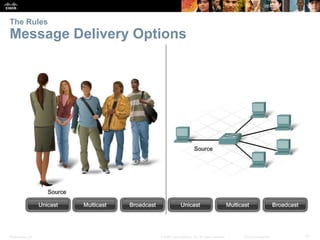
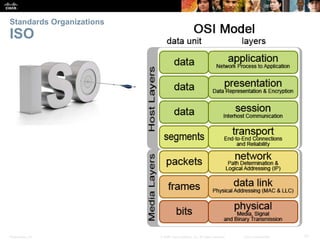
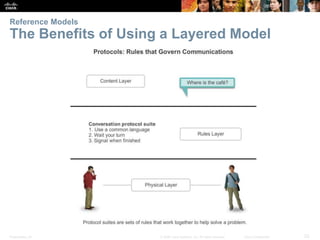
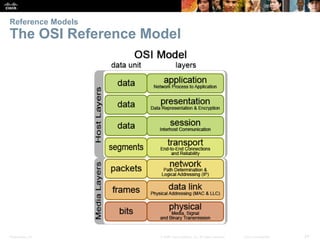
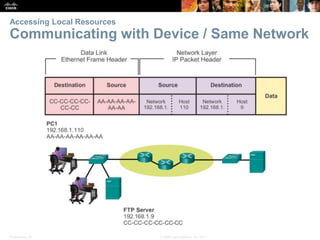
This document discusses network protocols and communications. It covers how rules facilitate communication between devices, the role of protocols and standards organizations in ensuring interoperability, and how devices access local and remote resources on a network. Specific topics covered include network protocols, protocol suites, standards bodies, data encapsulation, and using network models like OSI and TCP/IP. The chapter aims to explain the key concepts around how data is transmitted over a network according to common protocols and standards.