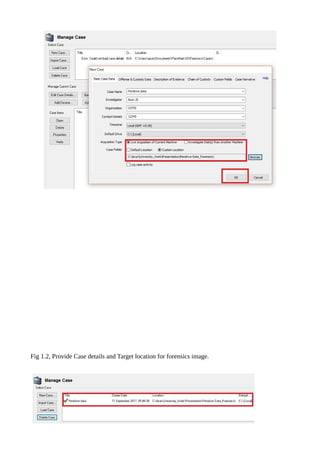
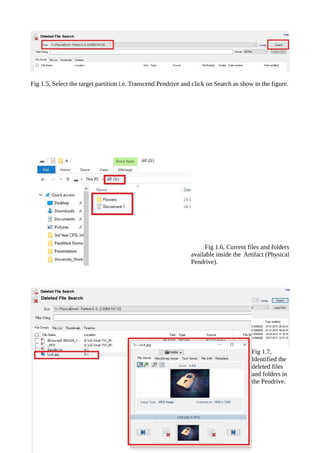
Operating system forensics is essential for investigating user actions on systems, particularly Windows, by interpreting data changes and understanding startup processes. Windows artifacts such as the registry and event logs contain crucial information regarding user activities and system changes, which can be analyzed using forensic tools like Passmark OSForensics. This tool aids in identifying suspicious activities and recovering deleted files efficiently across various Windows platforms.