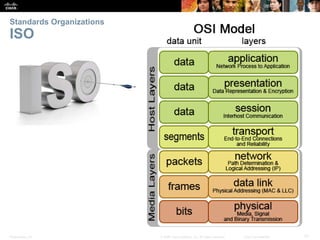
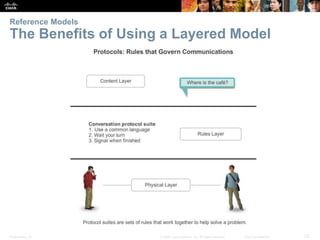
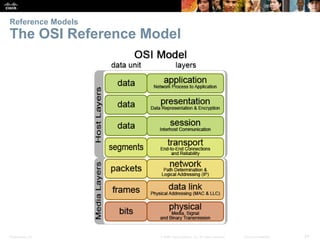
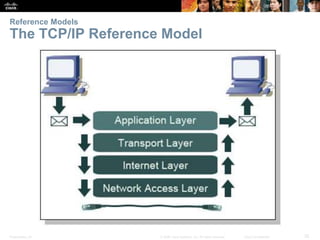
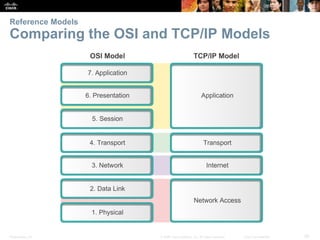
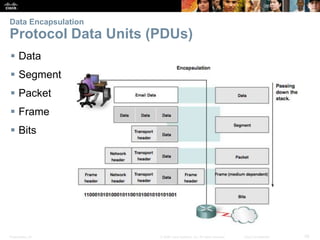
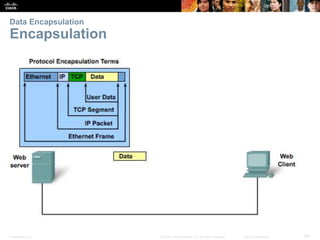
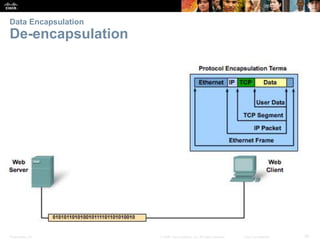
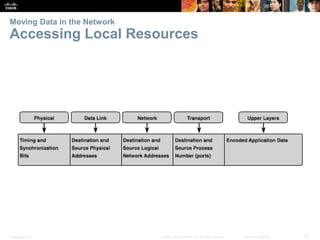
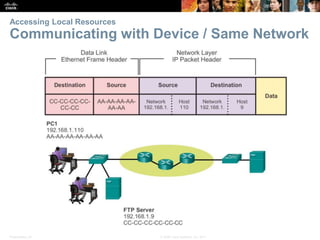
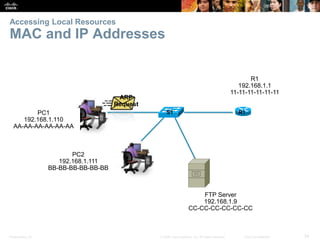
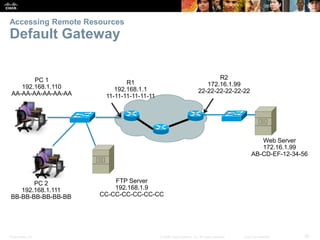
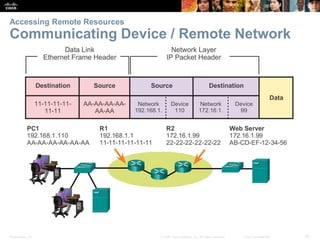
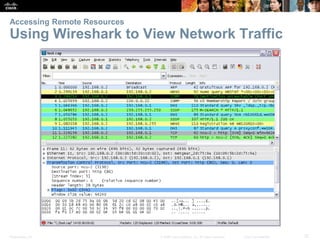
This document summarizes a chapter about network protocols and communications. It discusses how rules and protocols facilitate communication between networked devices. Key points covered include the roles of standards organizations in establishing protocols, how data is encapsulated as it moves through network layers, and how devices locate resources on both local area networks and remote networks using protocols like TCP/IP and addressing schemes.