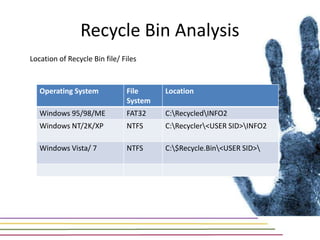
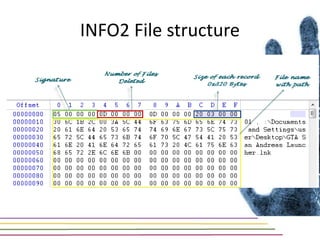
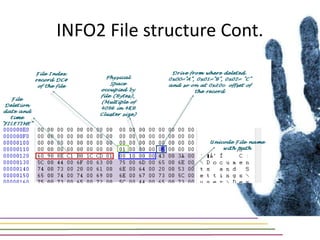
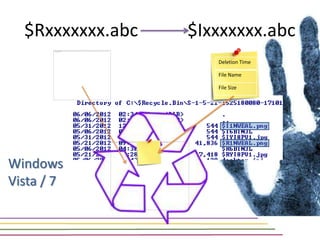
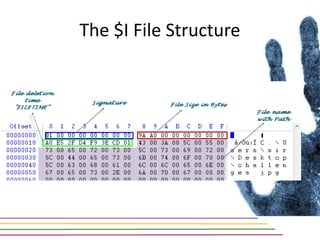
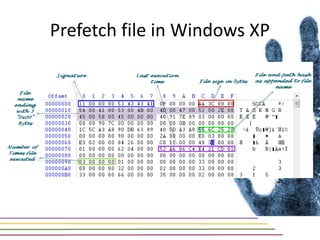
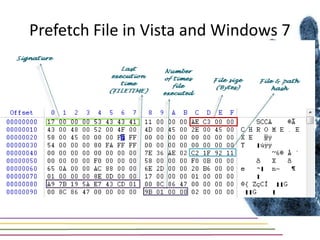
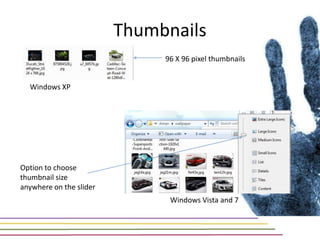
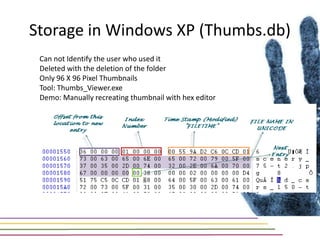
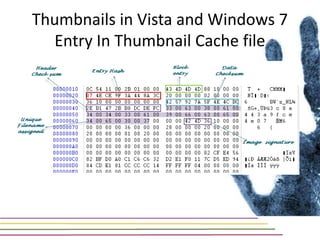
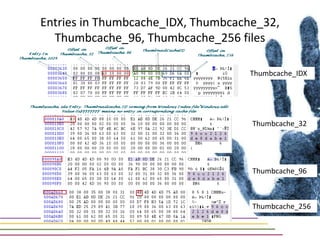
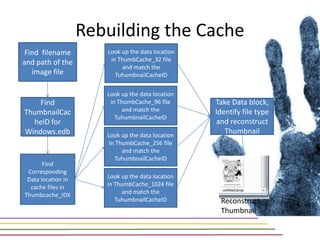
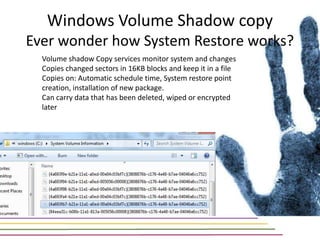
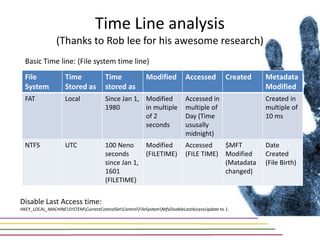
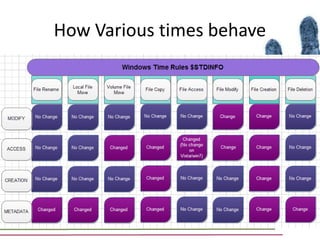
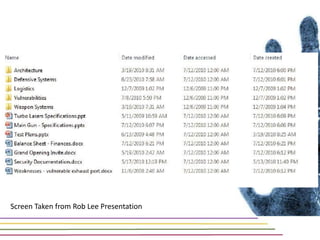
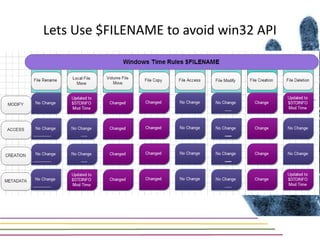
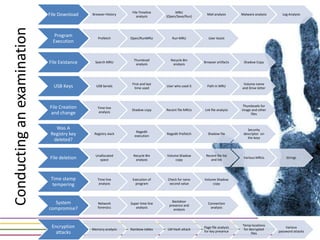
This document discusses various aspects of forensic analysis in Windows operating systems. It describes the location of recycle bin files, prefetch files, thumbnail caches, and volume shadow copies in different versions of Windows. It also discusses how timelines can be analyzed from files, registry entries, and other artifacts to reconstruct system activity. Time stamps are stored differently depending on the file system. The document provides examples of analyzing timelines, thumbnails, recycle bins, and shadow copies to investigate activity on a system.