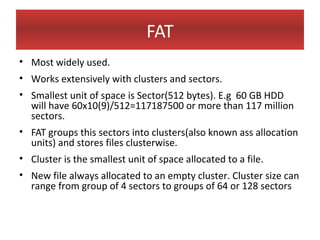
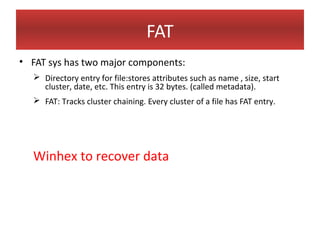
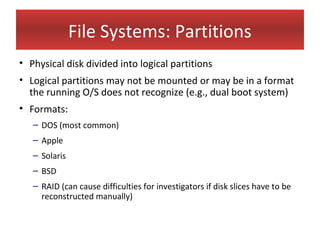
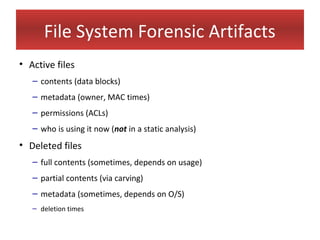
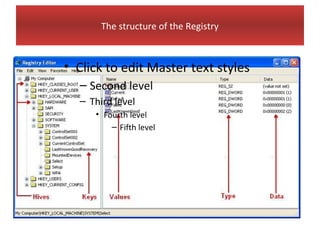
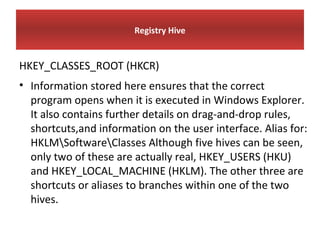
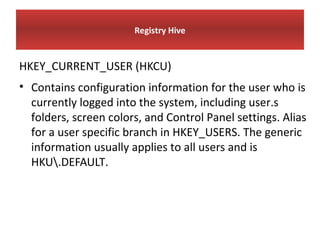
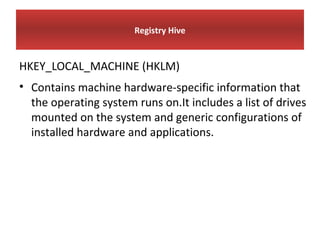
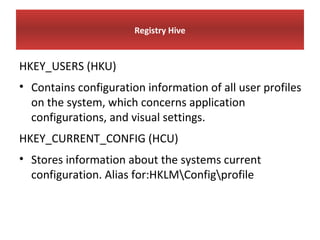
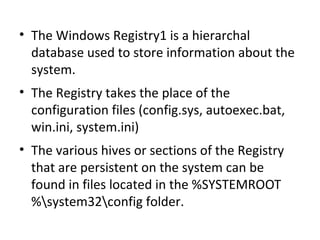
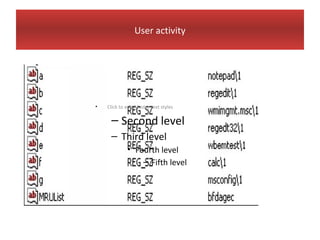
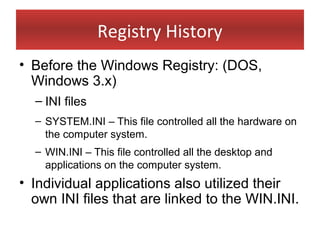
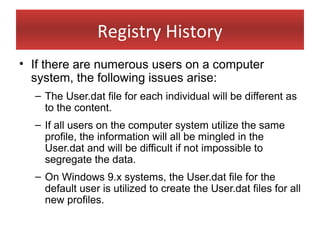
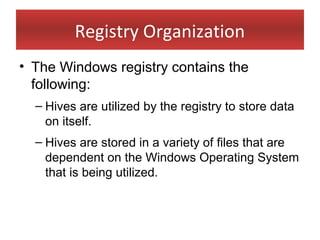
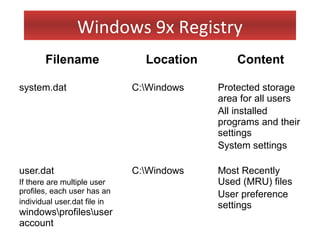
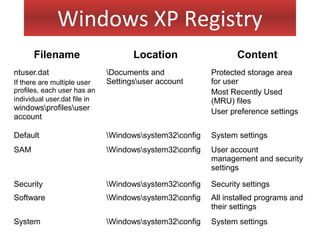
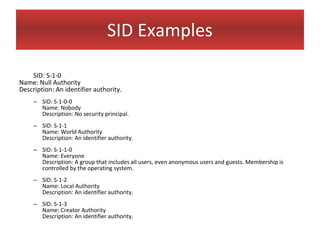
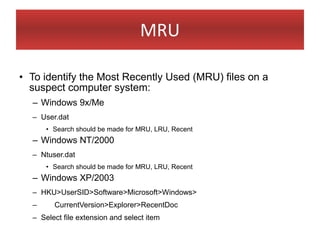
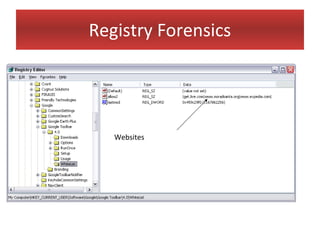
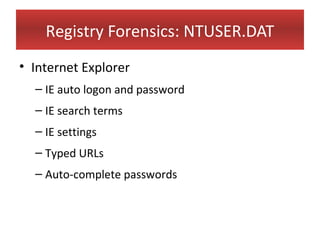
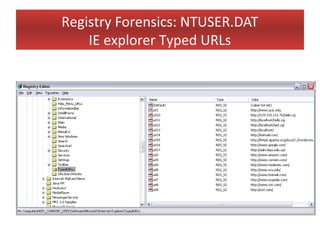
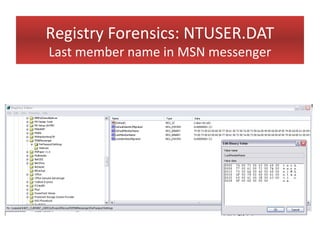
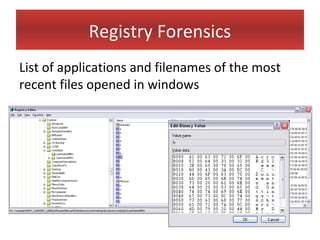
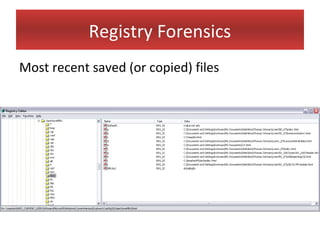
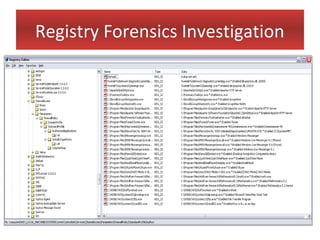
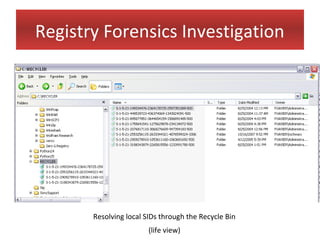
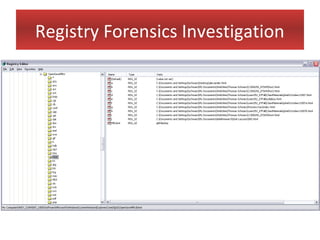
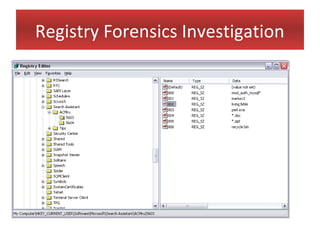
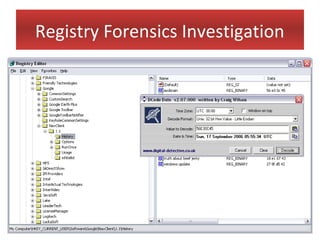
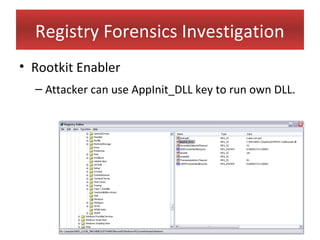
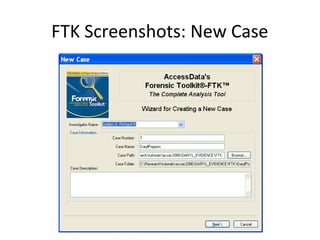
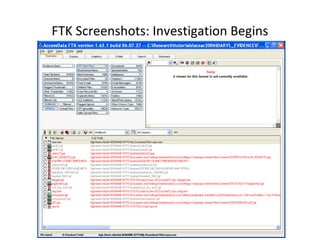
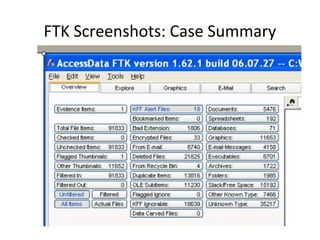
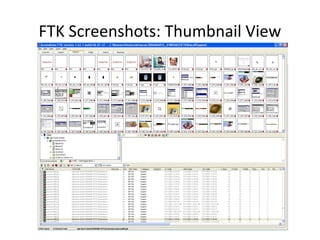
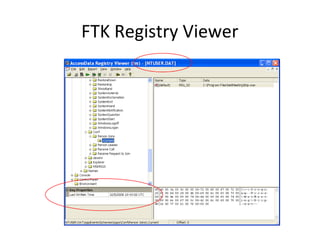
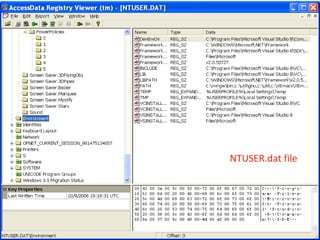
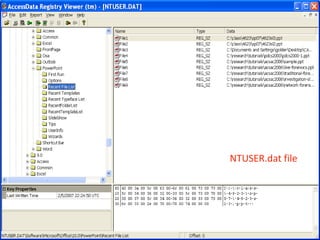
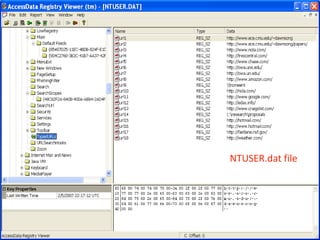
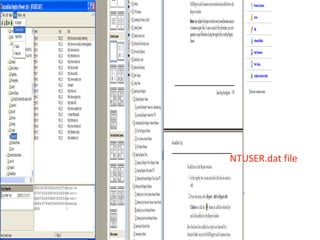
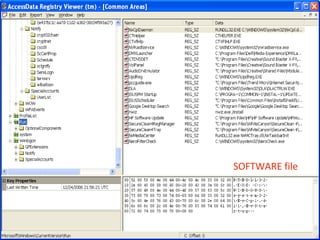
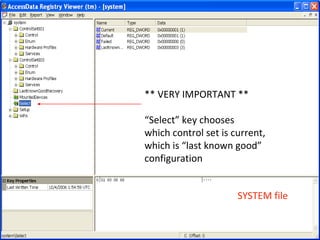
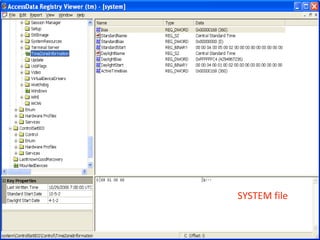
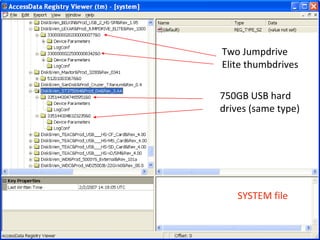
This document provides an overview of Windows file systems and how they are used for digital forensics investigations. It discusses the File Allocation Table (FAT) file system and how it tracks file clusters. It also describes the New Technology File System (NTFS) and how it stores file metadata and tracks unused data clusters. The document outlines how file deletion, renaming and moving works in Windows, and artifacts that can be recovered from deleted files. It identifies several useful file types for forensic analysis, like shortcut files, the Recycle Bin, print spool files and registry keys.