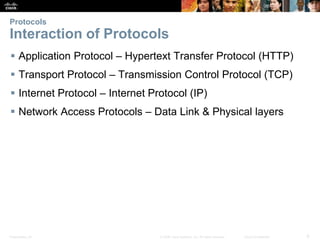
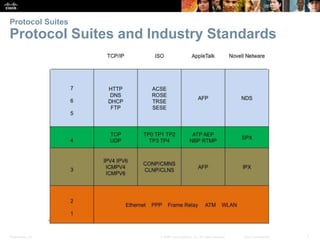
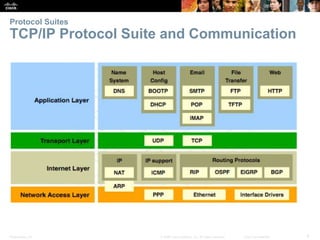
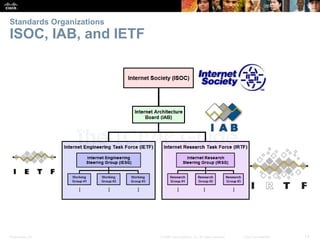
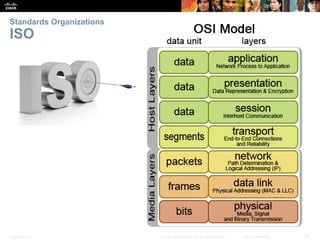
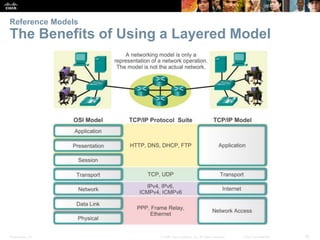
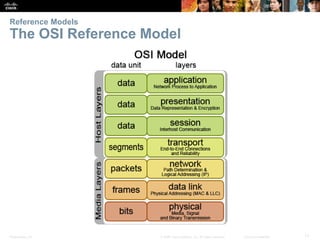
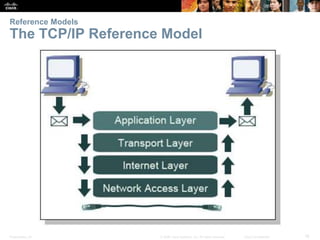
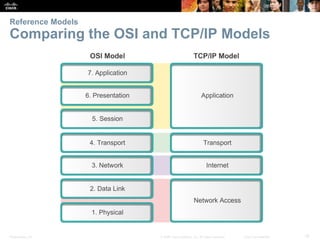
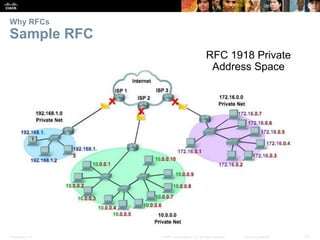
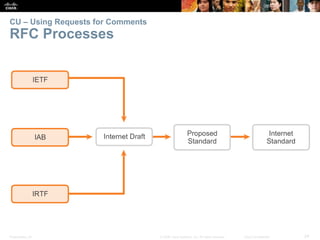
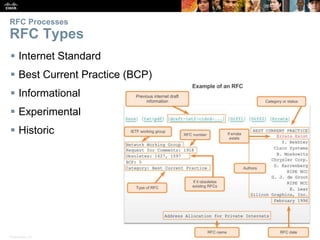
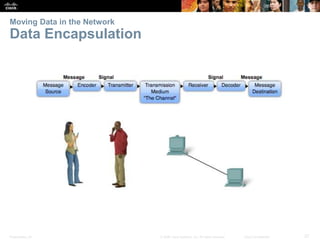
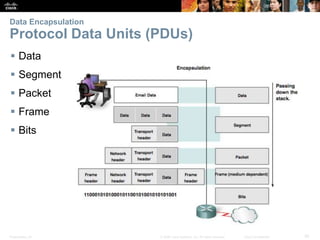
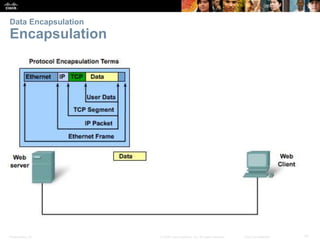
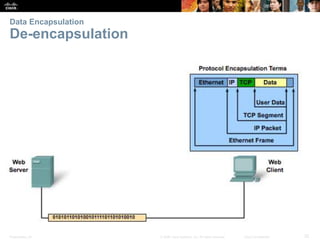
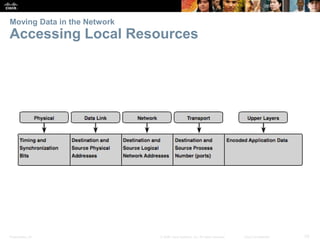
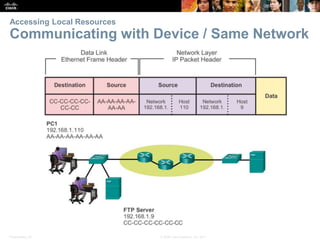
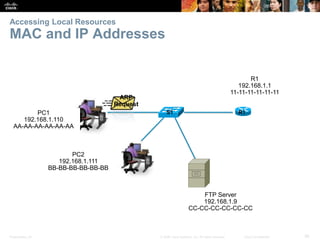
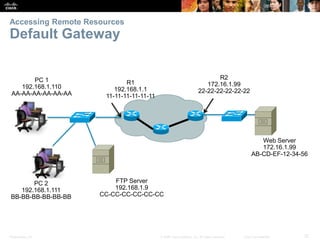
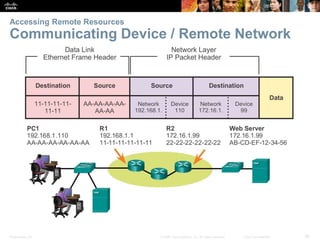
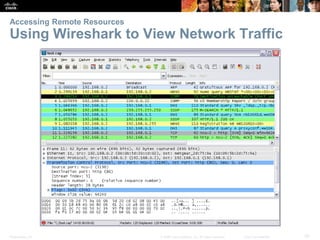
This document summarizes a chapter about network protocols and communications. It discusses how protocols establish communication rules and standards organizations develop protocols through processes like RFCs. It also describes how data is encapsulated when moving through networks and OSI and TCP/IP models for conceptualizing network layers. Specific topics covered include protocol suites, addressing, data encapsulation, accessing local and remote network resources, and standards bodies.