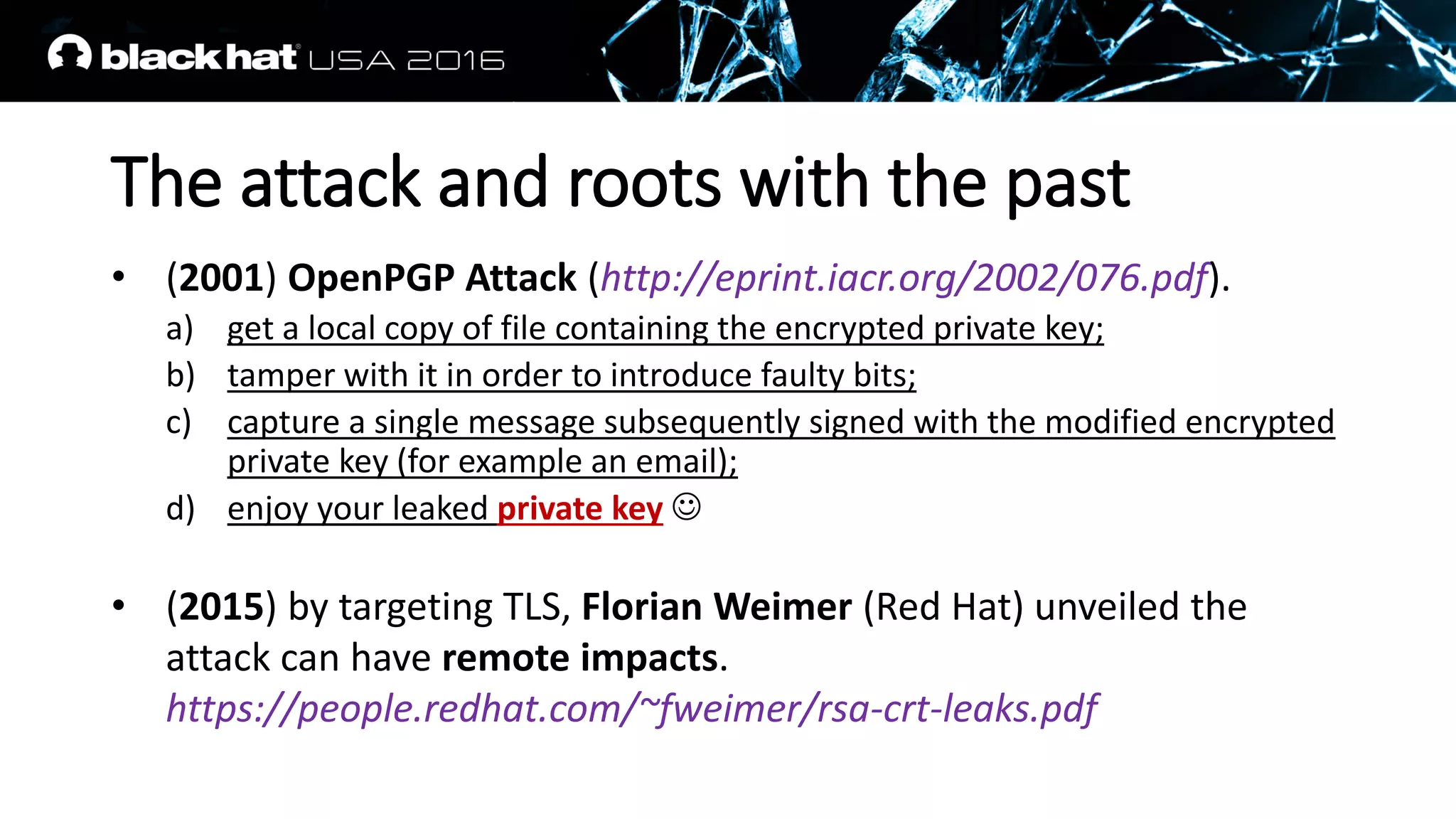
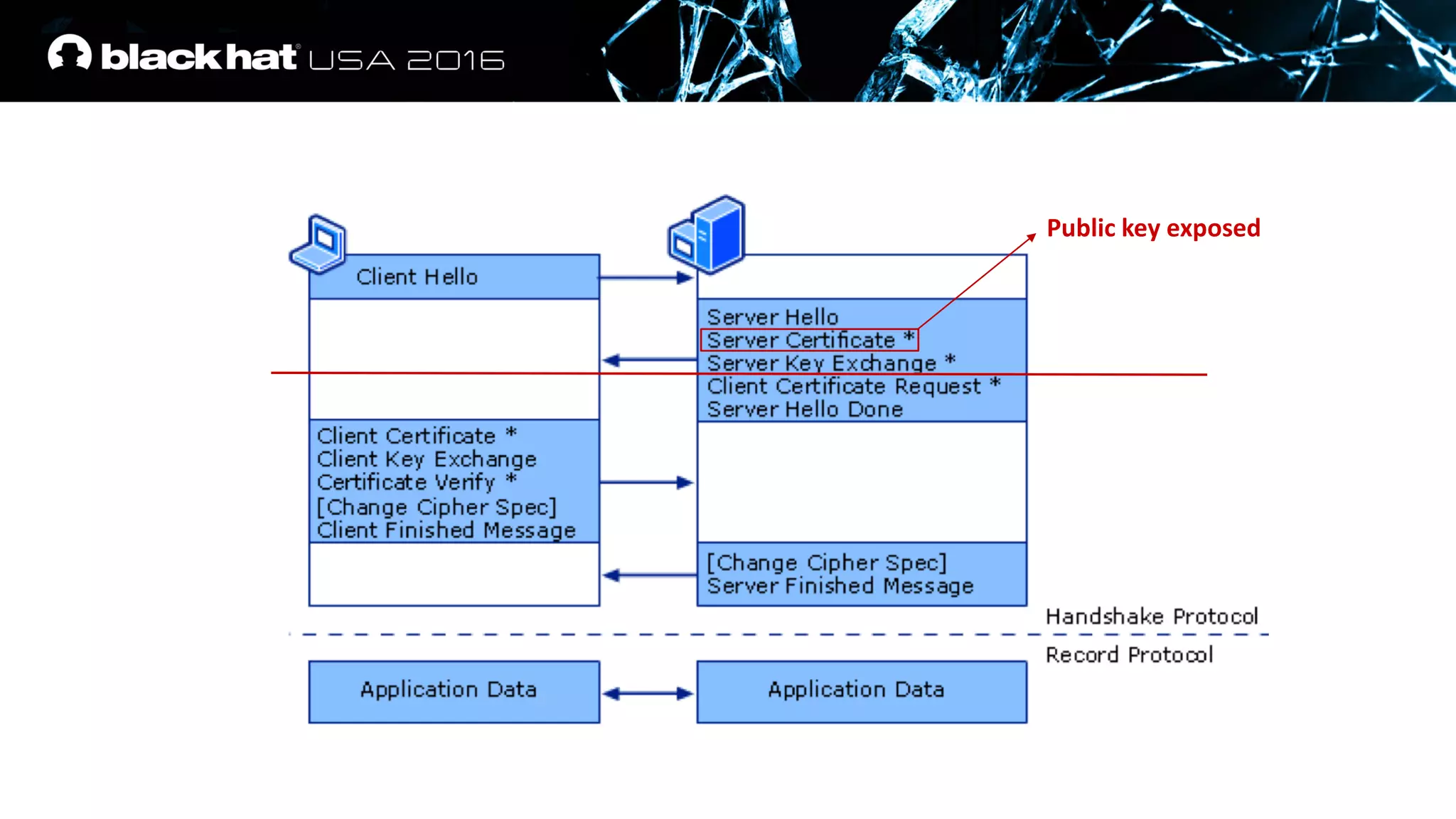
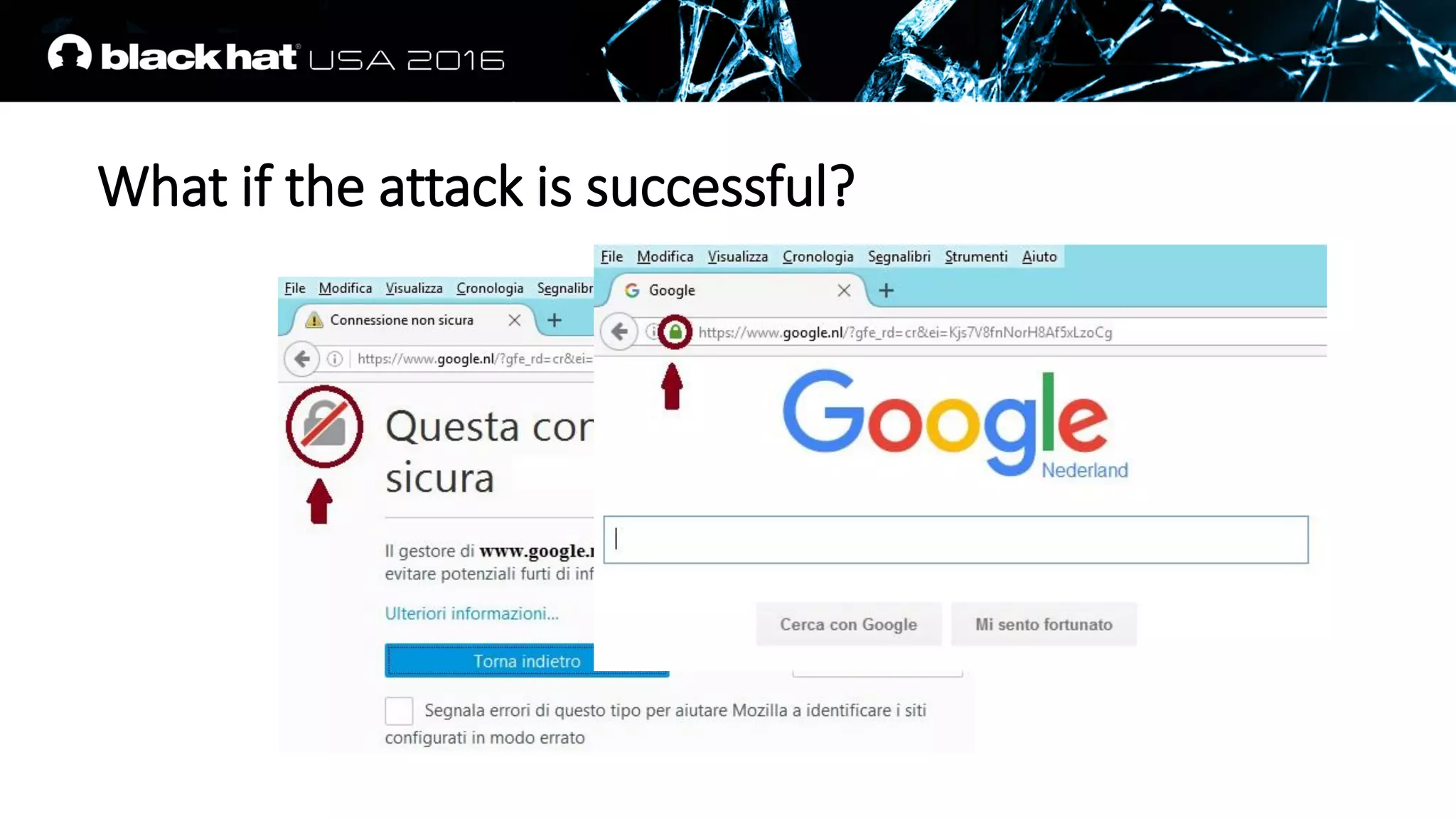
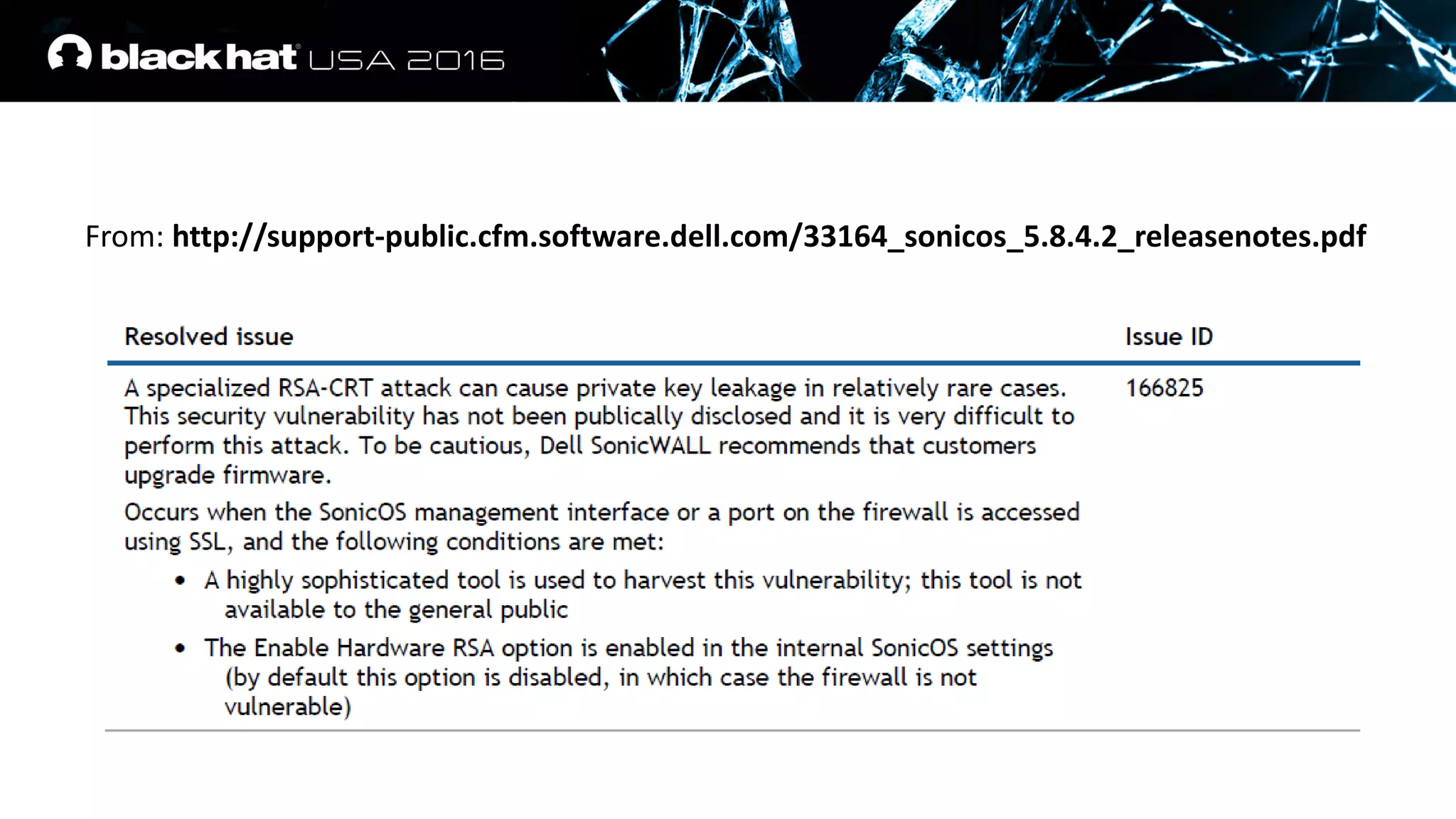
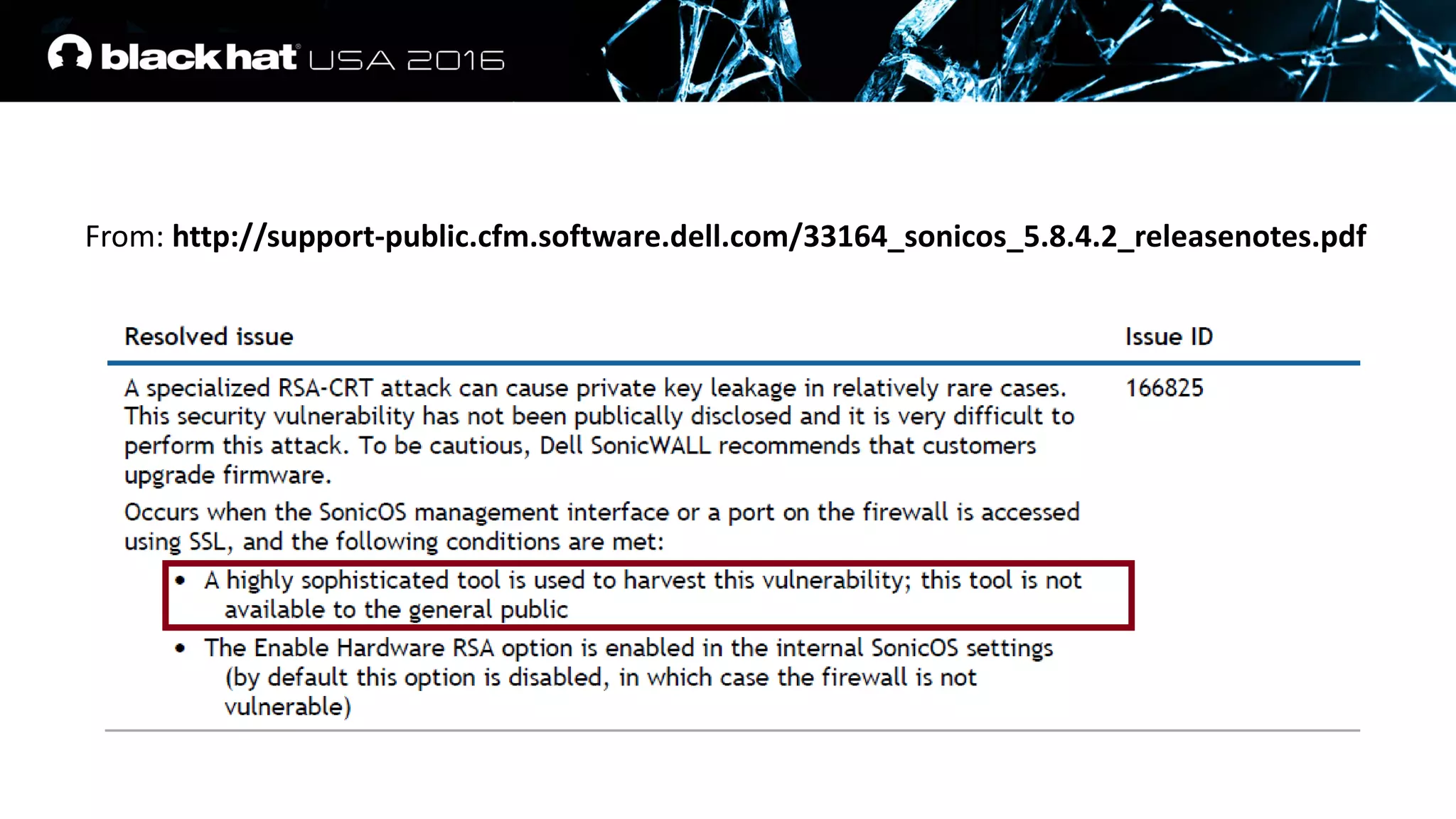
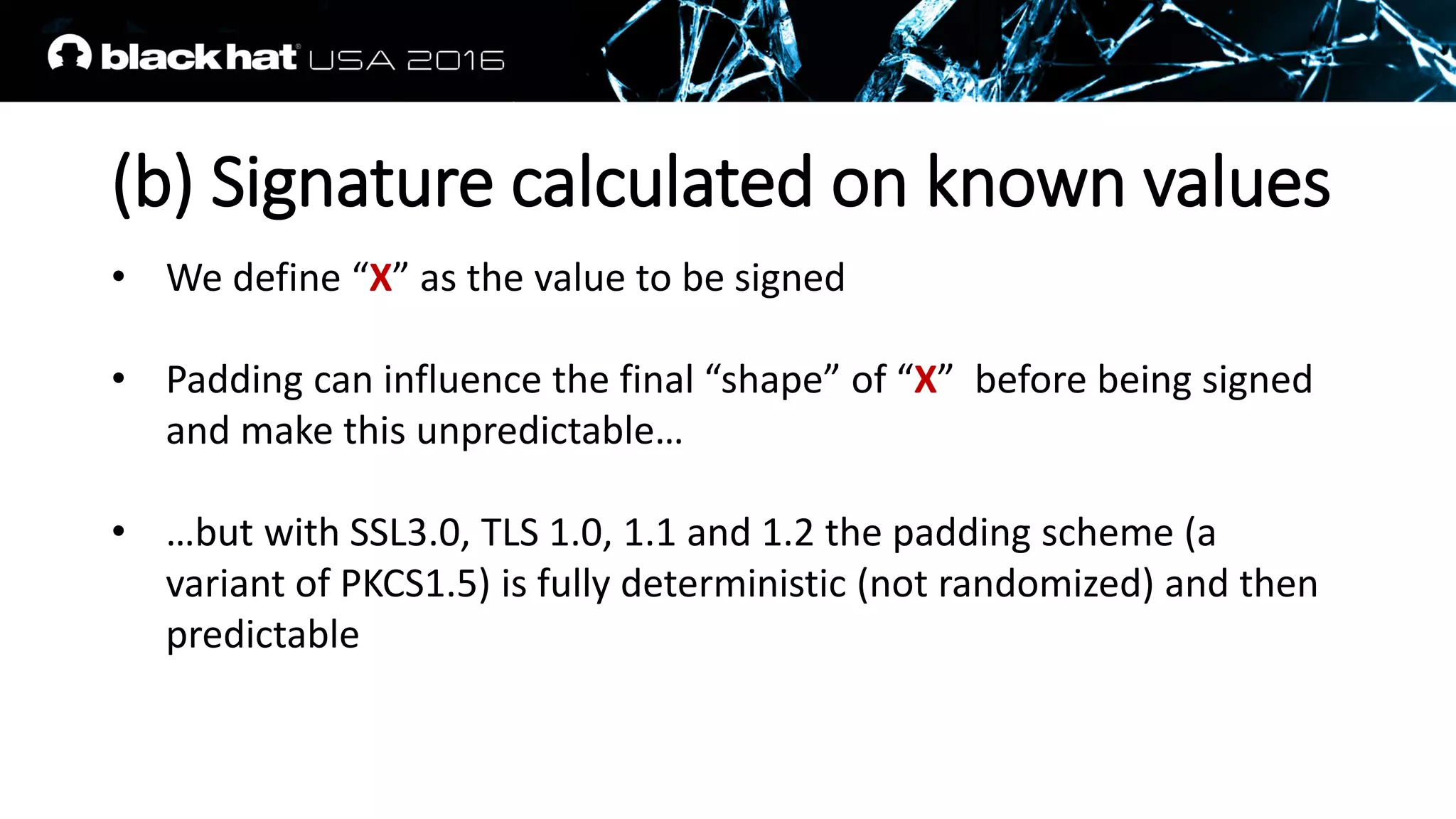
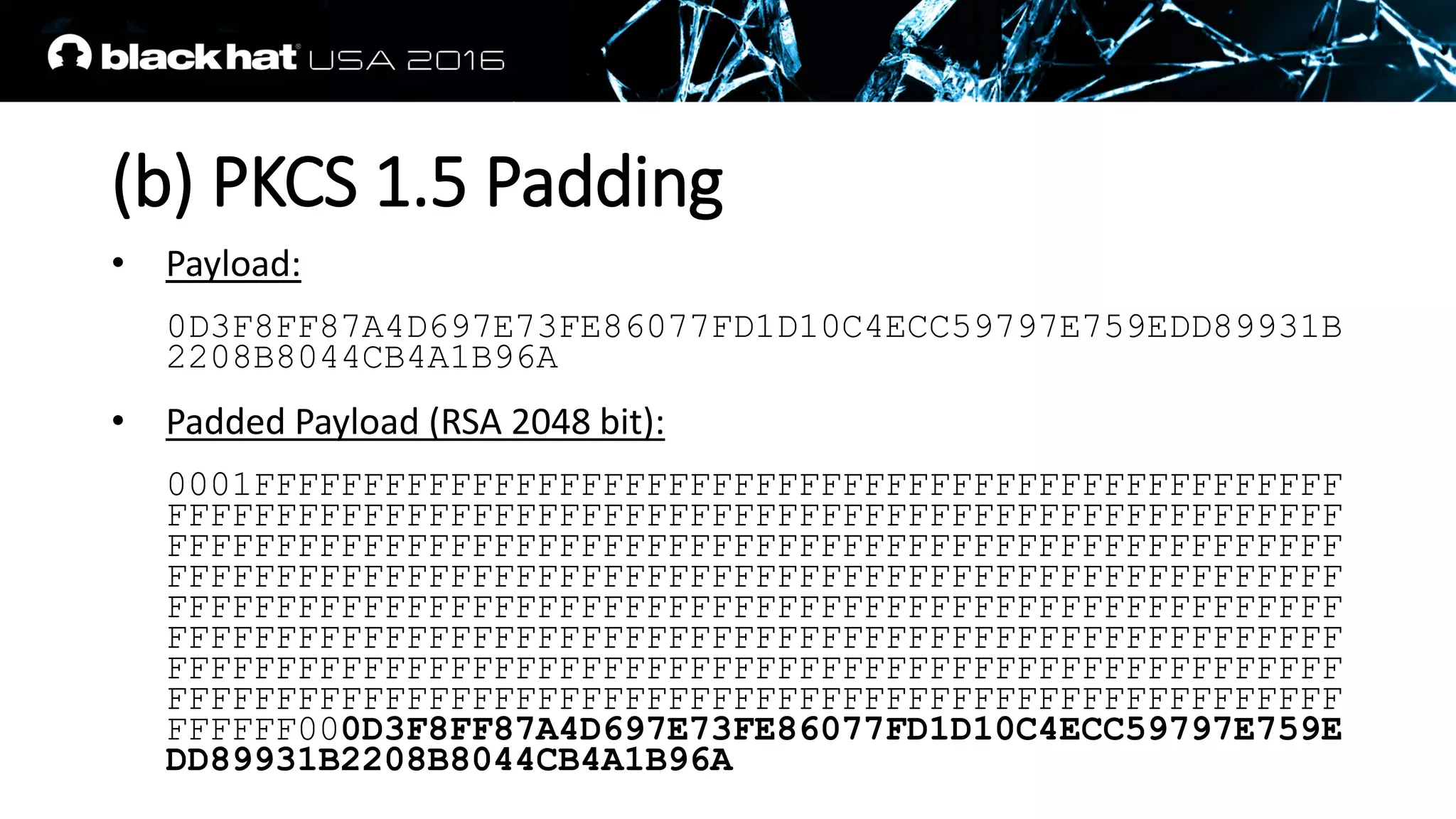
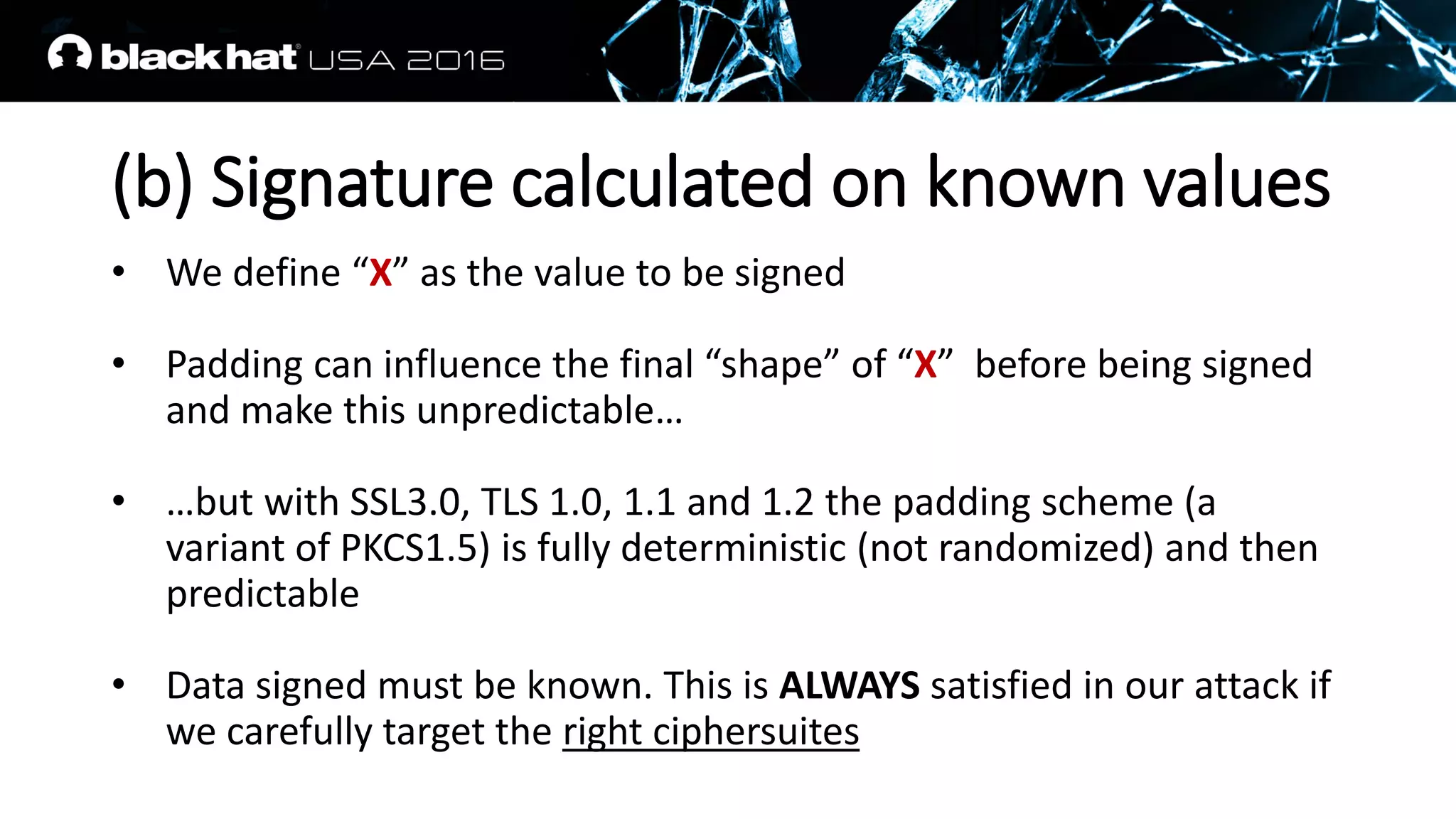
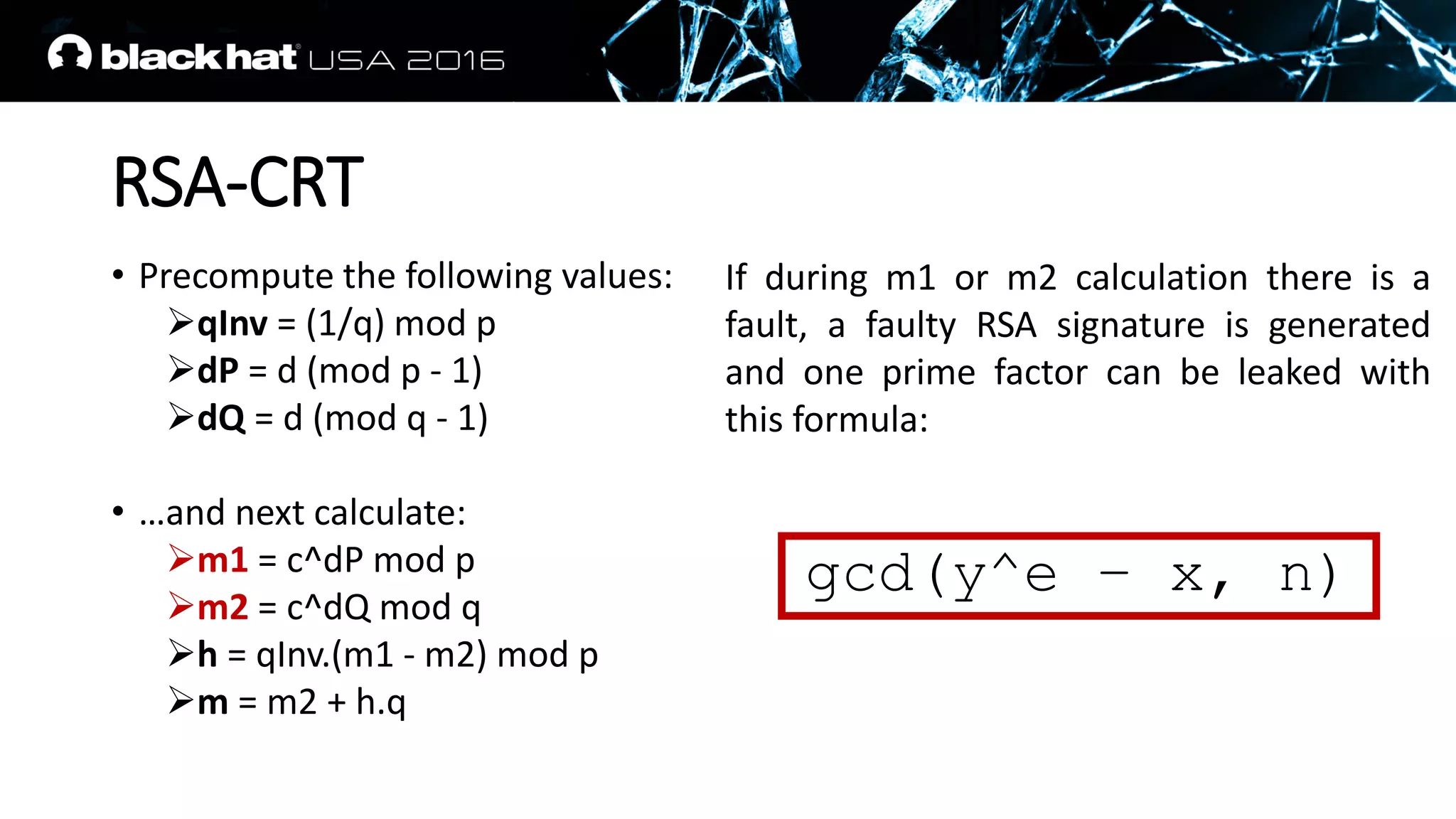
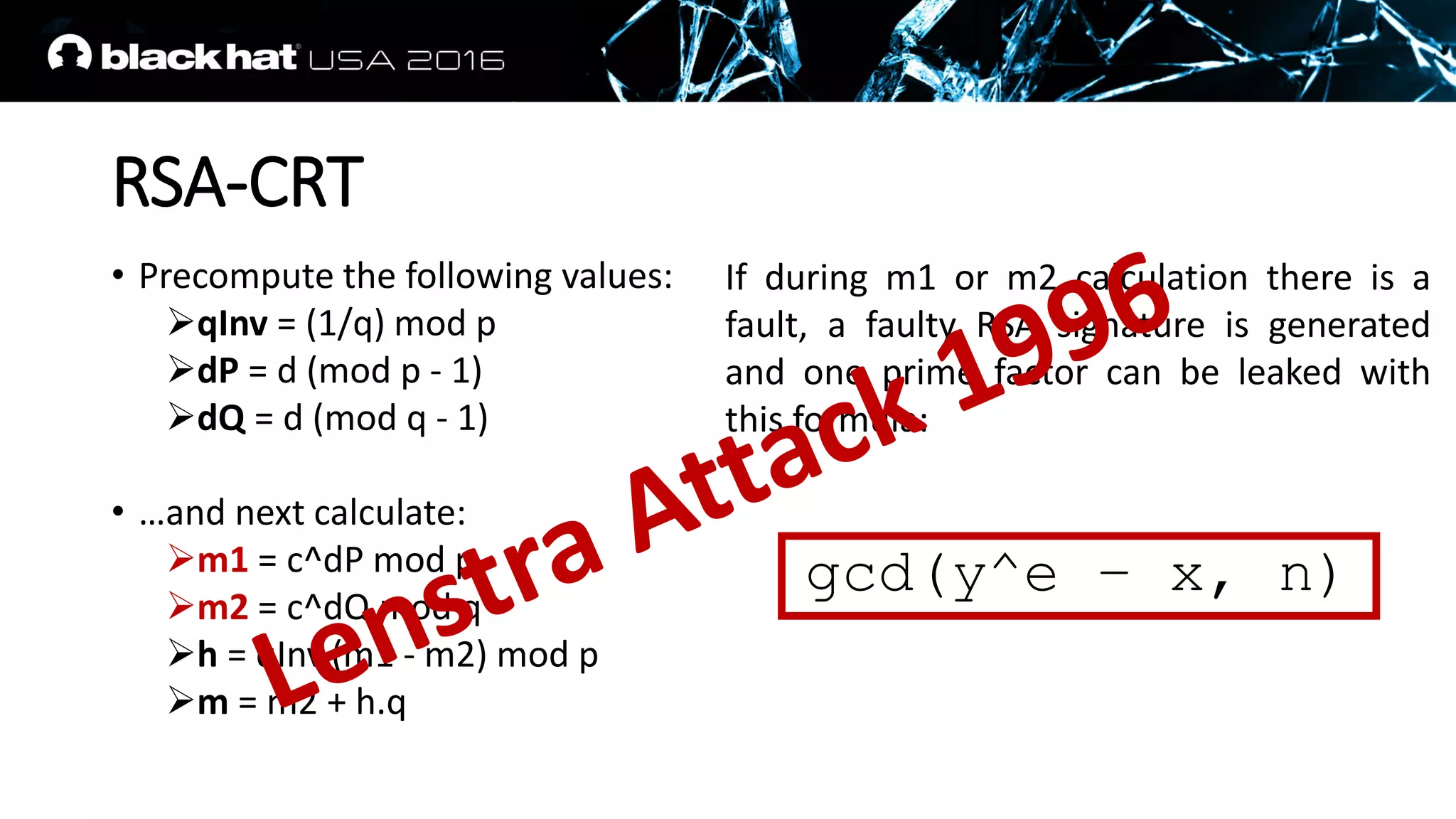
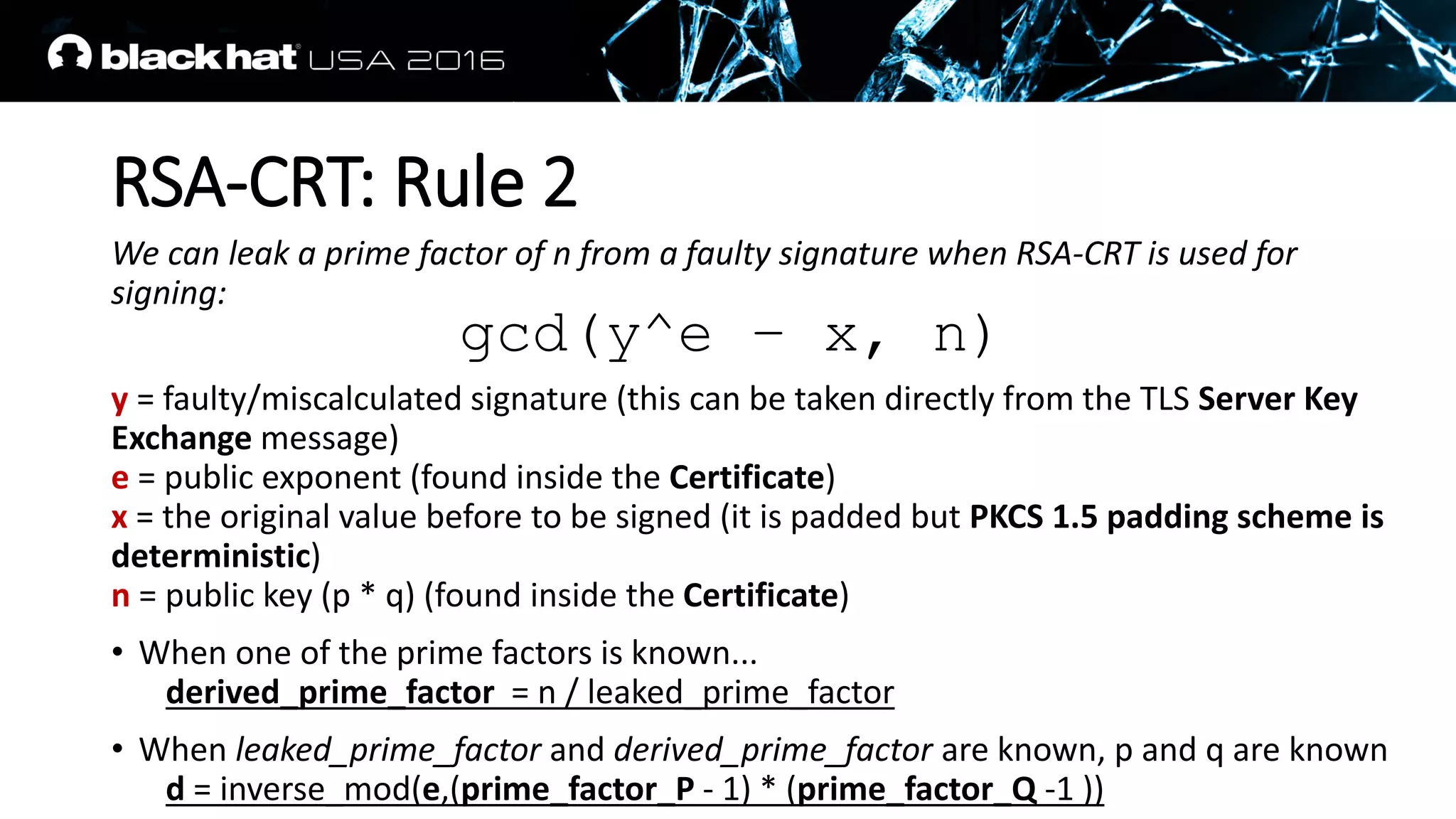
This document discusses recovering an RSA private key from a TLS session using a side channel attack that exploits the RSA-CRT optimization. It begins with background on side channel attacks and an overview of the roadmap. It then discusses how RSA signatures work, the RSA-CRT optimization, and how a fault during signature generation using RSA-CRT can leak a private key factor. The document demonstrates checking for faulty signatures in TLS and recovering the private key. It notes the attack requires RSA-CRT, signatures on known values, and a faulty signature.









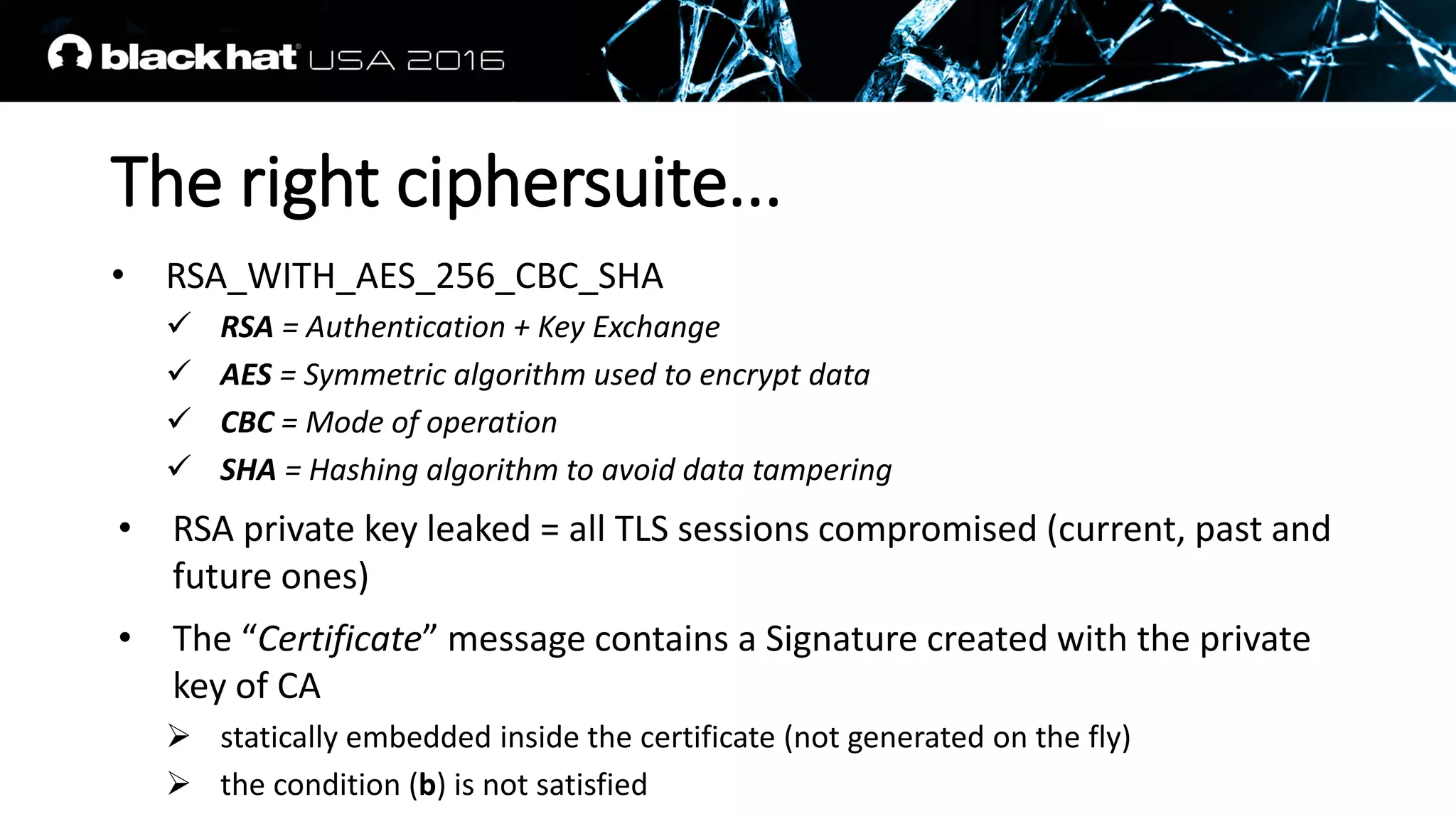
![The right ciphersuite...
• DHE_RSA_WITH_AES_256_CBC_SHA
DHE = Key Exchange
RSA = Only used for Authentication
[the rest is the same as previously mentioned]
• The key exchange is done using private/public keys generated on
the fly
Compromission of a private key breaks only that specific encrypted session,
not all the previously established
This is called "Perfect Forward Secrecy"](https://image.slidesharecdn.com/recover-a-rsa-private-key-from-a-tls-session-with-perfect-forward-secrecy-161124092931/75/Recover-A-RSA-Private-key-from-a-TLS-session-with-perfect-forward-secrecy-26-2048.jpg)
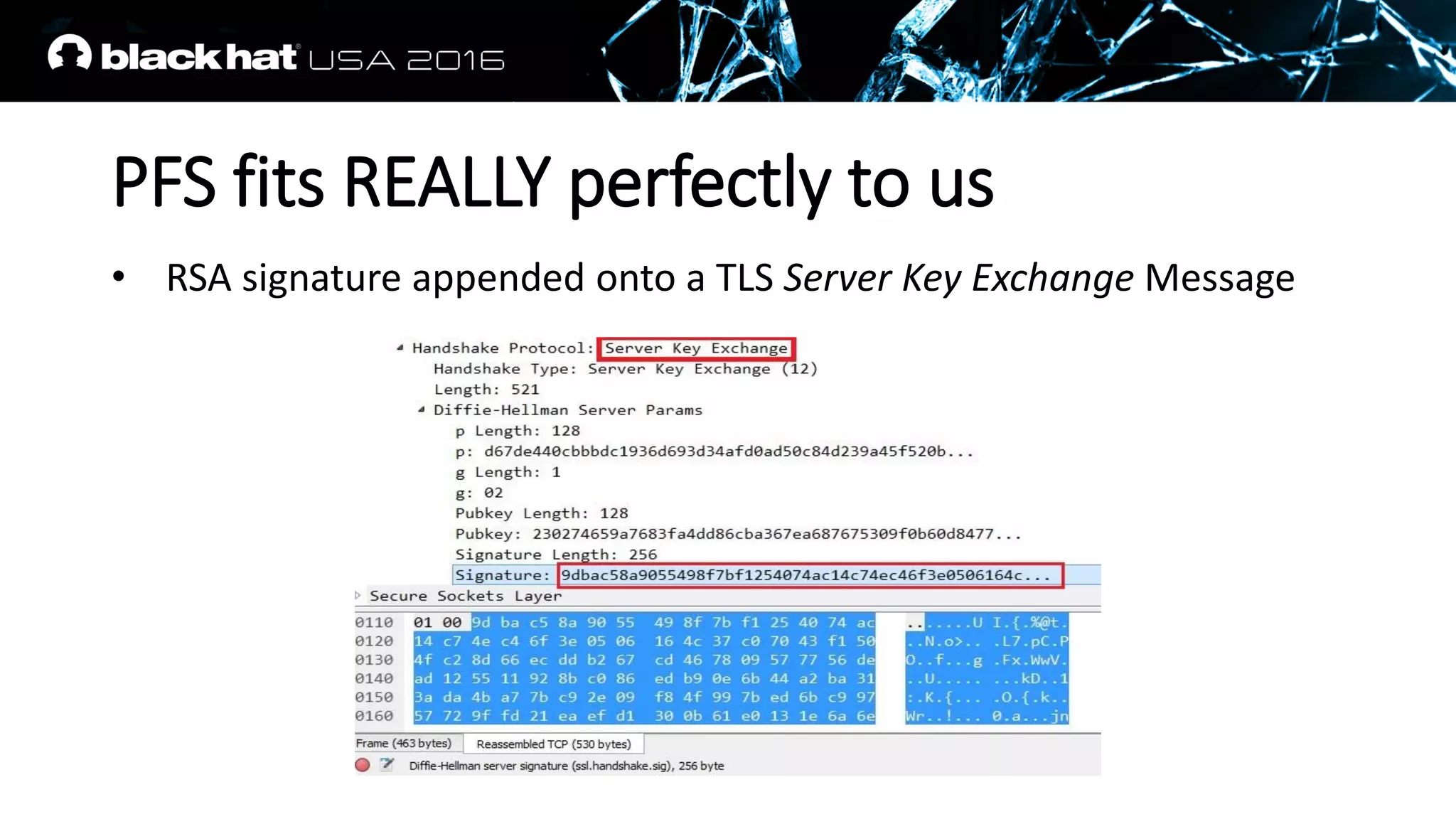
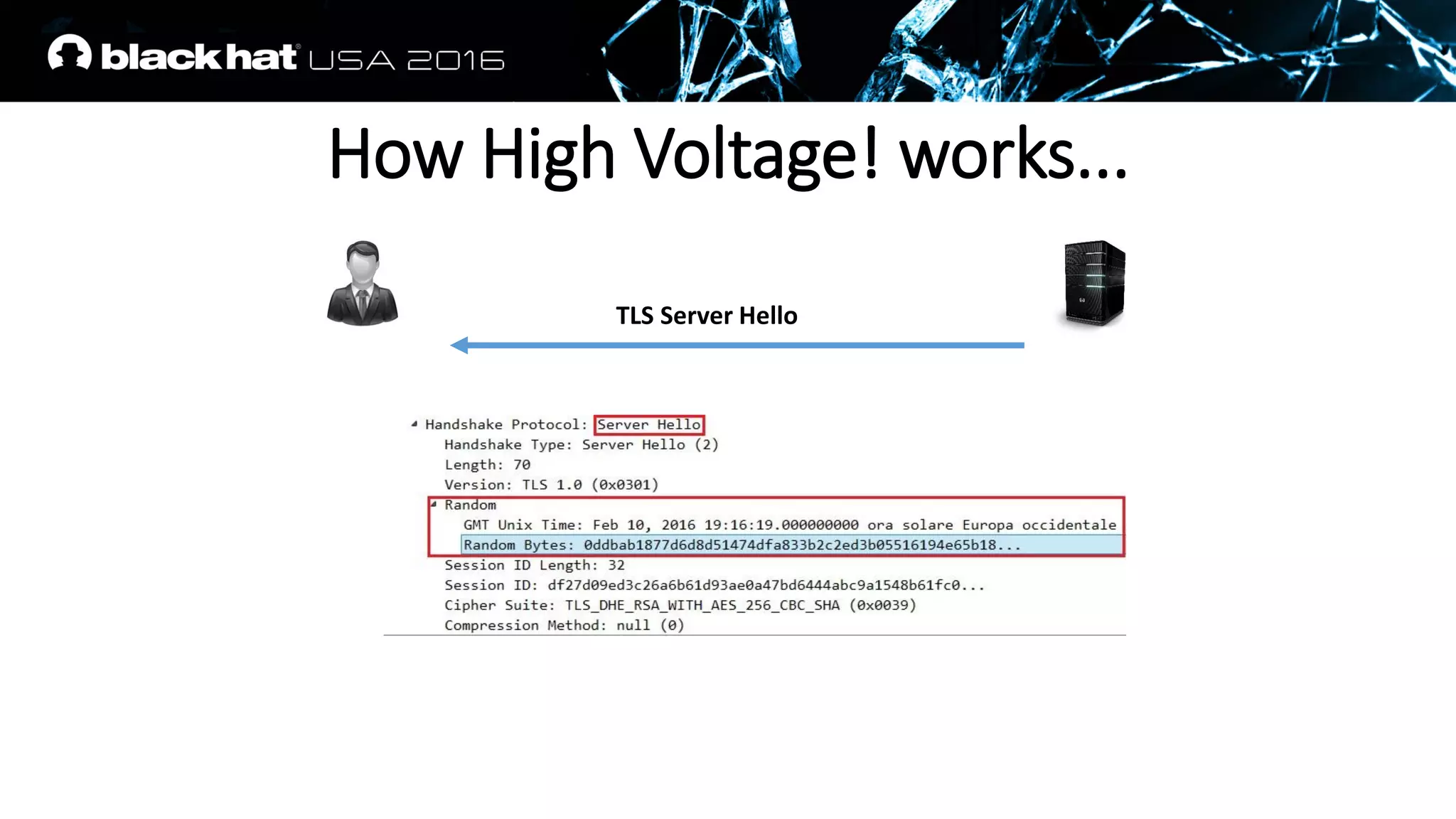
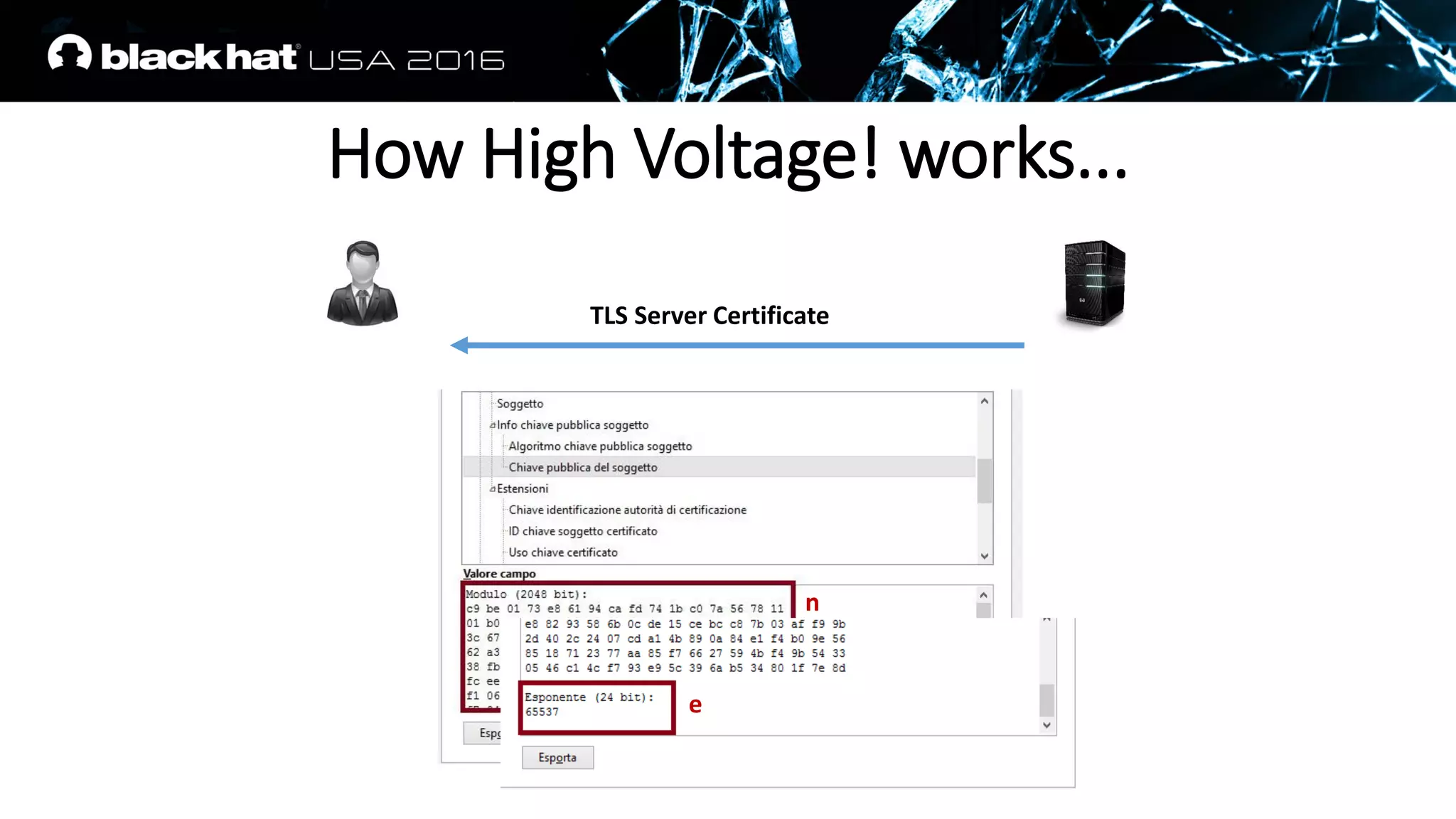
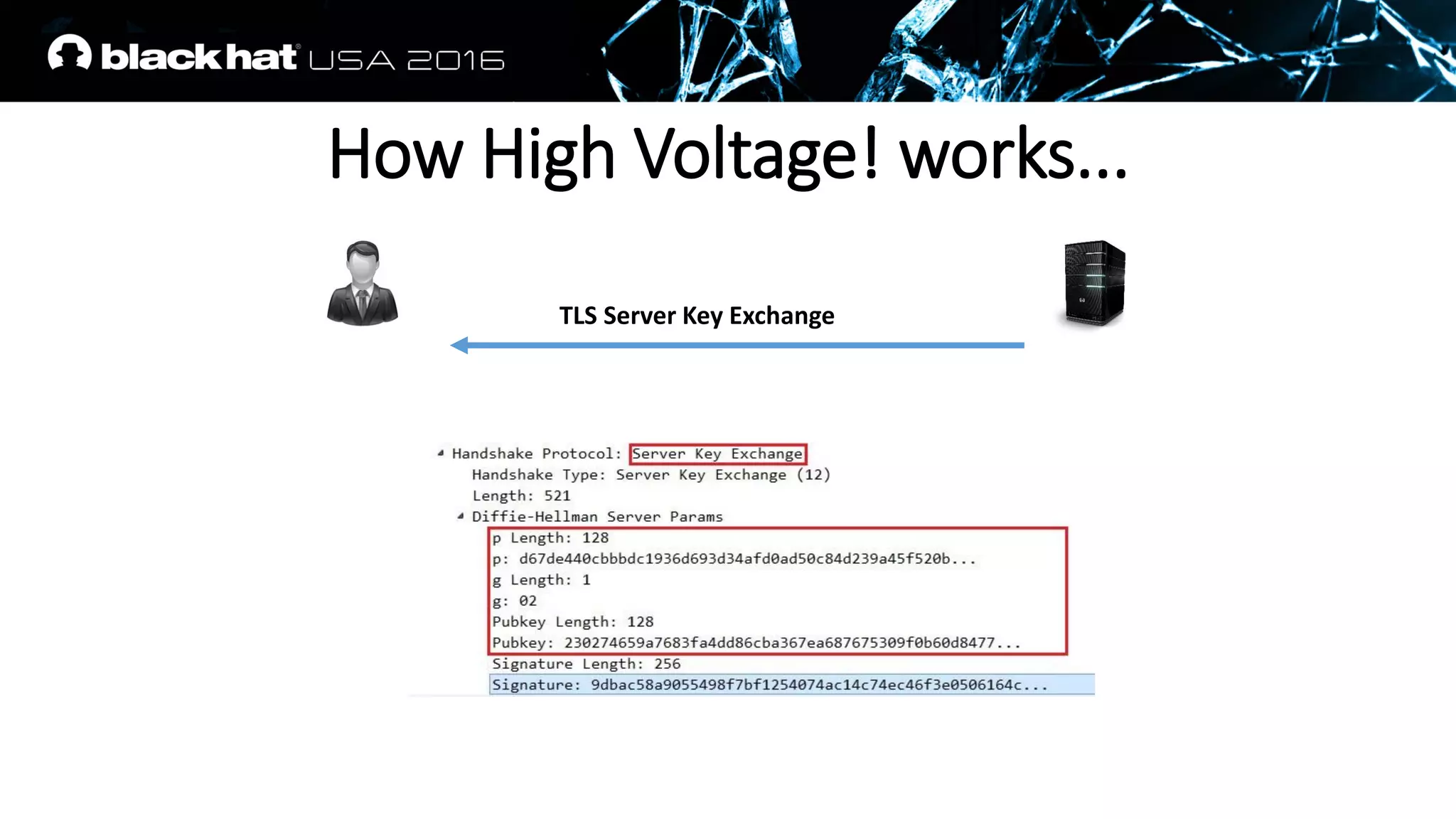
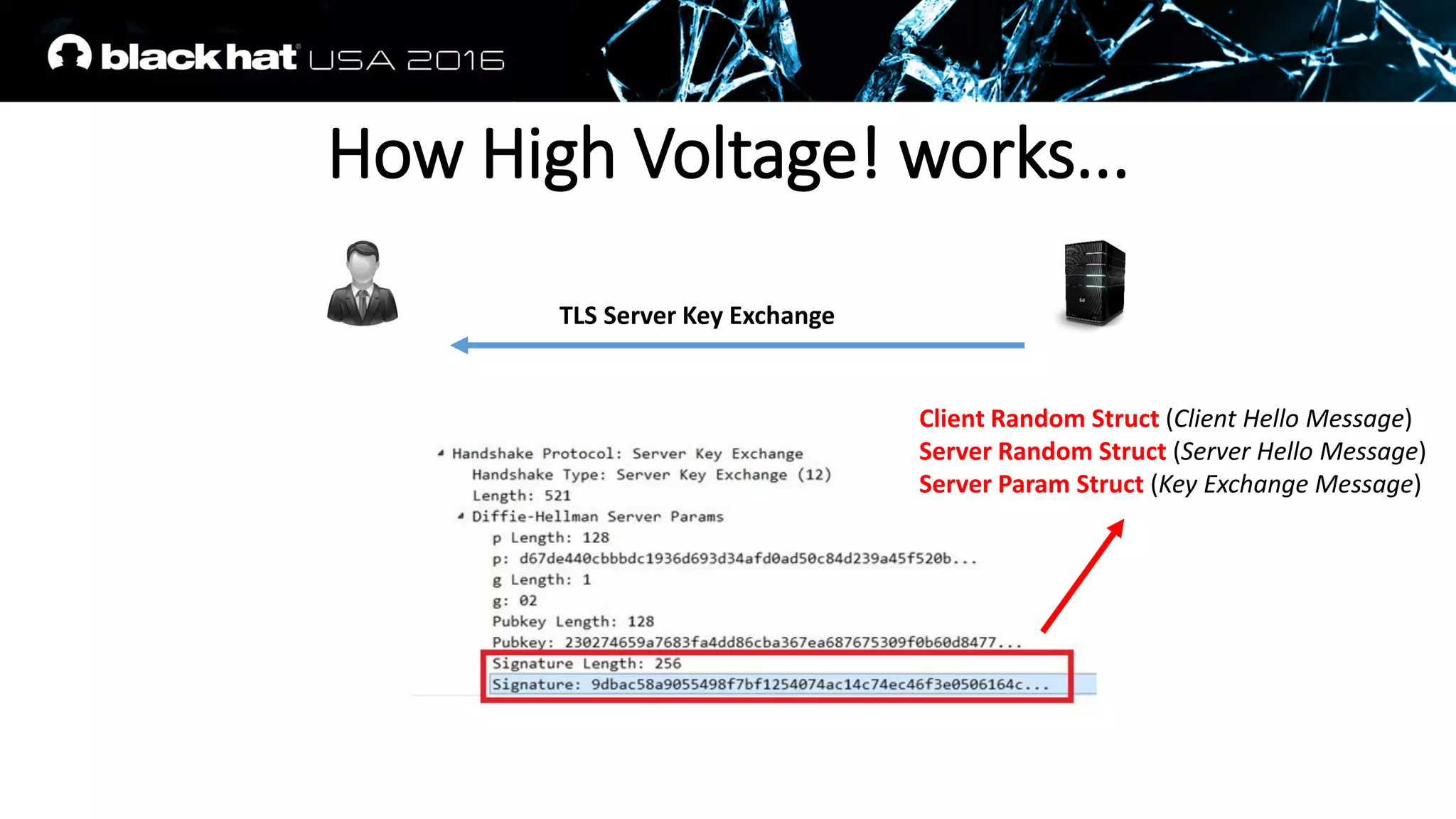
![PFS fits REALLY perfectly to us
• A RSA signature is appended on a TLS Server Key Exchange Message
• The values on which it is calculated are well known, padding scheme
is deterministic
Client Random struct (Client Hello Message)
Server Random struct (Server Hello Message)
Server Params struct (Server Key Exchange Message)
• DHE_RSA_WITH_AES_256_CBC_SHA and in general
[EC]DHE_RSA_WITH_ANY_ANY_ANY ciphersuites are good for us
The condition (b) is satisfied this time](https://image.slidesharecdn.com/recover-a-rsa-private-key-from-a-tls-session-with-perfect-forward-secrecy-161124092931/75/Recover-A-RSA-Private-key-from-a-TLS-session-with-perfect-forward-secrecy-28-2048.jpg)

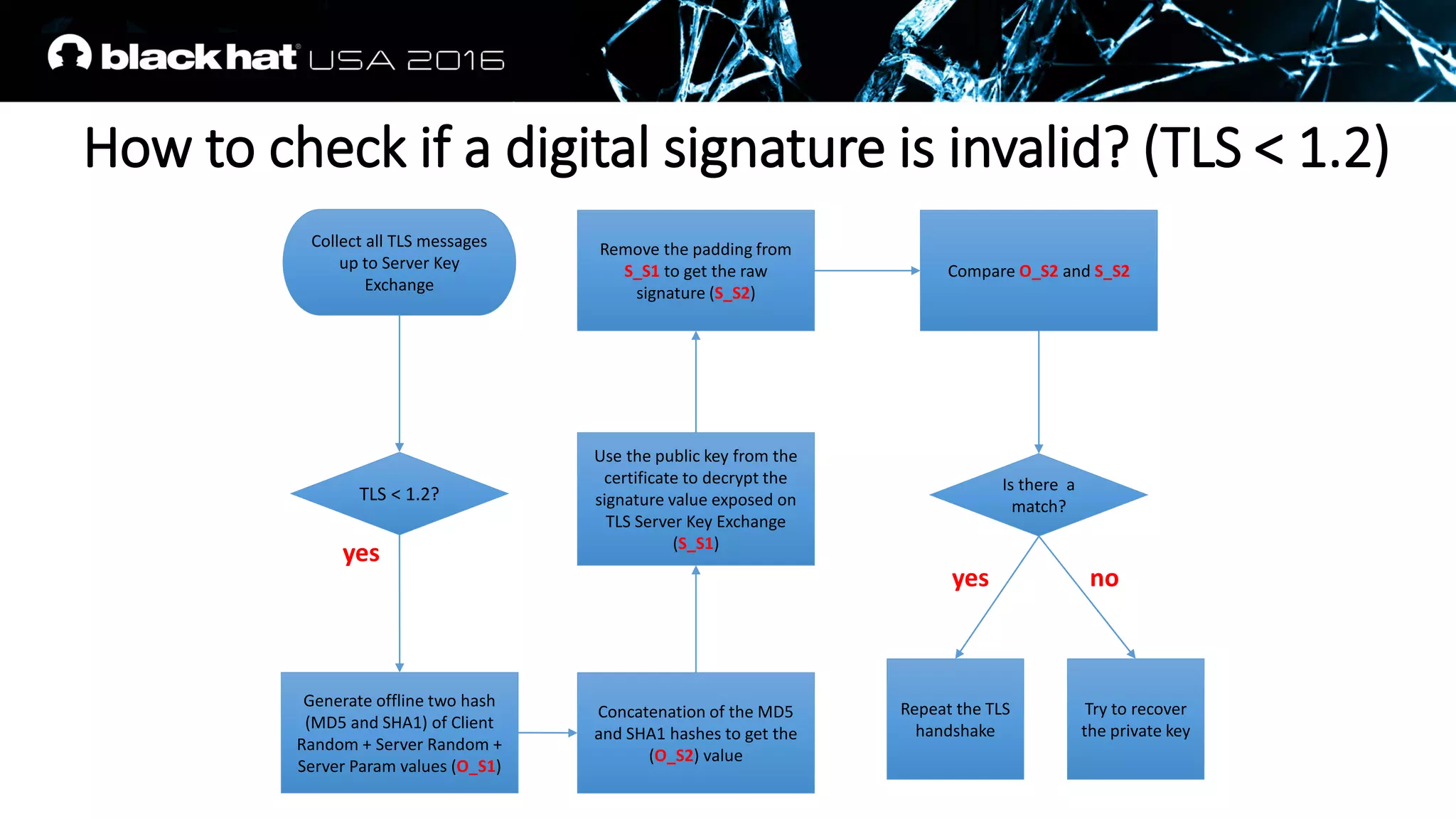
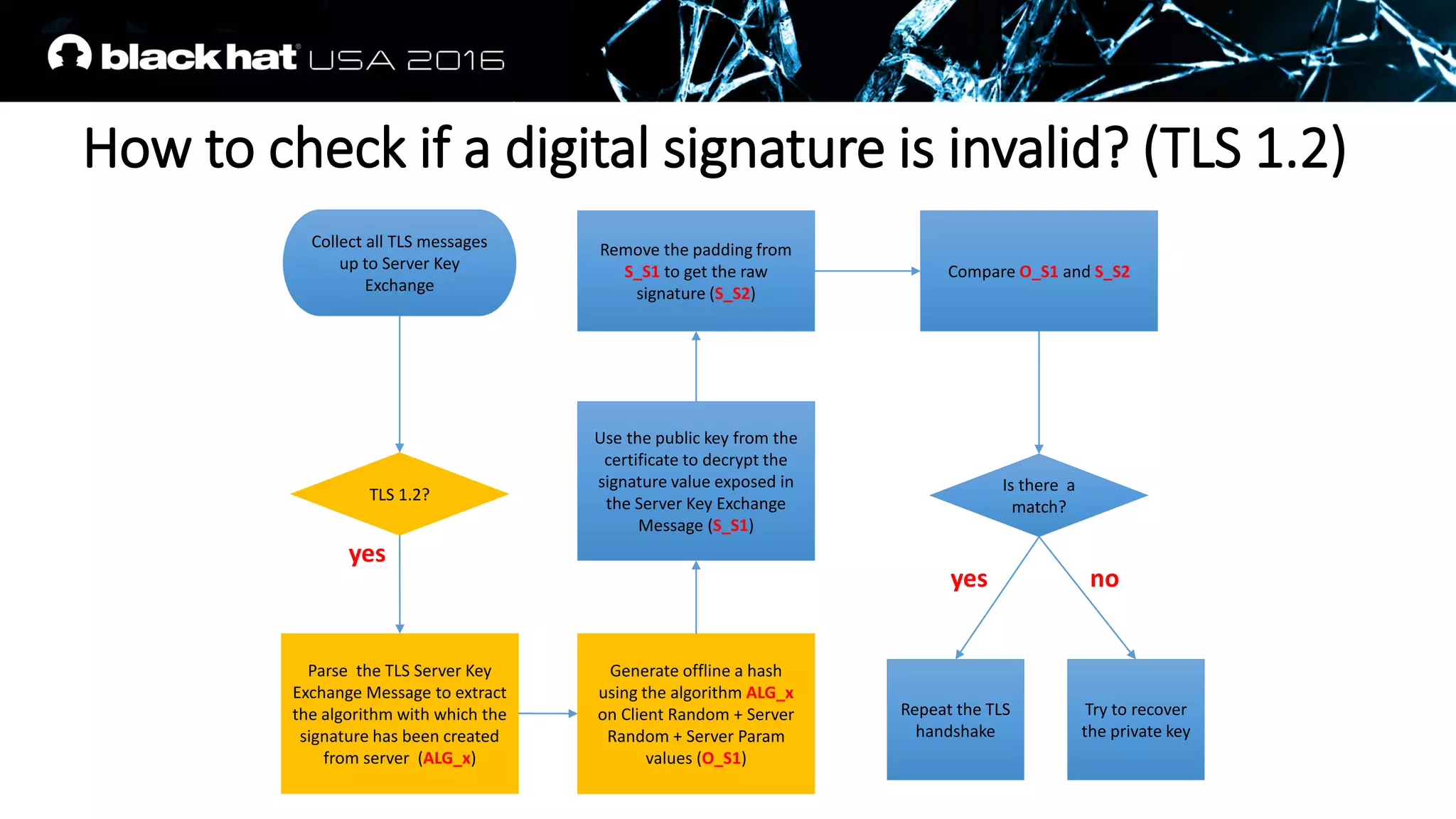







![IKEv1 Phase 1 Main Mode (Signature Auth)
IKE Phase 1 Authenticated With Signatures
Initiator Responder
----------- -----------
(1) HDR, SA -->
<-- (2) HDR, SA
(3) HDR, KE, Ni -->
<-- (4) HDR, KE, Nr
(5) HDR*, IDii, [ CERT, ] SIG_I -->
<-- (6) HDR*, IDir, [ CERT, ] SIG_R
* Indicates payload encryption](https://image.slidesharecdn.com/recover-a-rsa-private-key-from-a-tls-session-with-perfect-forward-secrecy-161124092931/75/Recover-A-RSA-Private-key-from-a-TLS-session-with-perfect-forward-secrecy-55-2048.jpg)
![IKEv1 Phase 1 Aggressive Mode (Signature Auth)
IKE Phase 1 Authenticated With Signatures
Initiator Responder
----------- -----------
(1) HDR, SA, KE, Ni, IDii -->
<-- (2)HDR, SA, KE, Nr, IDir,
[ CERT, ] SIG_R
(3) HDR, [ CERT, ] SIG_I -->](https://image.slidesharecdn.com/recover-a-rsa-private-key-from-a-tls-session-with-perfect-forward-secrecy-161124092931/75/Recover-A-RSA-Private-key-from-a-TLS-session-with-perfect-forward-secrecy-56-2048.jpg)