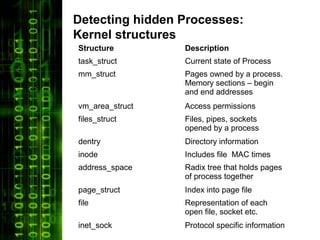
The document discusses Linux volatile memory forensic techniques. It begins by outlining challenges like numerous Linux builds/versions and changing kernel structures. It then covers areas like exploring kernel vulnerabilities, detecting malware/rootkits via memory analysis, and deriving kernel data structures from executables. Key techniques discussed are detecting hidden processes by analyzing the task_struct and related kernel data structures. The document concludes by arguing that understanding a system's kernel memory structures is essential for Linux volatile memory forensics.


![Deriving Kernel data structures
Reverse engineering kernel data structures – from
executable [10]
Graph based signatures (pointer pattern based) [11]
Utilization of debugging information [5]
Simulation of utilities based on kernel structures [13]
Understanding kernel data structures forms the core of
Volatile memory forensics – eg. enables detection of
Hidden Processes [9], [15], [16], [17]](https://image.slidesharecdn.com/subappt-120809231454-phpapp01/85/Linux-Forensics-6-320.jpg)
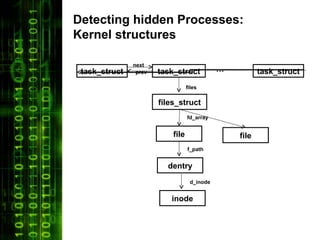
![Detecting hidden Processes:
Kernel structures (Kernel 2.6.32)
struct task_struct {
[0] volatile long int state;
[4] void *stack;
[8] atomic_t usage;
[12] unsigned int flags;
[16] unsigned int ptrace;
[20] int lock_depth;
[24] int prio;
[28] int static_prio;
[32] int normal_prio;
[36] unsigned int rt_priority;
[40] const struct sched_class *sched_class;
[44] struct sched_entity se;
[376] struct sched_rt_entity rt;
[412] struct hlist_head preempt_notifiers;
[416] unsigned char fpu_counter;
[420] unsigned int btrace_seq;
[424] unsigned int policy;
[428] cpumask_t cpus_allowed;
[432] struct sched_info sched_info;
[464] struct list_head tasks; //Circular linked list of processes,
tasks.next and task.prev
…
[3248] struct memcg_batch_info memcg_batch;
}
SIZE: 3264](https://image.slidesharecdn.com/subappt-120809231454-phpapp01/85/Linux-Forensics-9-320.jpg)



![Malware detection techniques
Based on:
Data access patterns and structural signatures
[4],[6],[8]
Binary analysis based on instruction sequence
[12]
task structure analysis [14]](https://image.slidesharecdn.com/subappt-120809231454-phpapp01/85/Linux-Forensics-14-320.jpg)
![Malware detection techniques [4]
Inter-structure pointers:
struct socket_alloc{
[0] struct socket socket;
[1] struct inode vfs_inode; //0x28
}
size: 392](https://image.slidesharecdn.com/subappt-120809231454-phpapp01/85/Linux-Forensics-15-320.jpg)
![Malware detection techniques [4]
socket_alloc
0
dentry
struct file
file f_dentry d_inode
40
vfs_inode](https://image.slidesharecdn.com/subappt-120809231454-phpapp01/85/Linux-Forensics-16-320.jpg)
![Rootkit Detection
Hidden Rootkit – DKOM and Function hooking
Remain undetected through normal modes of
detection such as ps
Finding hidden objects such as sockets and
processes based on field types and inter-structure
pointers in kernel structures [4, 6]
Behavioral analysis – such as data access
patterns [8]](https://image.slidesharecdn.com/subappt-120809231454-phpapp01/85/Linux-Forensics-17-320.jpg)
![Classification of various techniques
Title Analysis type Application
Detecting stealthy
malware with Inter-
Structure and In-execution Malware detection
imported Signatures
[4]
Characterizing Kernel
Malware Behavior
In-execution Malware detection
with Kernel Data
Access Patterns [8]
In-Execution Malware
Detection using Task
In-execution Malware detection
Structures of Linux
Processes [14]
Detecting Kernel-level
Rootkits
In-execution Rootkit detection
using Data Structure
Invariants [6]
Detecting Kernel- Pre execution Rootkit detection
Level Rootkits
Through Binary
Analysis [12]
Locating 386 paging Memory dump Hidden process
structures in memory analysis detection
images [9]](https://image.slidesharecdn.com/subappt-120809231454-phpapp01/85/Linux-Forensics-18-320.jpg)
![Classification of various techniques
Title Analysis type Application
FACE: Automated digital Memory dump analysis Evidence correlation
evidence discovery and
correlation [13]
The 7 dwarves: Post execution Identification of Kernel
debugging information structure offsets
beyond gdb [5]
SigGraph: Brute Force In-execution Identification of Kernel
Scanning of Kernel Data structures
Structure Instances
Using
Graph-based Signatures
[11]
Automatic Reverse In-execution Identification of Kernel
Engineering of Data structures from memory
Structures from Binary image
Execution [10]
An Analysis of Linux RAM Memory dump analysis Identification of
Forensics [16] forensically relevant data
structures (SUSE Linux
kernel 2.6)
Linux Memory Forensic: Memory dump analysis Identification of
Searching for processes forensically relevant data
[17] structures (kernel version
2.6.20 and 2.4.23)](https://image.slidesharecdn.com/subappt-120809231454-phpapp01/85/Linux-Forensics-19-320.jpg)

![References
[1] Wikipedia, http://en.wikipedia.org/wiki/Cyber_forensics
[2] ”Crash utility”, http://people.redhat.com/anderson/crash_whitepaper/
[3] Case, A., Marziale, L., Richard, G.G., “Dynamic recreation of kernel data
structures for live forensics”, Digital Investigations, 2010
[4] Liang, B., You, W., Shi, W., Liang, Z., “Detecting stealthy malware with Inter-
Structure and imported Signatures”, Proceedings of the 6th ACM Symposium on
Information, Computer and Communications Security, 2011
[5] Arnaldo Carvalho de Melo, "The 7 dwarves: debugging information beyond
gdb", Proceedings of the Linux Symposium, 2007
[6] Baliga, A., “Detecting Kernel-level Rootkits using Data Structure Invariants,
IEEE Transactions on Dependable and Secure Computing”, 2011
[7] Ramaswamy, A., “Detecting Kernel rootkits”, Dartmouth College Masters
Thesis, 2008
[8] Rhee, J., Lin, Z., Xu, D., “Characterizing Kernel Malware Behavior with Kernel
Data Access Patterns”, Proceedings of the 6th ACM Symposium on Information,
Computer and Communications Security, 2011
[9] Saur, K., Julian B. Grizzard, “Locating 386 paging structures in memory
images”, Digital Investigations, 2010
[10] Lin, Z., Zhang, X., Xu, D., “Automatic Reverse Engineering of Data
Structures from Binary Execution”, the 17th Network and Distributed System
Security Symposium, 2010
[11] Lin, Z., “SigGraph: Brute Force Scanning of Kernel Data Structure Instances
Using Graph-based Signatures”, 40th Annual IEEE/IFIP International Conference
on Dependable Systems and Networks, 2010](https://image.slidesharecdn.com/subappt-120809231454-phpapp01/85/Linux-Forensics-21-320.jpg)
![References
[12] Christopher , K., “Detecting Kernel-Level Rootkits Through Binary Analysis”,
Computer Security Applications Conference, 2004
[13] Case, A., Cristina, A., Marziale, L., Golden G. Richard, Roussev, V., “FACE:
Automated digital evidence discovery and correlation”, Digital Investigations,
2008
[14] Shahzad, F. et al, “In-Execution Malware Detection using Task Structures of
Linux Processes”, IEEE International Conference on Communications, 2011
[15] Burdach, M., “Digital Forensics of the physical memory”, 2005
[16] Urrea, J.M., “An analysis of Linux RAM forensics”, Naval Postgraduate
School Thesis, 2006
[17] Gao, Y., Cao, T., “Linux Memory Forensic: Searching for processes”,
Computer Security Applications Conference, 2010
[18] Movall, P., Nelson, W., Wetzstein, S., “Linux Physical Memory Analysis”,
Proceedings of the annual conference on USENIX Annual Technical Conference,
2005
[19] Wikipedia, http://en.wikipedia.org/wiki/Computer_forensics
[20] DFRWS. Dfrws 2005 forensics challenge,
http://www.dfrws.org/2005/challenge/index.shtml; 2005.
[21] Volatility framework, https://www.volatilesystems.com/default/volatility](https://image.slidesharecdn.com/subappt-120809231454-phpapp01/85/Linux-Forensics-22-320.jpg)
