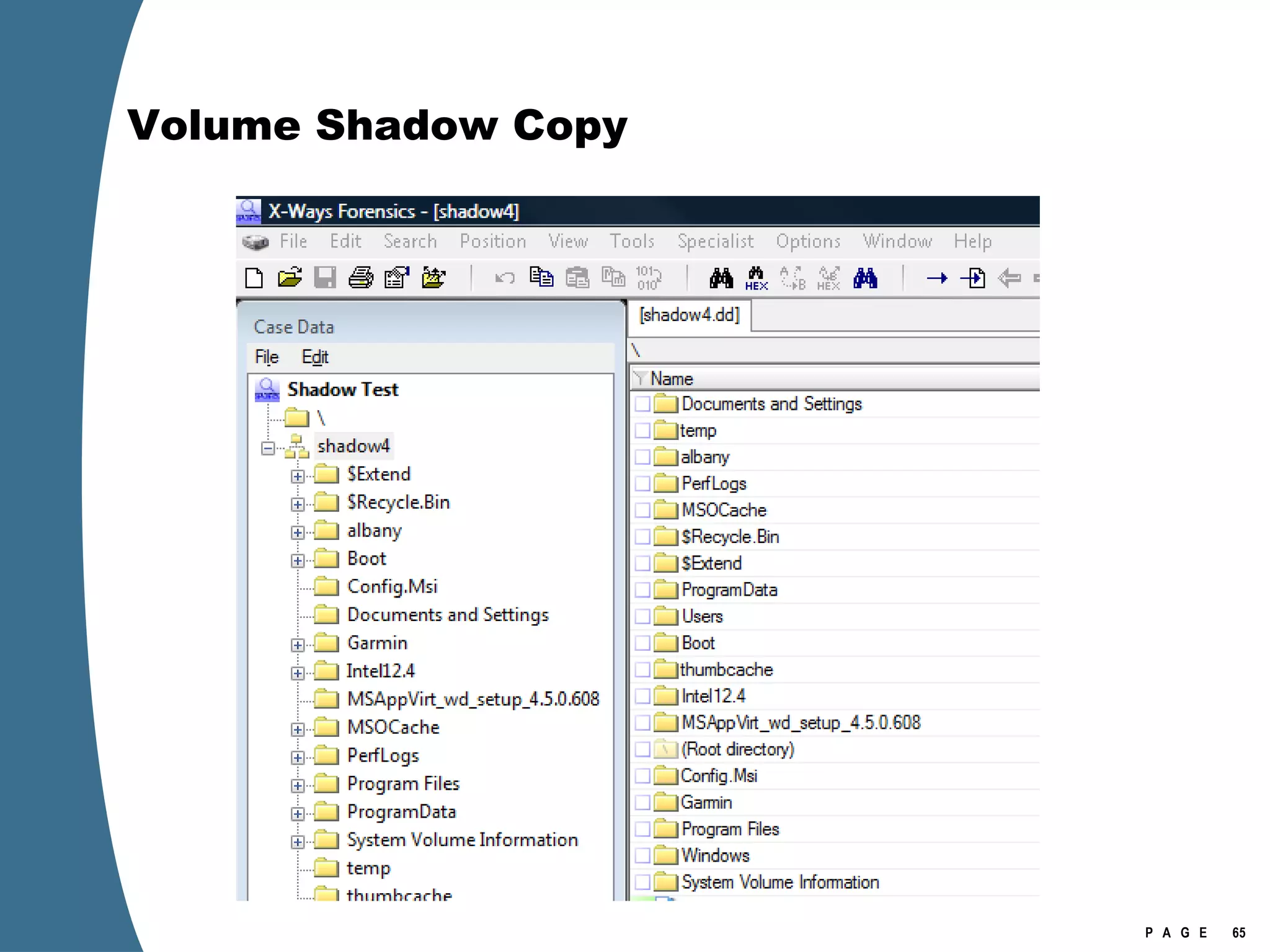
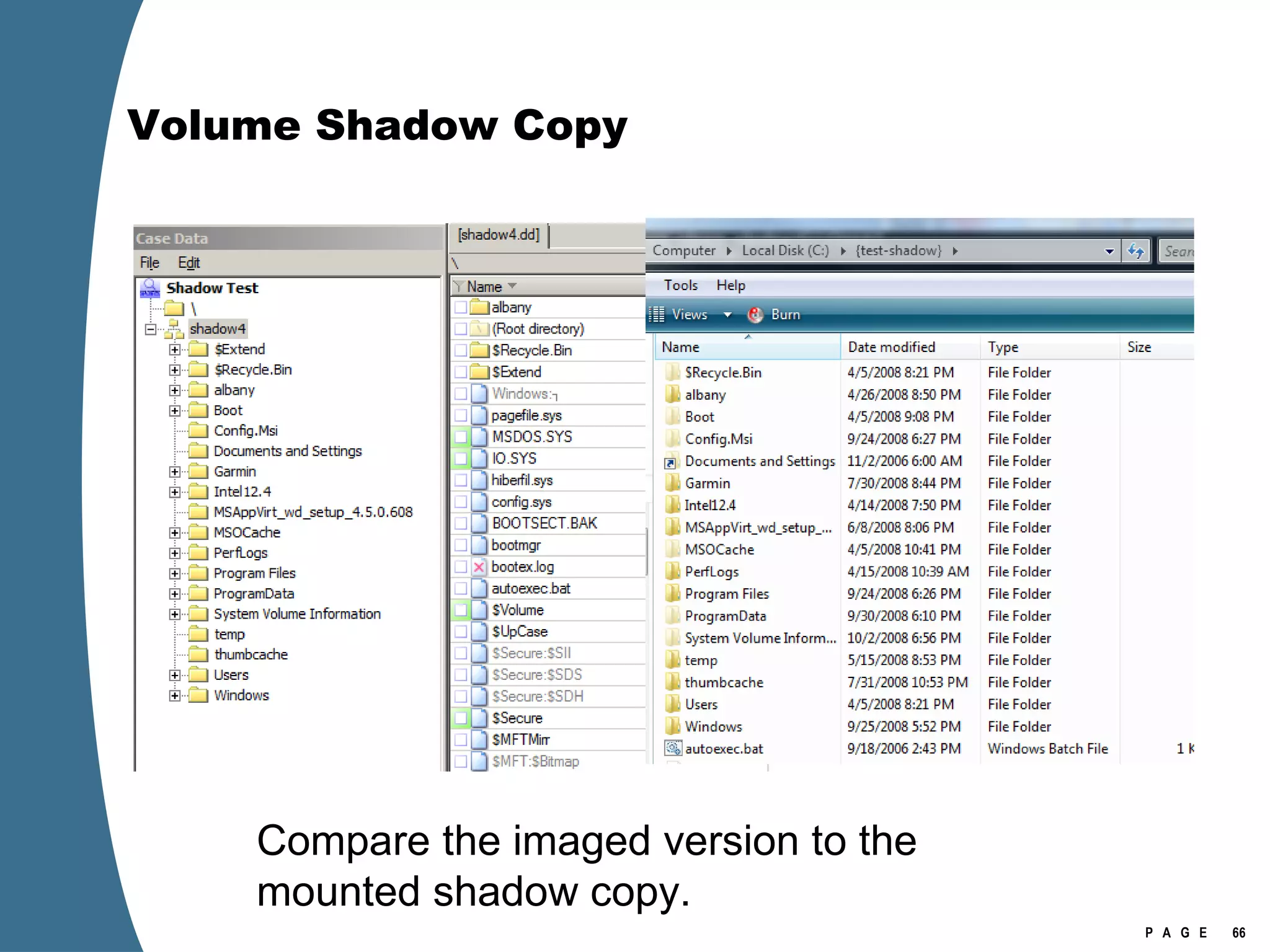
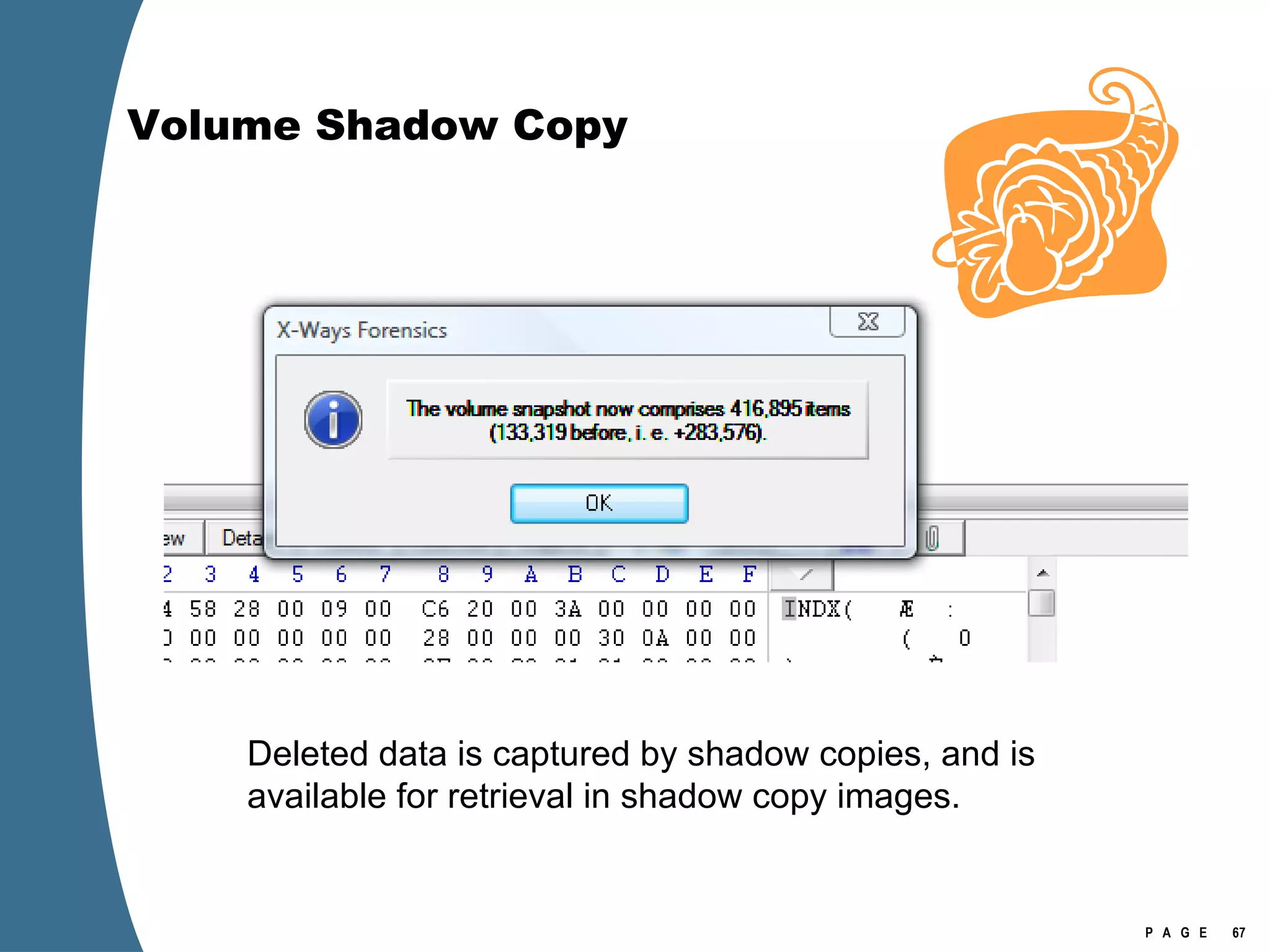
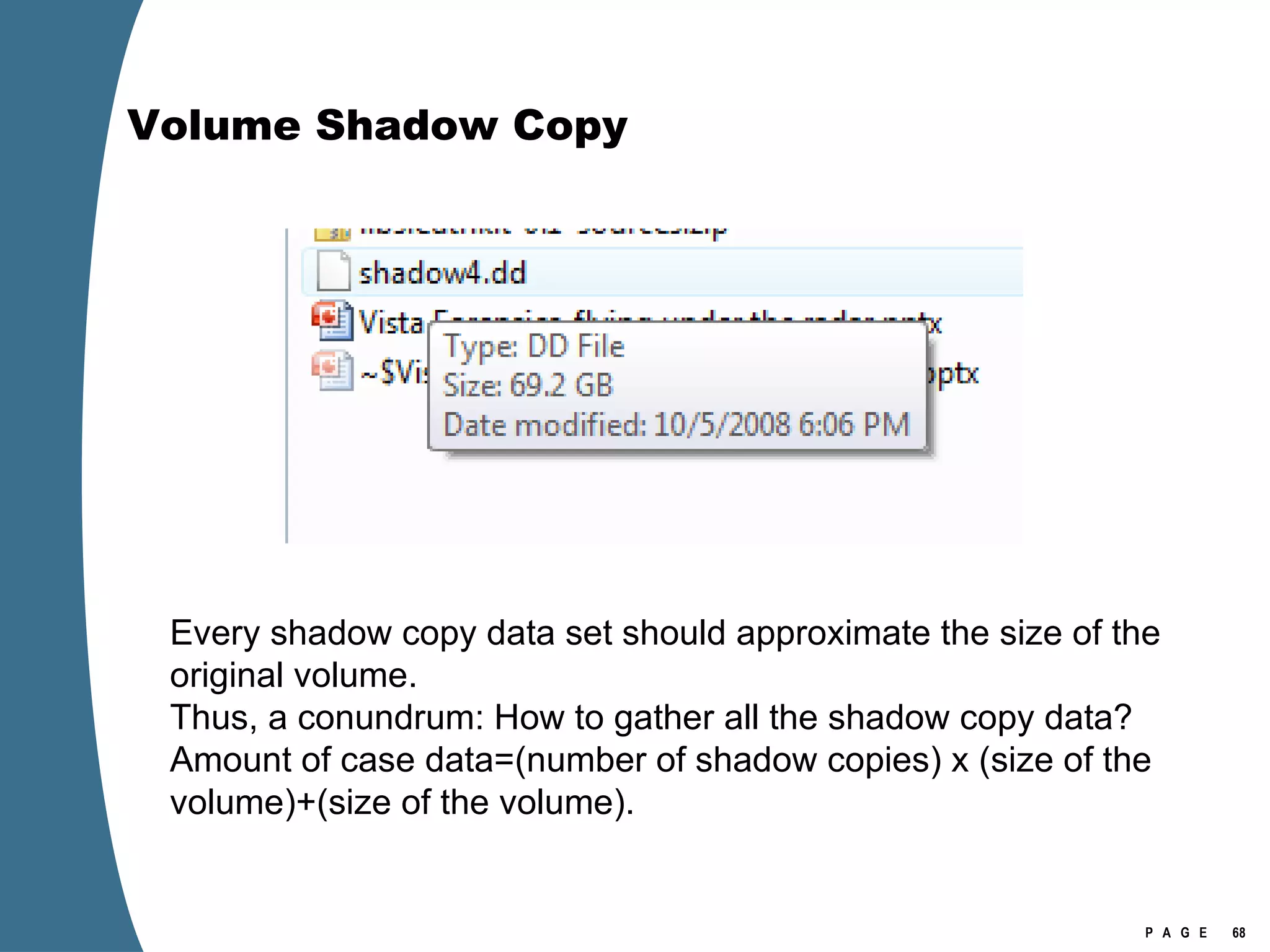
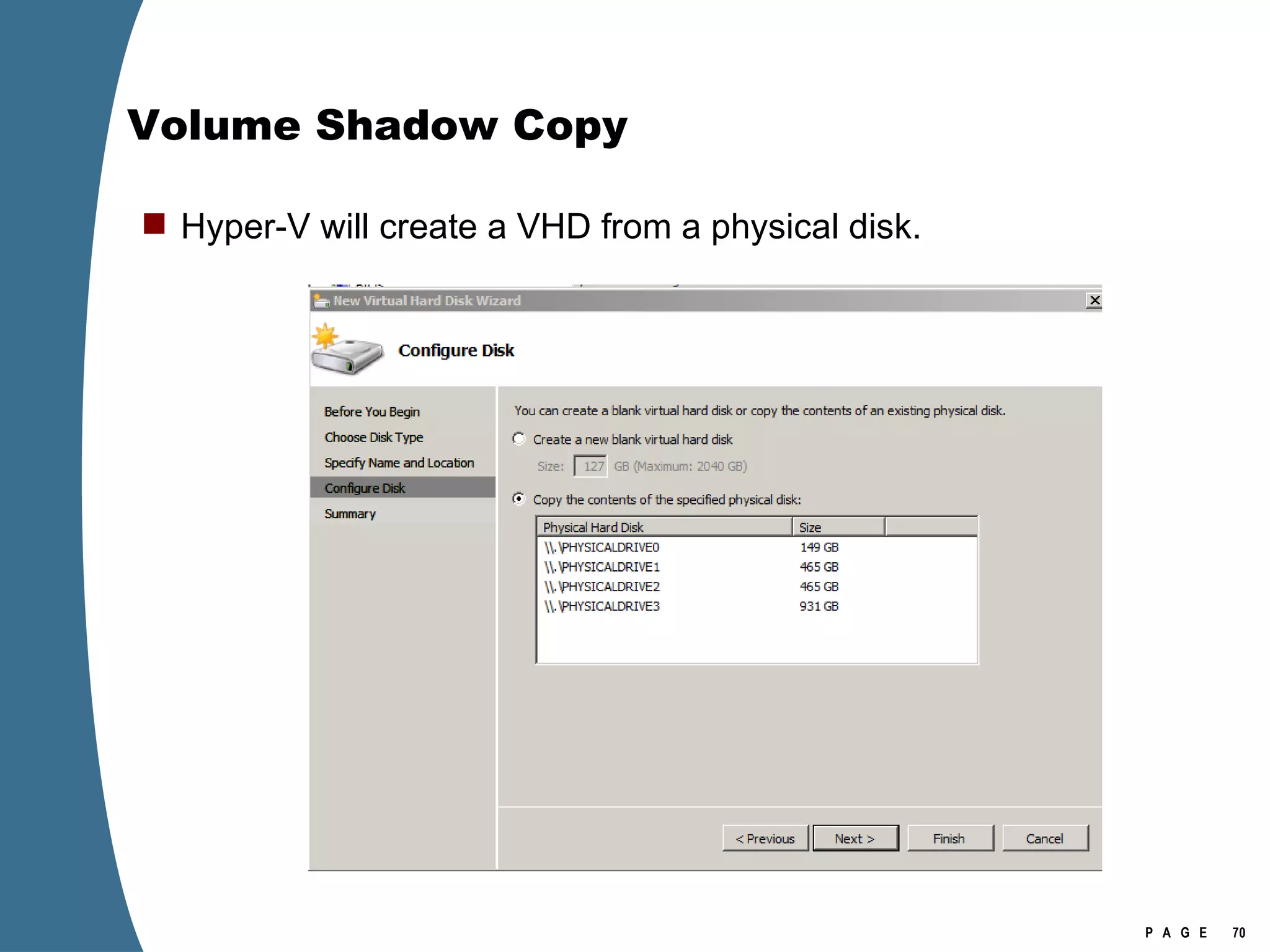
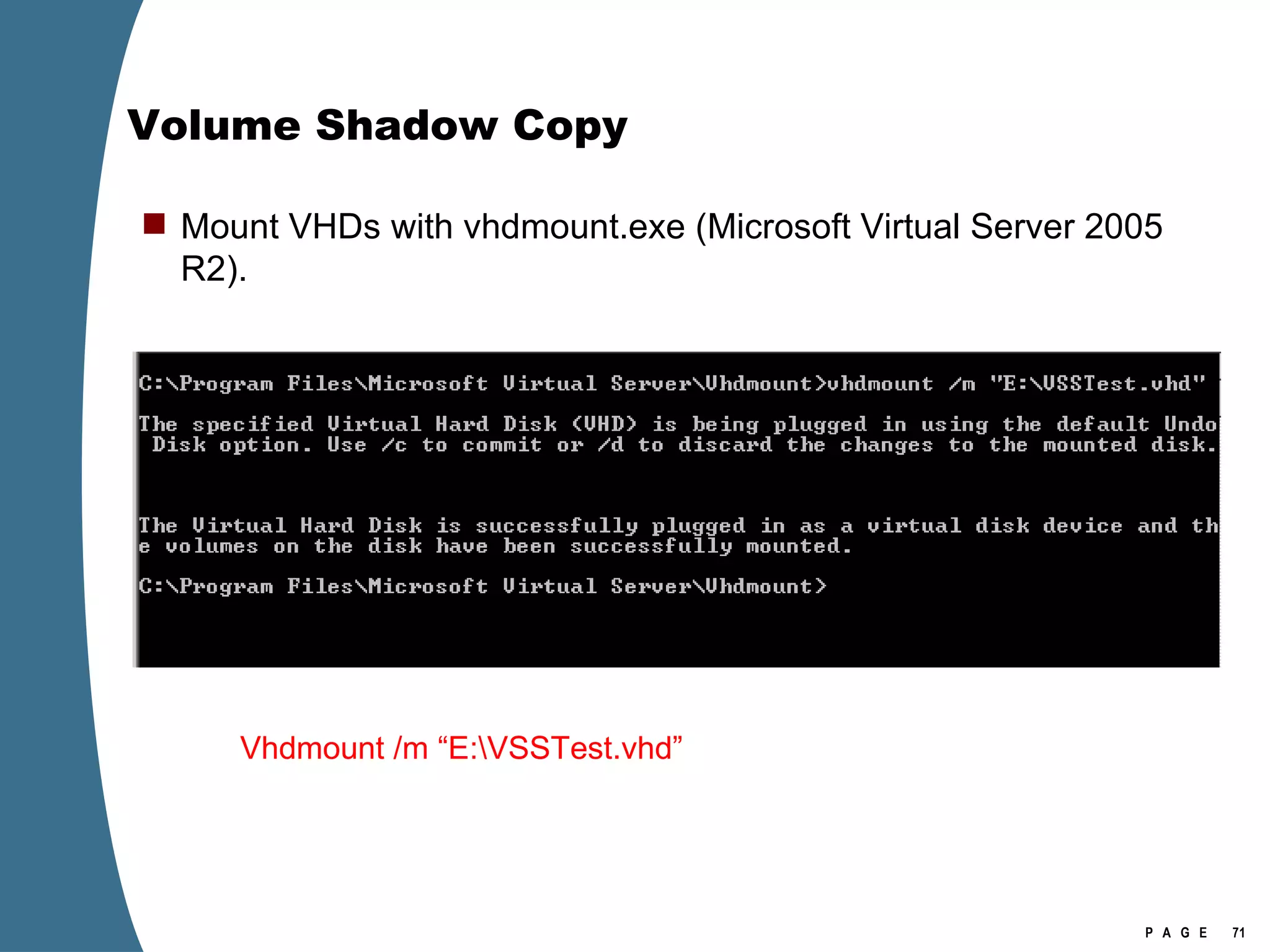
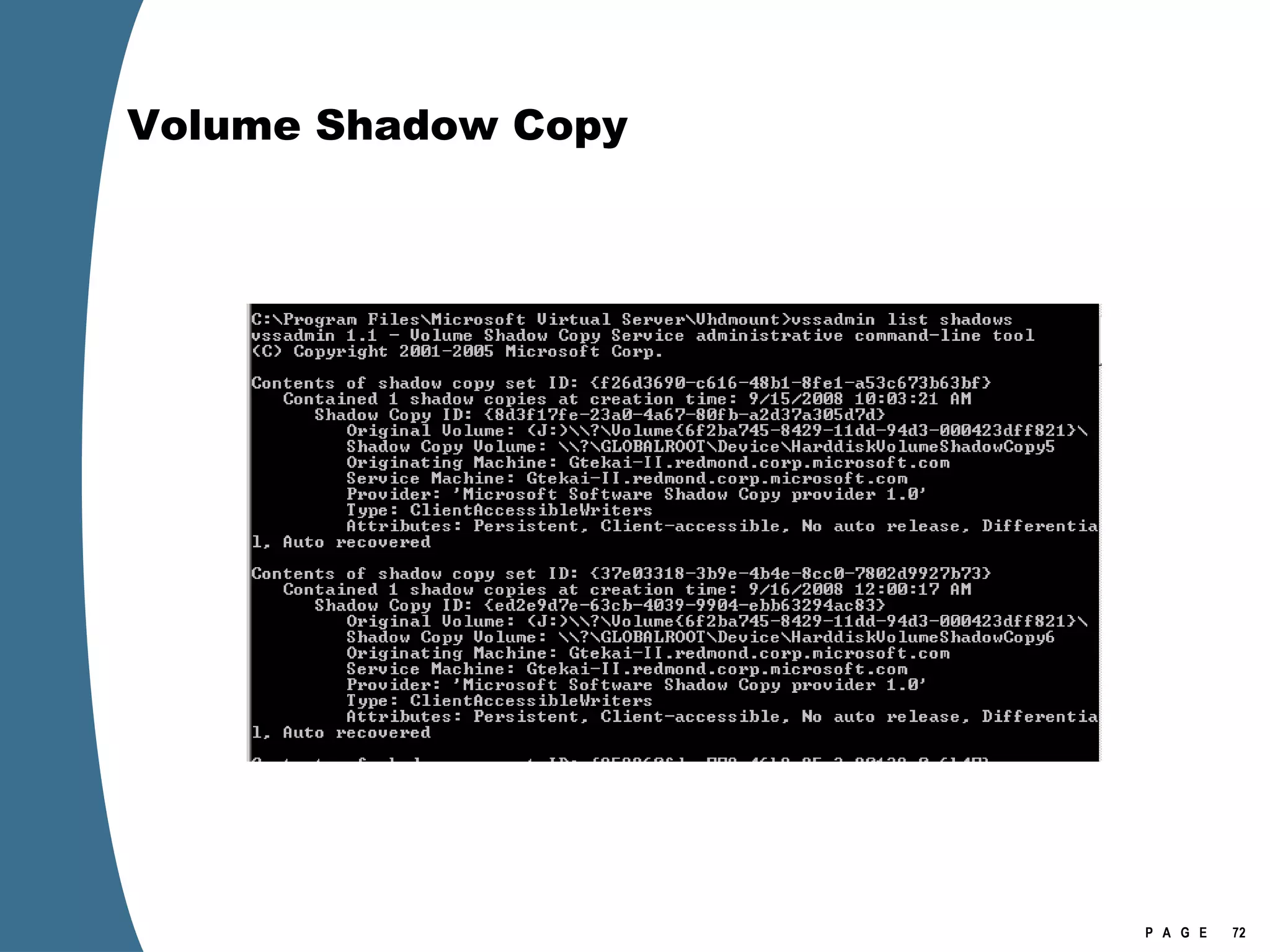
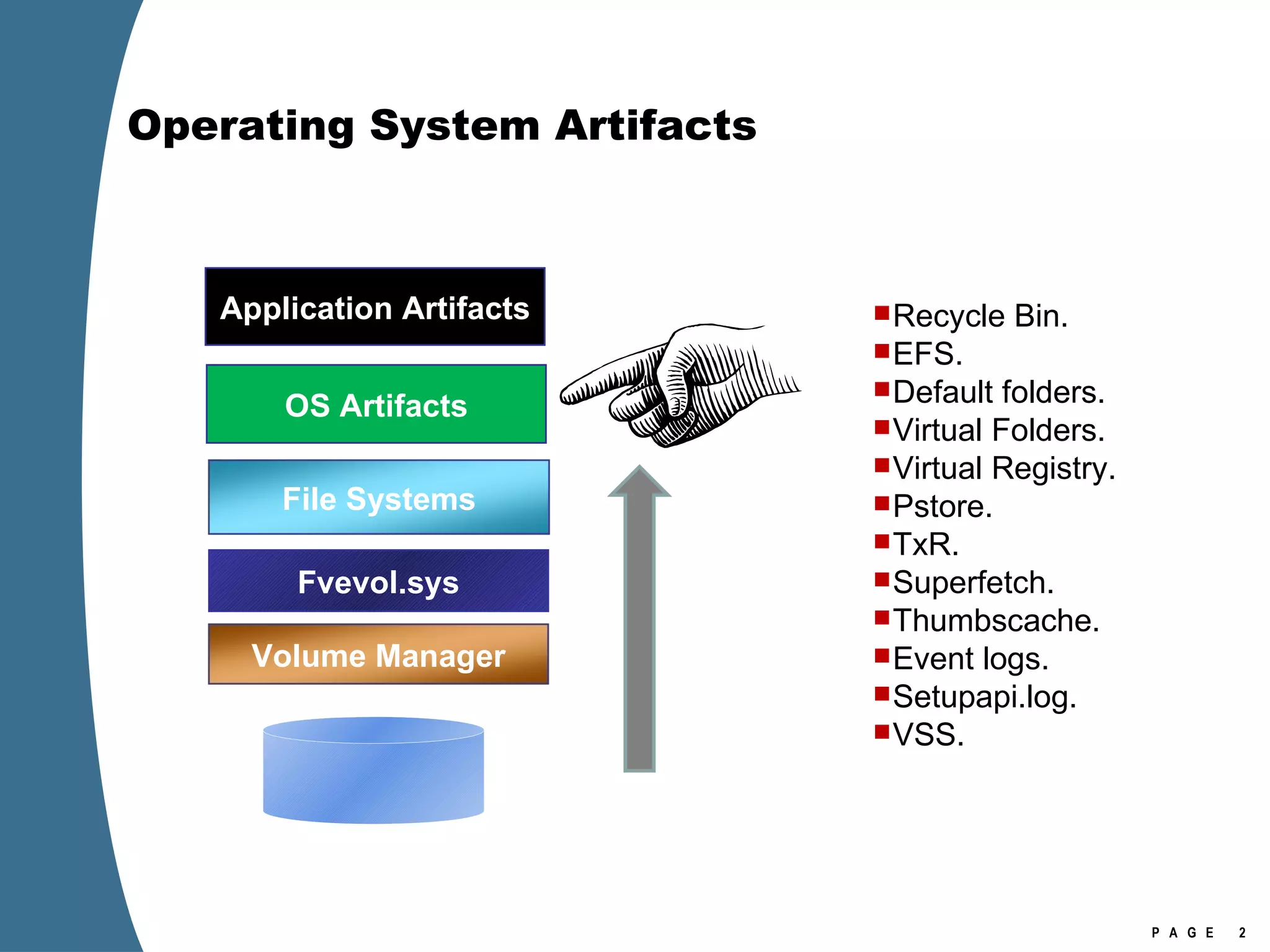
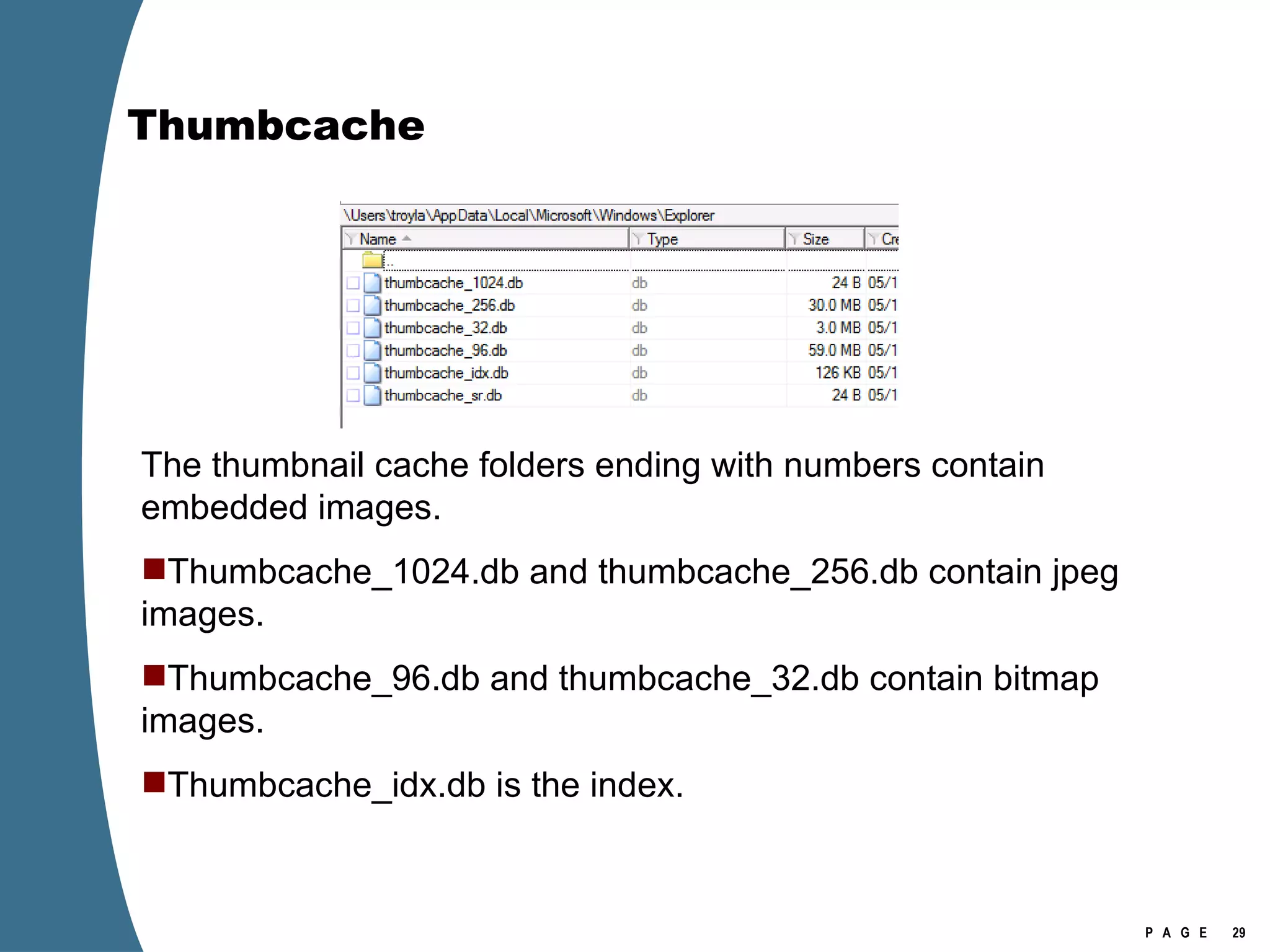
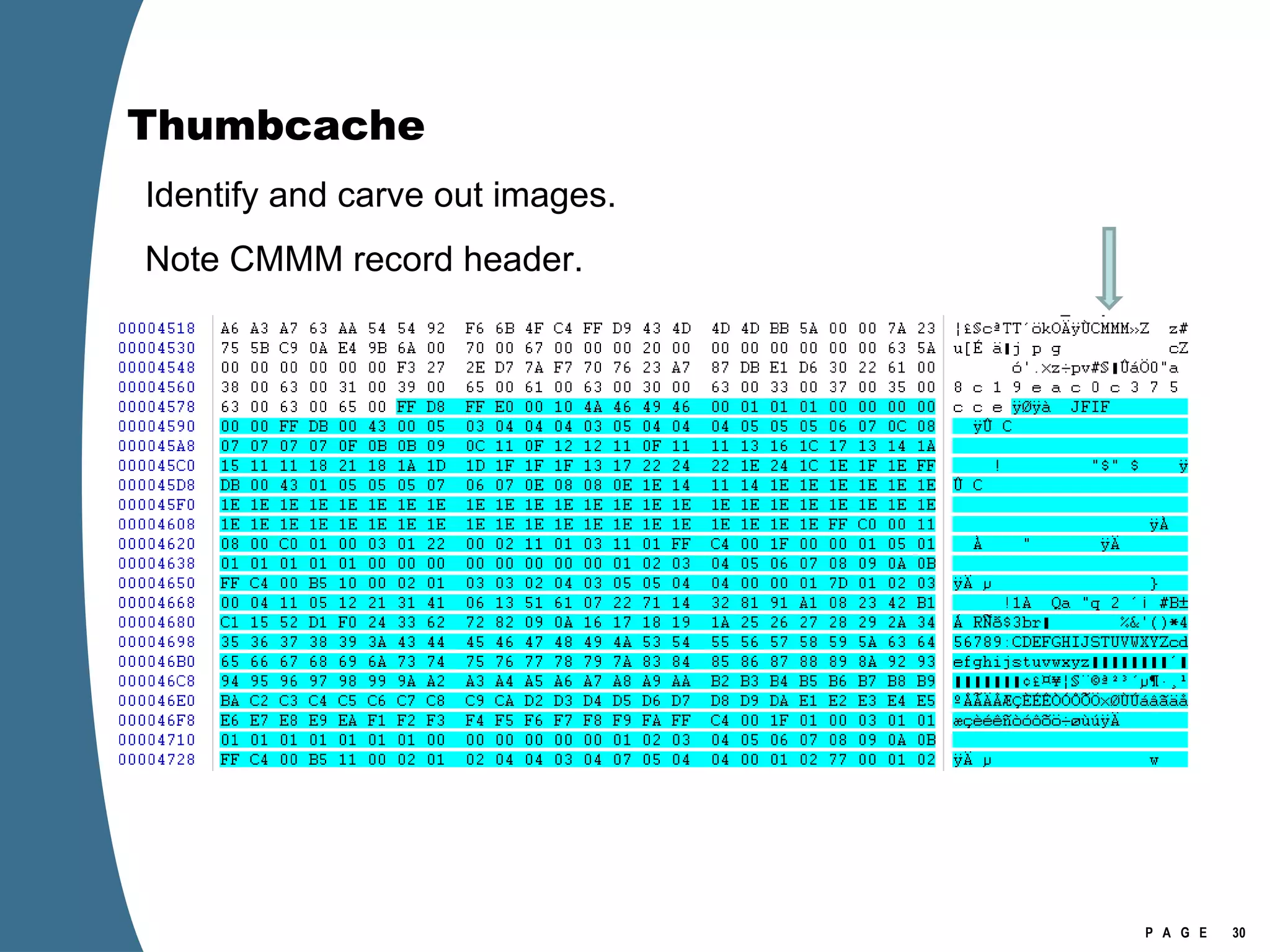
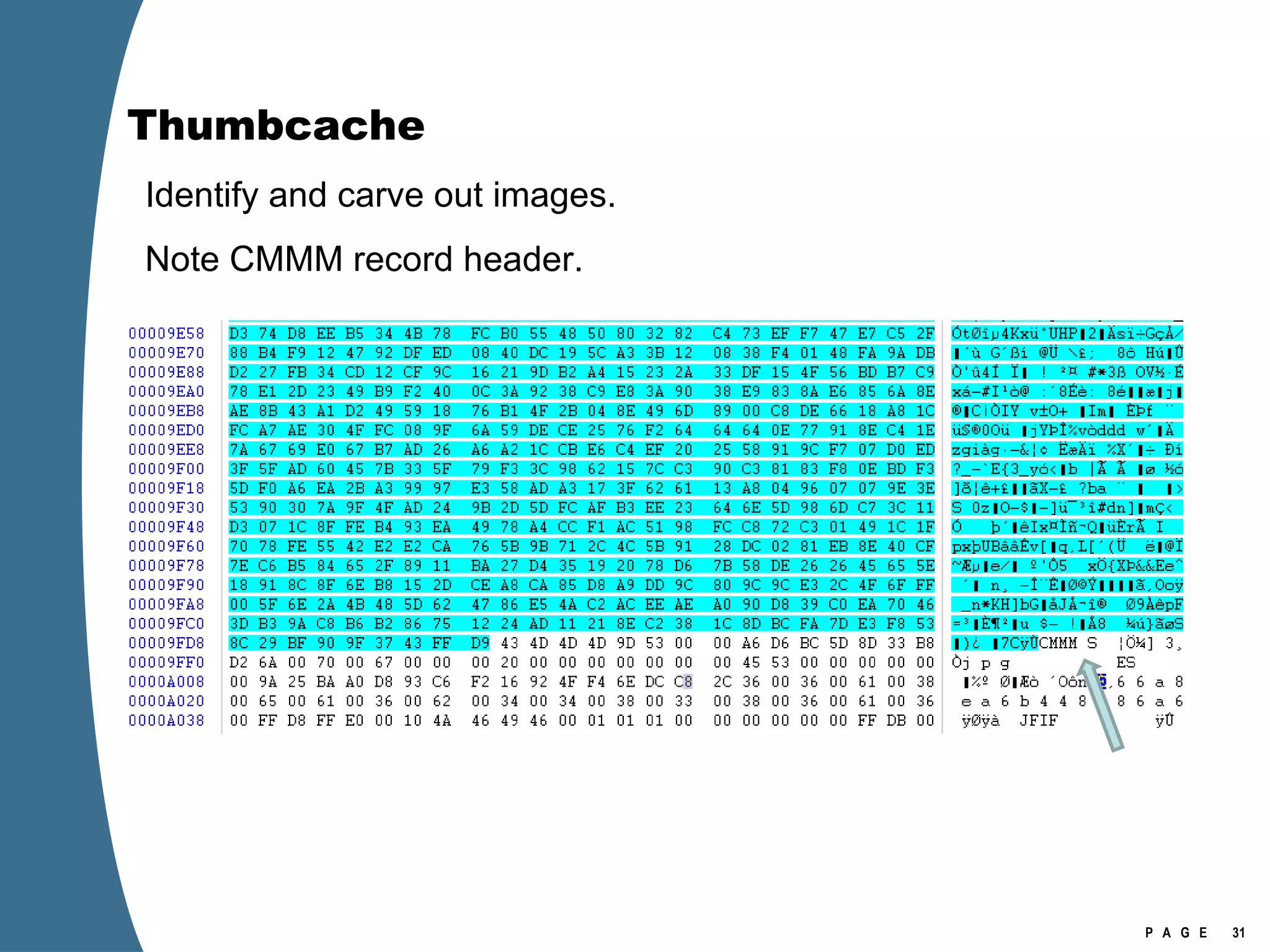
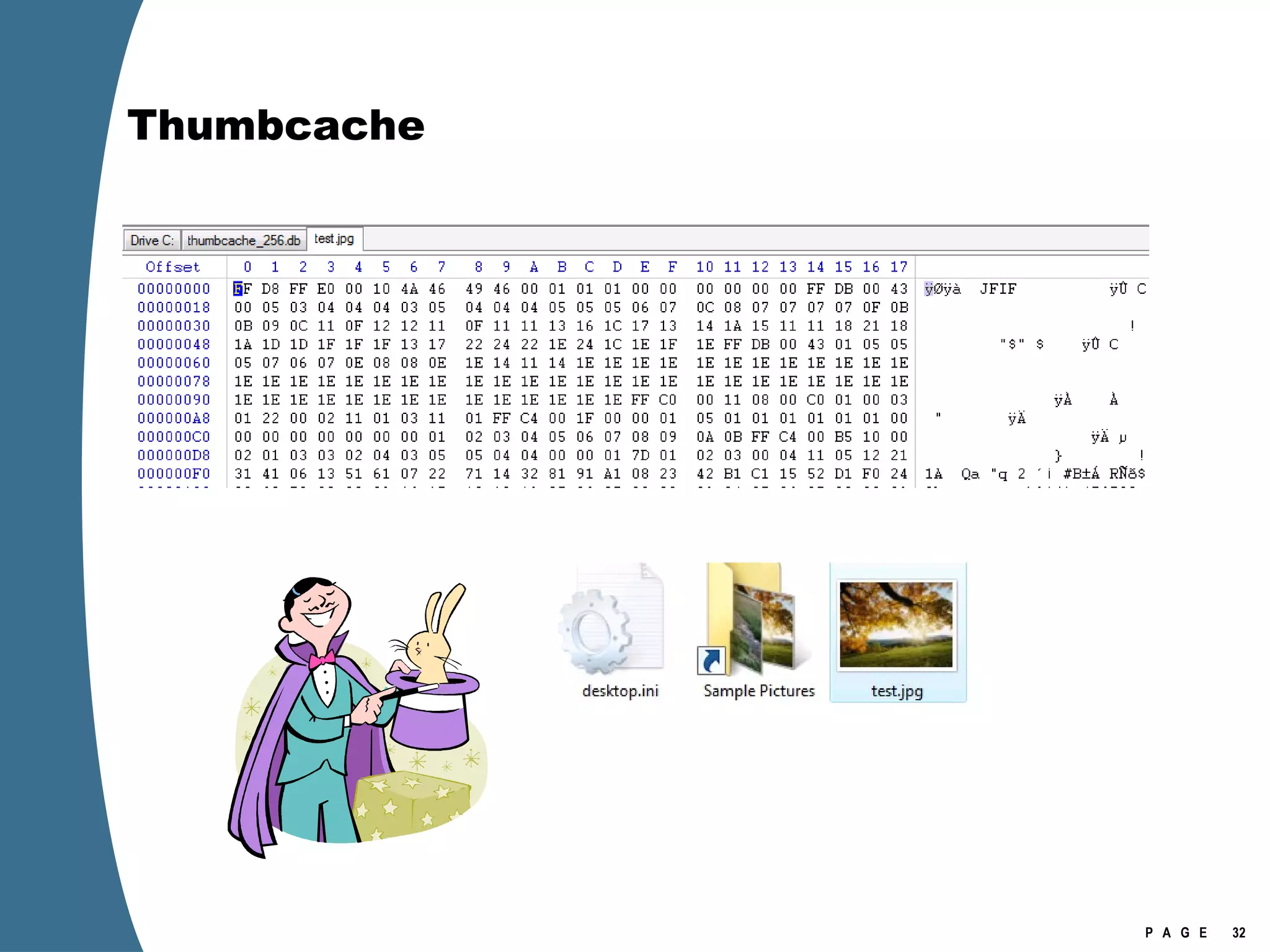
The document provides an overview of key forensic artifacts and changes in the Windows Vista operating system. In 3 sentences:
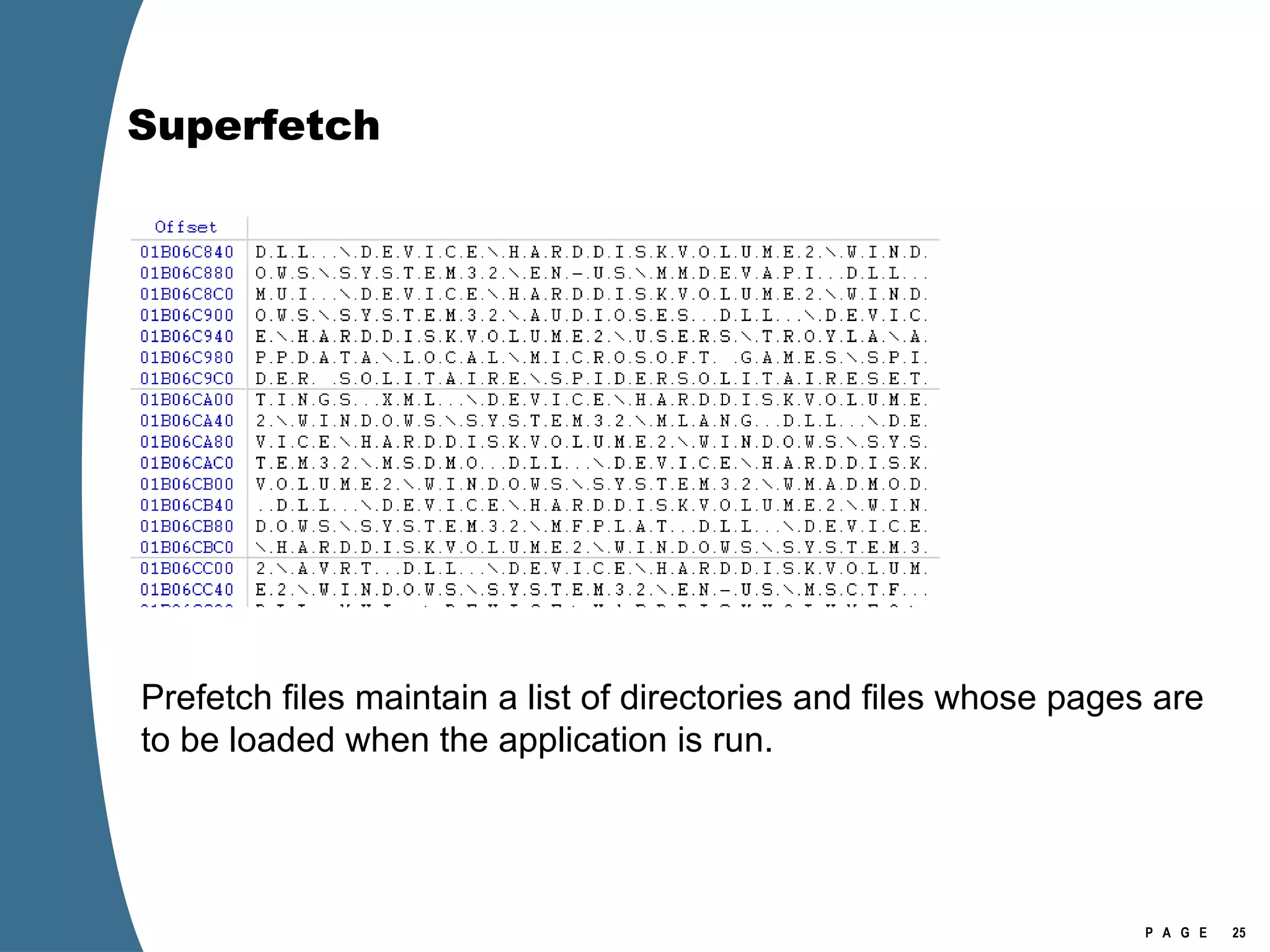
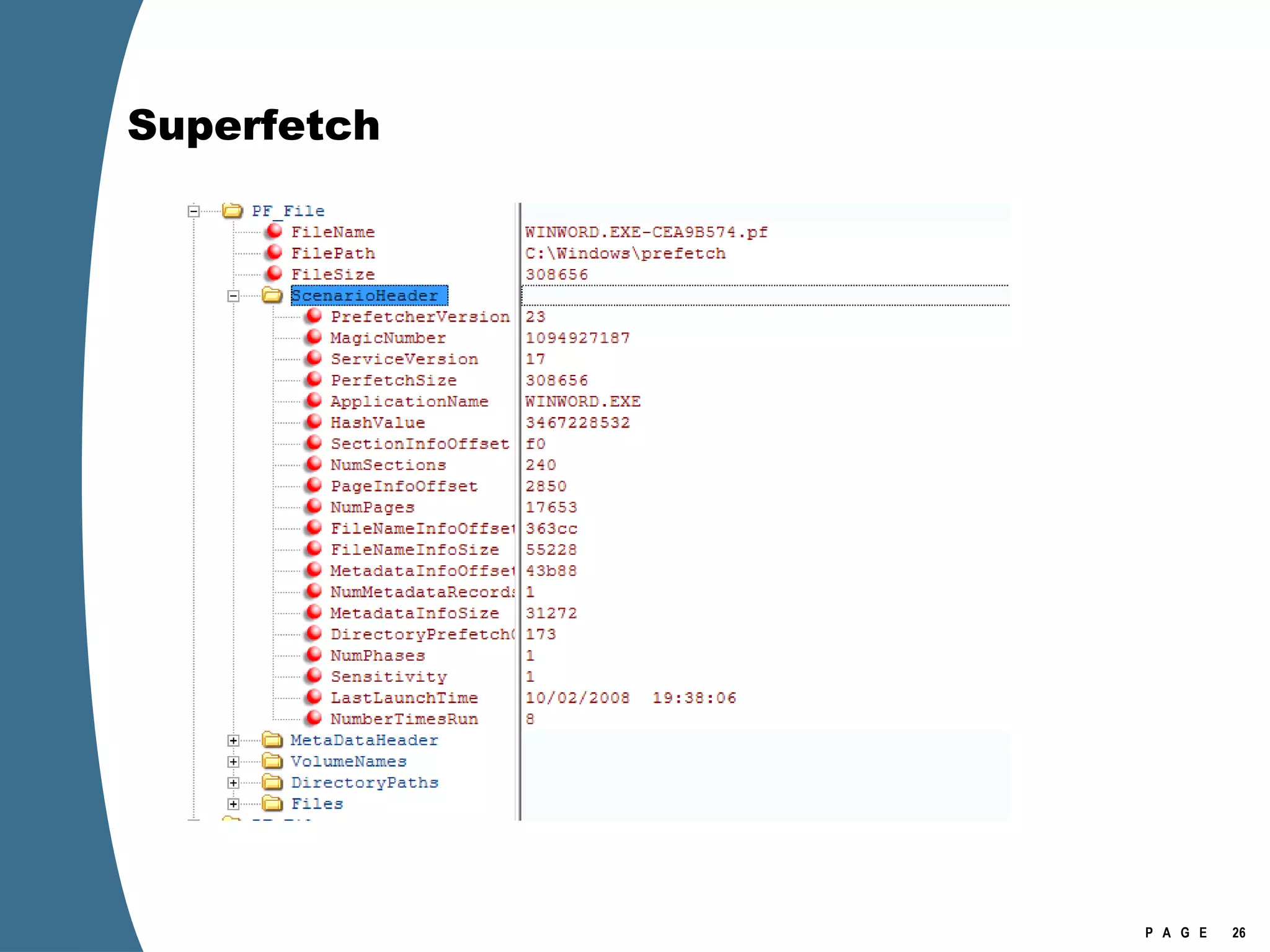
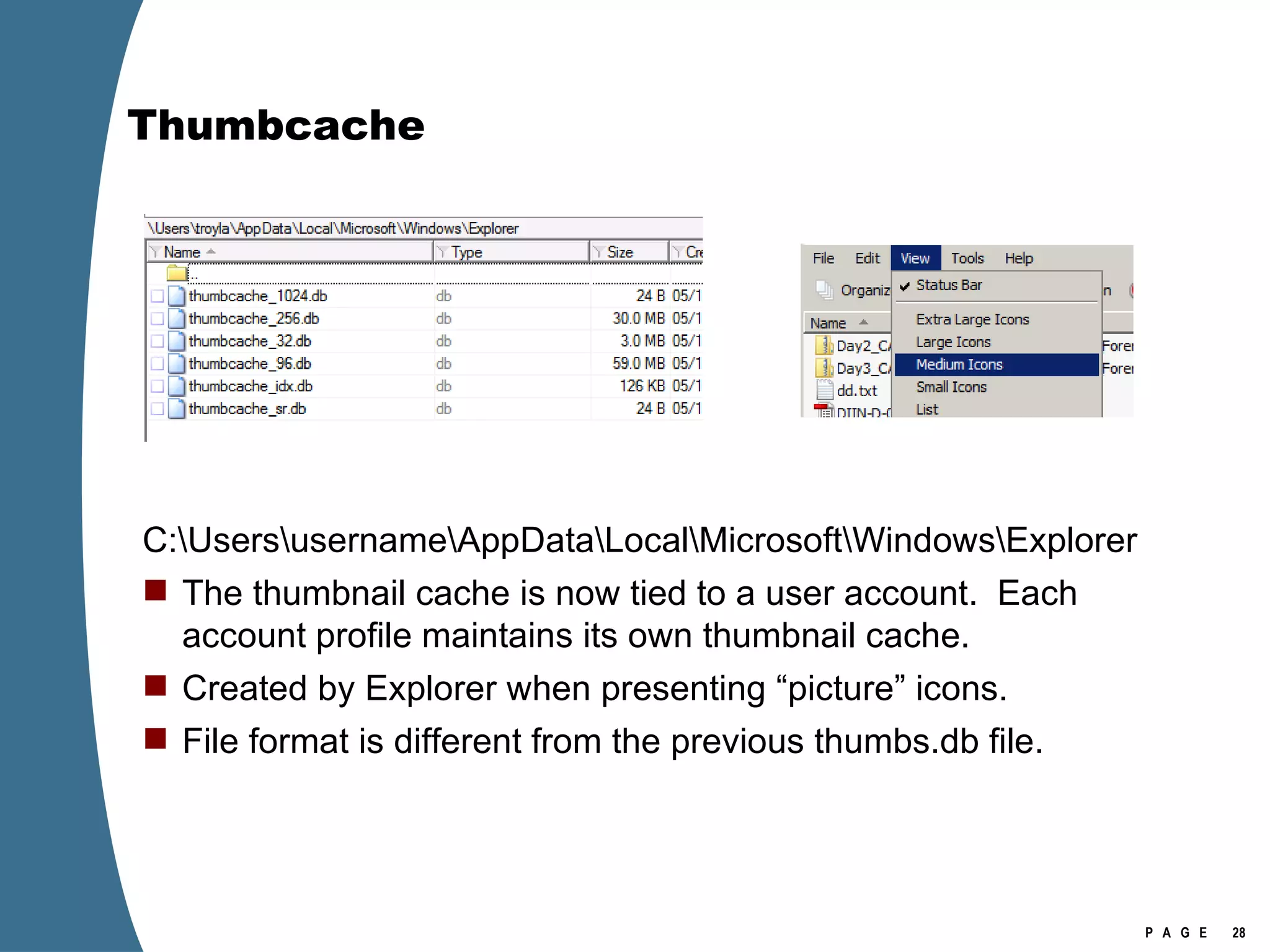
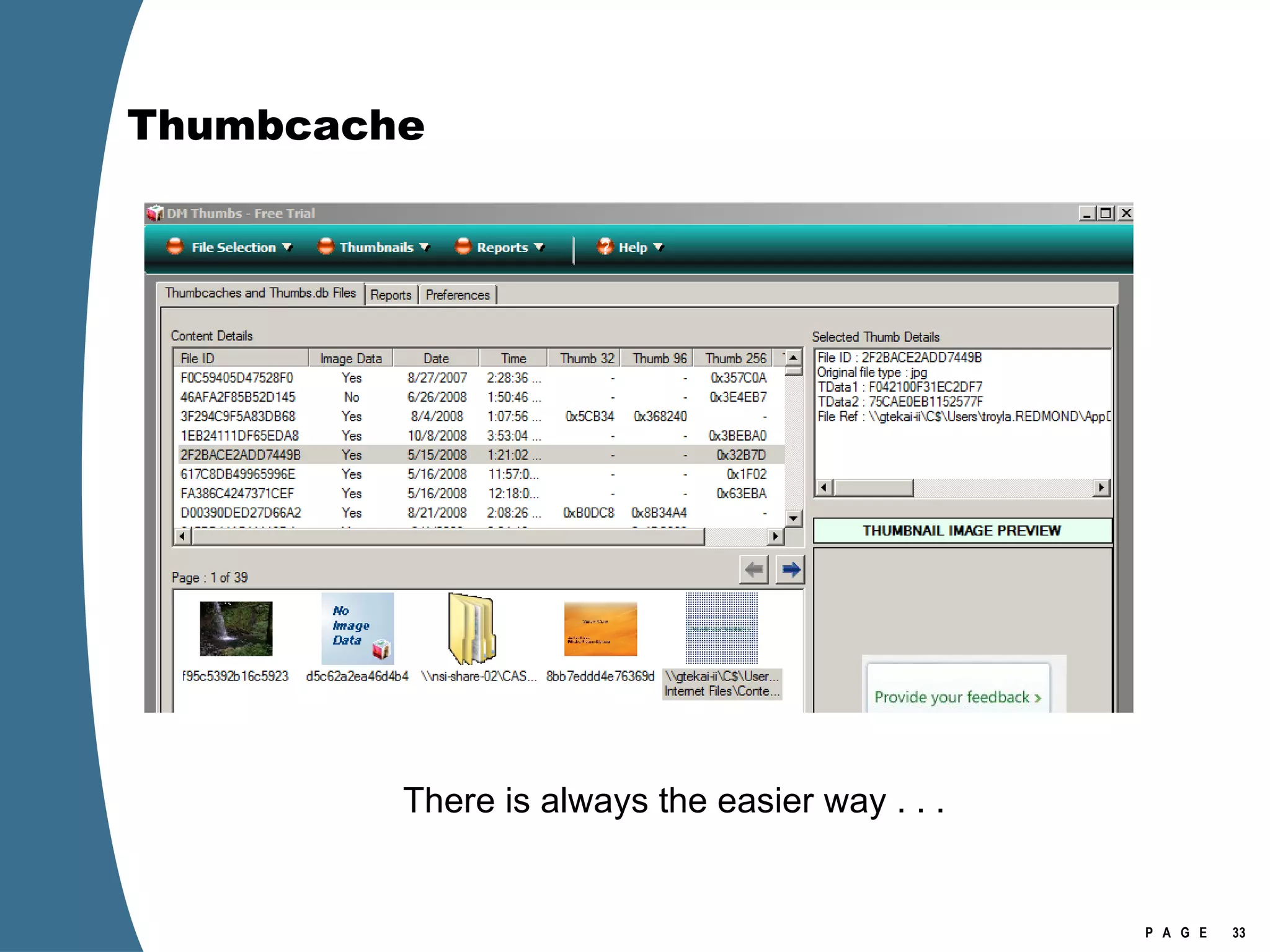
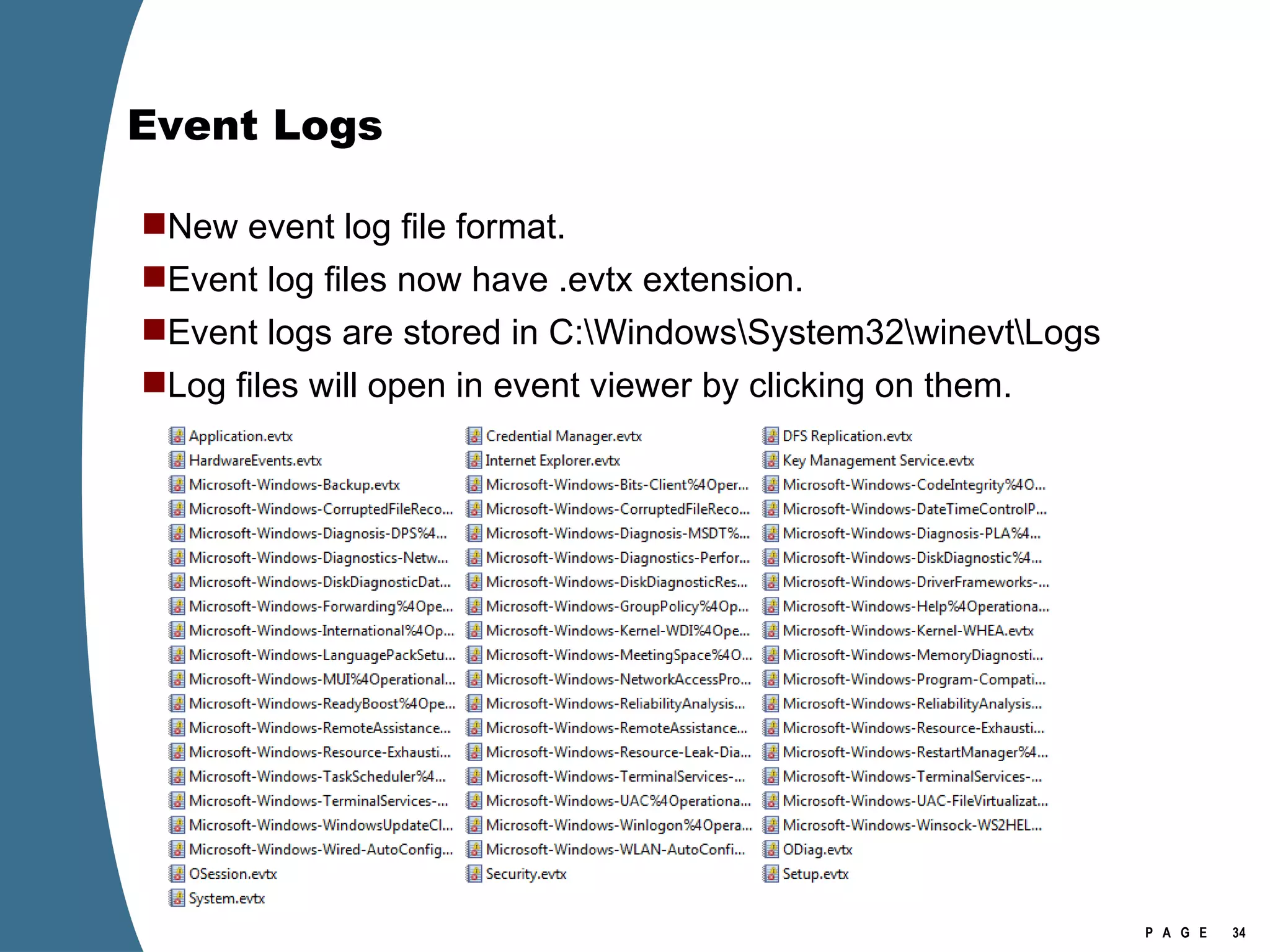
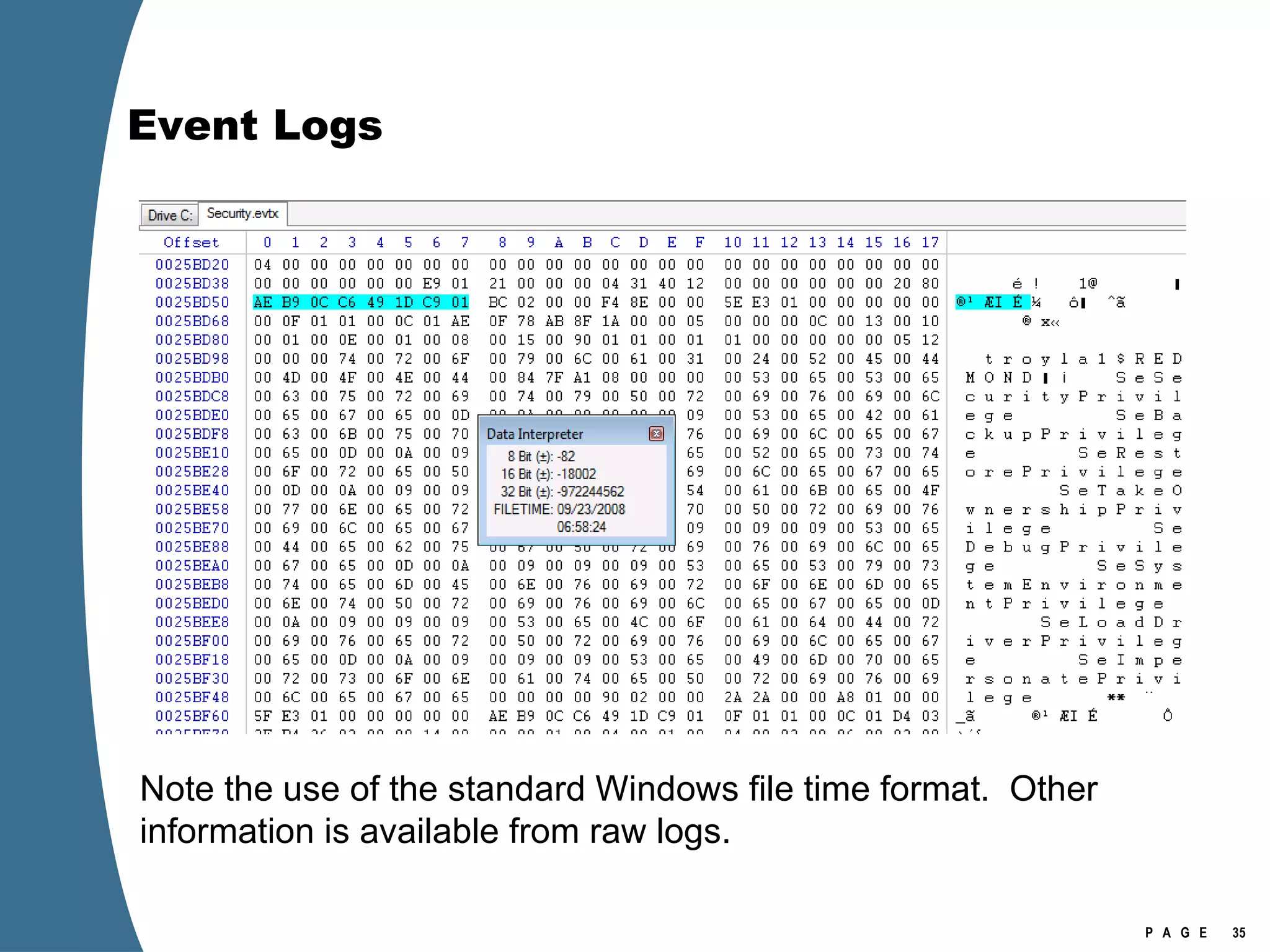
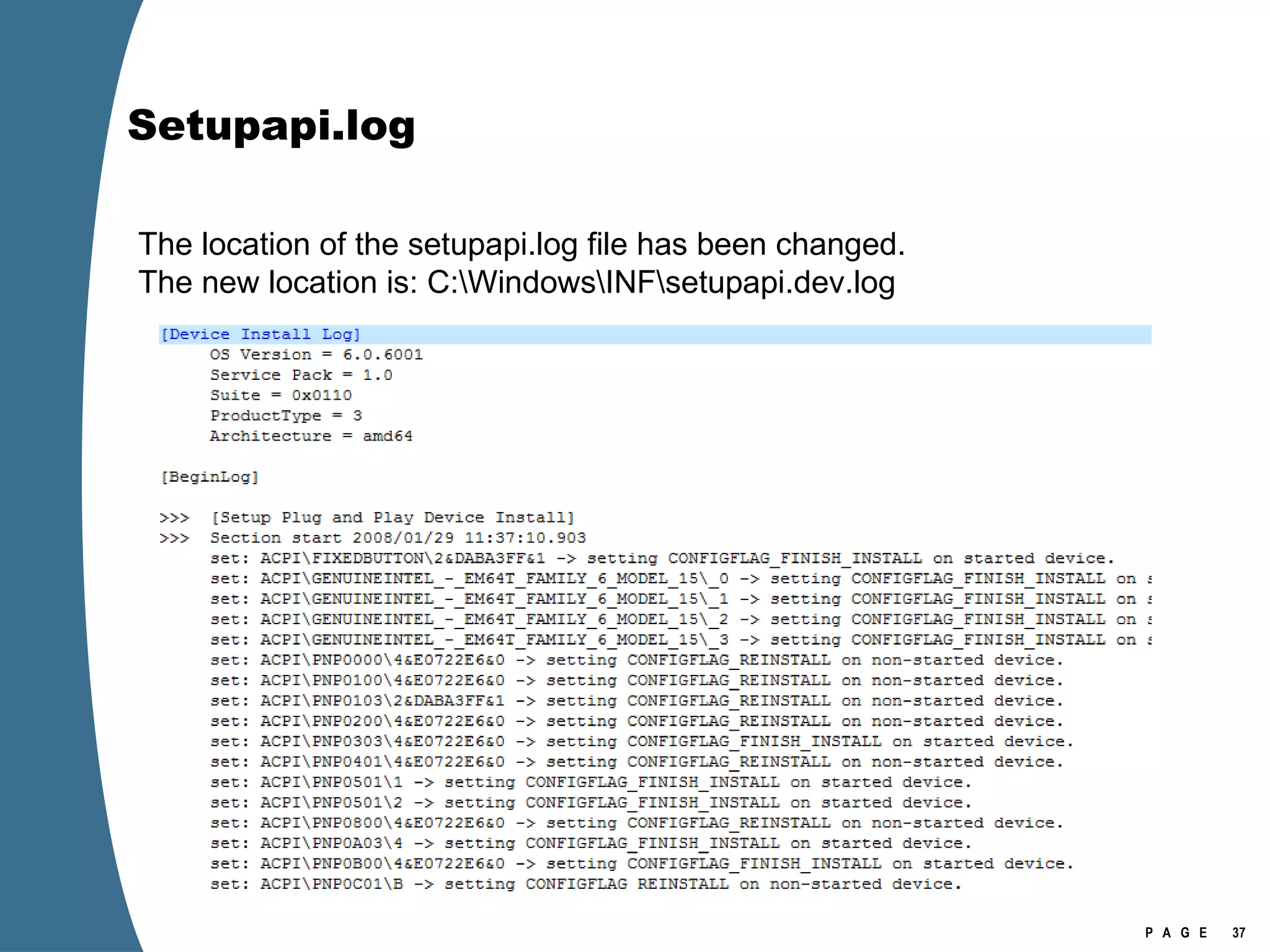
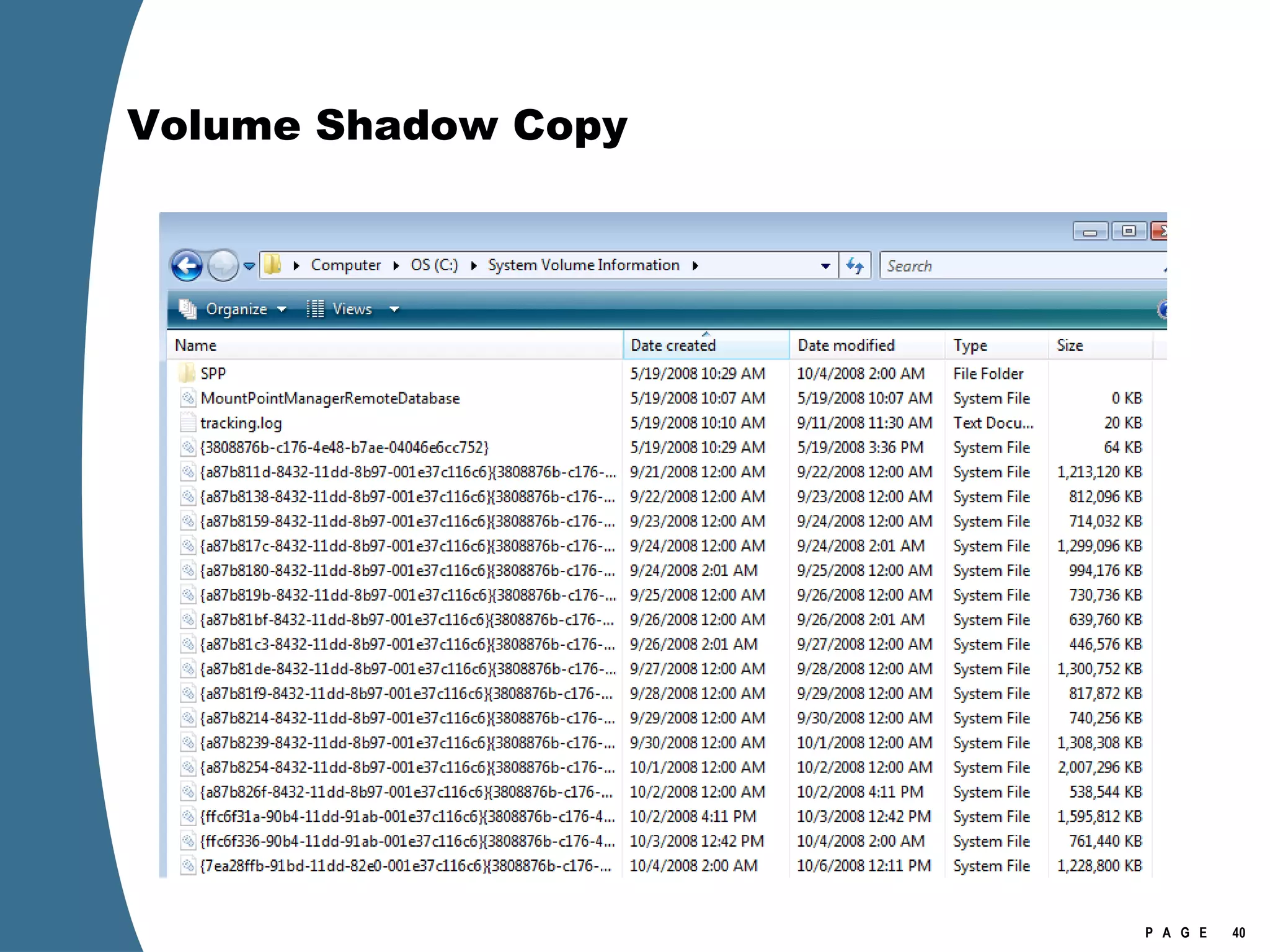
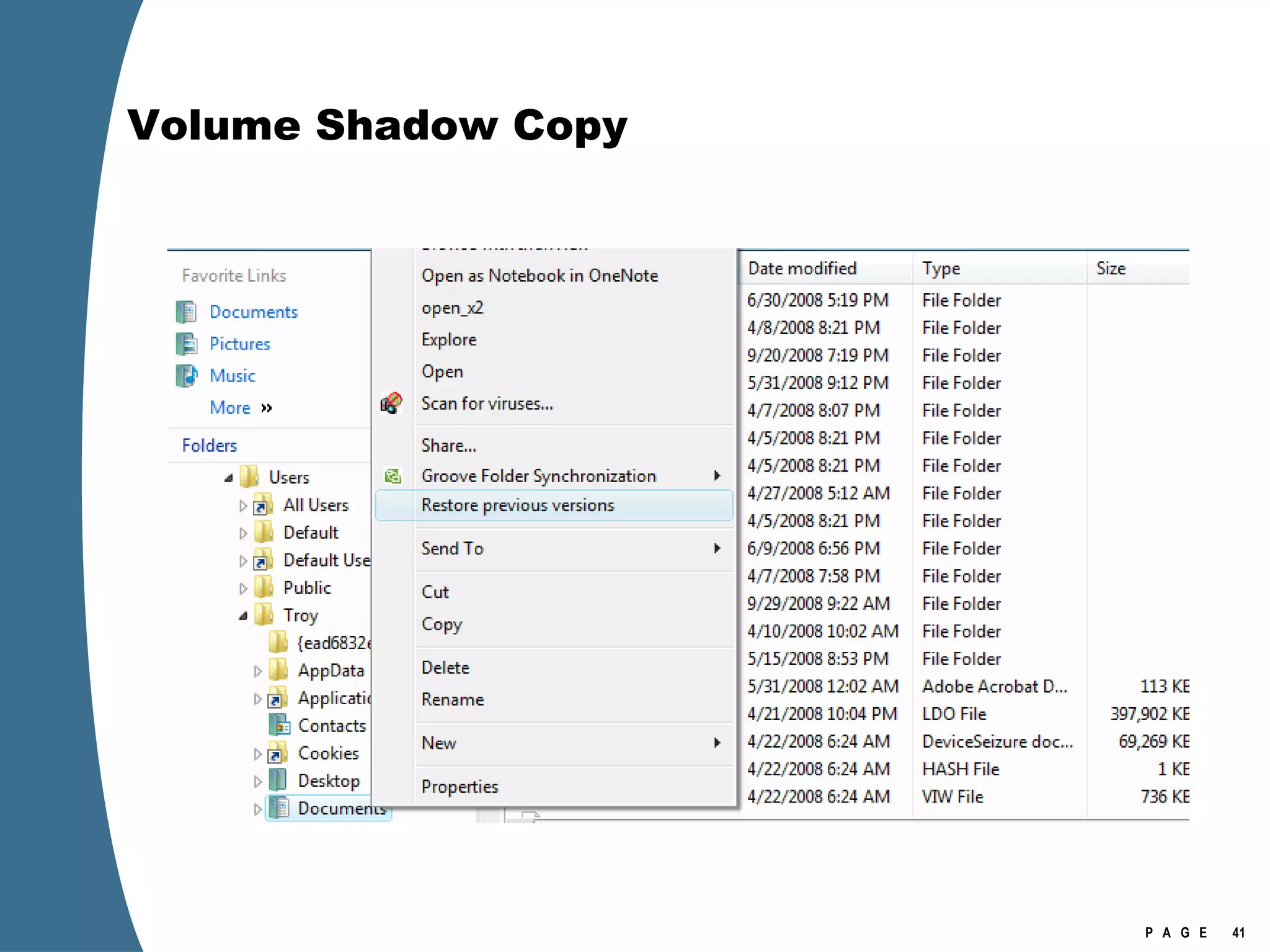
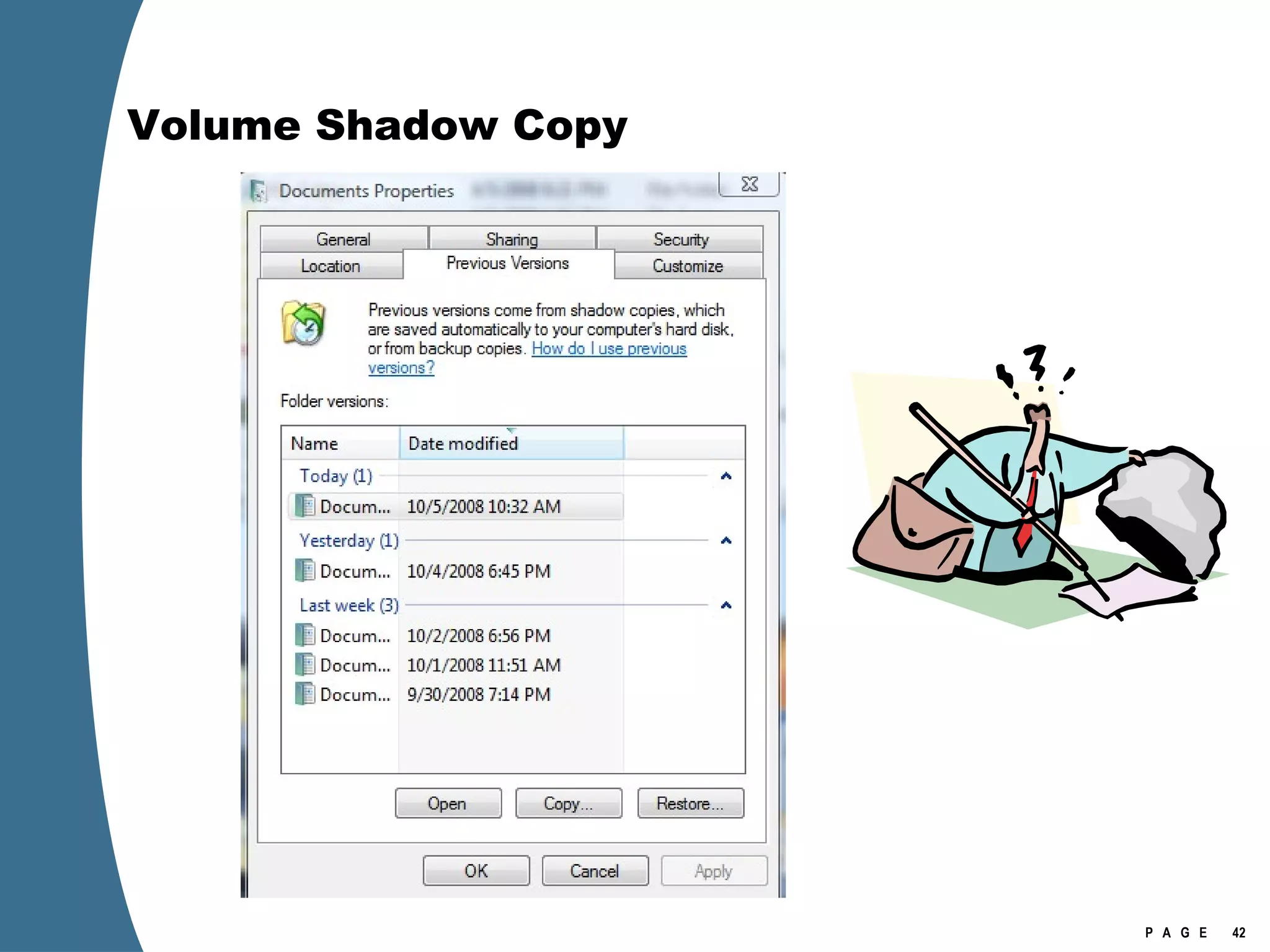
Vista introduced changes to the Recycle Bin, encryption with EFS keys on smart cards, default folder organization with junction links, registry virtualization for non-admin writes, an updated thumbnail cache format, new event log format with .evtx extension, and use of volume shadow copies for restoring previous versions of files and retrieving deleted data through differential disk imaging. Analysis of Vista systems requires examining multiple registry hives and investigating artifacts like prefetch files, volume shadow copies, and the thumbnail cache for evidentiary value.

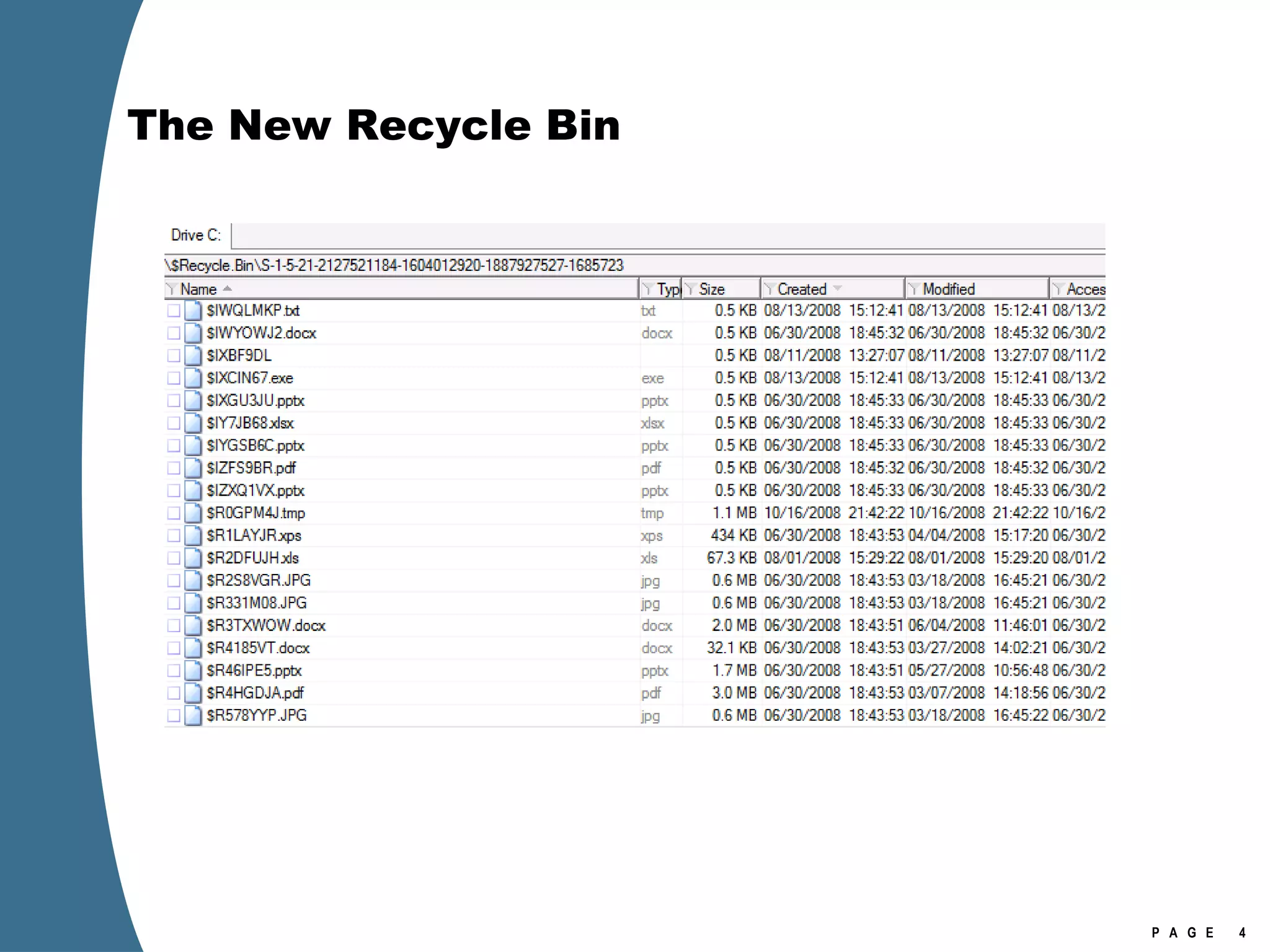
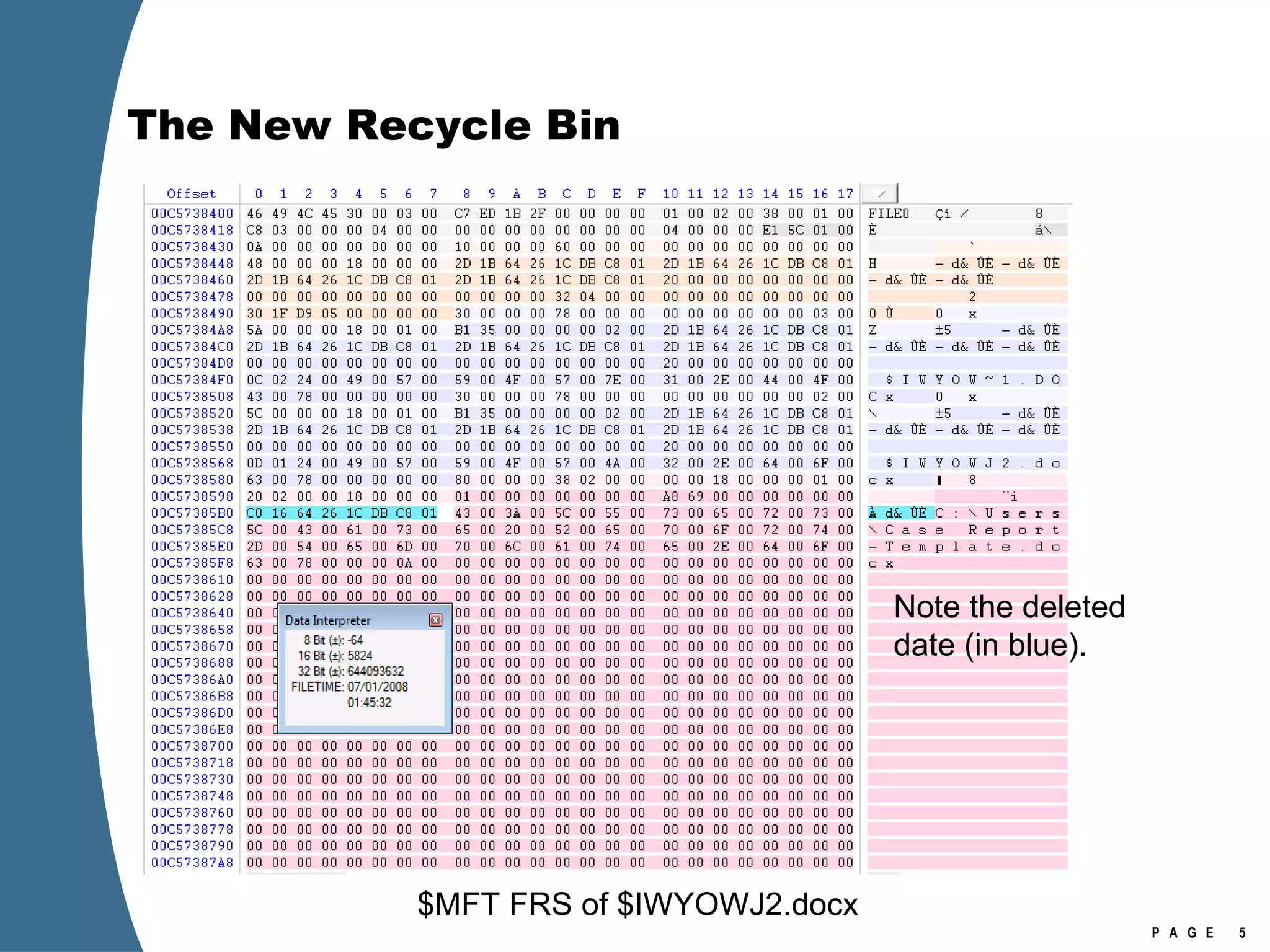
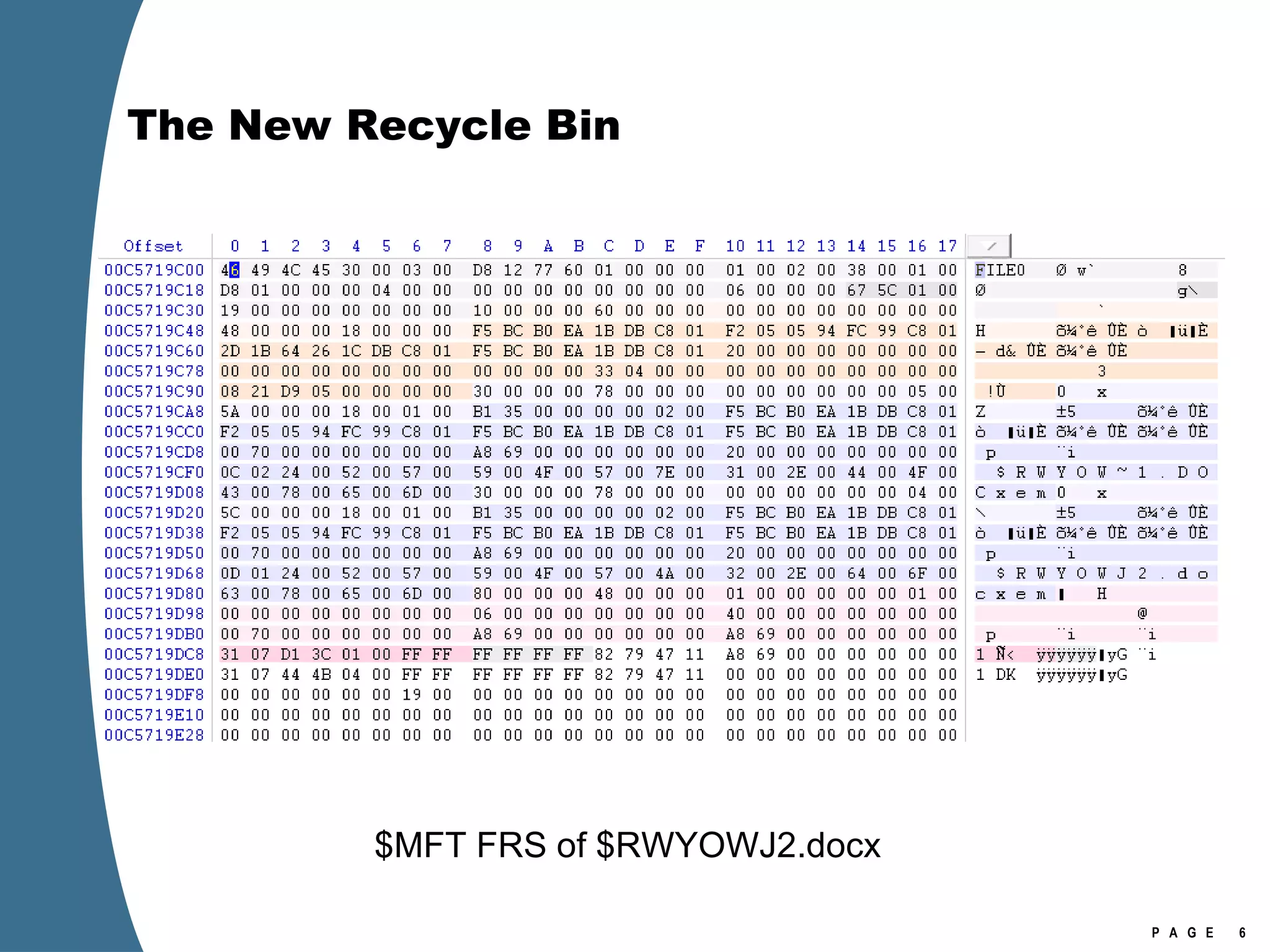
![The New Recycle Bin [Volume]:\$Recycle.Bin $Recycle.Bin is visible in Explorer (view hidden files). Per user store in a subfolder named with account SID No more Info2 files. When a file is deleted—moved to the Recycle Bin—it generates two files in the Recycle Bin. $I and $R files. $I or $R followed by several random characters, then original extension. The random characters are the same for each $I/$R pair. $I file maintains the original name and path, as well as the deleted date. $R file retains the original file attributes, other than the name attribute (which is changed to $R******.ext).](https://image.slidesharecdn.com/ctinwindowsforensicsoverview-090406155625-phpapp02/75/Vista-Forensics-3-2048.jpg)
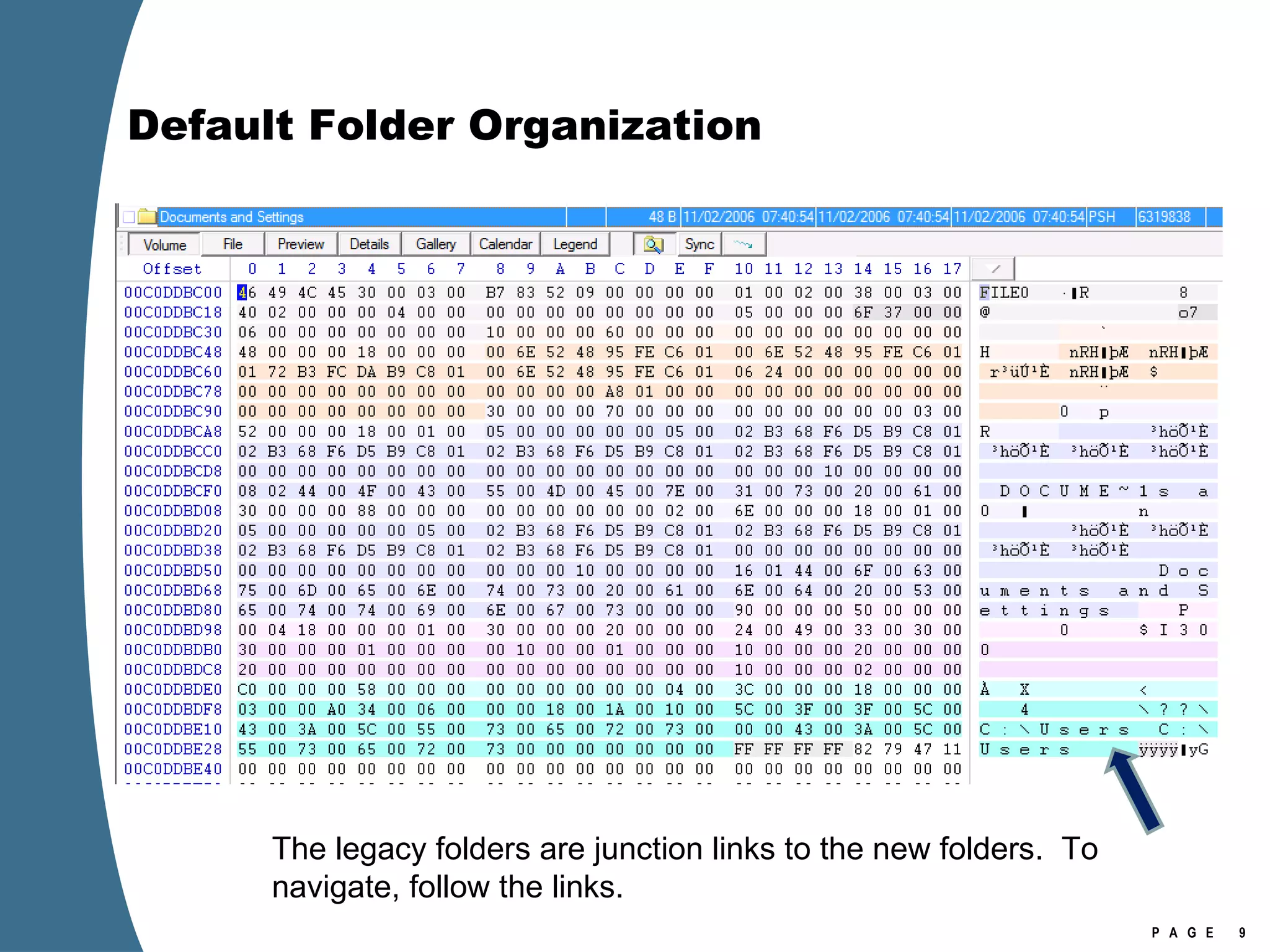
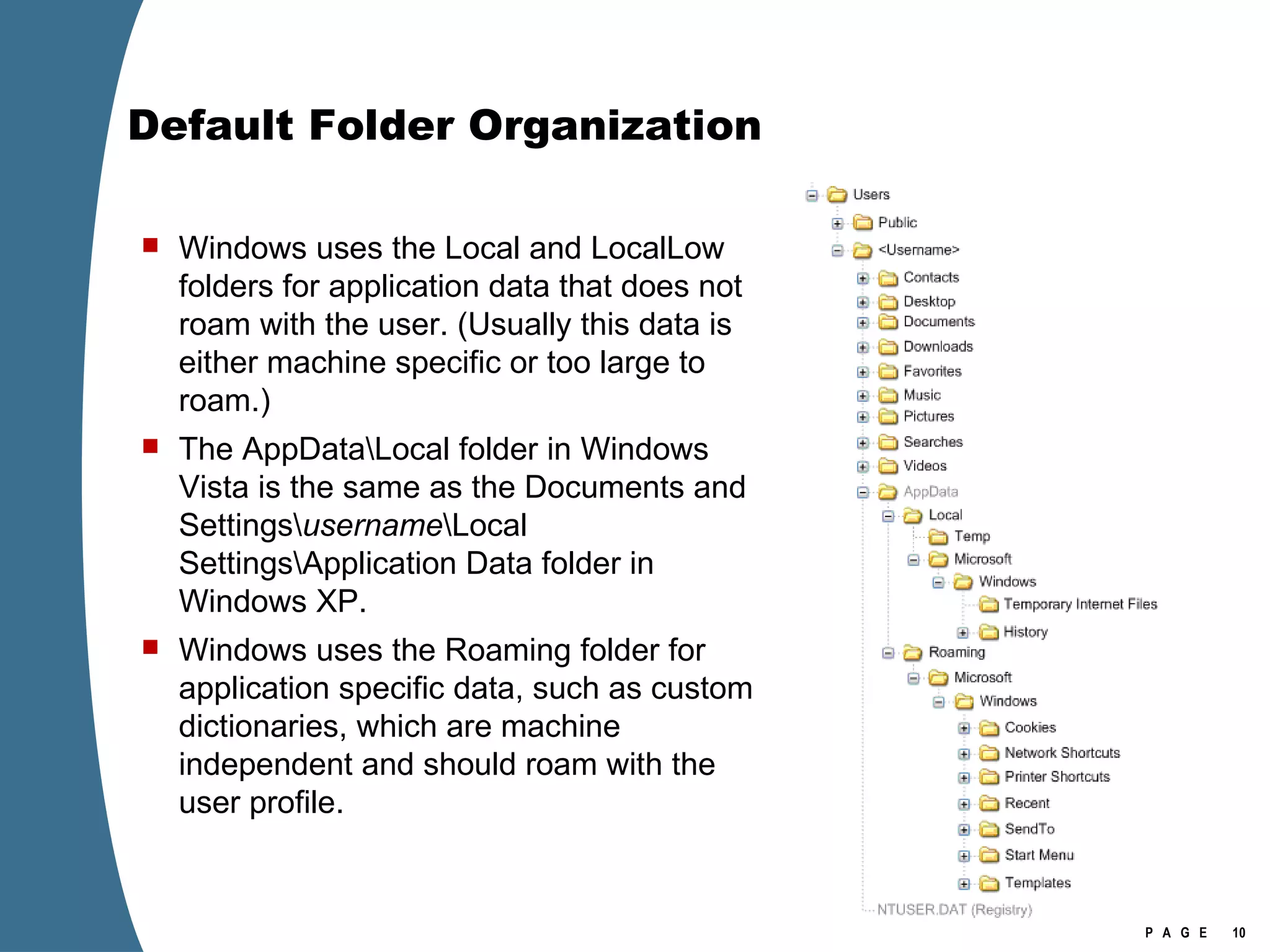
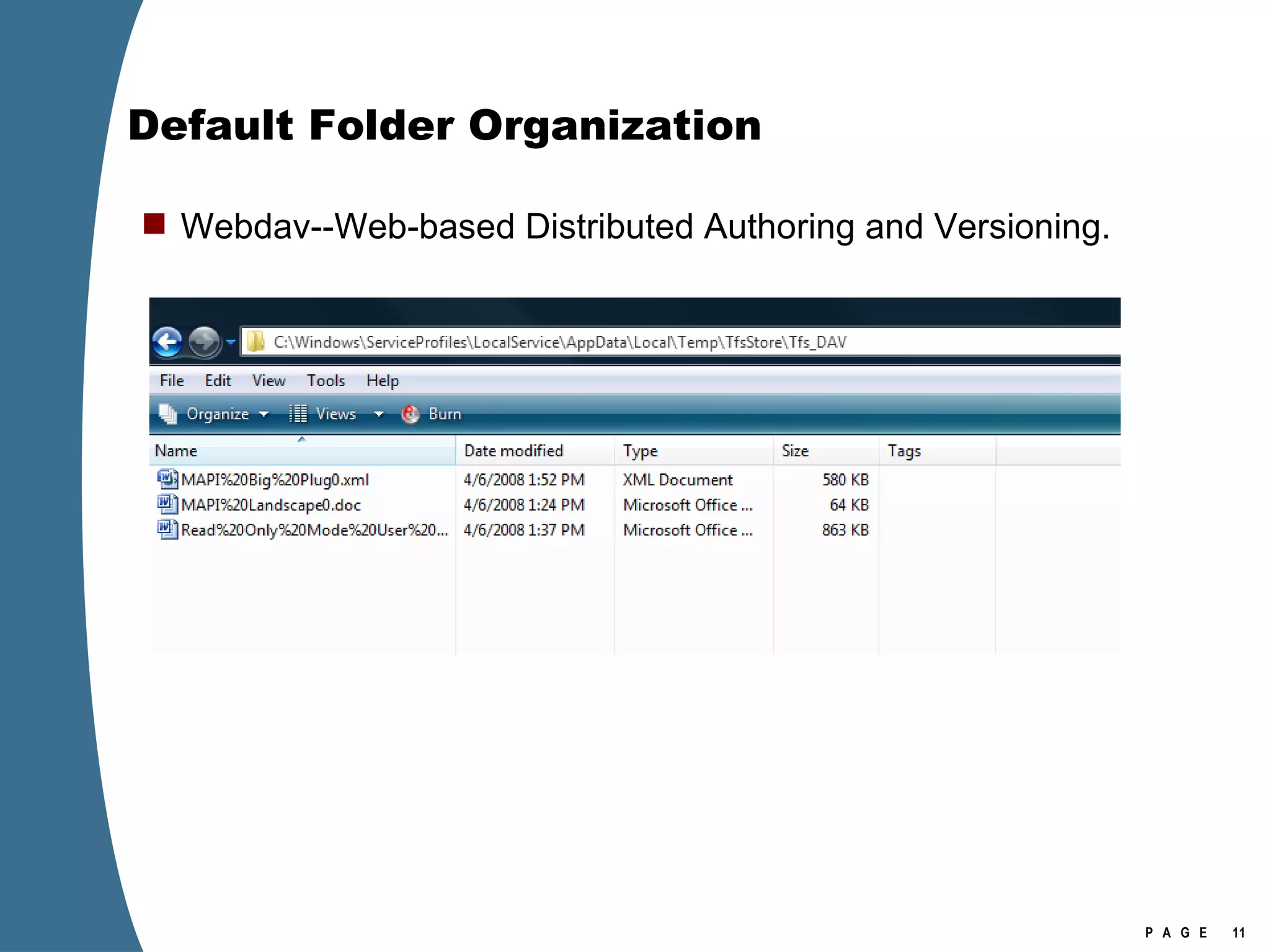
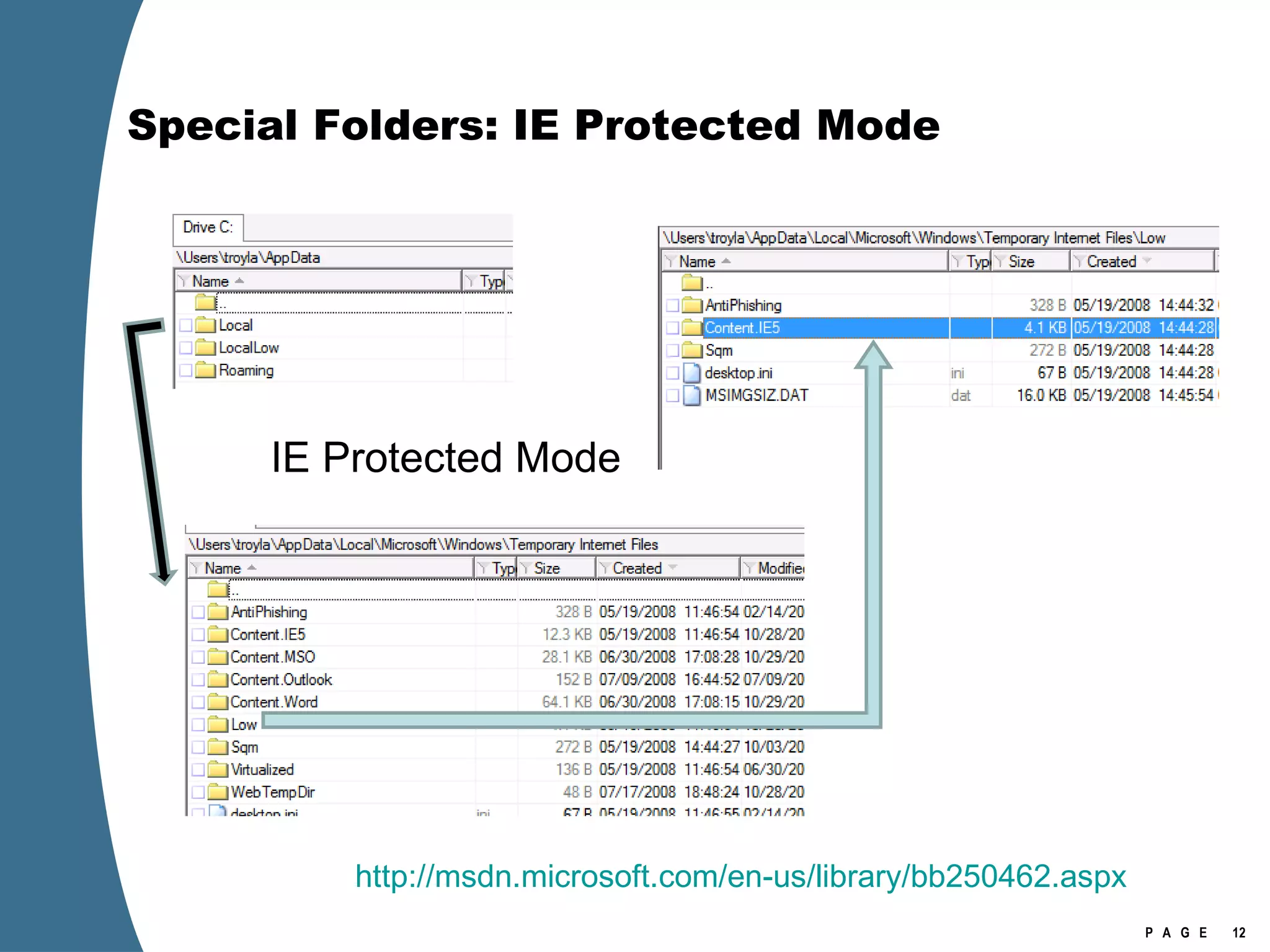
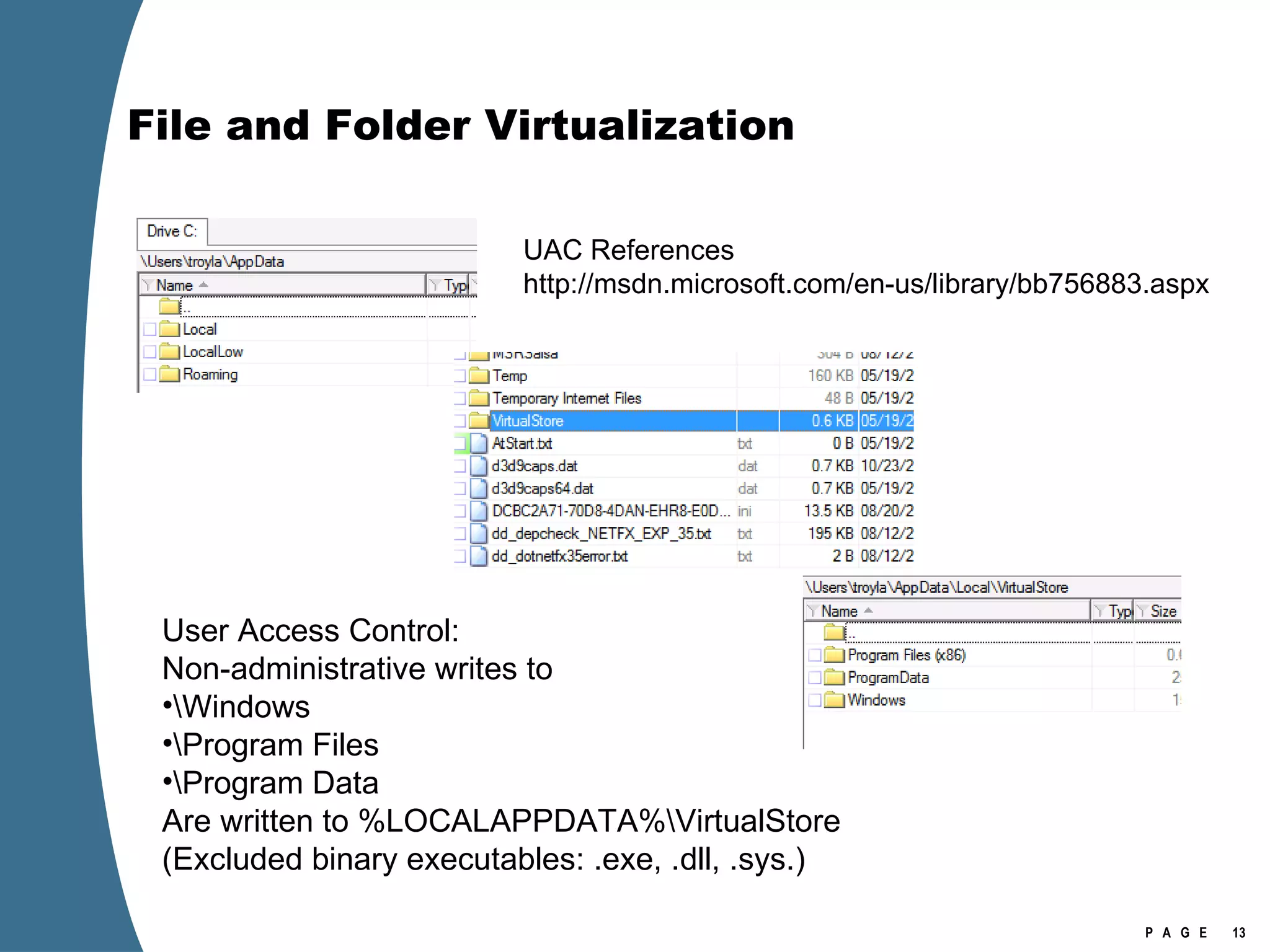
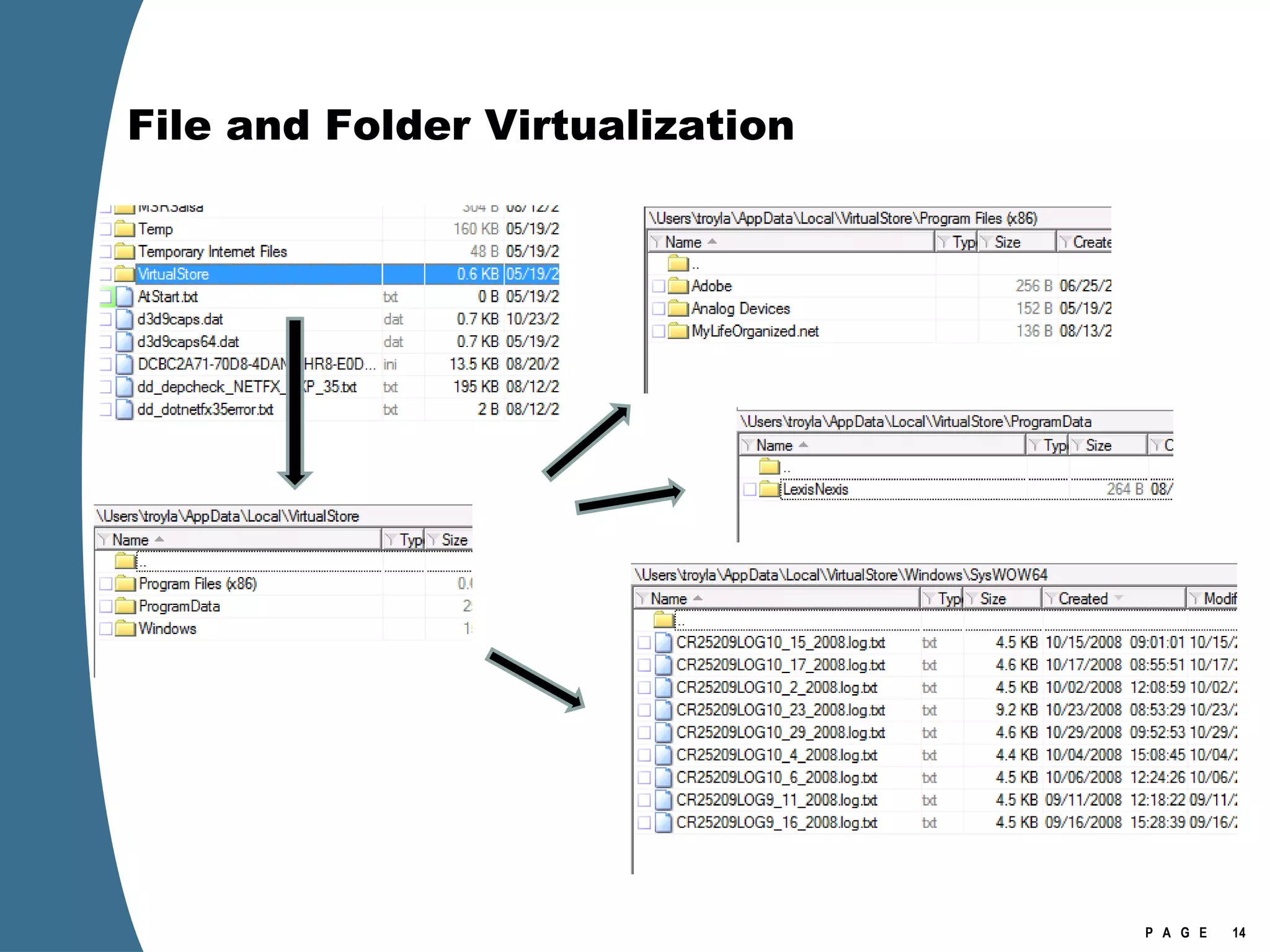
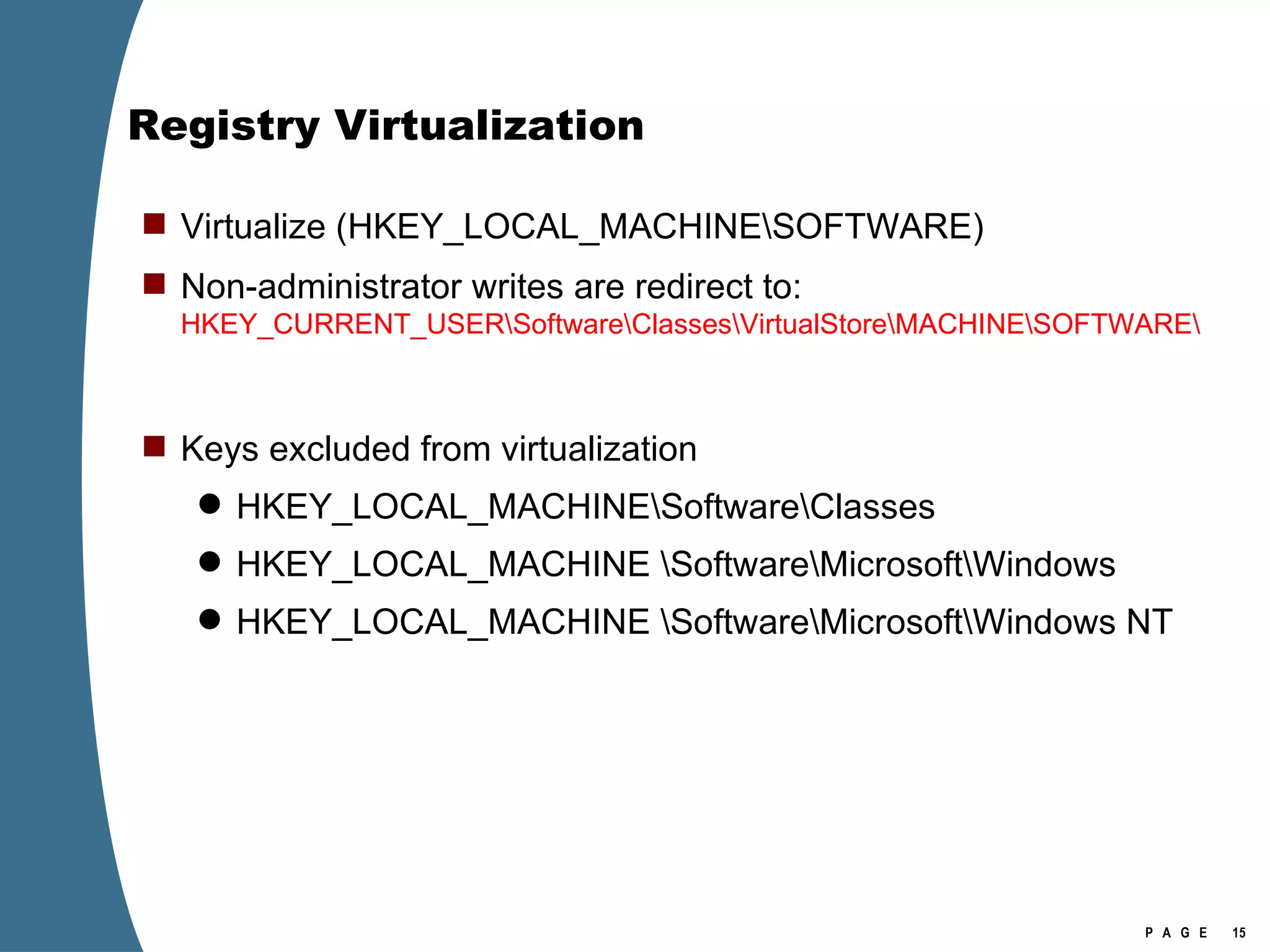
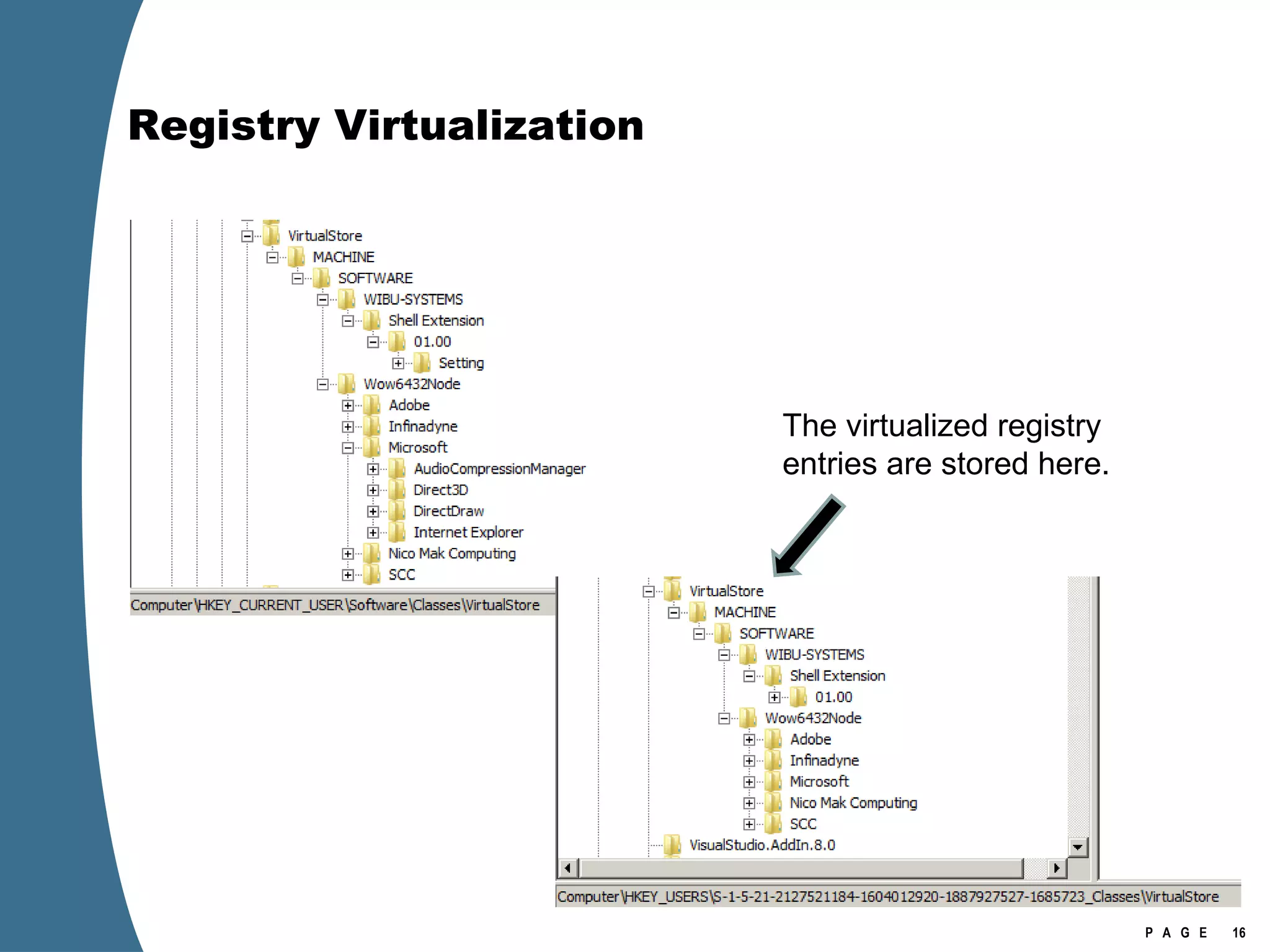
![Registry Virtualization Location of the registry hive file for the VirtualStore Is NOT the user’s NTUSER.DAT It is stored in the user’s UsrClass.dat \Users\[user]\AppData\Local\Microsoft\Windows\UsrClass.dat Investigation of Vista or Windows 2008 requires the investigator to examine at least two account specific registry hive files for each user account. NTUSER.DAT UsrClass.dat](https://image.slidesharecdn.com/ctinwindowsforensicsoverview-090406155625-phpapp02/75/Vista-Forensics-17-2048.jpg)



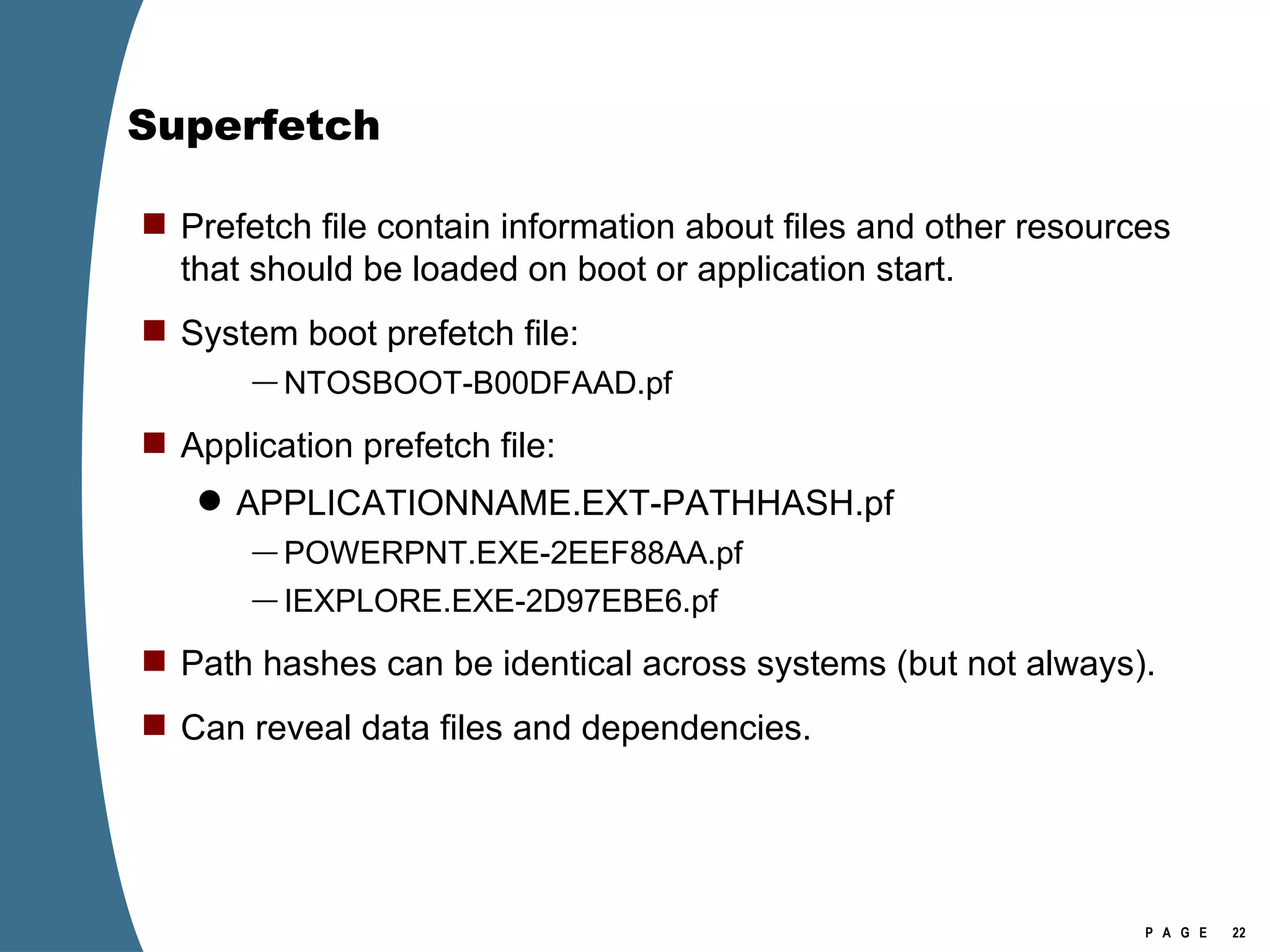



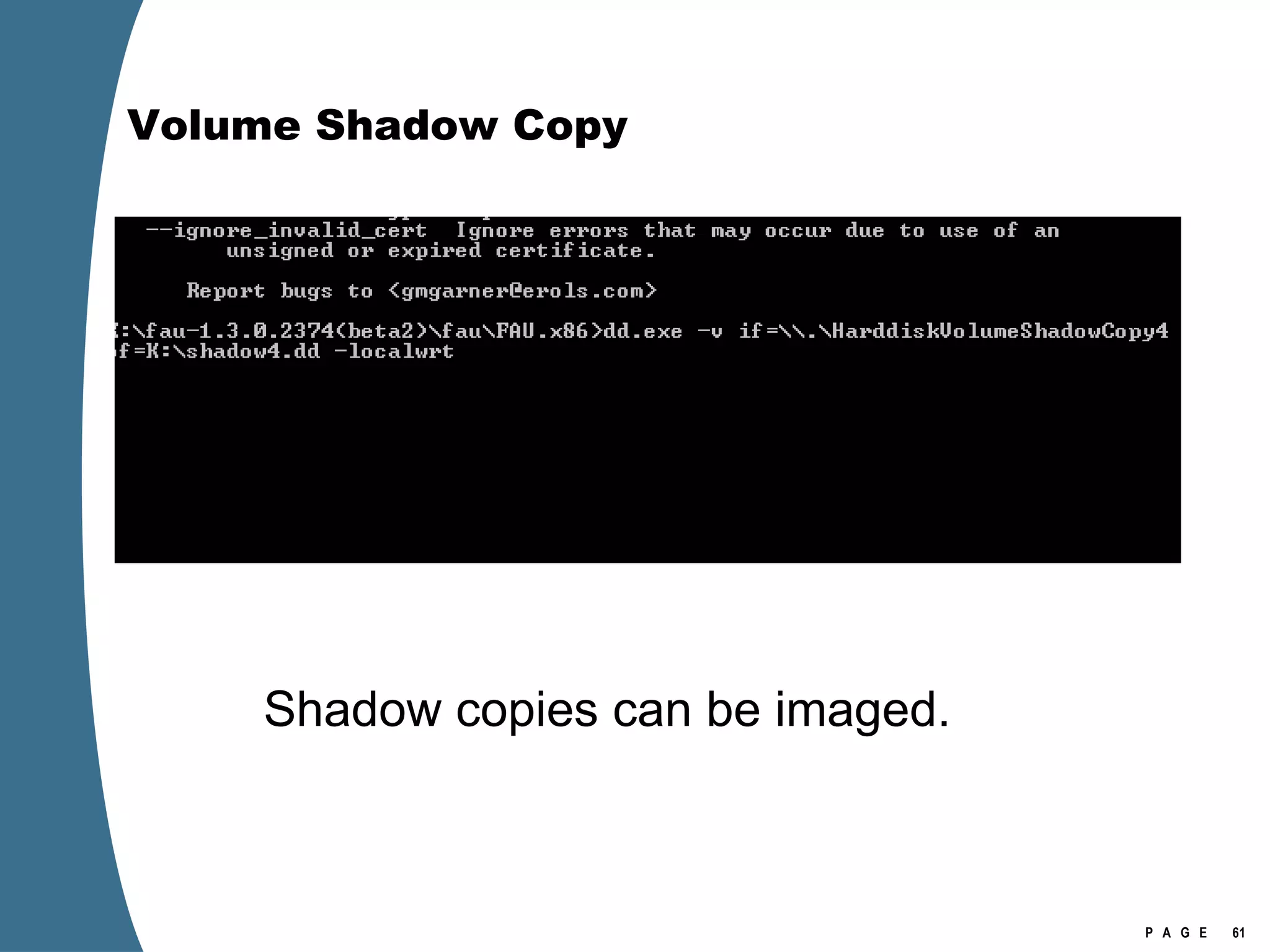
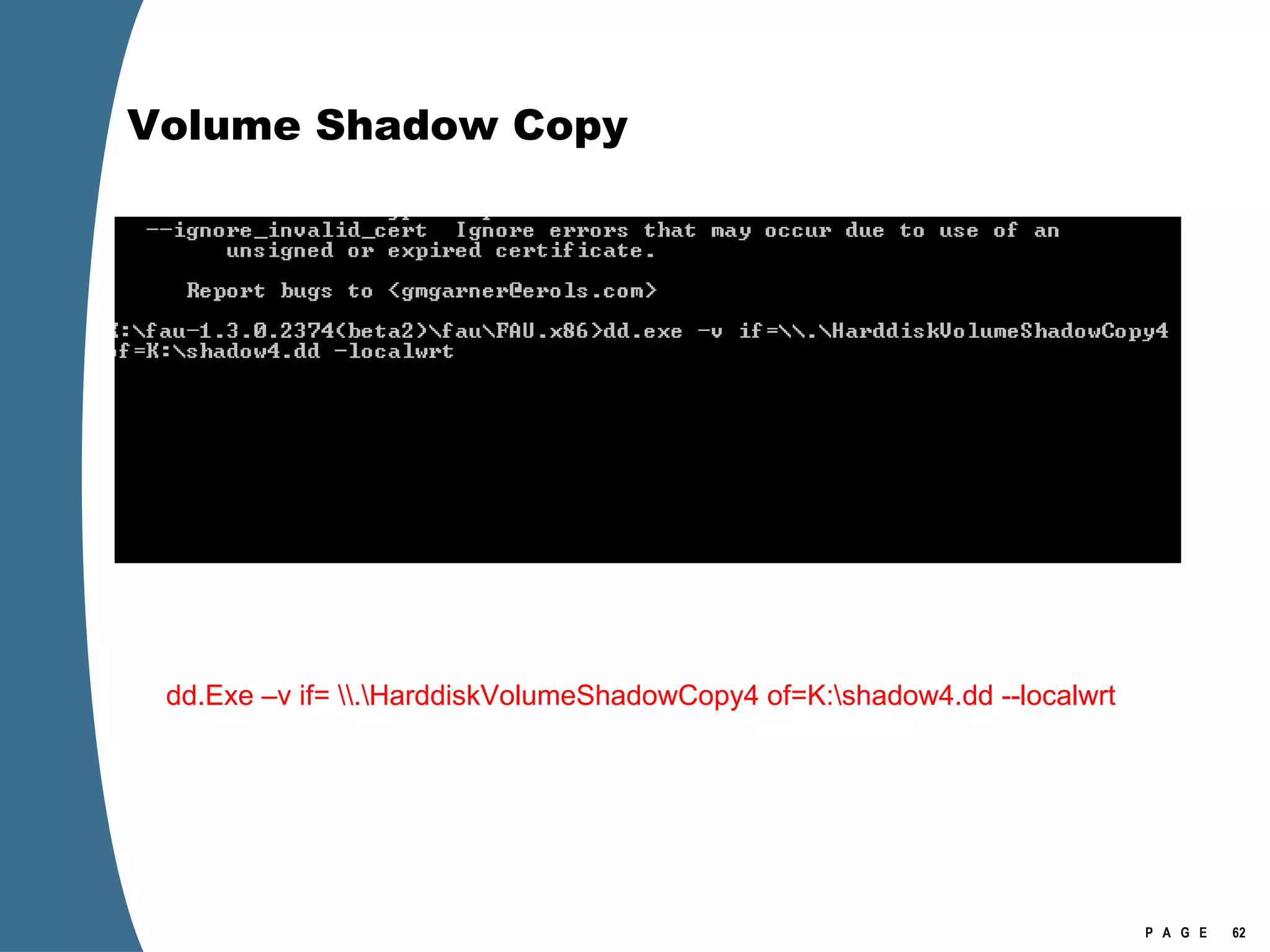
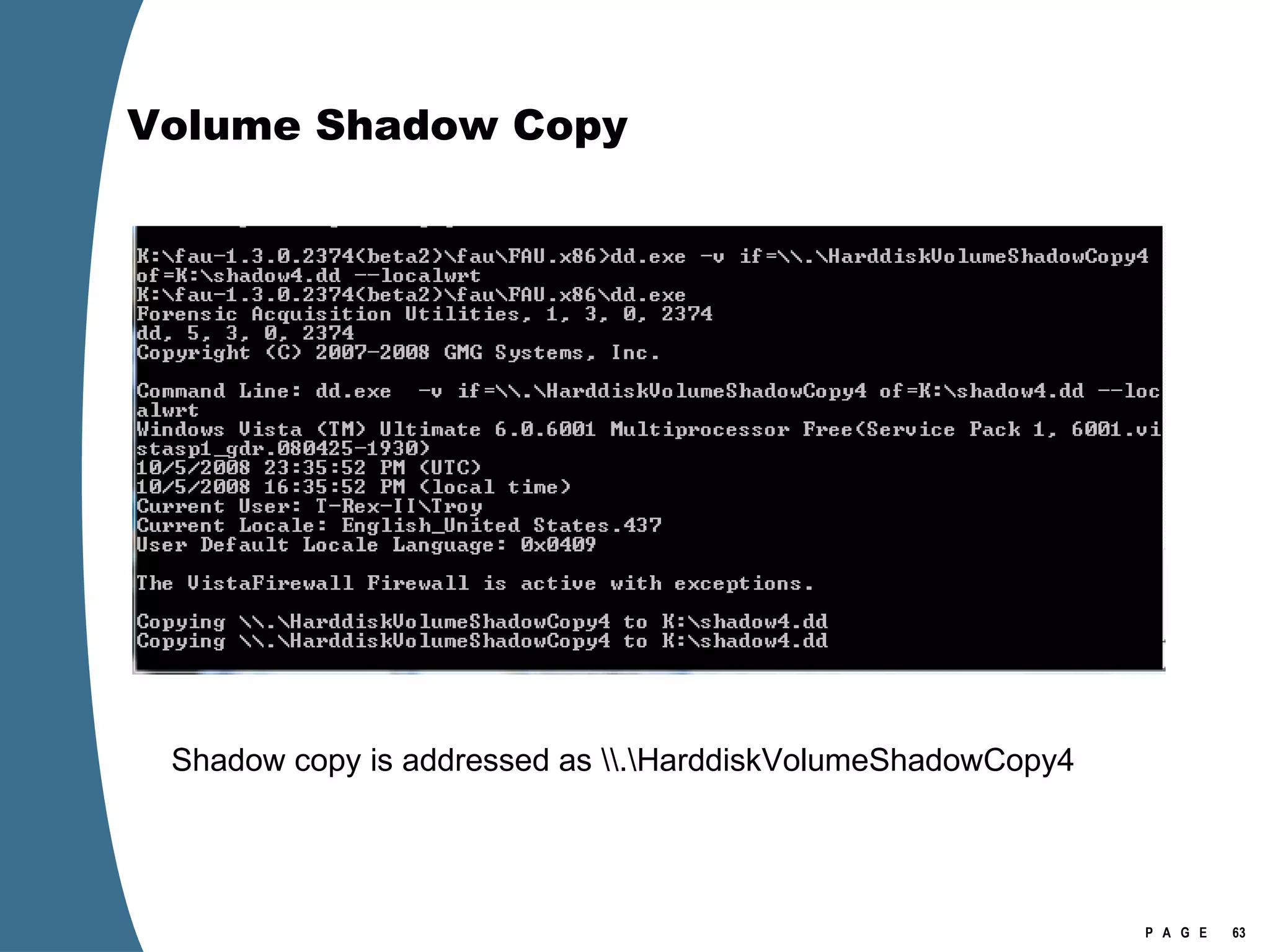
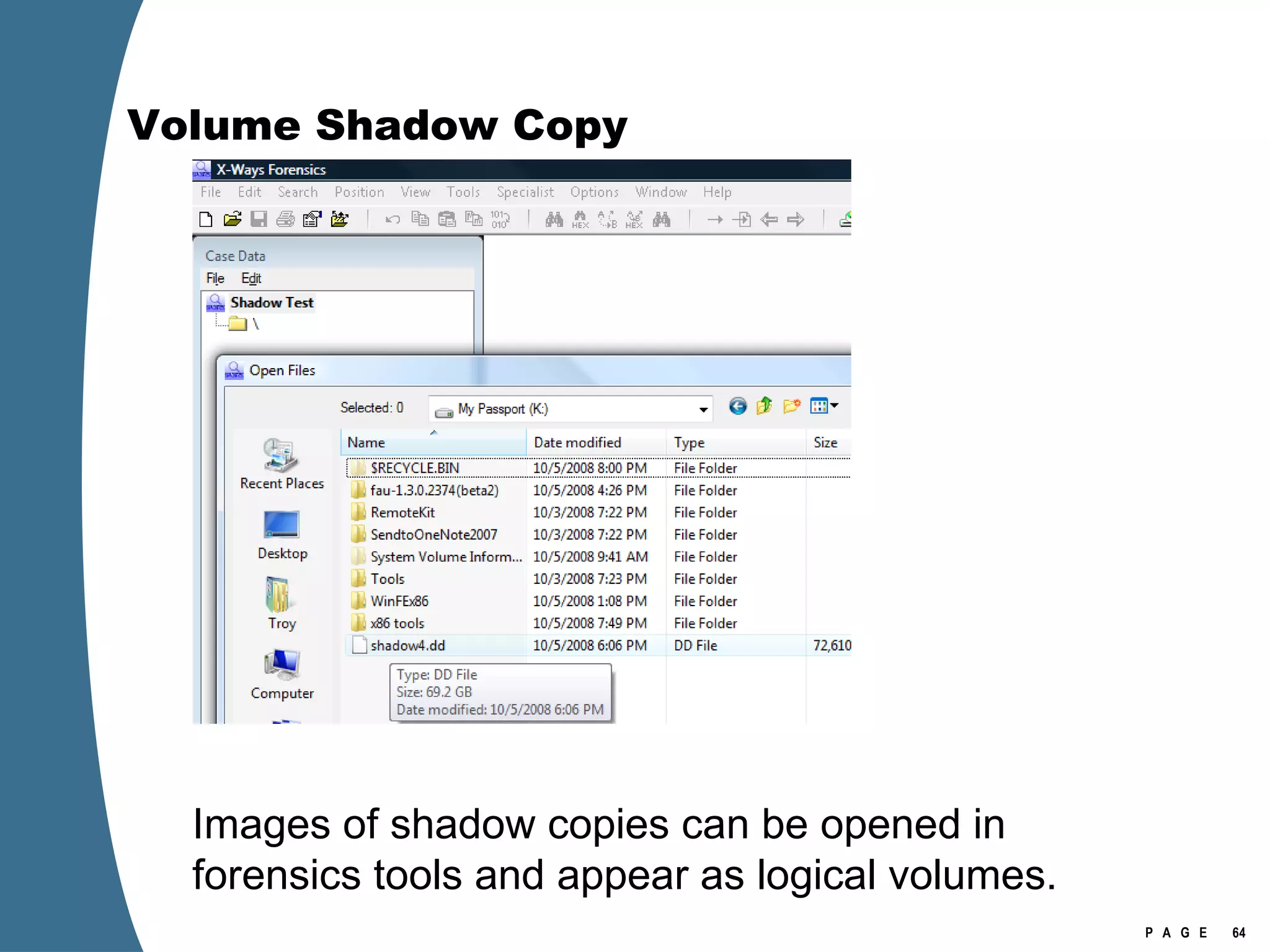
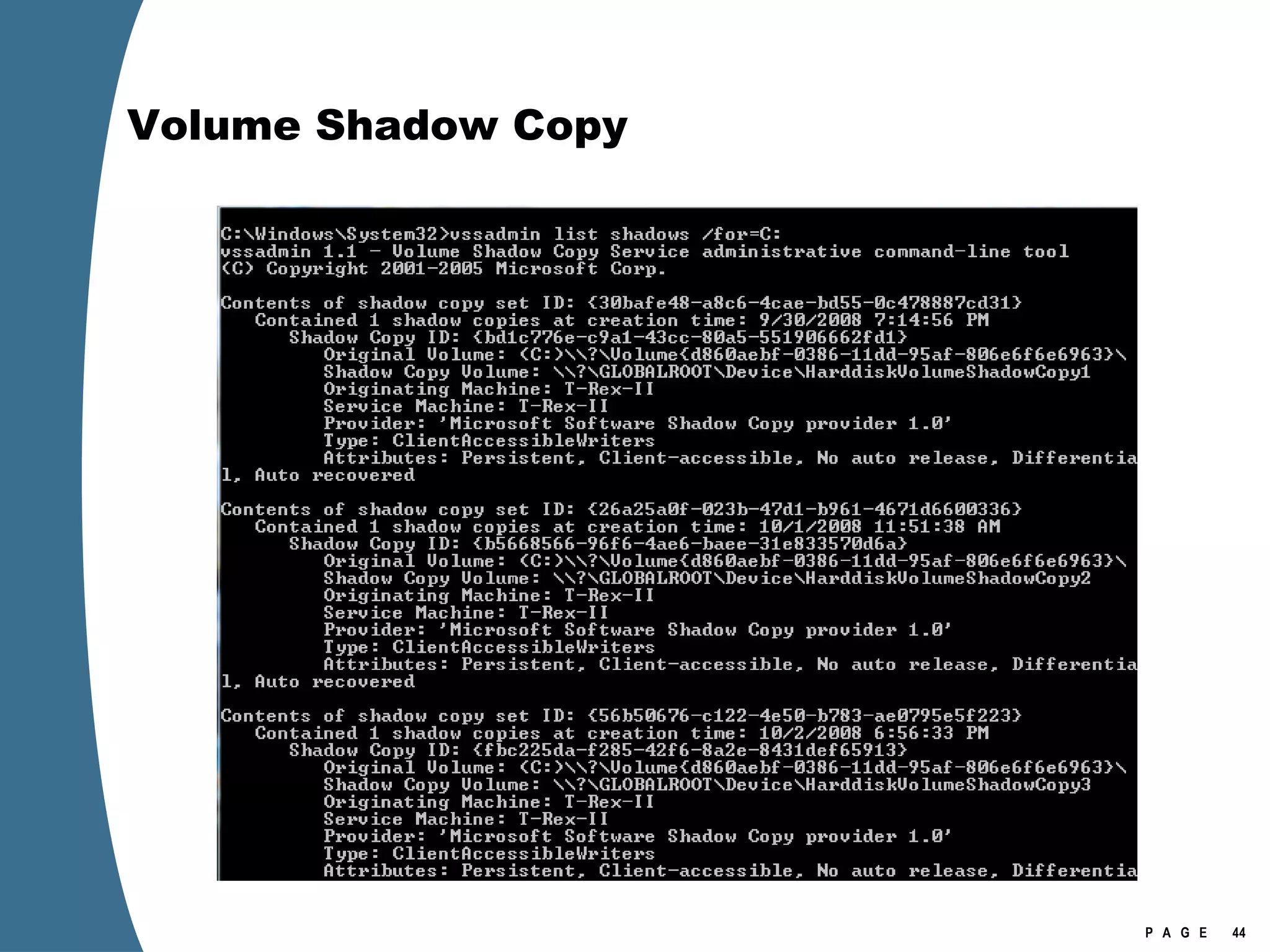
![Volume Shadow Copy vssadmin list shadows /for=[volume]:](https://image.slidesharecdn.com/ctinwindowsforensicsoverview-090406155625-phpapp02/75/Vista-Forensics-43-2048.jpg)
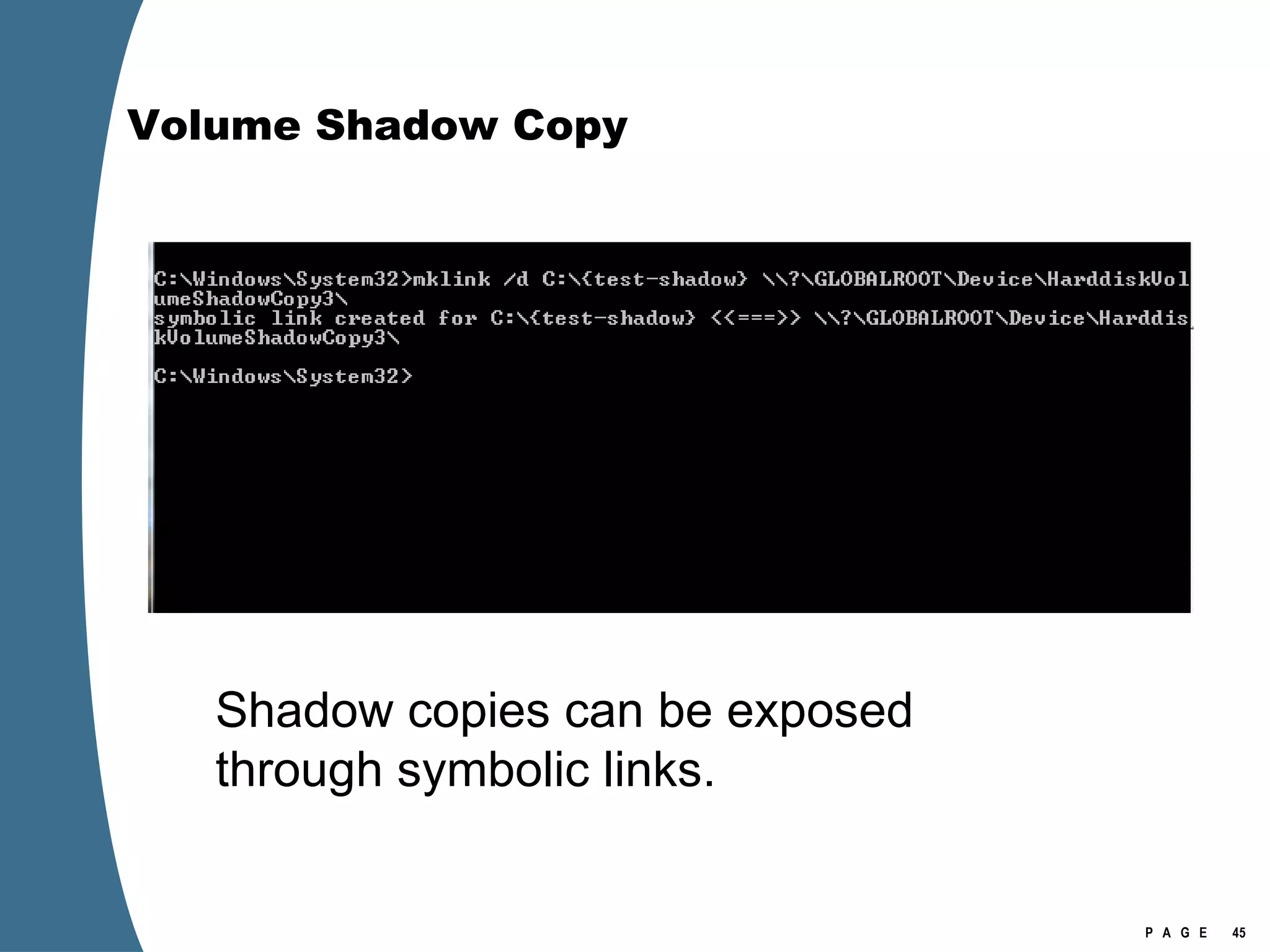
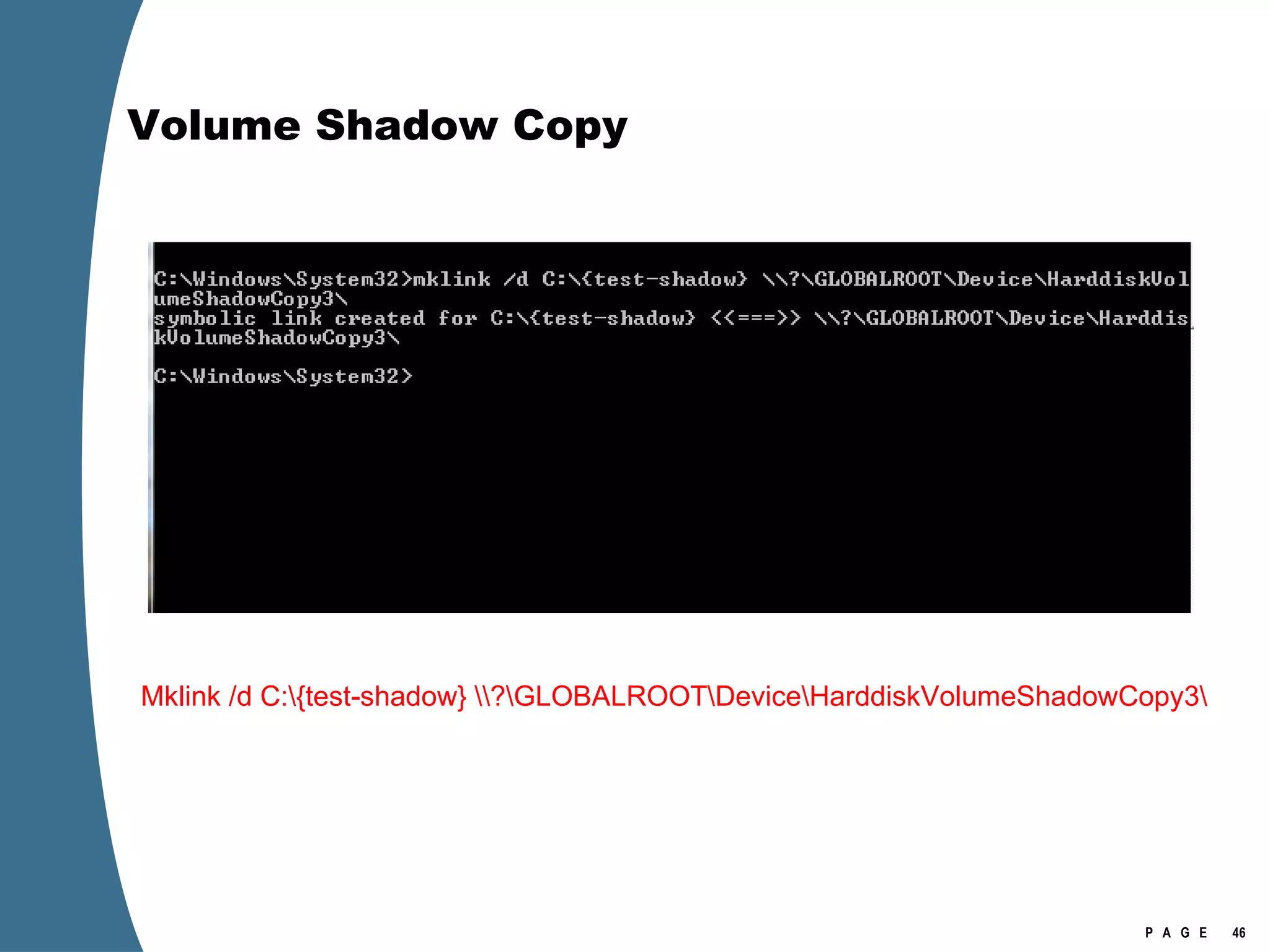
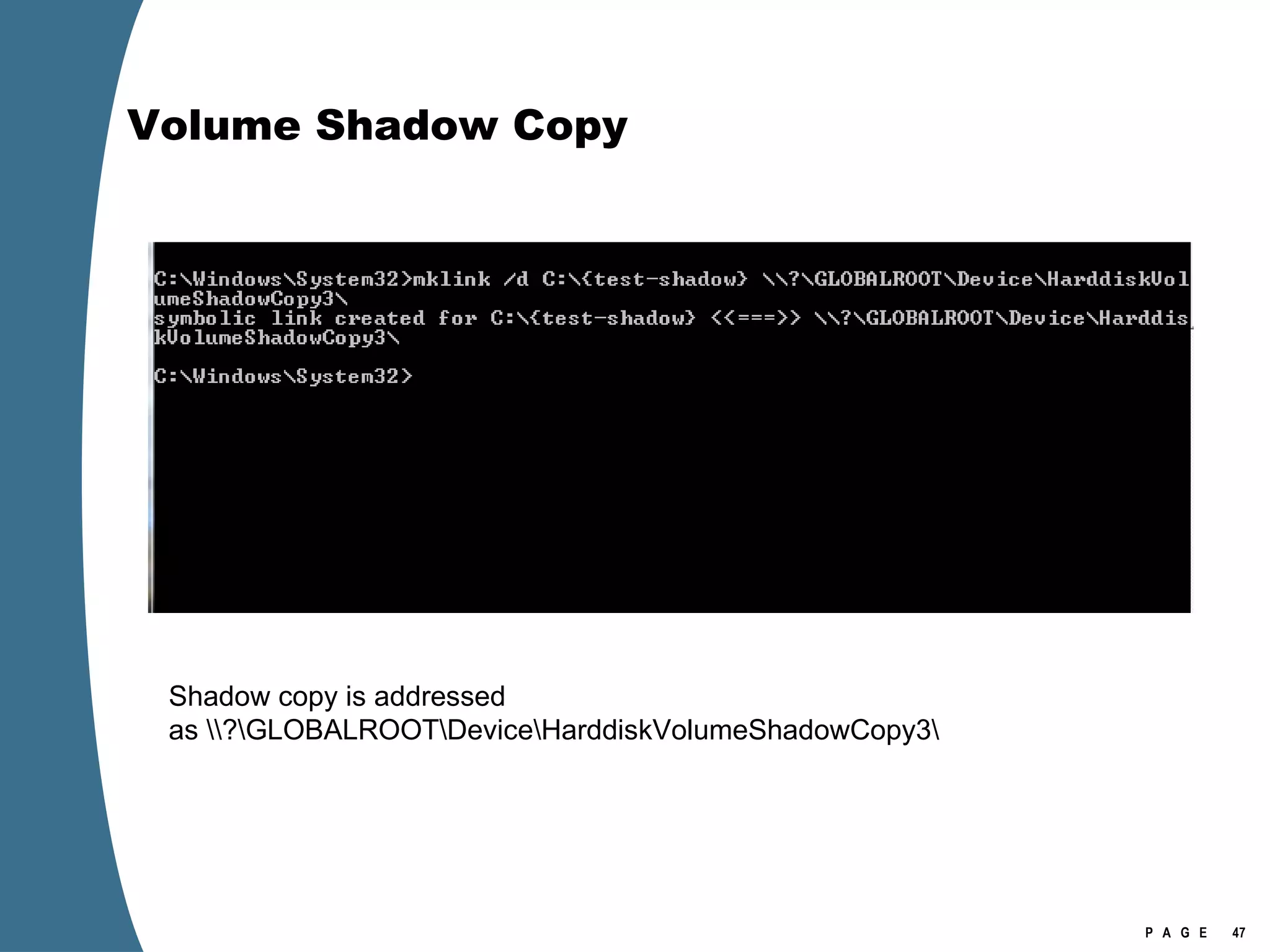
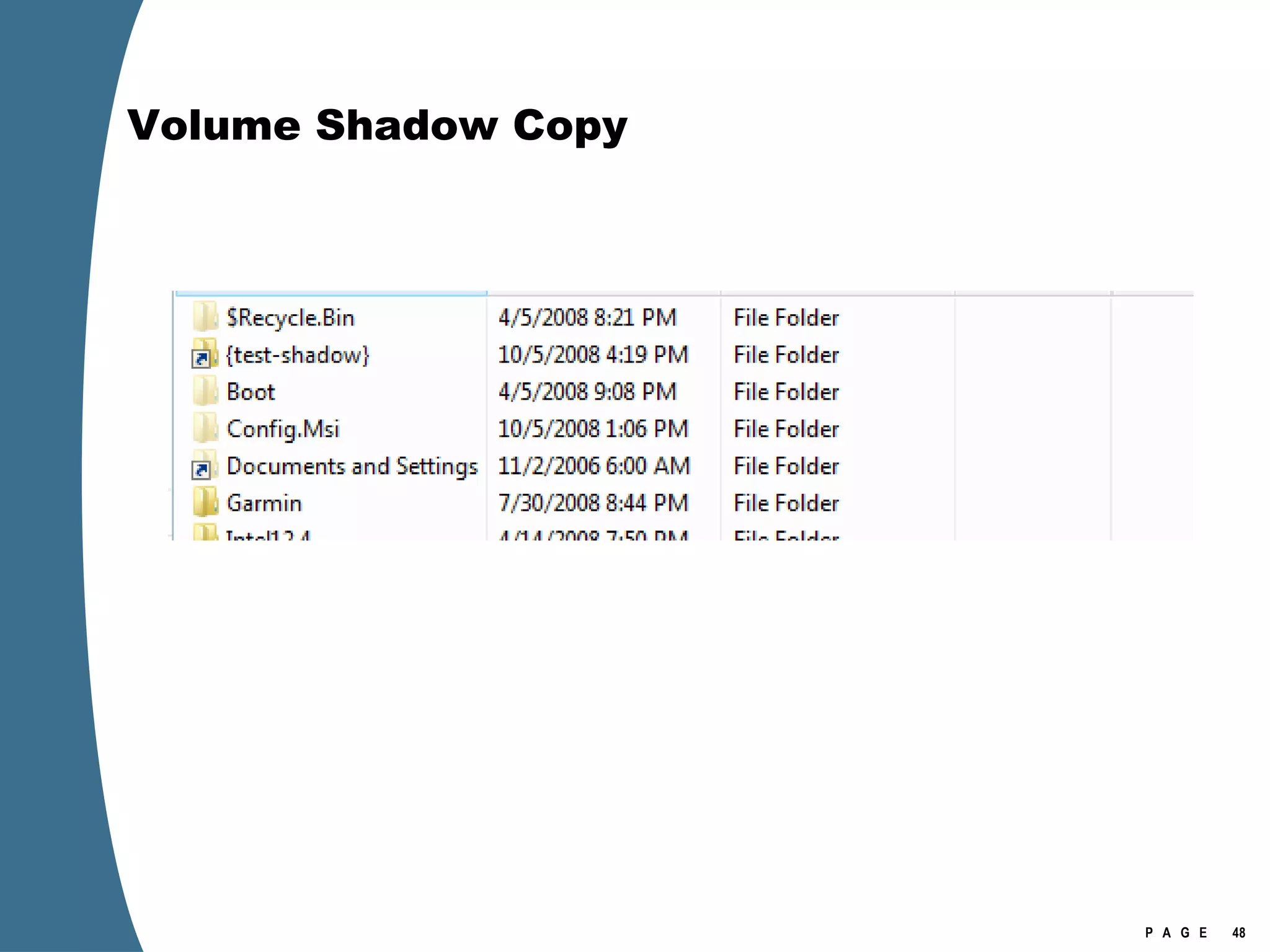
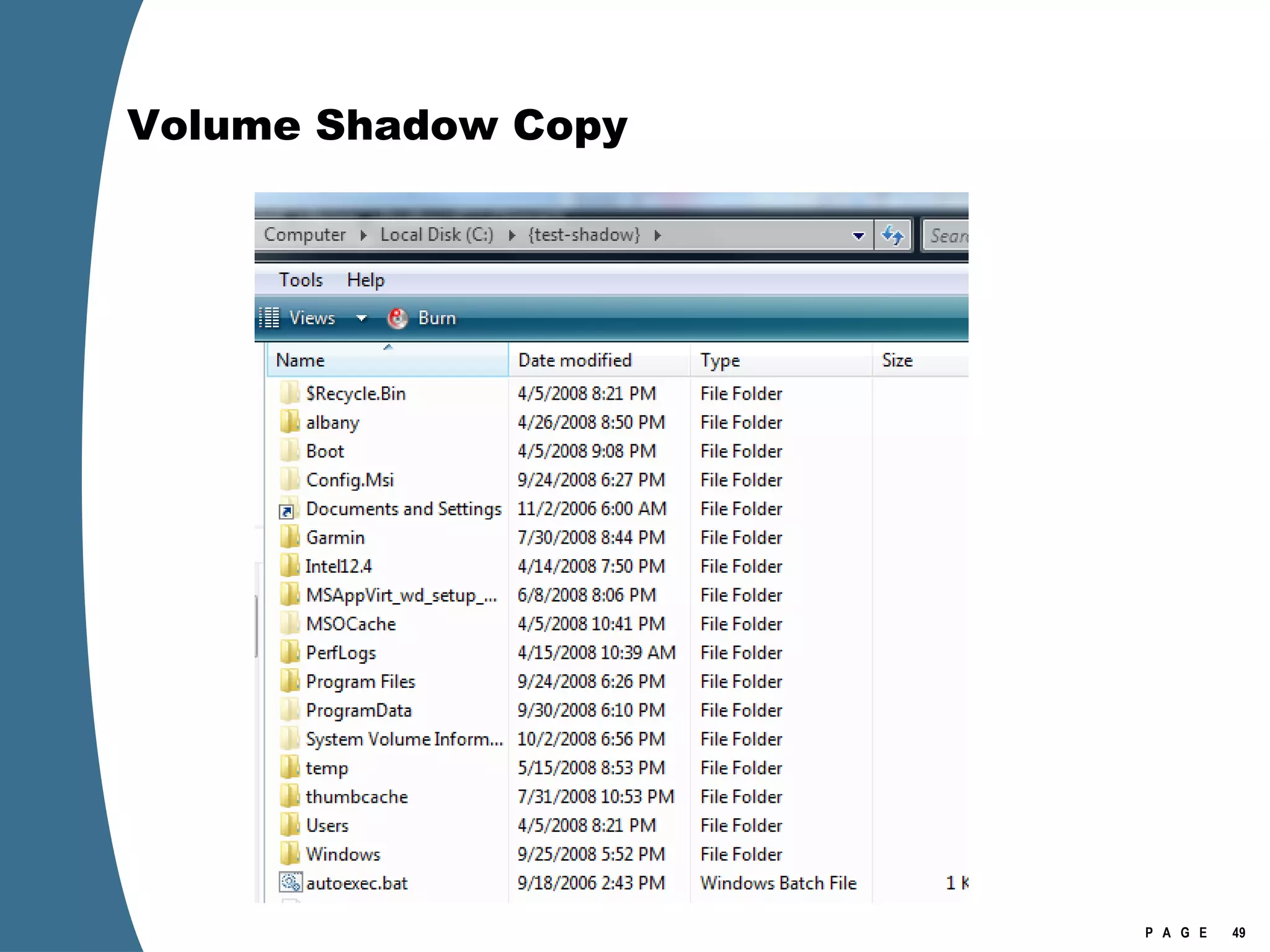
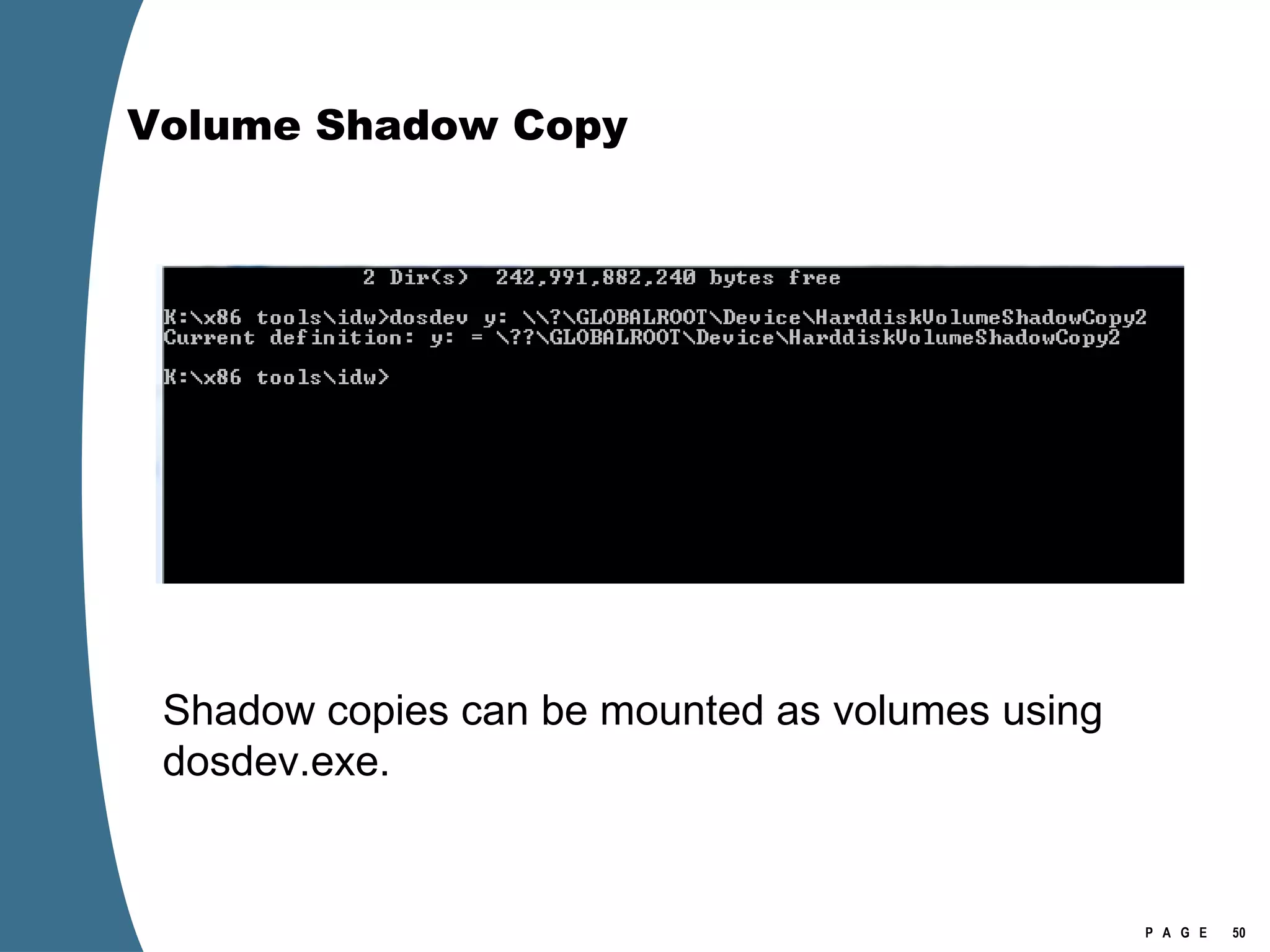
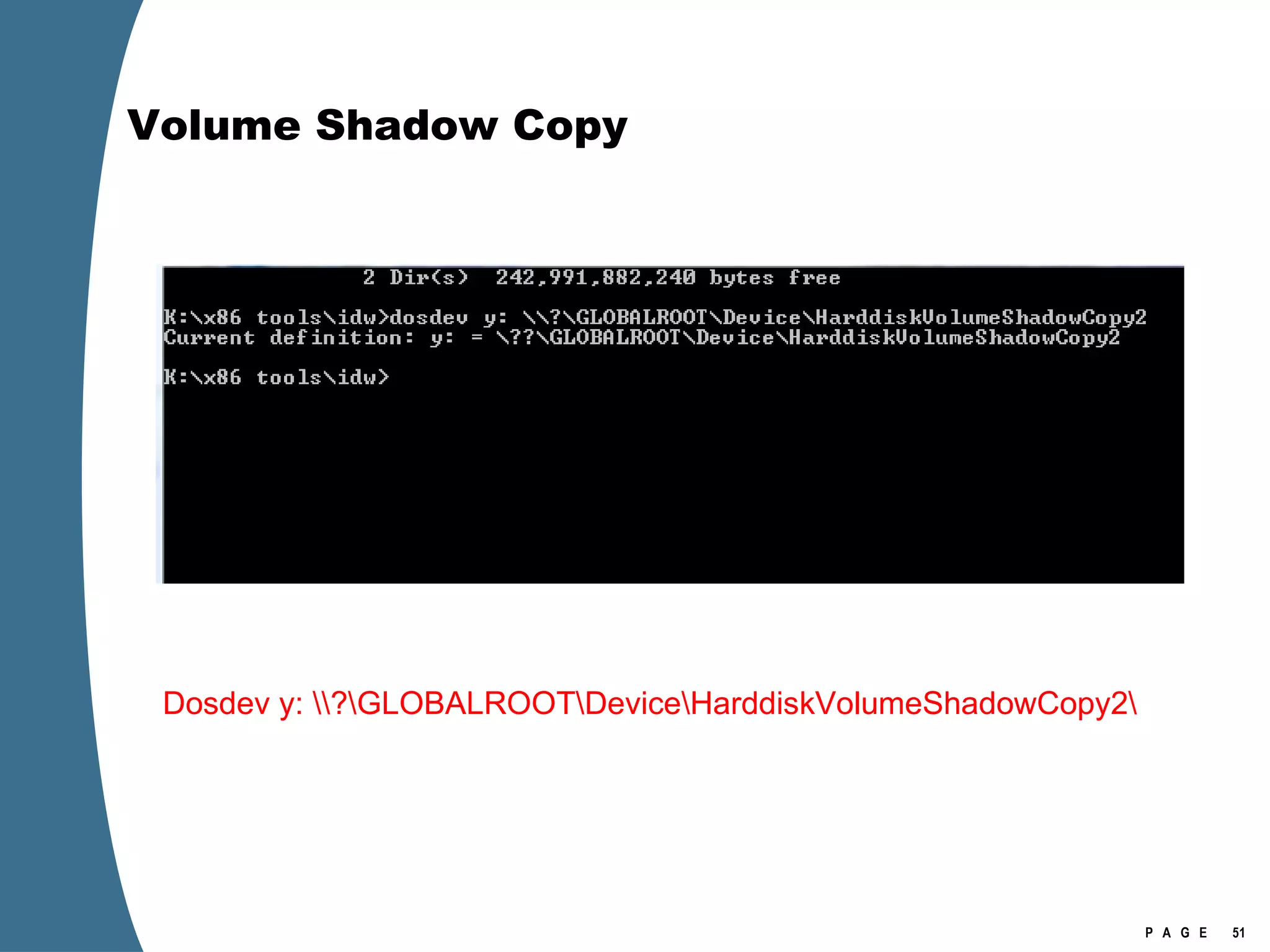
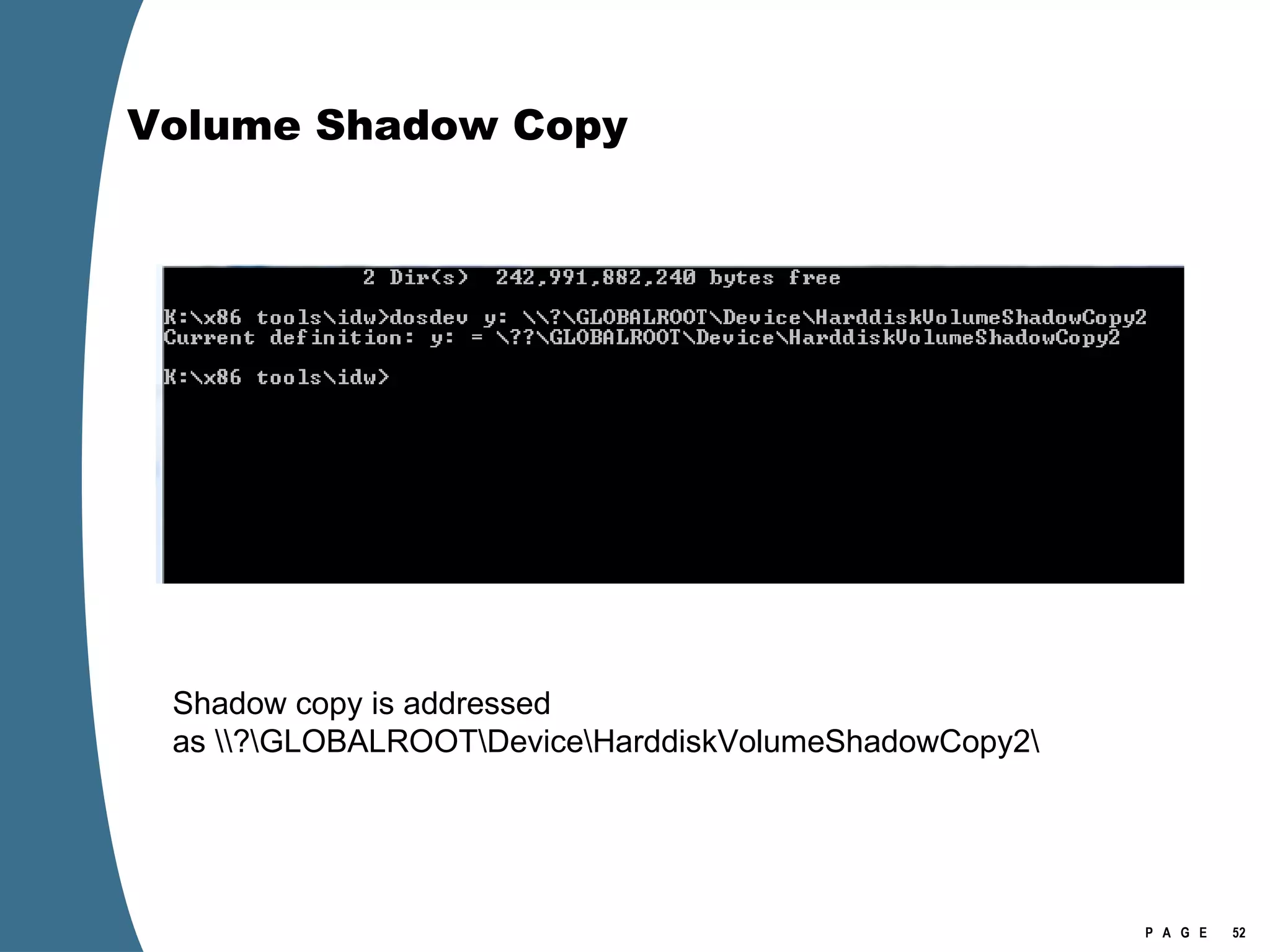
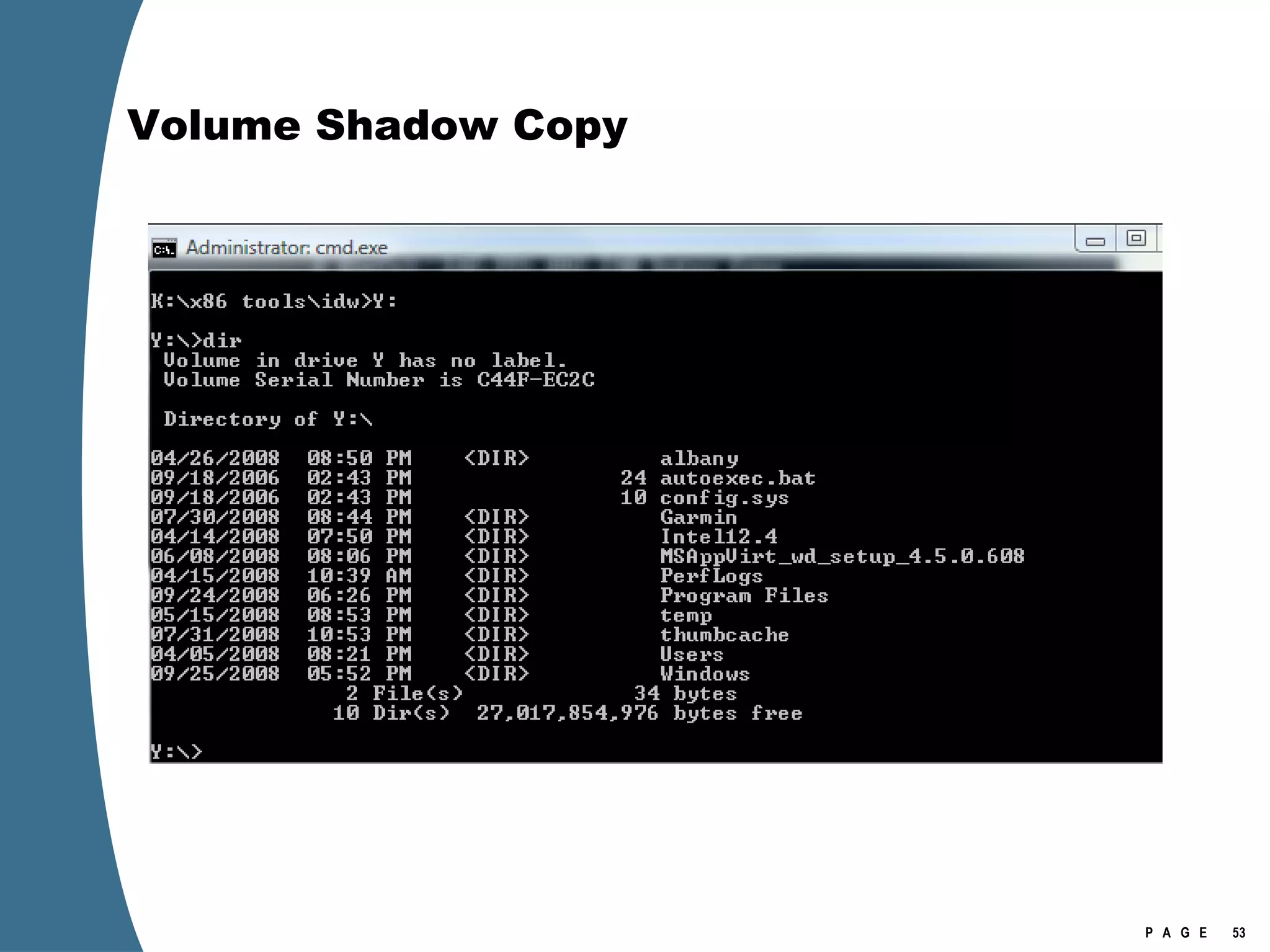
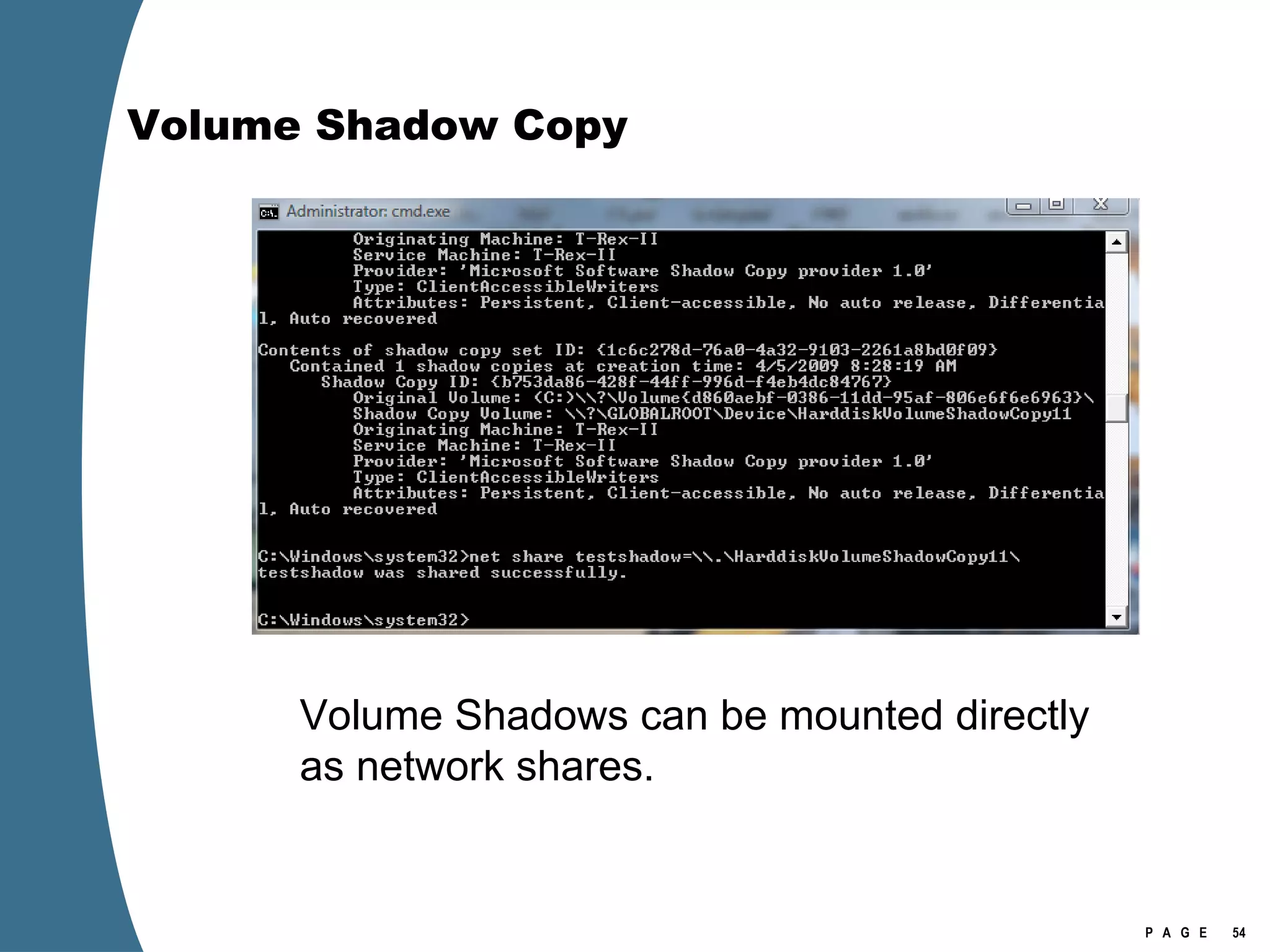
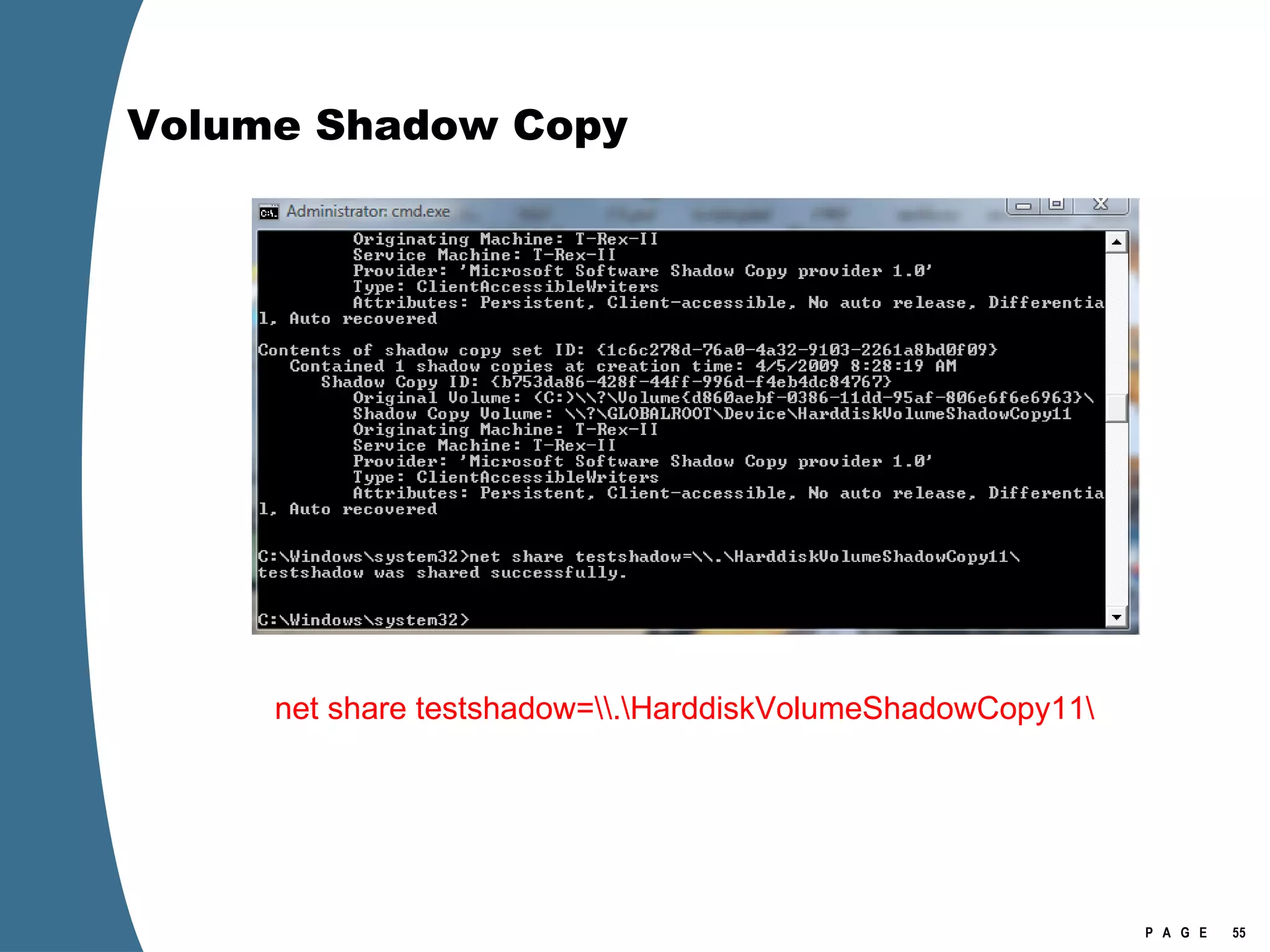
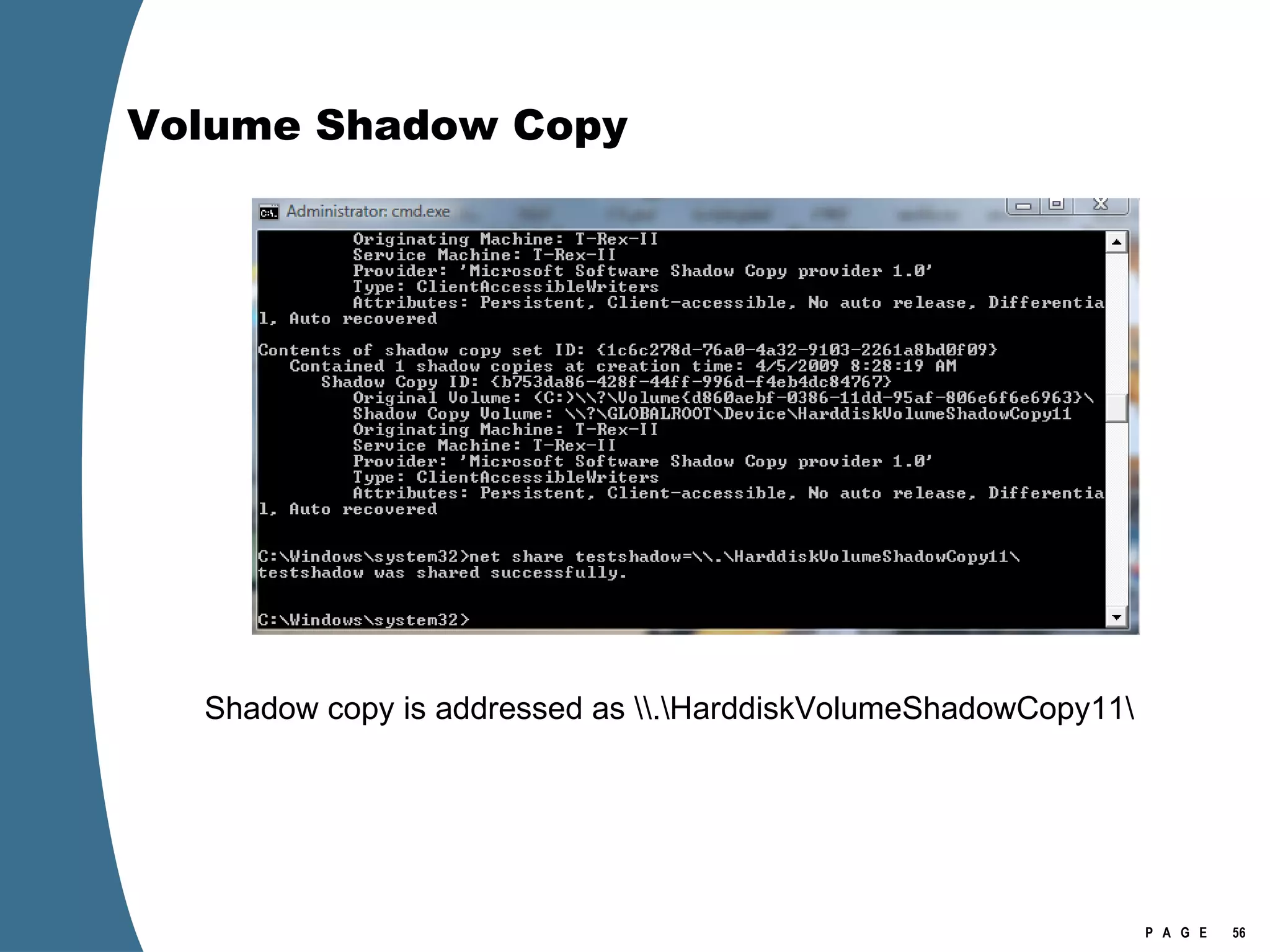
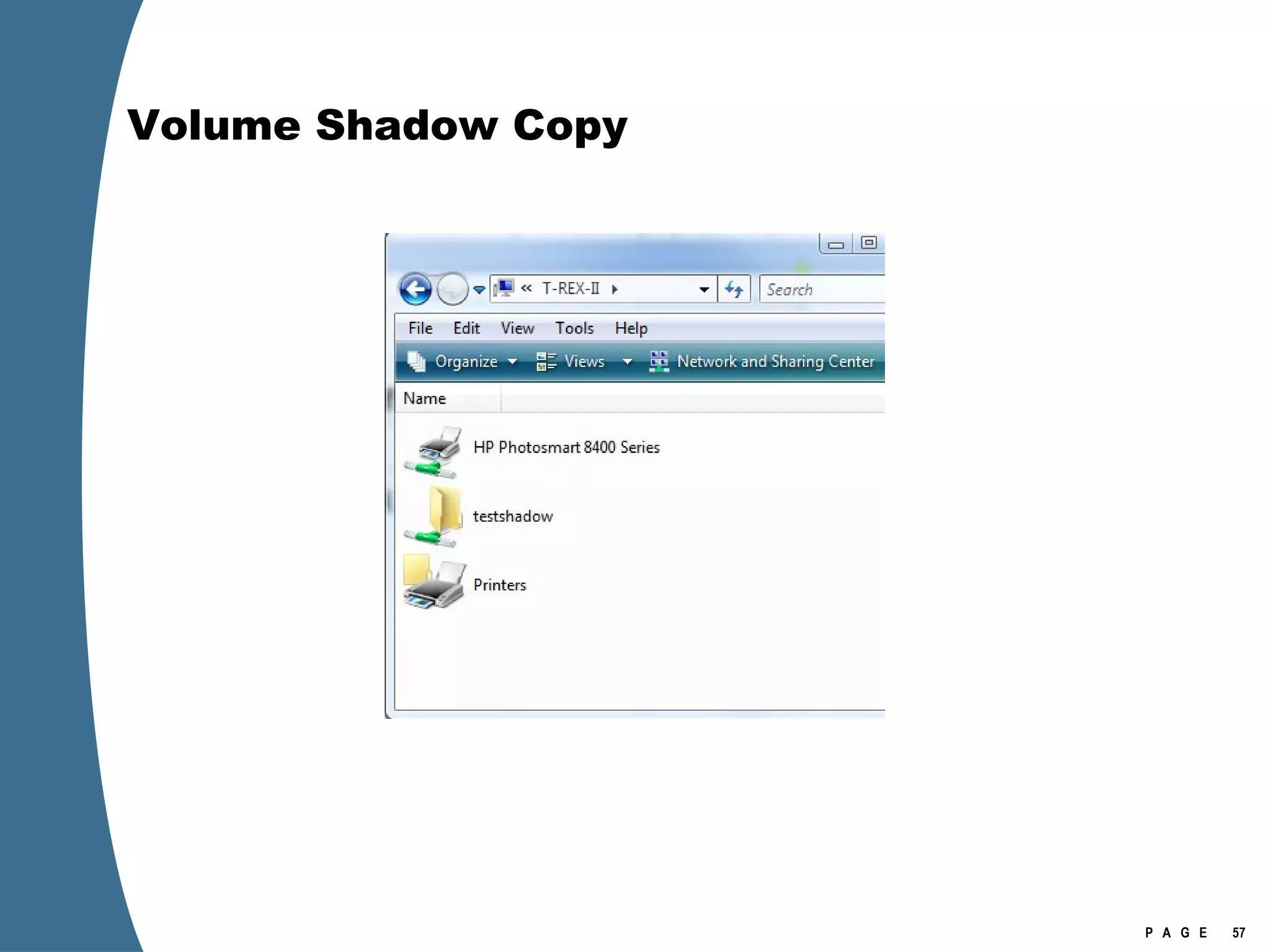
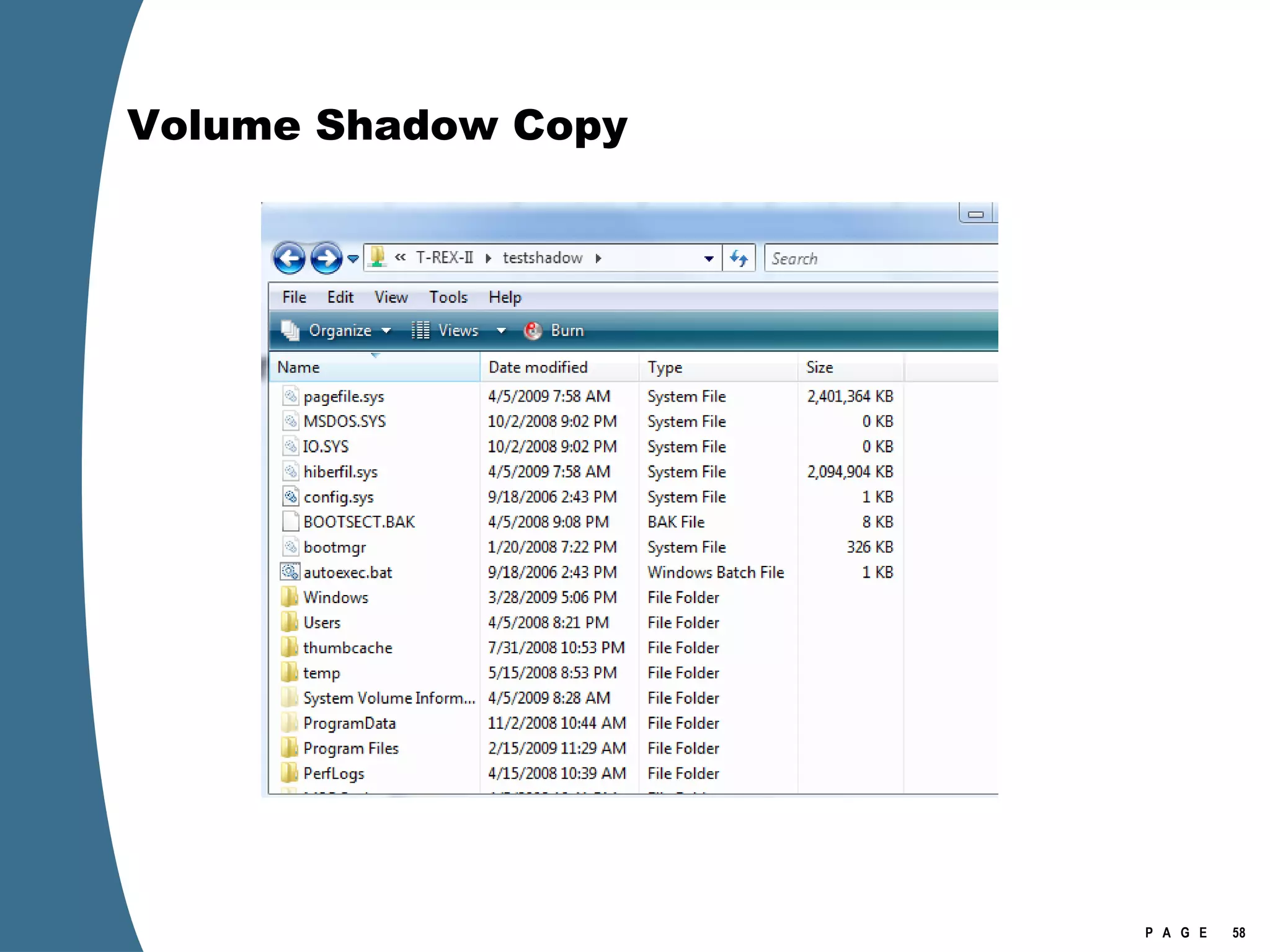
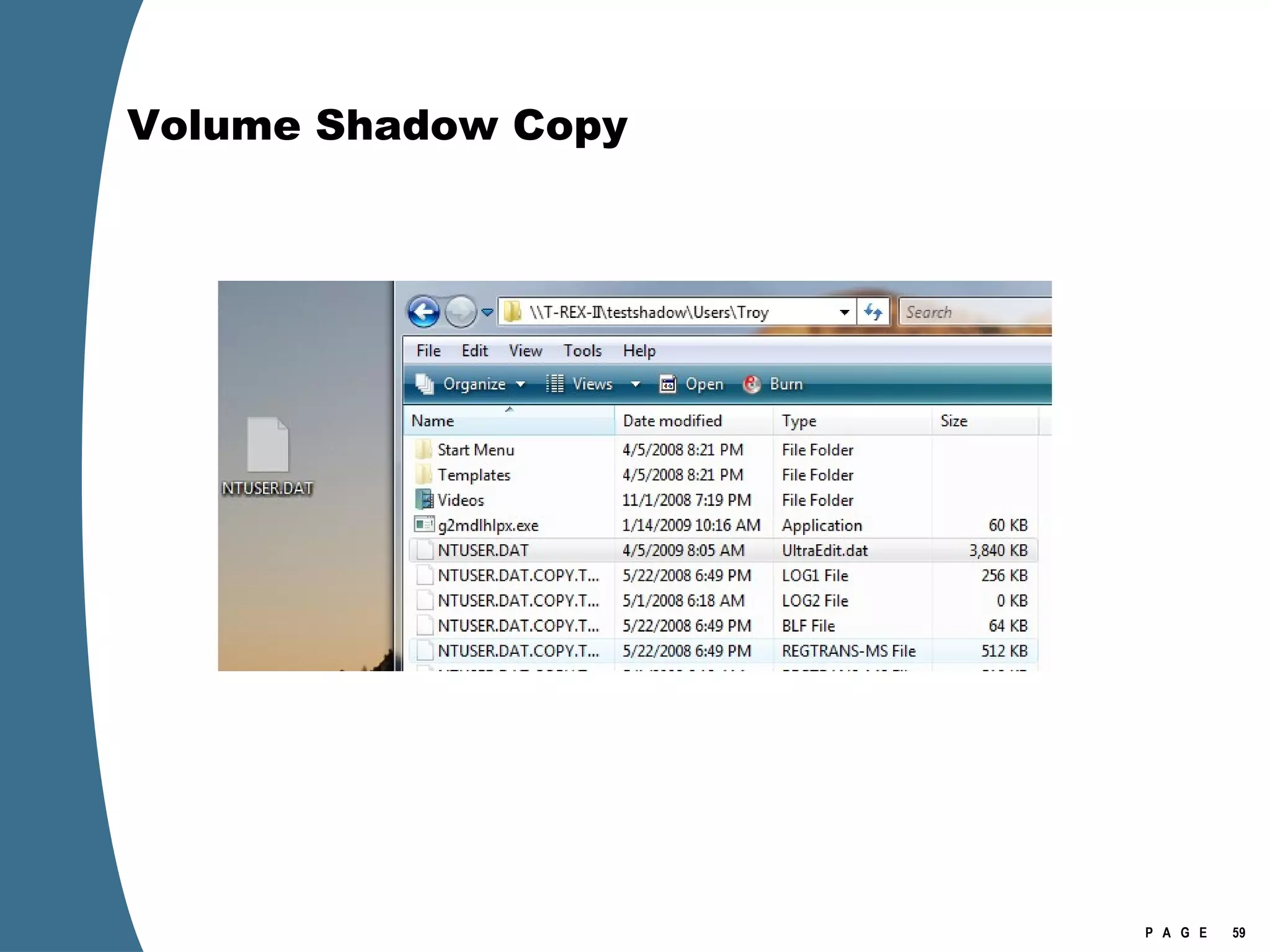
![Volume Shadow Copy > psexec \\[computername] vssadmin list shadows /for=C: > psexec \\[computername] net share testshadow=\\.\HarddiskVolumeShadowCopy20\ PsExec v1.94 - Execute processes remotely . . . testshadow was shared successfully. net exited on [computername] with error code 0. > robocopy /S /R:1 /W:1 /LOG:D:\VSStestcopylog.txt \\[computername] \testshadow D:\vssTest Log File : D:\VSStestcopylog.txt . . .](https://image.slidesharecdn.com/ctinwindowsforensicsoverview-090406155625-phpapp02/75/Vista-Forensics-60-2048.jpg)