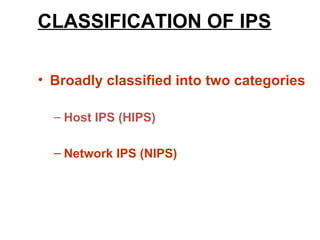
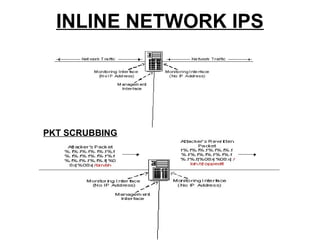
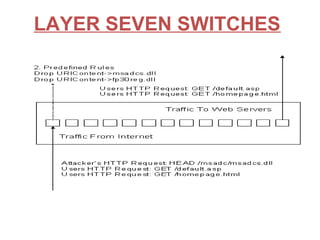
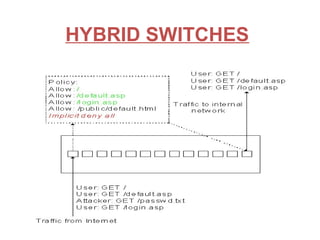
An intrusion detection system (IDS) monitors network traffic and system activities for suspicious activity that could indicate a security threat or attack. An IDS analyzes patterns in traffic to identify potential threats. There are network IDS that monitor entire network traffic and host IDS that monitor individual systems. An IDS detects threats but does not prevent them. An intrusion prevention system (IPS) can detect and prevent threats by blocking malicious traffic in real-time. An IPS combines IDS detection capabilities with preventative blocking functions. Common types of IPS include inline network IPS, layer 7 switches, application firewalls, and hybrid switches.