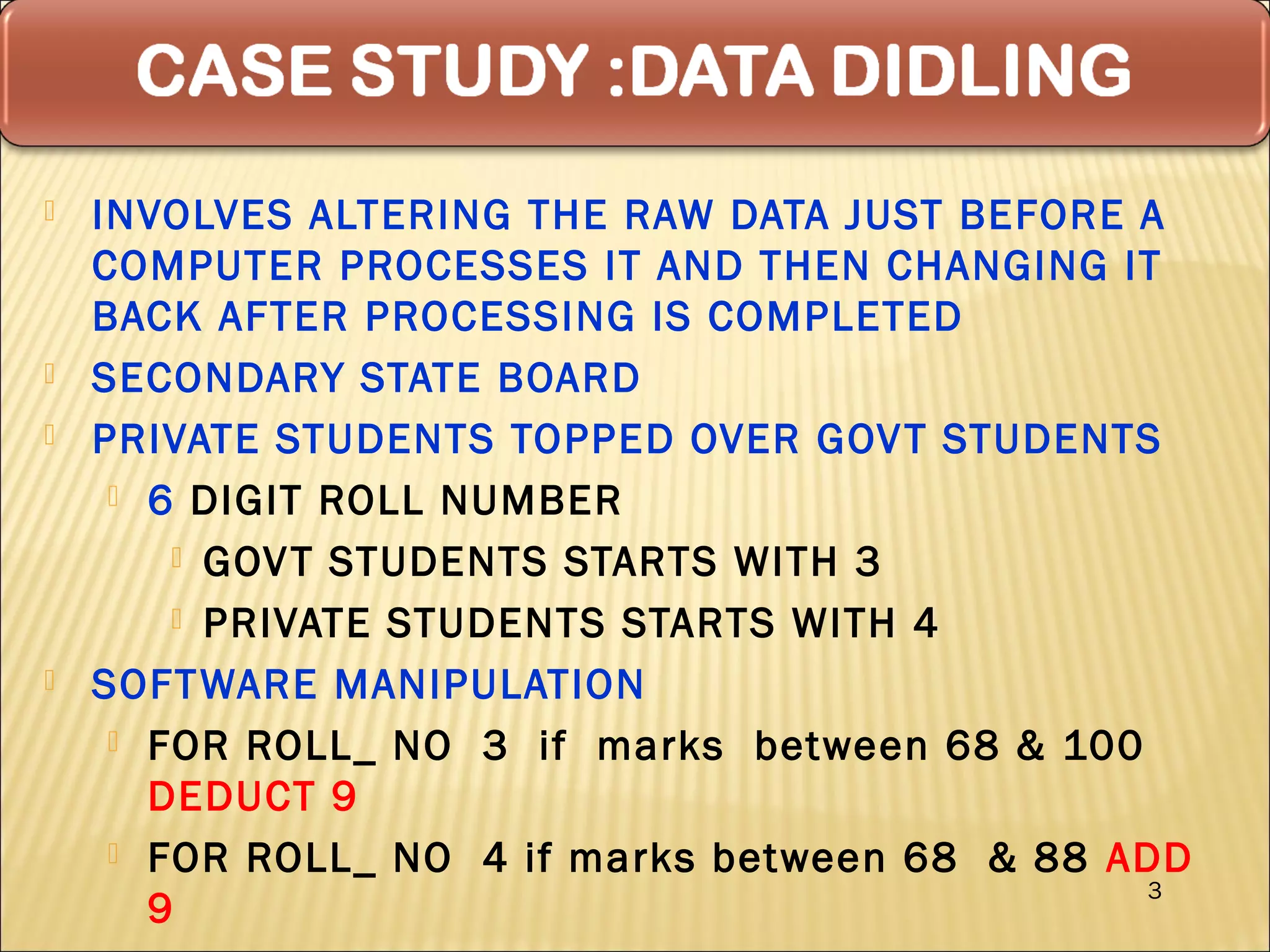
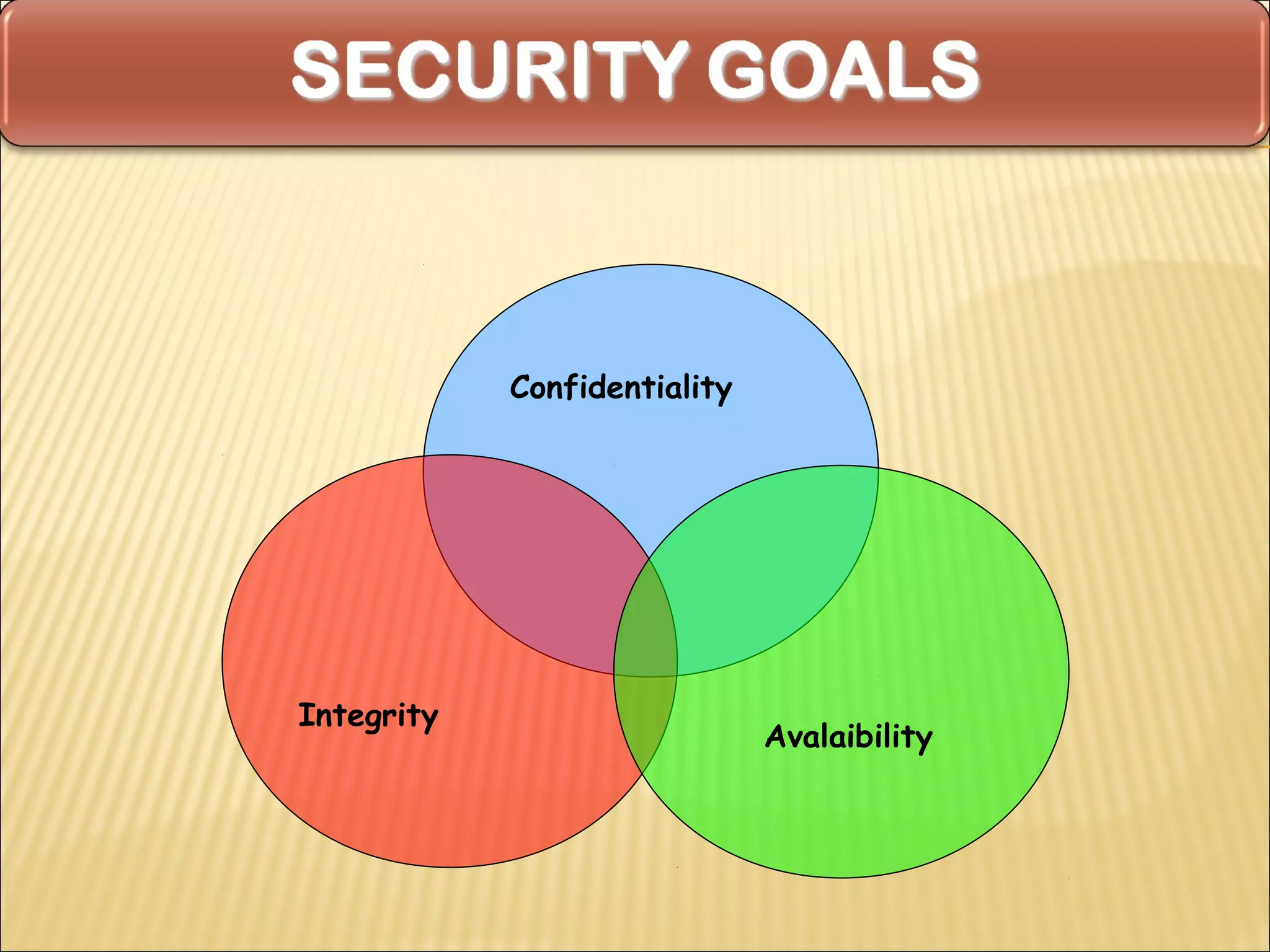
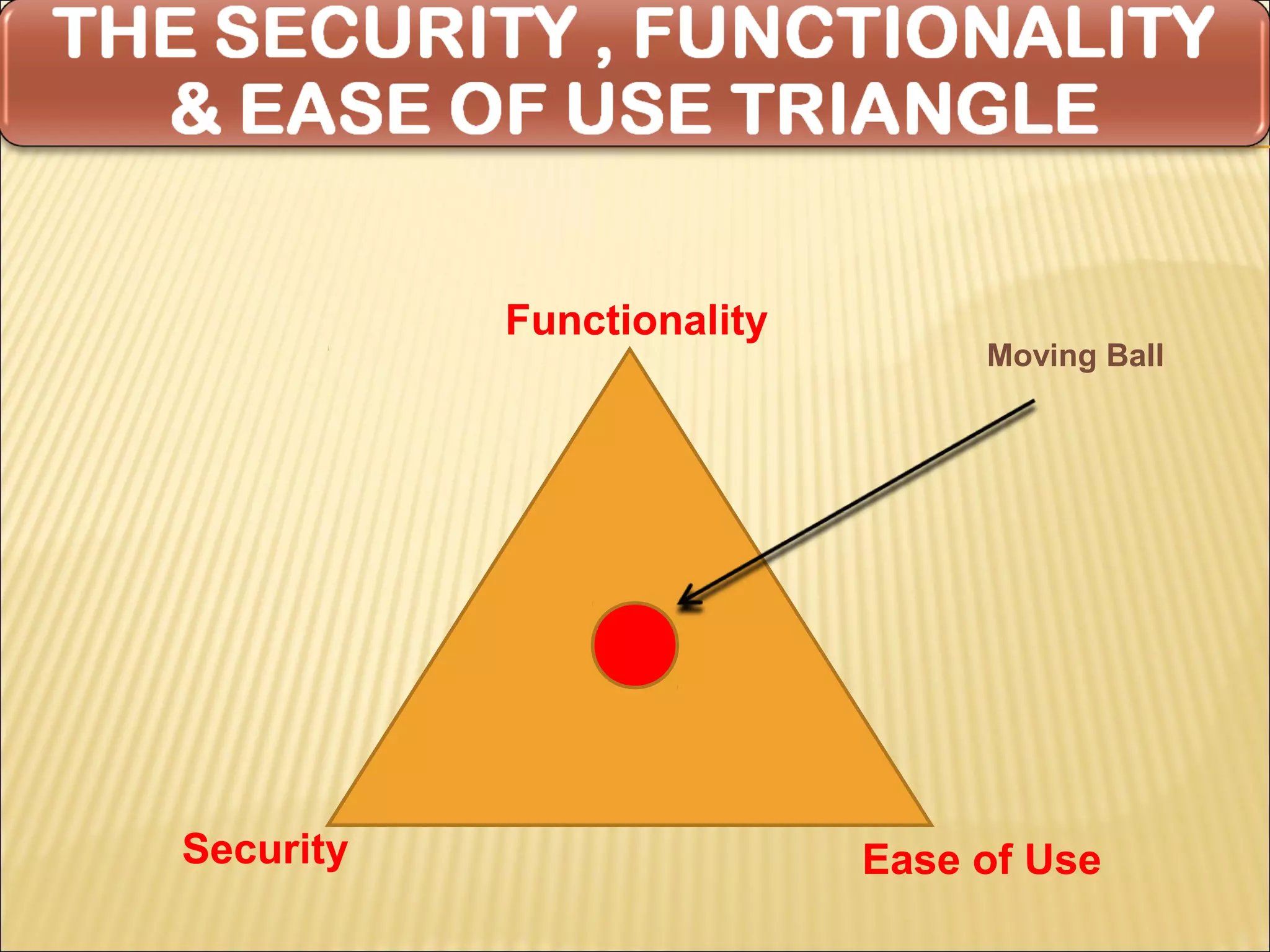
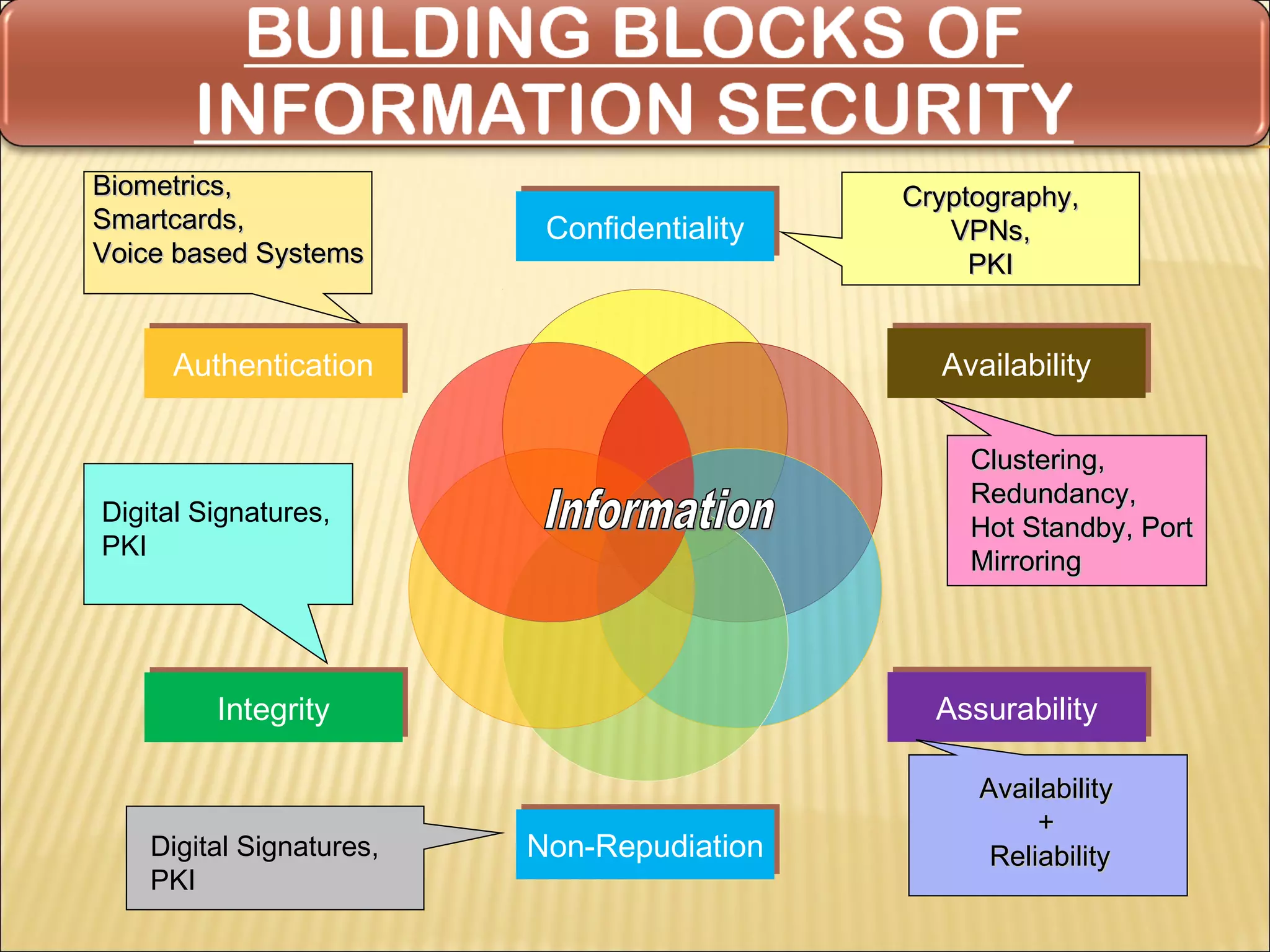
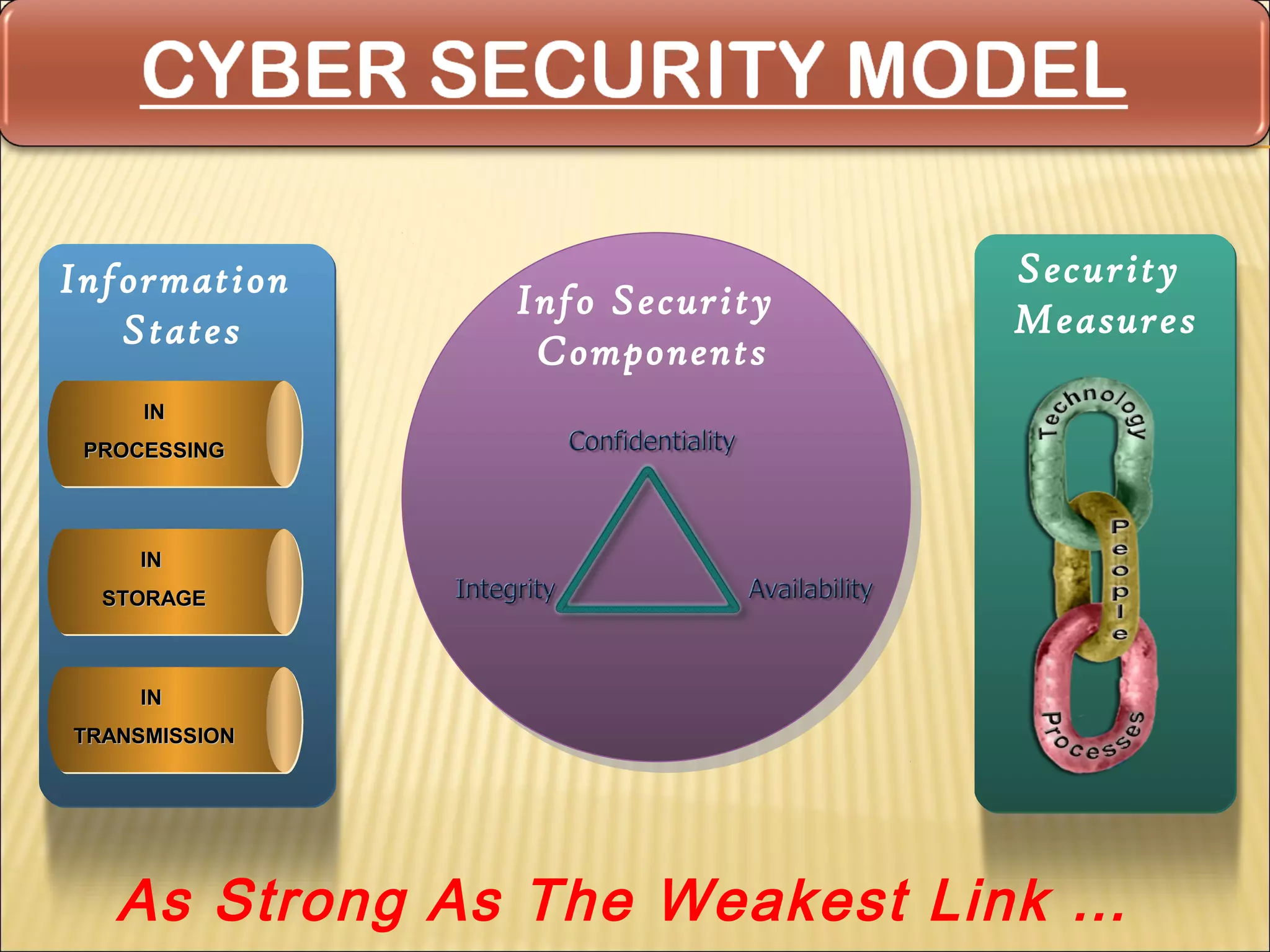
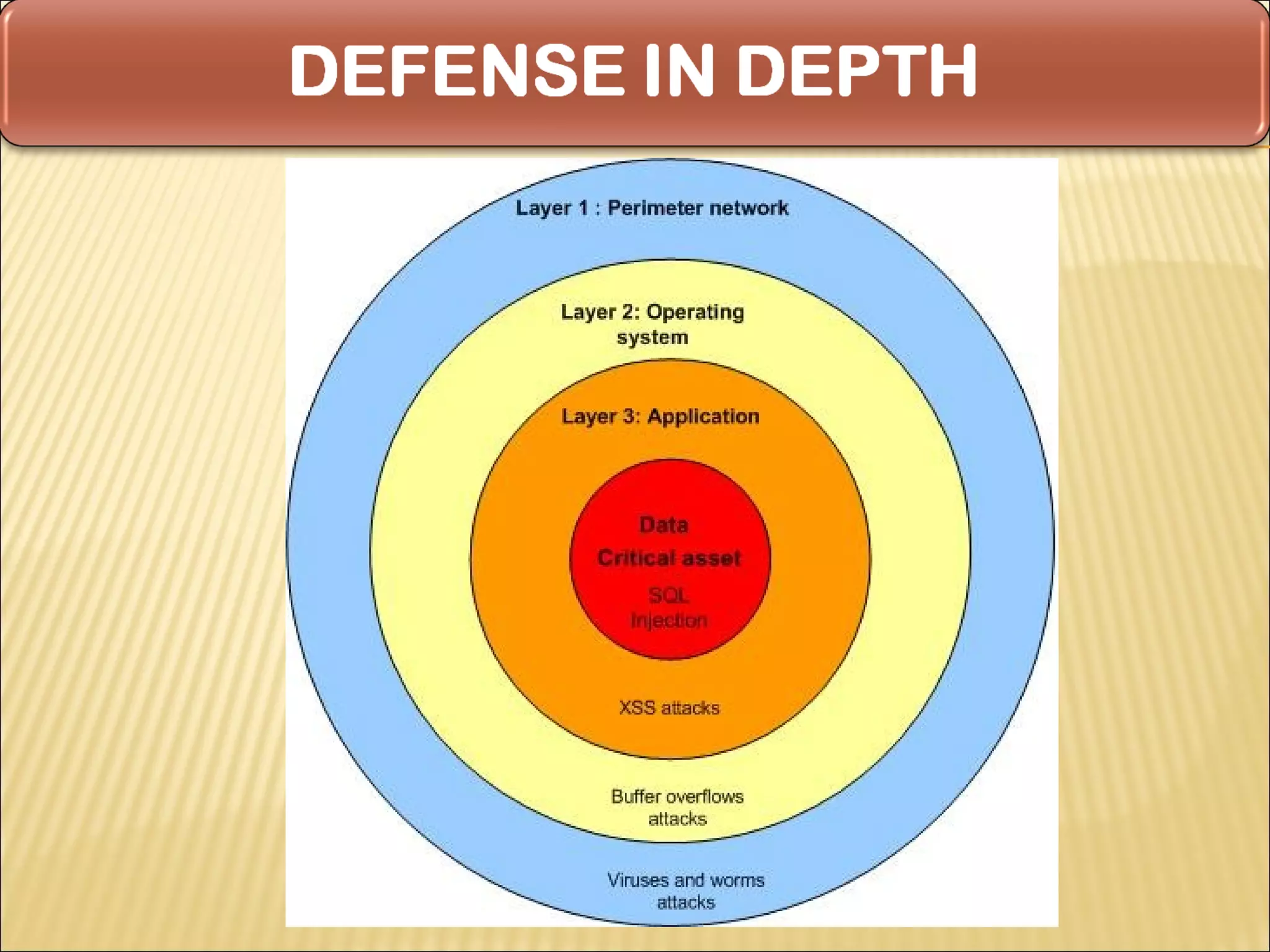
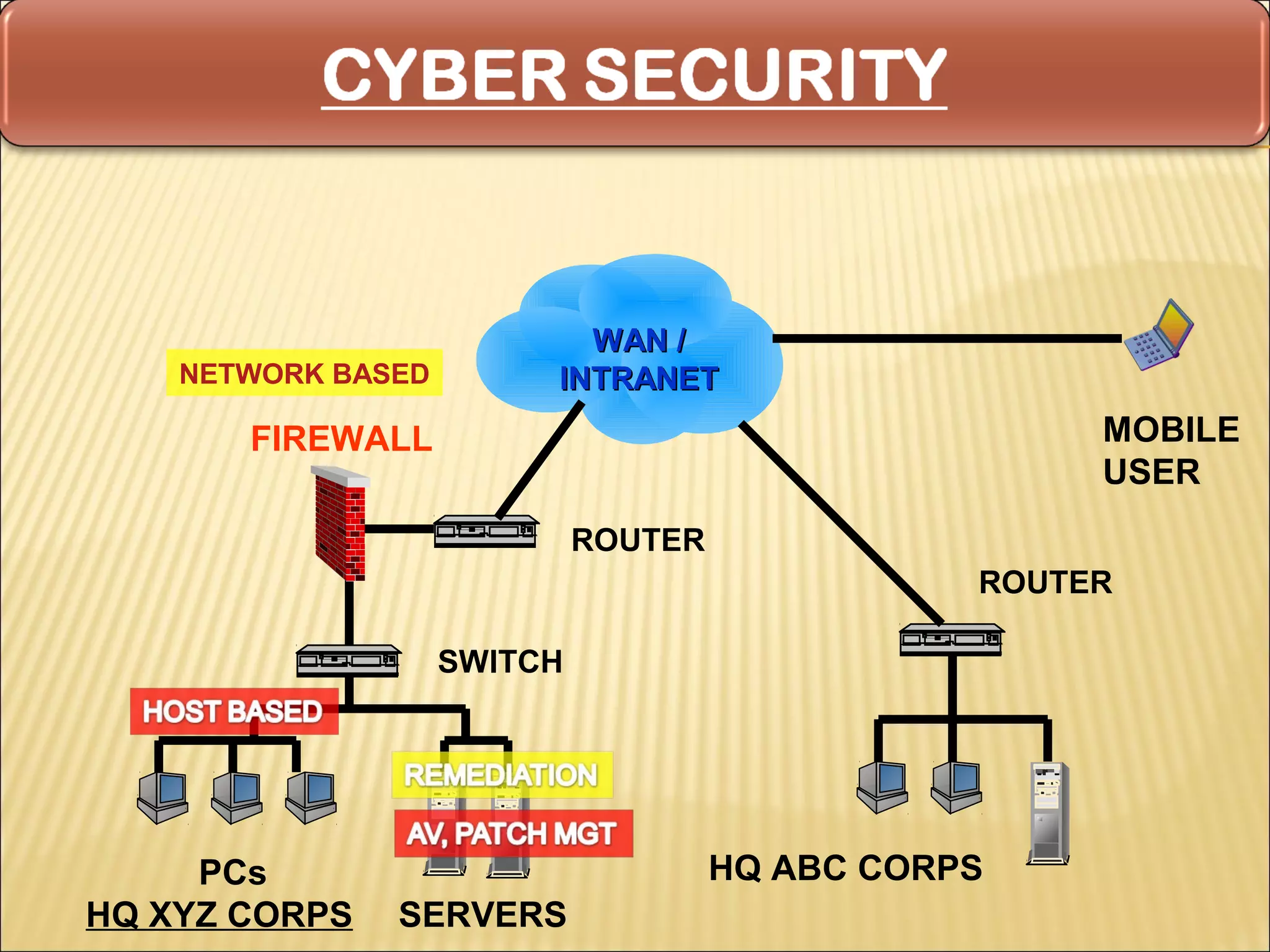
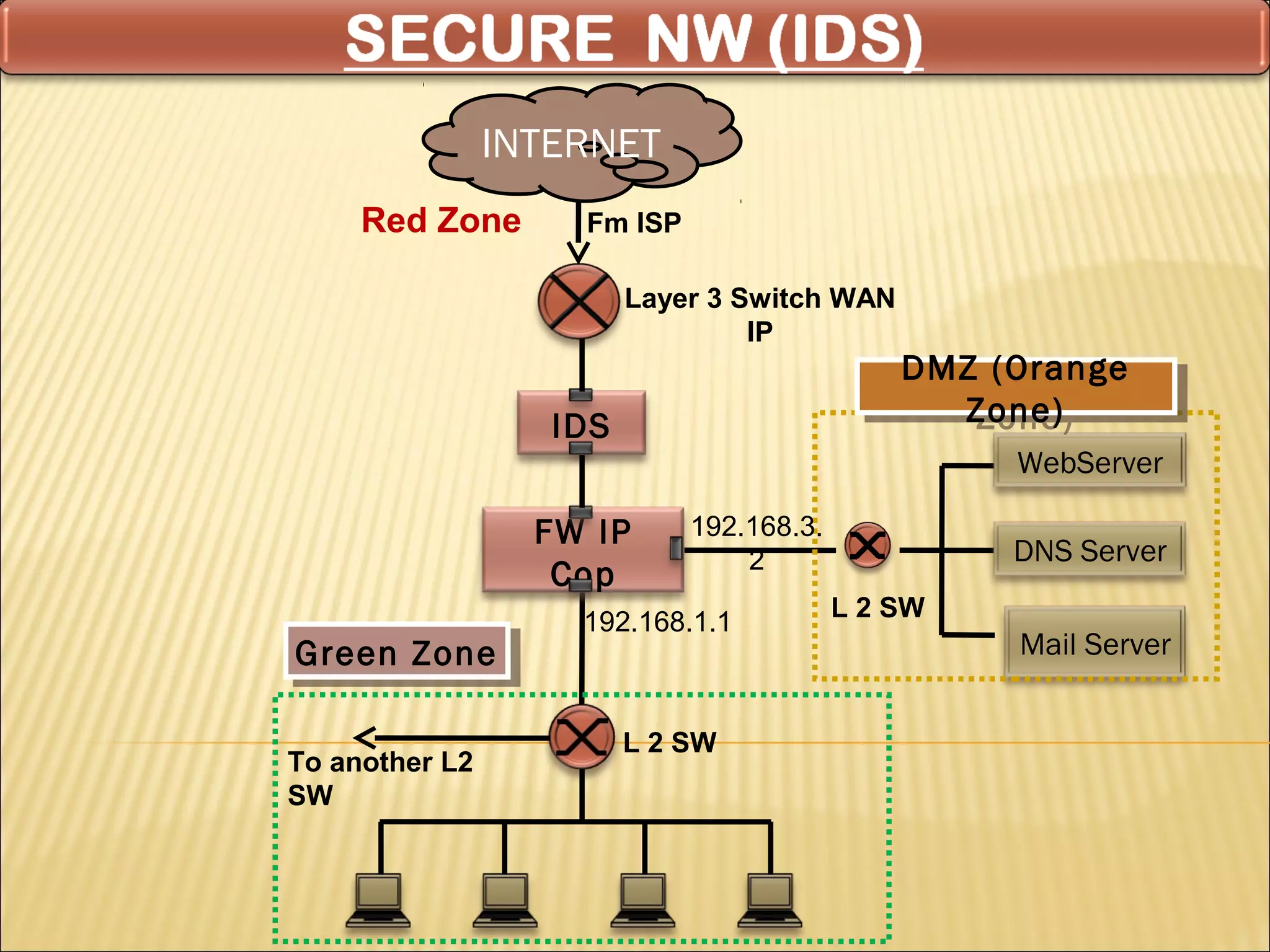
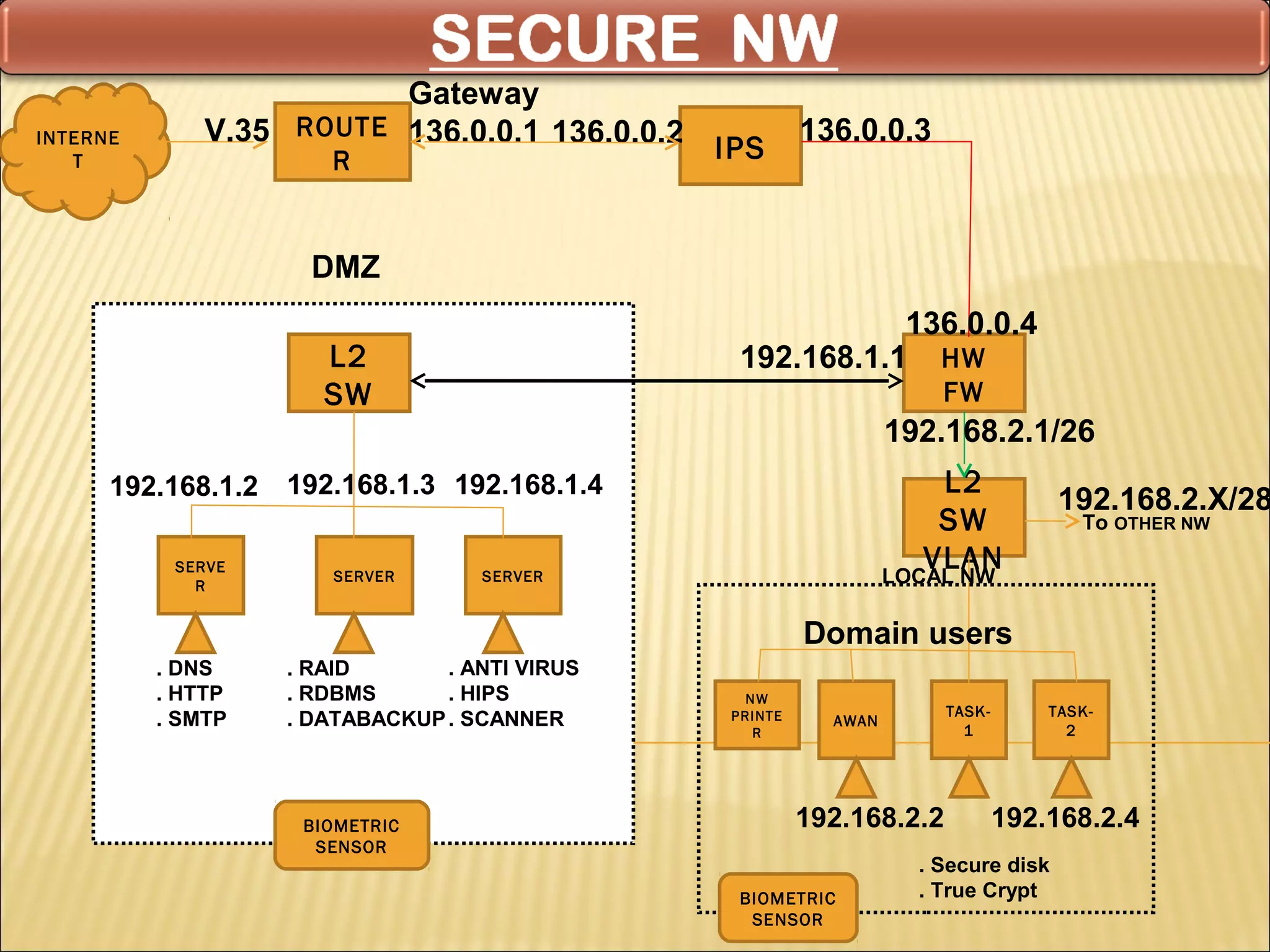
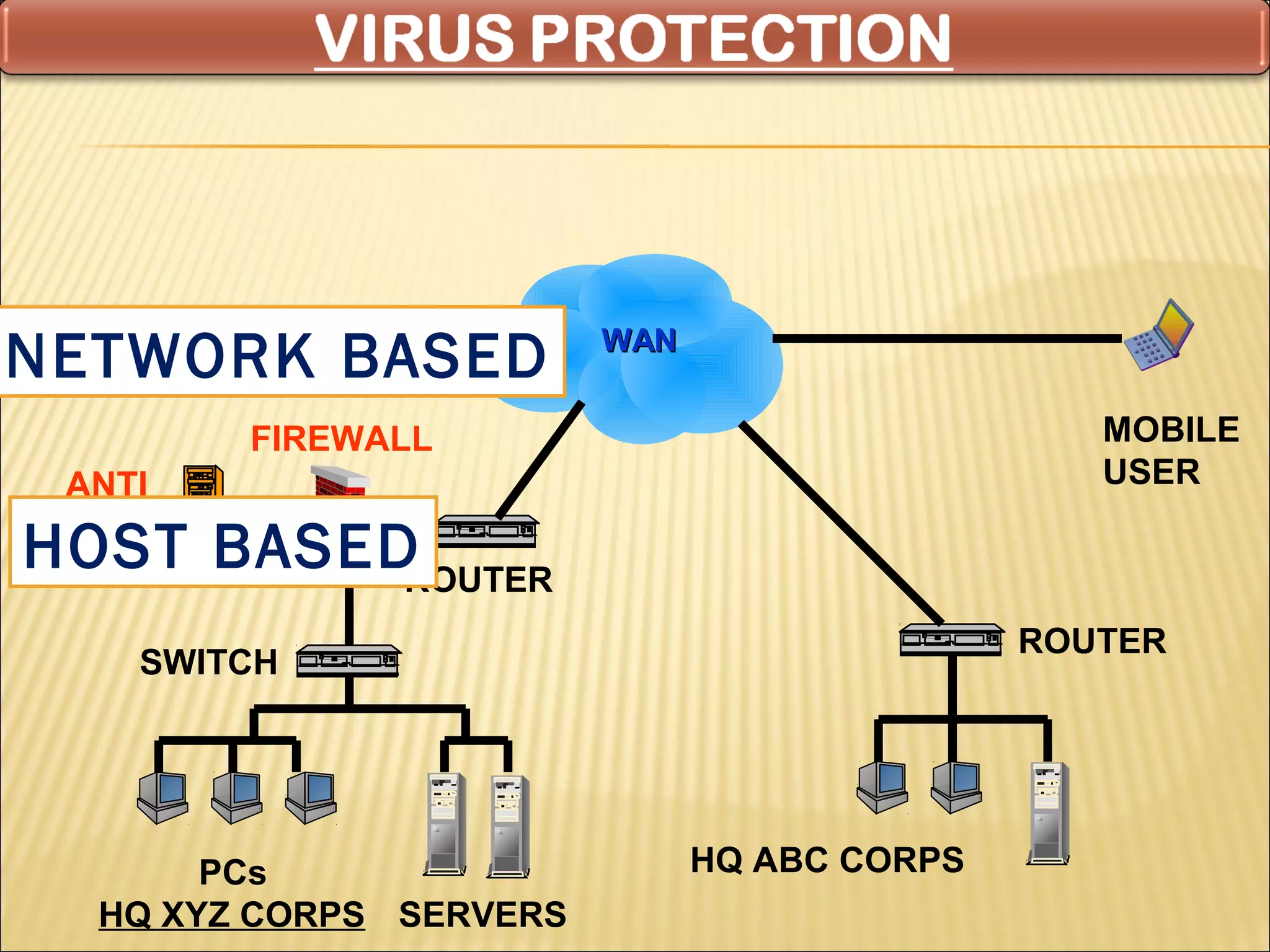
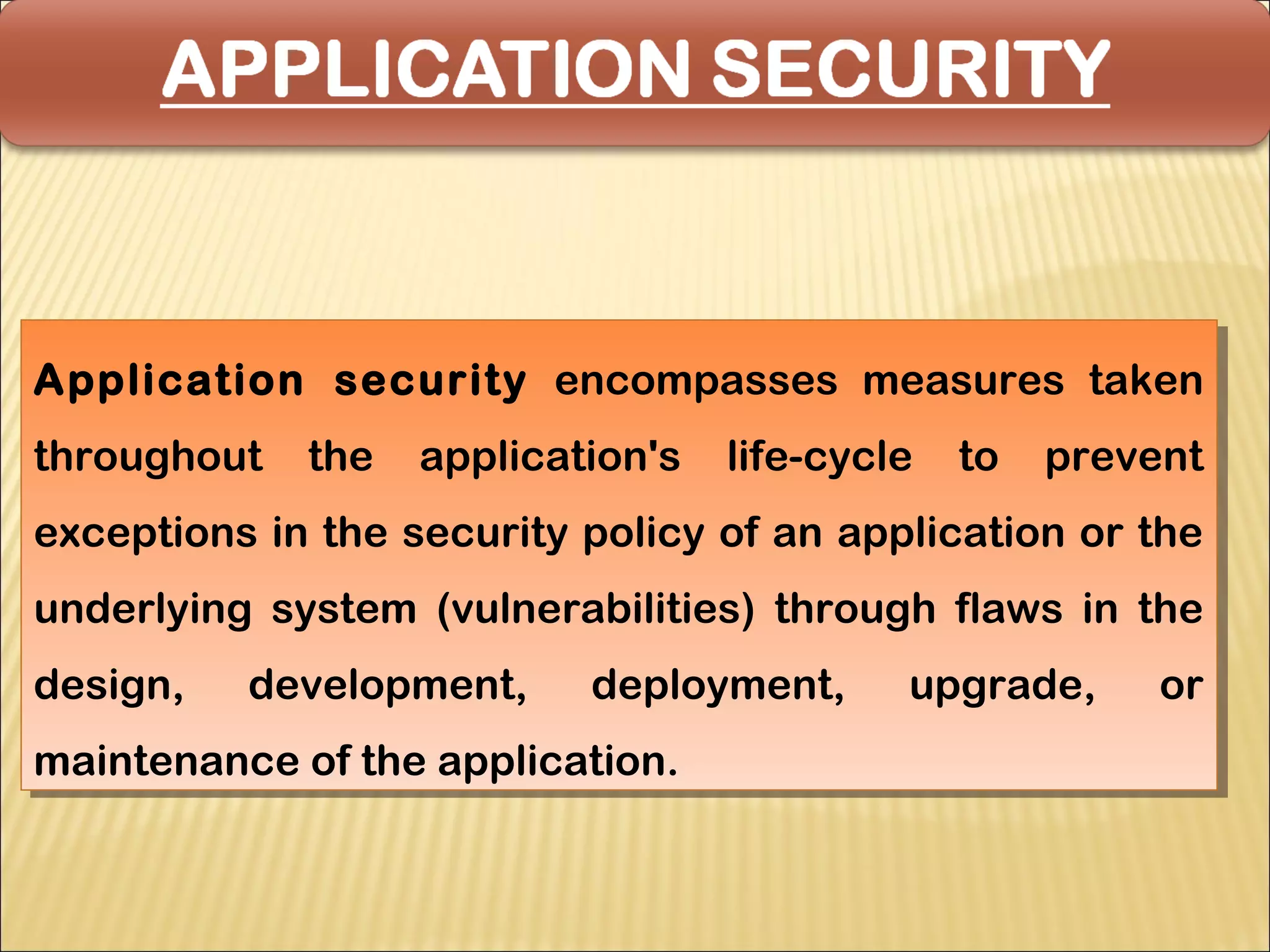
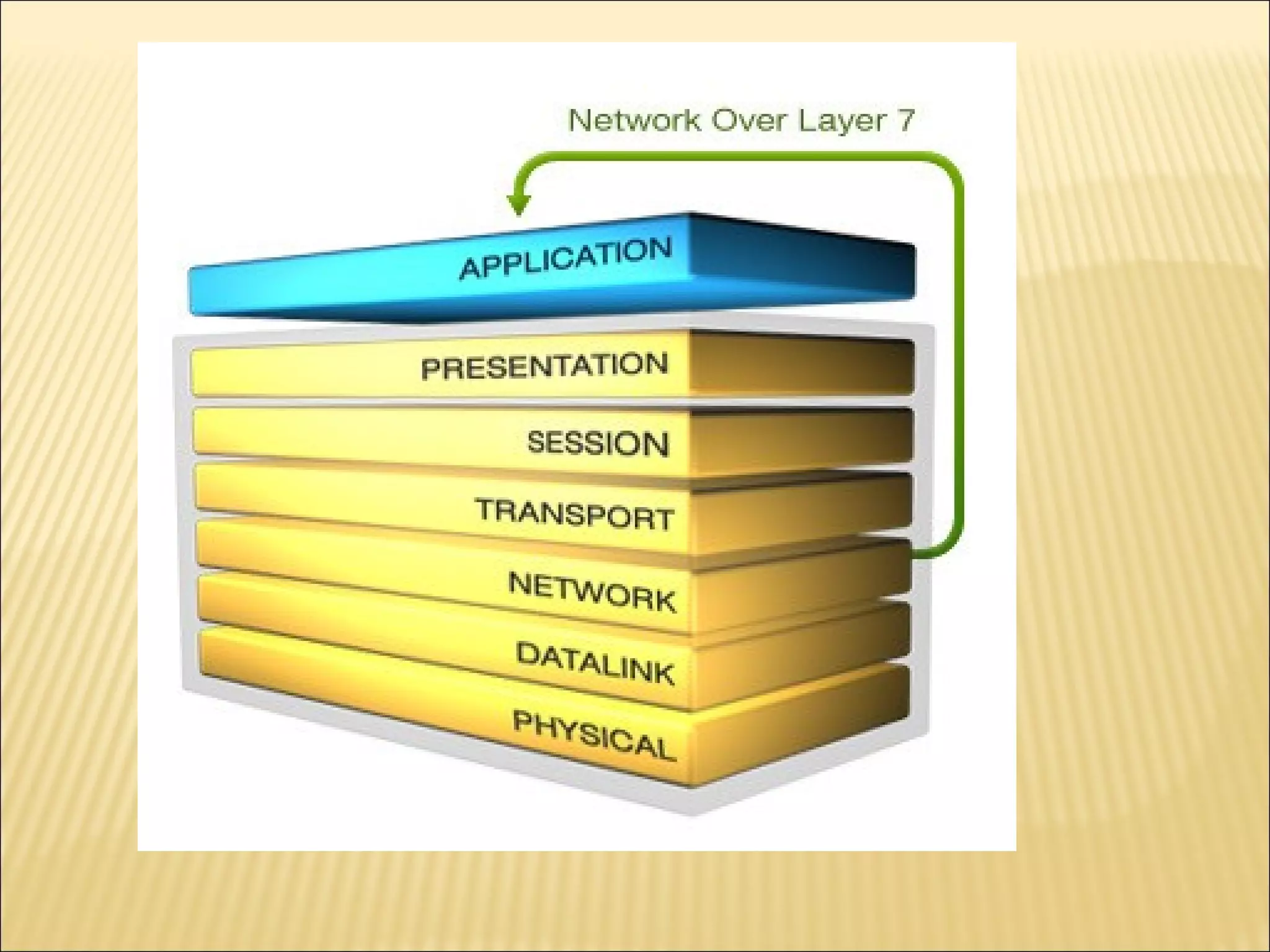
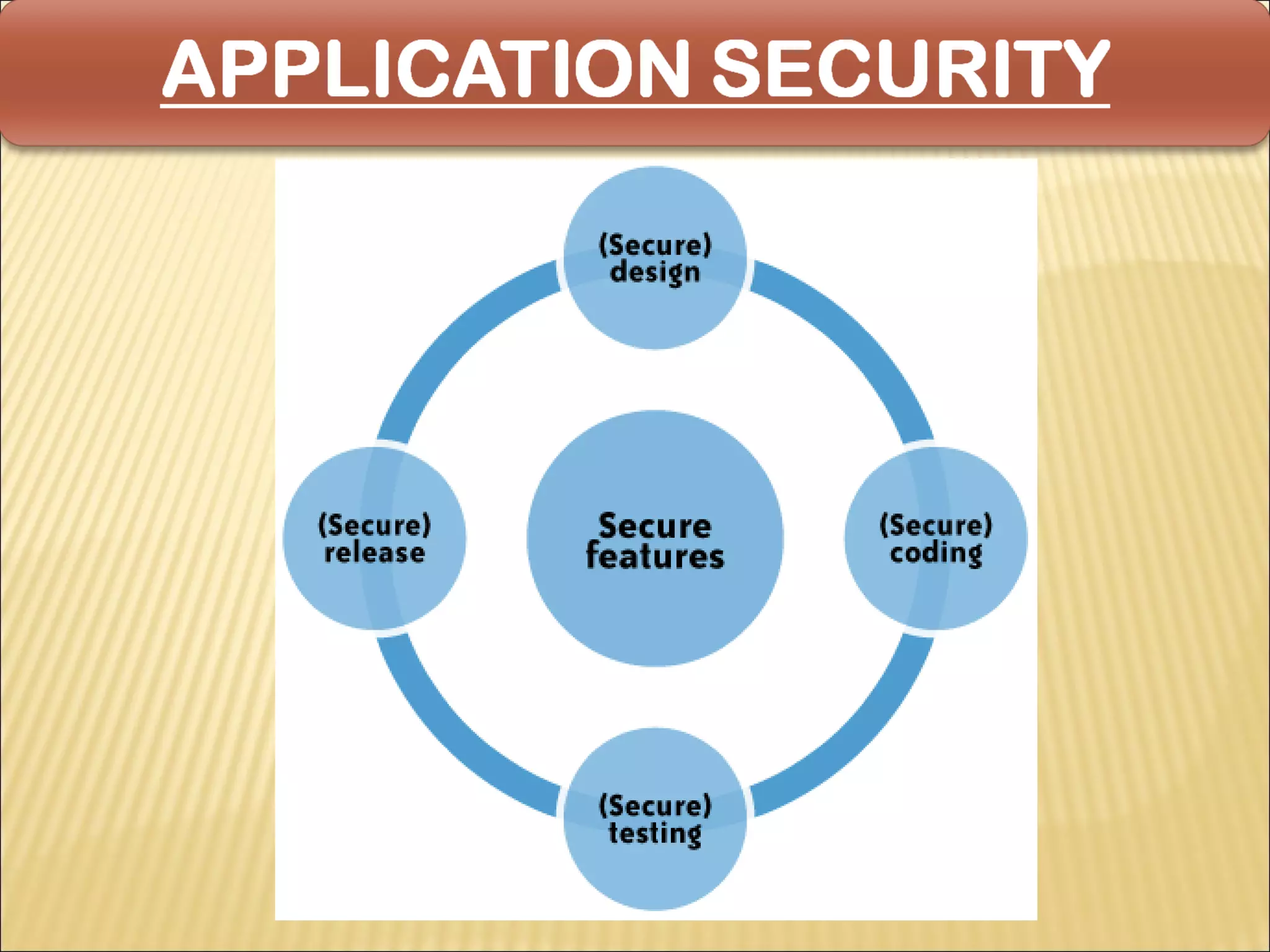
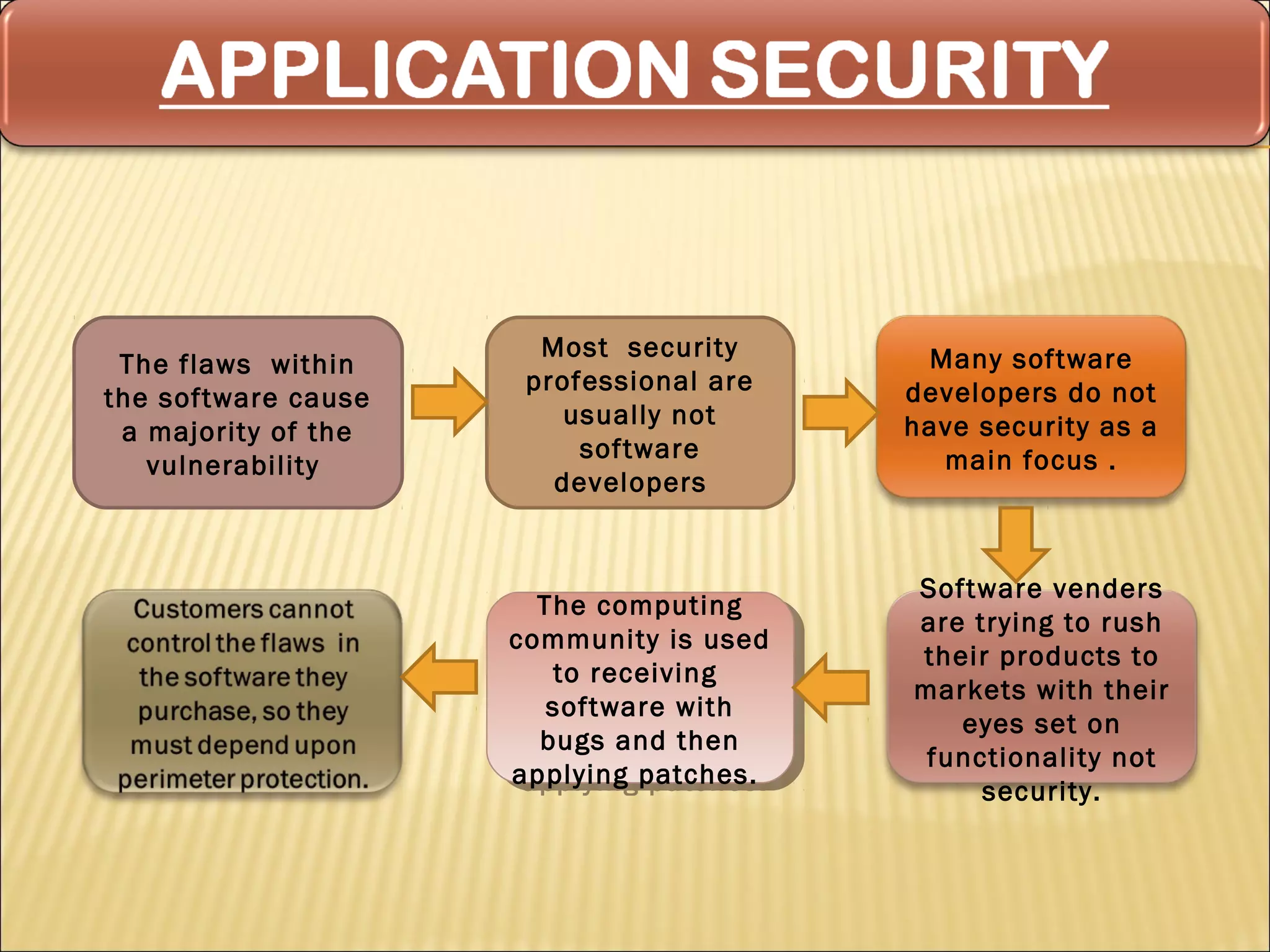
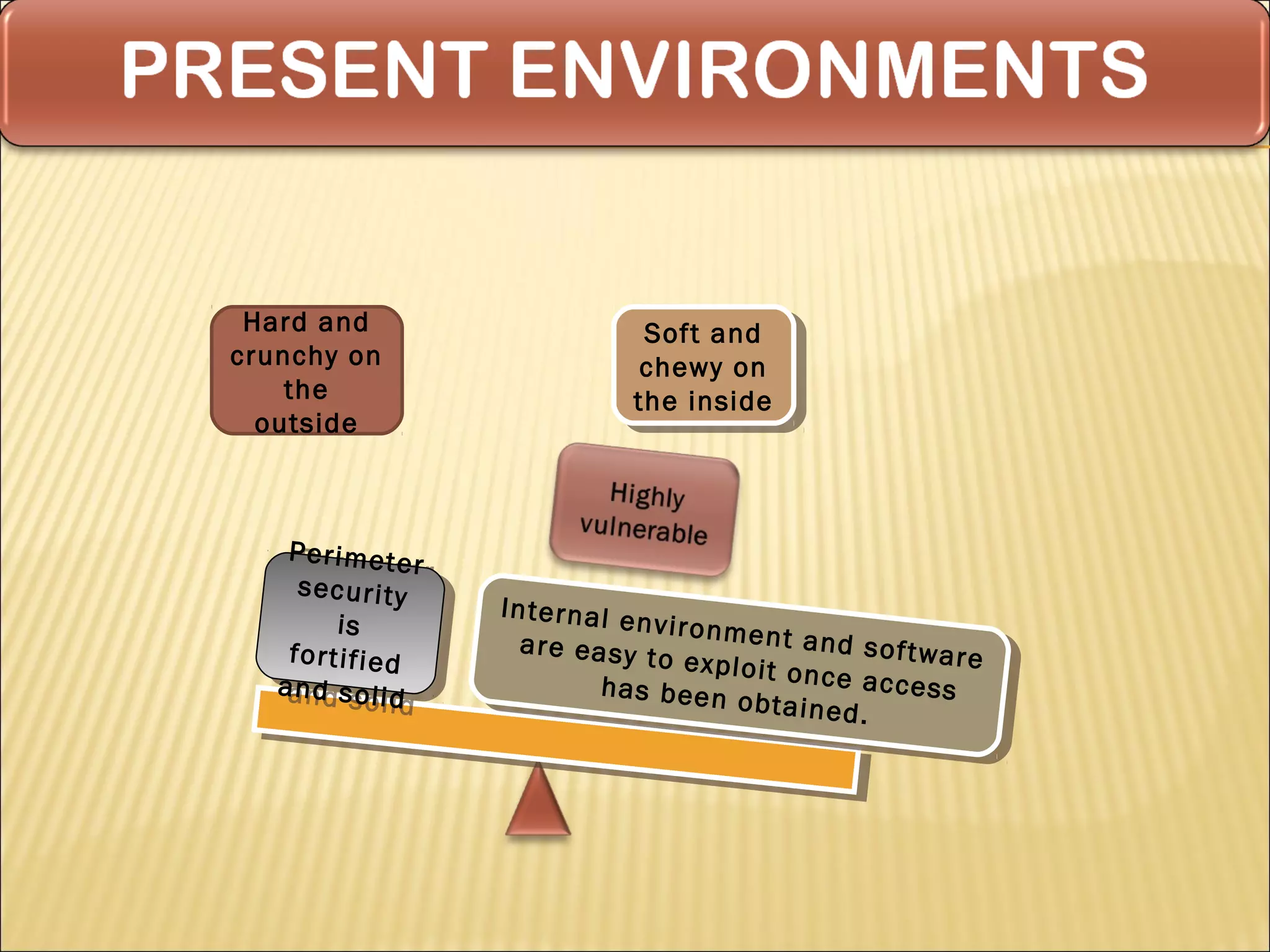
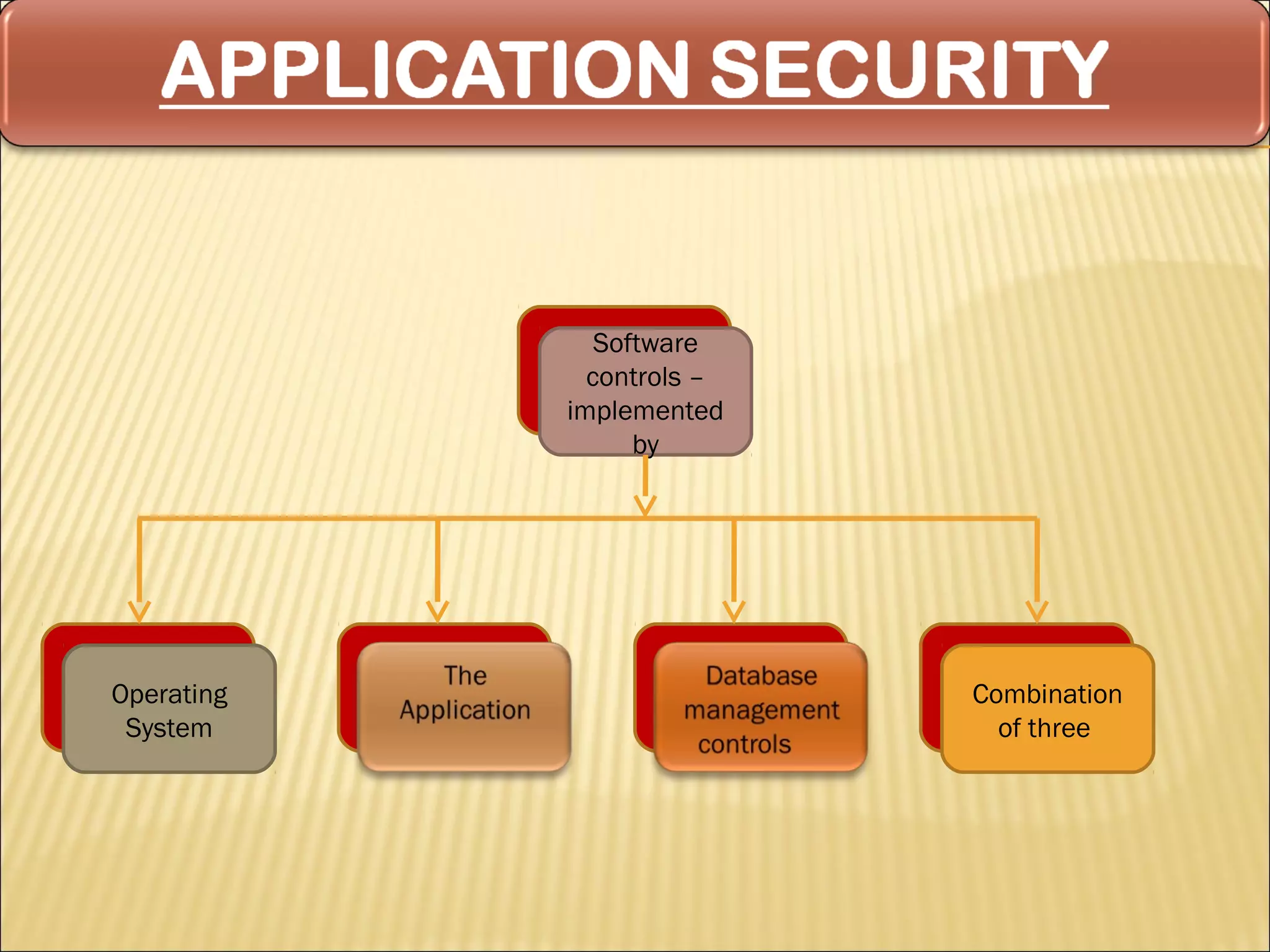
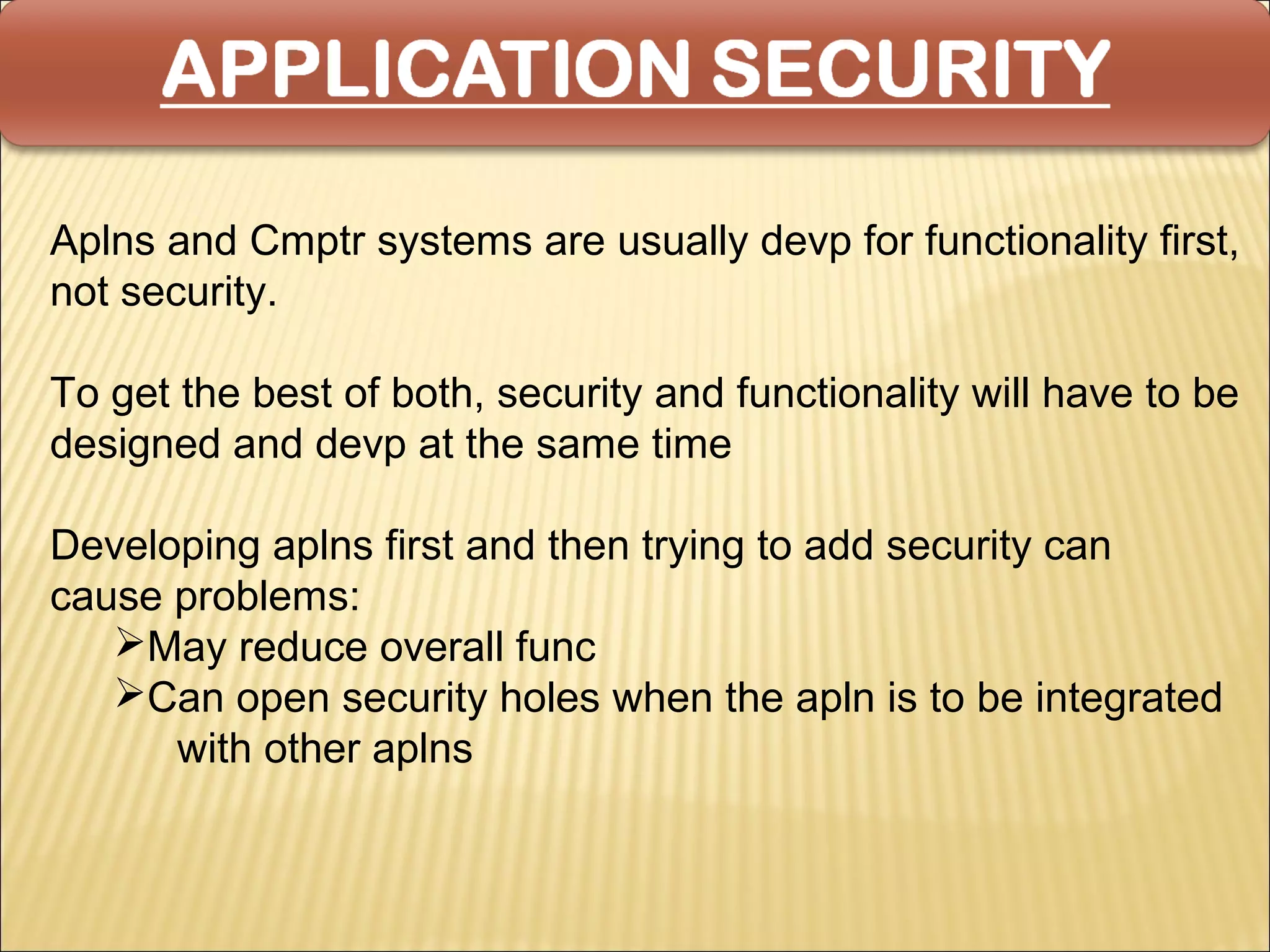
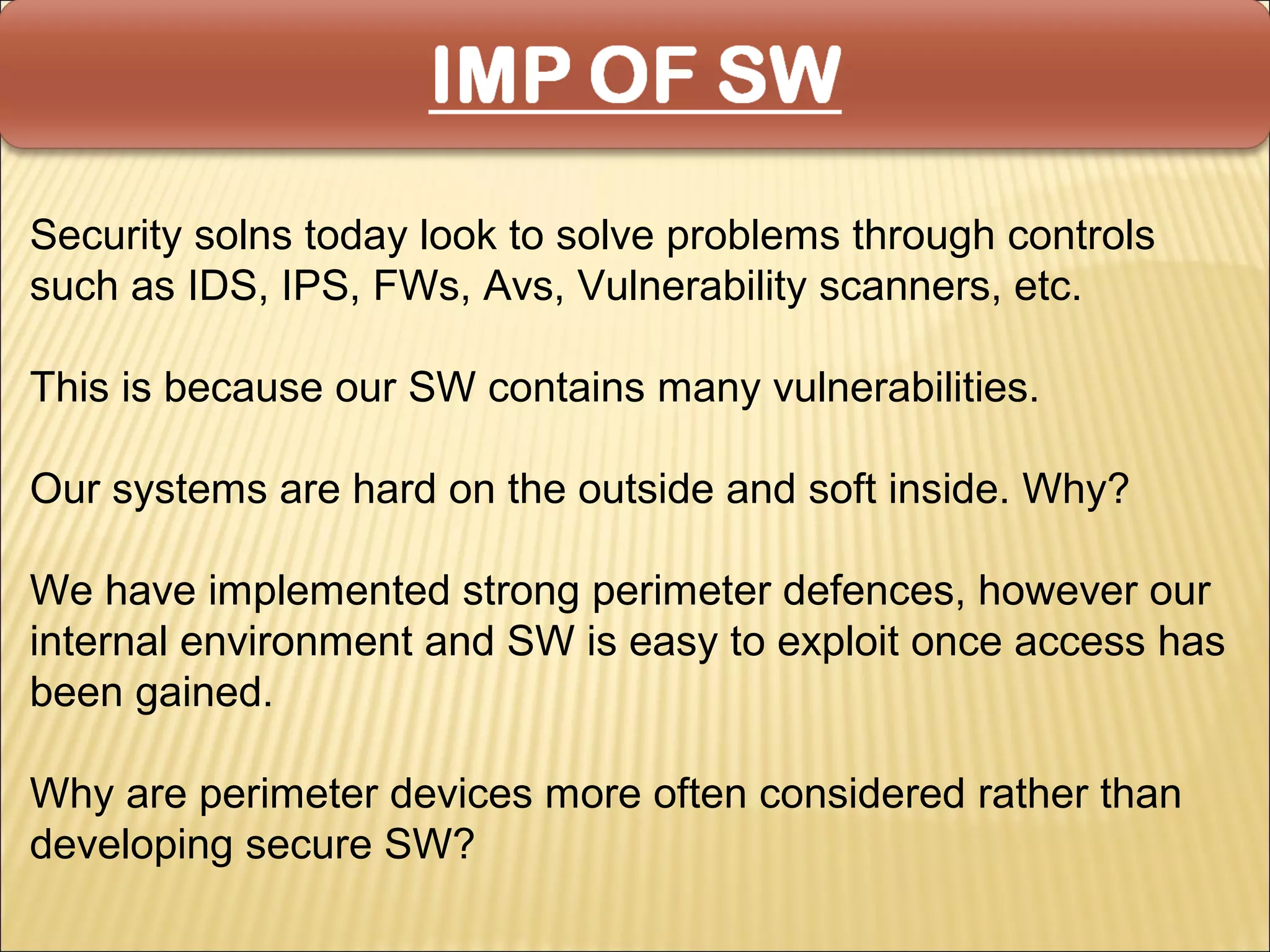
Cyber security at the application level involves protecting applications from vulnerabilities through proper security measures implemented during the software development lifecycle. This includes securing applications from flaws introduced during design, development, deployment, upgrade or maintenance. Application security aims to prevent exceptions to the security policy by addressing vulnerabilities in the application or underlying system. Key aspects of application security include input validation, access controls, and output encoding.